The Week in Breach News: 08/30/23 – 09/05/23

This week: Thieves went data shopping at Forever 21, more trouble for DeFI companies in a hacking incident at Kroll, Chinese nation-state hackers hit Japan’s National Center of Incident Readiness and Strategy for Cybersecurity (NISC) and a new phishing training kit in BullPhish ID.

See what the biggest cybersecurity challenges are right now in our Mid-Year Cyber Risk Report 2023. DOWNLOAD IT>>

Kroll
Exploit: Hacking
Kroll: Financial and Risk Advisory Company

Risk to Business: 1.676 = Severe
Kroll, a financial advisory firm, has recently experienced a data breach. The firm is handling bankruptcy proceedings for DeFi companies FTX, BlockFi, and Genesis Global Holdco. Kroll said that on August 19, bad actors targeted a T-Mobile account belonging to an employee and gained access to it. The hackers then gained access to files containing the personal information of bankruptcy claimants in the matters of BlockFi, FTX and Genesis. The company was quick to make it clear that the damage is restricted to only those three matters.
How It Could Affect Your Customers’ Business: Business service providers hold a variety of information, especially personal data, that makes them prime targets for cyberattacks
Kaseya to the Rescue: Every company needs to be ready for trouble with an incident response plan in place to minimize downtime and speed up recovery. This checklist can help. DOWNLOAD CHECKLIST>>
Paramount
Exploit: Hacking
Paramount: Entertainment Company



Risk to Business: 1.832 = Moderate
Paramount Global disclosed a data breach after its systems got hacked and attackers gained access to personally identifiable information (PII). Paramount said in breach notification letters that the attackers had access to its systems between May and June 2023. In the attack, bad actors stole some customers’ names, date of birth, Social Security number or other government-issued identification number (such as driver’s license number or passport number) and information related to their relationship with Paramount. Paramount claims that about 100 people were impacted in this incident which remains under investigation.
How It Could Affect Your Customers’ Business: Customers develop distrust for companies that allow their personal data to be stolen.
Kaseya to the Rescue: See how the solutions in Kaseya’s Security Suite help IT professionals minimize risk, avoid cyberattacks and build a cyber-savvy workforce. WATCH THE WEBINAR>>
Forever 21
https://nextdoorsec.com/recent-cyber-incident-hits-forever-21/
Exploit: Hacking
Forever 21: Fashion Retailer





Risk to Business: 1.673 = Severe
Clothing retailer Forever 21 has disclosed a data breach to the Office of the Maine Attorney-General that the personal information of over 500,000 people was exposed in a cyberattack. The retailer said that a cyberattack hit its systems in March 2023. In the incident, bad actors gained access to what appears to be employee data including an employee’s full name, social security number (SSN), date of birth, bank account number and Forever 21 health plan information. Forever 21 said that it has hired a specialist firm to investigate the incident.
How It Could Affect Your Customers’ Business: Retailers aren’t just at risk for exposing customer data, employee data must be protected too.
Kaseya to the Rescue: What cyberattacks are the most popular this year, and what should you be preparing for in 2024? This webinar tells you everything. WATCH WEBINAR>>
The National Safety Council
https://securityaffairs.com/150138/security/nasa-tesla-doj-verizon-2k-leaks.html
Exploit: Supply Chain Attack
Metropolitan Police: Law Enforcement Agency


Risk to Business: 1.710 = Severe
The U.S. National Safety Council (NSC), a non-profit that works to improve driving and workplace safety training, has admitted that a glitch in its’ website left information about some of the world‘s largest companies unprotected for five months. In total, the unsecured website leaked nearly 10,000 emails and passwords of their members, exposing information and leaked credentials for about 2000 organizations, including governmental organizations like the U.S. Department of Justice (DoJ), U.S. Navy, The Occupational Safety and Health Administration (OSHA) as well as big corporations like Tesla, Siemens and Exxon. NSC says that it has fixed the problem.
How It Could Affect Your Customers’ Business: Employee mistakes like this one can be more costly than a cyberattack, but training can prevent them.
Kaseya to the Rescue: Explore how security awareness training helps organizations defend against today’s most dangerous cyber threats in this infographic. DOWNLOAD IT>>
Callaway
Exploit: Hacking
Callaway: Golf Equipment Manufacturer





Risk to Business: 1.673 = Severe
Golf Giant Callaway has revealed that it fell victim to a cyberattack that may have exposed consumer data. The company said that the August 1 incident affected the availability of its e-commerce services briefly and exposed certain customer information to bad actors. Exposed customer data includes full names, shipping addresses, email addresses, phone numbers, order histories, account passwords and answers to security questions. This impacts customers of Callaway’s other brands as well including Odyssey, Ogio, and Callaway Gold Preowned.
How it Could Affect Your Customers’ Business: A successful cyberattack or data security incident impacting one of a company’s brands can easily extend to others quickly.
Kaseya to the Rescue: Our eBook How to Build a Security Awareness Training Program helps IT professionals design and implement an effective training program quickly. DOWNLOAD IT>>


See the path from a cyberattack to a defensive success with managed SOC in this infographic. GET IT>>


Commission des services electriques de Montréal (CSEM)
https://therecord.media/montreal-electricity-organization-lockbit-victim
Exploit: Ransomware
Commission des services electriques de Montréal (CSEM): Infrastructure Manager





Risk to Business: 2.312 = Severe
The LockBit cybercrime gang has claimed responsibility for an attack on Montréal’s 100-year-old electricity infrastructure management organization, Commission des services electriques de Montréal (CSEM). The organization confirmed the attack occurred on August 3 but said it refused to pay the unnamed ransom. CSEM was quick to reassure the public that the data snatched in the attack represents a low risk for both the security of the public and for the operations carried out by the CSEM. The organization said all its systems have been restored and it is working with national authorities and law enforcement in Quebec to investigate the incident.
How it Could Affect Your Customers’ Business: Any successful cyberattack against a utility company or manager is scary, even a minor one like this.
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET THE FACT SHEET>>



Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>


Australia – University of Sydney
Exploit: Hacking
University of Sydney (USYD): Institution of Higher Learning



Risk to Business: 1.302 = Extreme
The University of Sydney (USYD) has announced that a data breach at a third-party service provider may have exposed the personal information of recently applied and enrolled international applicants. The public university started operations in 1850. USYD has not offered specifics about the types or nature of data stolen in the incident, saying that it is still under investigation. The university said that impacted students will be contacted and receive support to mitigate the risk of exposure.
How it Could Affect Your Customers’ Business: Colleges and Universities have been high on cybercriminal priority lists and look set to continue to hold that position in 2024
Kaseya to the Rescue: Follow the path to see how Managed SOC defends businesses from cyberattacks efficiently and effectively without breaking the bank in a handy infographic. GET IT>>


Learn about SMB attitudes toward cybersecurity and other growth opportunities for MSPs. GET INFOGRAPHIC>>


Japan – National Center of Incident Readiness and Strategy for Cybersecurity (NISC)
https://therecord.media/japan-cybersecurity-agency-breached-report
Exploit: Nation-State Attack
National Center of Incident Readiness and Strategy for Cybersecurity (NISC): Government Agency

Risk to Business: 1.282 = Extreme
New reporting says that Chinese hackers breached Japan’s cybersecurity agency and potentially accessed sensitive data stored on its networks for nine months before being discovered. The agency admitted in August that personal data linked to stored email exchanges may have been compromised by the same threat actors in a cyberattack that hit the agency in October of last year. Chinese officials have denied that China is behind the attack.
How it Could Affect Your Customers’ Business: Chinese threat actors being able to penetrate security and dwell for months is not a good look for the agency.
Kaseya to the Rescue: What are the biggest risks that organizations face right now? Find the answer in our Mid-Year Cyber Risk Report 2023! DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>




New phishing simulation kit & landing page in BullPhish ID
A new phishing simulation kit is now live
The new “Netflix – Free Trial V2” phishing simulation kit is now available. This phishing exercise will help employees learn about phishing attacks that use brand impersonation to trick users.
New landing page for custom phishing kits
A new landing page, called OopsLandingPage, is now available in English for use when creating a custom phishing kit. When using this landing page in your phishing kit, users will be taken to this page after clicking on the email and the step of taking them to a credential submission page will be skipped. Therefore, the Data Submitted status won’t be tracked, but No Action, Emails Opened and Links Clicked will still be tracked. The new landing page includes guidelines for identifying phishing threats and a link to the video course How to Avoid Phishing Scams.


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


Top cyberattack trends of 2023 webinar
Watch this recording of our Top Cyberattack Trends of 2023 webinar and delve into the rising tide of cyberthreats. Learn about the most notable data breaches and gain expert insight into the current advanced threat landscape. Don’t let cybercriminals get the upper hand. Watch the recording today!
Did you miss… the Ransomware Rollback Feature Sheet for Datto EDR? DOWNLOAD IT>>


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>





Refresh Your Phishing Basics
Protecting a business from cybercrime starts by protecting it from phishing. From business email compromise to ransomware, 9 in 10 damaging cyberattacks start with a phishing message. Those messages can be very sophisticated, making it hard for employees to make smart choices when handling them. It’s also important to note that 36% of all data breaches involved phishing. This perennial favorite of bad actors threatens every organization, no matter the size, and wears many devious disguises. Therefore, it’s important for every IT professional to be up-to-speed on the basics of phishing and how it is evolving in 2023.
Excerpted in part from Phishing 101, available now. DOWNLOAD IT>>
Learn the language
It can feel like you need to learn a whole new language to really understand cybersecurity. So, before we look at strategies to combat phishing, let’s first make sense of the chatter.
Account takeover (ATO): A form of identity theft and fraud, the goal of an ATO attack is for a malicious third party to capture and exploit a user’s account credentials, enabling the attacker to pose as the victim for other operations.
Angler phishing: Phishing through social media that includes direct messages and phony alert emails from social media sites.
Brand impersonation: Pretending to send messages from a well-known brand to masquerade as a trusted source.
Business email compromise (BEC): Using legitimate email accounts from a business partner to fraudulently obtain money or data.
Credential theft: Tricking the victim into providing their credentials to bad actors, sometimes using a website or link.
Lure: Also called bait or a hook, the lure is an email or message that phishing practitioners use to attract their target’s attention.


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>
Malware attack: A piece of malicious code or software that infects systems to facilitate cybercrime like data encryption or theft. All ransomware is, by nature, malware. However, there are other types of malware, like key loggers and payment skimmers, that can be delivered via phishing. One of the most dangerous malware attacks that businesses face today is wiper malware. This malware deletes your files in a way that is unrecoverable.
Phishing attack: A cyberattack in which a cybercriminal sends a victim a message that is designed to lure them into taking an action that facilitates another kind of cyberattack, like getting someone to open an attachment that contains ransomware. Phishing can also defraud the victim out of valuable information like passwords.
Phishing resistance: This is the amount of savvy that employees show when faced with phishing — a skill set that enables them to spot and stop dangerous messages.
Payload: The “bomb” that a phishing message carries, which is typically some manner of malware or ransomware.


What cybercriminal tricks do employees fall for in phishing simulations? Find out in this infographic. GET IT>>
Quarantine: A separate system location where dangerous messages are sent for review for a preset period of time in order to prevent them from reaching most employees.
Ransomware: A subtype of malware, ransomware encrypts a victim’s data and systems, enabling cybercriminals to demand a ransom for the decryption key. Ransomware can also be used to steal data, shut down production lines and take infrastructure offline. It is the preferred weapon of nation-state cybercriminals.
Spear phishing: Learning details about the target and then crafting an email that will entice them to interact with it. This is the most common form of phishing, often utilizing data about the victim gathered from the dark web. It is also the primary delivery system for malware and ransomware.
Spoofing: Attacks that take a legitimate message, clone it and then use it to facilitate a phishing attack.
Whaling/CEO fraud: A highly targeted, sophisticated attack aimed at a CEO or another senior executive in order to persuade them to perform an action, such as a wire transfer of funds.


See the keys to selecting a Managed SOC to find the perfect one for your clients & your MSP. GET CHECKLIST>>
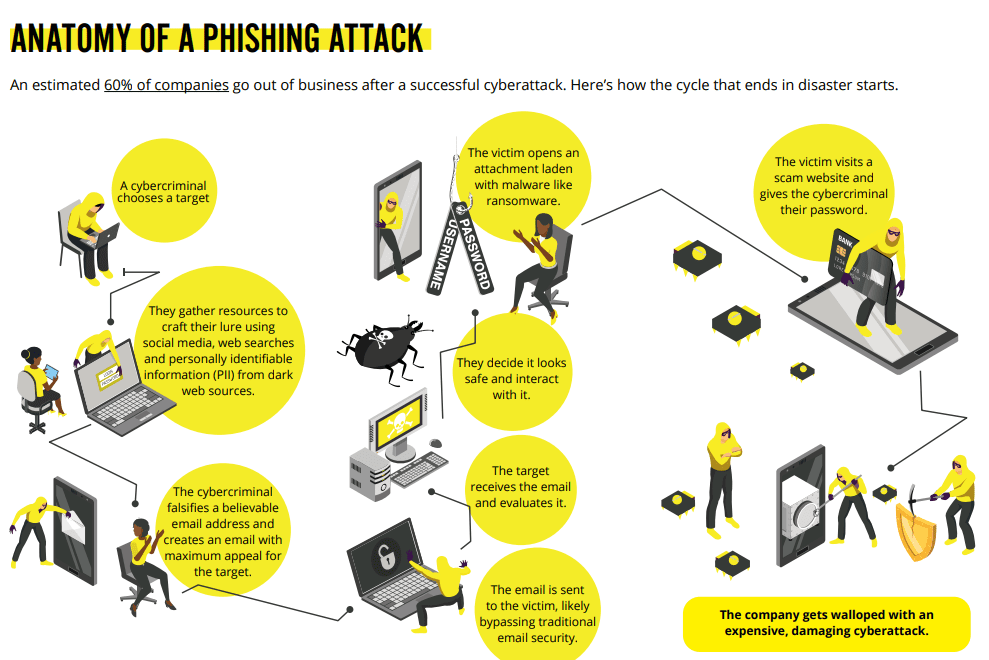
Anatomy of a phishing attack
An estimated 60% of companies go out of business after a successful cyberattack. Here’s how the cycle that ends in disaster starts.
- A cybercriminal chooses a target.
- They gather resources to craft their lure using social media, web searches and personally identifiable information (PII) from dark web sources.
- The cybercriminal falsifies a believable email address and creates an email with maximum appeal for the target.
- The email is sent to the victim, likely bypassing traditional email security.
- The target receives the email and evaluates it.
- They decide it looks safe and interact with it.
- The victim opens an attachment laden with malware, like ransomware.
- The victim visits a scam website and gives the cybercriminal their password.
- The company gets walloped by an expensive, damaging cyberattack.

Source: Kaseya
Phishing simulations teach employees to spot and stop phishing
Security awareness training that includes phishing simulations is an extremely effective and affordable way to keep employees from falling victim to phishing and improve a company’s overall security posture. In a report by Microsoft, analysts determined that when employees receive simulated phishing training, they’re 50% less likely to fall for phishing.
Here are the results of hundreds of phishing simulations using BullPhish ID to give you an insight into the cybercriminal tricks that employees might fall for.
The top three phishing simulation emails that successfully drew clicks
- Office 365: “Suspicious Login” with 10,879 clicks.
- FedEx: “Package Delivery” with 6,535 clicks.
- Google Docs: “Invitation to Edit” with 4,492 clicks.
Top three phishing simulation campaigns that captured credentials and data
- FedEx: “Package Delivery” with 2056 captures.
- Office 365: “Suspicious Login” with 1736 captures.
- COVID-19: “SharePoint Webinar” with 1440 captures.
Source: Kaseya


This infographic helps IT professionals get the most out of a security awareness training solution. DOWNLOAD IT>>
Kaseya’s Security Suite Offers IT Professionals the Tools for Security Success
Get powerful protection and must-have tools for keeping businesses out of cybersecurity trouble with Kaseya’s Security Suite.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents employee mistakes and reduces a company’s risk of being hit by a cyberattack.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection around with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
Graphus — Automated email security is a cutting-edge solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
Kaseya Managed SOC powered by RocketCyber — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).


See how Managed SOC gives businesses an essential edge against cyberattacks. DOWNLOAD INFO SHEET>>


Must-have Security Tools For 2023 And Beyond
Rapid-fire Demos of the Kaseya Security Suite
Wednesday, September 13th |1 pm ET / 10 am PT
To actively combat the ever-evolving threat landscape of 2023 and beyond, you must consistently reimagine cybersecurity. Join our cybersecurity experts on September 13 at 1 PM ET / 10 AM PT to learn how our innovative cybersecurity products — Graphus, Dark Web ID, BullPhish ID and Kaseya Managed SOC powered by RocketCyber — take your security to the next level. Register today and discover how you can significantly bolster your IT security. REGISTER NOW>>
August 31: Kaseya + Datto Connect Local Sweden REGISTER NOW>>
September 7: Kaseya + Datto Connect Local Netherlands REGISTER NOW>>
September 14: Kaseya + Datto Connect Local San Antonio REGISTER NOW>>
September 21: Kaseya + Datto Connect Local Nashville “Building the Business” Series REGISTER NOW>>
September 26: Kaseya + Datto Connect Local Sugarland Sales & Marketing Series REGISTER NOW>>
September 28: Kaseya + Datto Connect Local Charlotte REGISTER NOW>>
October 2 – 4: Kaseya DattoCon in Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!