The Week in Breach News: 01/31/24 – 02/06/24

This week: A cyberattack shuts down a New Jersey school district, Global Affairs Canada experiences its second breach in as many years, phishing costs the Passenger Rail Agency of South Africa $1 million and a dive into the surge in data breaches.

See why choosing a smarter SOC is a smart business decision. DOWNLOAD AN EBOOK>>

AnyDesk
Exploit: Hacking
AnyDesk: Technology Company

Risk to Business: 1.437 = Extreme
AnyDesk confirmed that it has experienced a cyberattack that resulted in hackers gaining access to the company’s production systems. Anydesk, makers of a popular remote desktop access solution, discovered the intrusion last Friday. The company ultimately determined their systems had been compromised. The threat actors stole source code and code signing certificates. AnyDesk says they have revoked security-related certificates and remediated or replaced systems as necessary. The company was quick to reassure customers that AnyDesk was safe to use and that there was no evidence of end-user devices being affected by the incident. Ransomware was not involved.
How It Could Affect Your Customers’ Business: Cyberattacks on suppliers and service providers can be a fast path to cybersecurity trouble for the businesses they have relationships with.
Kaseya to the Rescue: Get tips for mitigating risk created by business relationships in our eBook The Comprehensive Guide to Third-Party and Supply Chain Risk. DOWNLOAD IT>>
Freehold Township School District (New Jersey)
Exploit: Hacking
Freehold Township School District (New Jersey): Municipal Education Authority






Risk to Business: 1.691 = Severe
Freehold Township School District informed staff, families and students that its schools and offices would be closed due to a cybersecurity incident on January 28. The incident impacted eight K-8 schools, leaving them closed for a day at the beginning of the new term as parents scrambled for daycare. Freehold High School, which is part of a separate school district, was not impacted. Officials did not say if any data had been stolen.
How It Could Affect Your Customers’ Business: Schools have been firmly in cybercriminals’ sights because they can’t afford downtime, making them more likely to pay a ransom.
Kaseya to the Rescue: Learn more bout the cybersecurity threats that K-12 schools are experiencing in our infographic The Top Cyber Threats Schools Face and How to Stop Them. GET IT>>
Keenan & Associates
https://www.bankinfosecurity.com/insurance-broker-notifying-15-million-health-info-hack-a-24210
Exploit: Ransomware
Keenan & Associates: Insurance Broker






Risk to Business: 1.643 = Severe
California-based Keenan & Associates, an insurance brokerage that handles employee benefits, workers’ compensation and property liability, is notifying more than 1.5 million individuals that it fell victim to a ransomware attack in August 2023. In the incident bad actors gained access to some internal systems at for about a week, between Aug. 21 and Aug. 27. A wide assortment of data was snatched including an insured’s names, birthdates, numerical identifiers such as Social Security, passport number and driver’s license, health insurance information and general health information.
How It Could Affect Your Customers’ Business: This is just the kind of treasure trove that cybercriminals love to get their hands on.
Kaseya to the Rescue: Learn about the growing list of cybersecurity challenges that organizations face in the Kaseya Security Survey Report 2023. DOWNLOAD IT>>
The Government of Fulton County, Georgia
https://www.cnn.com/2024/01/30/tech/fulton-county-cyberattack/index.html
Exploit: Ransomware
The Government of Fulton County, Georgia: Regional Government



Risk to Business: 1.462 = Extreme
Fulton County, Georgia experienced a cyberattack that has knocked out a number of the county government’s systems and services. County officials said in a statement that the county government’s communication, court and tax systems are all experiencing outages, including the Fulton County Board of Equalization and the Board of Assessors. The Fulton County Superior Court was unable to function briefly, including being unable to issue marriage licenses and certificates or process firearms registrations. Residents are being told that their tax payments will not be posted until the system is back online. County officials reassured voters that there was no evidence indicating the cyberattack is related to the state’s election process. However, Fulton County officials are still restricted from accessing the state’s voter registration system, aa a precautionary measure. No timeline has been given on the restoration of services, and no ransom was announced.
How It Could Affect Your Customers’ Business: A cyberattack on a city or regional government can have dangerous consequences when it impedes the operation of emergency services.
Kaseya to the Rescue: Ransomware is often an email-based cyberattack that can lead to disaster. Our Preventing Email-Based Cyberattacks Checklist helps businesses stay out of trouble. DOWNLOAD IT>>


See the challenges companies face & how they’re overcoming them in our Kaseya Security Survey Report 2023 DOWNLOAD IT>>


Global Affairs Canada
Exploit: Hacking
Global Affairs Canada: Government Agency






Risk to Business: 1.702 = Severe
Global Affairs Canada (GAC), the Canadian equivalent to the U.S. state department, said it is investigating a data breach. GAC said in a statement that its investigation has revealed that there has been unauthorized access to the personal information of users, including employees. The data breach affected two internal drives as well as the emails, calendars and contacts of several staff members. The breach occurred between December 20, 2023, and January 24, 2024. The suspected cause of the data breach is a compromised Virtual Private Network (VPN) that is managed by the Federal Government’s Shared Services Canada (SSC).
How it Could Affect Your Customers’ Business: A cyberattack like this could potentially expose sensitive and dangerous information like state secrets.
Kaseya to the Rescue: Learn more about the trade in data and credentials on the dark web and how bad actors make a profit in our infographic 5 Ways the Dark Web Endangers Businesses. DOWNLOAD IT>>


France – Schneider Electric
https://securityaffairs.com/158320/data-breach/schneider-electric-cactus-ransomware-attack.html
Exploit: Ransomware
Schneider Electric: Energy Management Company


Risk to Business: 2.736 = Moderate
The Cactus ransomware group has claimed responsibility for a ransomware attack that hit French energy management and digital transformation company Schneider Electric. The group claims that it stole terabytes of data. The attack impacted the services of Schneider Electric’s Resource Advisor cloud platform causing outages. No other departments or services were impacted. The incident kicked off with an attack on the Sustainability Business division of the company on January 17th.
How it Could Affect Your Customers’ Business: Industrials and infrastructure providers are at high risk for a cyberattack and need to bolster security to prevent downtime.
Kaseya to the Rescue: An endpoint detection and response solution can help businesses stop the spread of a cyberattack fast. This checklist helps you find the right one. DOWNLOAD IT>>


Find out how Datto EDR helps with Health Insurance Portability and Accountability Act (HIPAA) compliance. GET INFO>>


South Africa – Passenger Rail Agency of South Africa (PRASA)
https://www.darkreading.com/endpoint-security/south-african-railways-reports-1m-phishing
Exploit: Phishing
Passenger Rail Agency of South Africa (PRASA): Government Agency






Risk to Business: 1.736 = Serious
Passenger Rail Agency of South Africa (PRASA) has admitted that it lost an estimated one million dollars to a phishing scam, suspected to be a business email compromise (BEC) attack. The organization said that it was ultimately able to claw back half of the money it lost. The incident was revealed in the agency’s annual report.
How it Could Affect Your Customers’ Business: Transportation infrastructure continues to be a priority target for ransomware groups looking to profit from a high-profile attack.
Kaseya to the Rescue: Every organization needs to be ready for trouble with an incident response plan in place. This checklist can help. DOWNLOAD CHECKLIST>>



In The Educator’s Guide to Cybersecurity, see the cyber threats that schools face & how to mitigate them. DOWNLOAD IT>>


Australia – Football Australia
https://www.bankinfosecurity.com/medical-lab-database-exposed-13m-records-covid-test-info-a-24168
Exploit: Human Error
Football Australia: Sports Governing Body






Risk to Business: 1.602 = Severe
Football Australia (FA) has experienced a data breach as a result of a blunder. A developer inadvertently left a crucial server reference in code accessible to the public, leaving a huge treasure trove of information open for the taking. The information exposed may include players’ contracts containing data like personally identifiable information and passport scans. Fan data associated with ticket purchases and information about the FA’s digital infrastructure was also exposed. Researchers discovered the 27 AWS buckets of exposed data, which have been available since early January 2024. FA said that it has informed the Office of the Australian Information Commissioner (OAIC) about the breach.
How it Could Affect Your Customers’ Business: Human error will never fail to be the top cause of cybersecurity problems for businesses, but security awareness training can help mitigate the risk.
Kaseya to the Rescue: See how security awareness training helps keep cybersecurity threats from becoming cybersecurity disasters. DOWNLOAD INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>




The ID Agent & Graphus Q1 Product Innovation webinar replay is now available
Learn more about the innovations and product enhancements we’ve made to our solutions in Q1 2024 plus get the first look at what’s next for ID Agent and Graphus. We’ve had a busy innovation cycle, with bold new updates and fresh integrations that will make your life easier.


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


Get our 5 Minute Guide to Phishing Attacks and Prevention infographic!
Phishing has reached unprecedented levels, and cybercriminals’ phishing tricks are growing more sophisticated every day. Our 5-Minute Guide to Phishing Attacks and Prevention infographic breaks down the basics of the phishing threats that users face daily as well as offering tips to prevent phishing attacks from causing trouble. MSPs: This infographic is great for social sharing and email marketing! DOWNLOAD IT>>
Did you miss… our eBook How to Use Mitre ATT&CK to Create a Smarter SOC? DOWNLOAD IT>>


Follow the path to see how Managed SOC heroically defends businesses from cyberattacks. GET INFOGRAPHIC>>




2023 Data Breaches Reached a New Record (and Why That Matters More Than Ever for Businesses)
In the ever-evolving landscape of cybersecurity, 2023 marked a significant milestone, albeit not one to celebrate. Data breaches soared to unprecedented levels, reaching a new record high that sent shockwaves through industries and individuals alike. In the 2023 Data Breach Report from the non-profit Identity Theft Research Center (ITRC), analysts reported an unprecedented surge of data breaches. As we reflect on the implications of this alarming trend, it becomes increasingly evident why it matters now more than ever for businesses and MSPs to be aware of the danger that this trend represents and the steps that can be taken to help businesses secure their data.



In The Educator’s Guide to Cybersecurity, see the cyber threats that schools face & how to mitigate them. DOWNLOAD IT>>
Data breaches are up by over 70%
In 2023, as cybercrime of all kinds experienced explosive growth, the world witnessed a staggering surge in data breaches across various sectors, including finance, healthcare, retail and government. ITRC reports that in 2023 there were 3,205 publicly reported data compromises that impacted an estimated 353,027,892 individuals. That’s a massive 72% increase in events over the previous record high of 1860 set in 2021, and 78% over 2022 – and no organization, regardless of size or industry, seemed immune to the onslaught of cyber threats.
Businesses should be deeply concerned about a new record number of data breaches due to the significant implications they pose for both their operations and reputation. Data breaches not only jeopardize sensitive information, including customer data and proprietary business secrets, but they also inflict financial losses. The erosion of consumer trust resulting from a breach can have long-lasting repercussions, leading to diminished brand loyalty and decreased revenue streams. Beyond immediate financial impacts, businesses face long-term challenges in rebuilding their credibility and implementing robust cybersecurity measures to safeguard against future breaches.
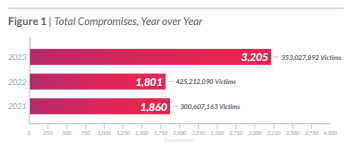

Source: ITRC 2023 Data Breach Report
Data breaches by sector saw some ups and downs (mostly ups)
In 2023’s epic cybercrime wave, especially in terms of ransomware attacks, most industries saw increases in the number of data breaches recorded. However, a lucky few saw slight decreases in the reported number of cyberattacks that resulted in data breaches. Two sectors had a particularly bad year for data breaches in 2023: Healthcare and Financial Services. Both reported more than double the total number of data breaches in 2023 that they reported the year before. Healthcare led all industries in terms of the number of reported compromises in each of the past five years, but Utilities was the sector that had the biggest estimated number of victims in 2023.
The Top 5 Industries by Number of Data Breaches Recorded in 2023
| Industry | Companies 2023 | Victims 2023 | Companies 2022 | Victims 2022 |
| Healthcare | 809 | -56M | 343 | -28M |
| Financial Services | 744 | -61M | 269 | -27M |
| Professional Services | 308 | -30M | 223 | -69M |
| Manufacturing | 259 | -5M | 249 | -24M |
| Technology | 167 | -65M | 87 | -249M |
Source: ITRC 2023 Data Breach Report


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>
Cyberattacks are at the root of most data breaches
The cybersecurity world moves fast, but some things never change. As in each of the past five (5) years, the vast majority of data compromises were linked to cyberattacks in 2023. In a rare spot of good news, phishing-related and ransomware attacks were down slightly. But malware and zero day attacks jumped significantly compared to previous years. In addition, compromises related to system and human errors more than tripled in 2023, led by a 590% increase in data being exposed in correspondence, like sending an email full of customer information to the wrong person. Breaches involving a physical action like the loss of a document, device theft or skimming devices only had a small increase, while physical breaches are down 65% since 2018.
For businesses, the consequences of data breaches are multifaceted and far-reaching. Beyond the immediate financial losses incurred from remediation efforts and regulatory fines, breaches erode consumer trust and tarnish brand reputation. In an era where customer loyalty is paramount, even a single data breach can have lasting repercussions on an organization’s bottom line. The escalating arms race between cybercriminals and cybersecurity professionals underscores the need for robust defense mechanisms and proactive risk management strategies.


Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>
Data protection regulations make keeping data safe a top priority for businesses
In response to the escalating threat landscape, governments around the world have introduced stringent regulations aimed at bolstering cybersecurity and safeguarding data privacy. Measures such as the European Union’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) impose strict requirements on organizations regarding data protection and breach notification. Noncompliance with these regulations can cost businesses a fortune and limit their ability to bounce back quickly from a data security incident.
While such regulations serve as important safeguards, their effectiveness ultimately depends on robust enforcement mechanisms and compliance efforts by businesses. Failure to adhere to these regulations not only exposes organizations to legal repercussions but also undermines the trust of consumers and stakeholders. Some businesses have chosen to not be forthcoming about their data security trouble. Researchers discovered that public companies were more likely to withhold actionable information about their data breach than other entities. Publicly traded companies withheld information about an attack in 47% of notices compared to 46 % of private companies, government agencies, education institutions and nonprofit organizations.


Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>
7 Tips for preventing a data breach
These tips can help IT professionals keep data safe.
Regular Updates and Patch Management: Keep all software, operating systems and applications up to date with the latest security patches. Vulnerabilities in outdated software are often exploited by attackers.
Employee Training and Awareness: Conduct regular cybersecurity awareness training for employees to educate them about phishing scams, social engineering tactics and other common attack vectors. Ensure they know how to recognize and report suspicious activity.
Access Control: Implement the principle of least privilege, ensuring that users only have access to the resources and data necessary for their role. Regularly review and revoke access rights for former employees or those who no longer require them.
Incident Response Plan: Develop and regularly update an incident response plan outlining the steps to take in the event of a data breach. This should include procedures for containing the breach, notifying affected parties and restoring normal operations.


What cybercriminal tricks do employees fall for in phishing simulations? Find out in this infographic. GET IT>>
Vendor and Third-Party Risk Management: Assess the security practices of third-party vendors and service providers that have access to your data. Ensure they adhere to robust cybersecurity standards and have adequate measures in place to protect your information.
Regular Security Audits and Assessments: Conduct regular security audits and assessments to identify vulnerabilities and weaknesses in your systems and processes. Address any findings promptly to mitigate potential risks.
Monitor for Suspicious Activity: Implement robust monitoring and logging systems to detect and respond to suspicious activity in real-time. This includes monitoring for unusual login attempts, file access patterns, and network traffic anomalies.


Learn about the top cyber threats K-12 schools face and how to mitigate them. DOWNLOAD INFOGRAPHIC>>
Kaseya’s Security Suite offers IT professionals the right tools for keeping data safe
Kaseya’s Security Suite has the tools that IT professionals need to mitigate cyber risk easily and affordably.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents employee mistakes and reduces a company’s risk of being hit by a cyberattack.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection around with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
Graphus — Automated email security is a cutting-edge solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
Kaseya Managed SOC powered by RocketCyber — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).
Vonahi Penetration Testing – How sturdy are your cyber defenses? Do you have dangerous vulnerabilities? Find out with vPenTest, a SaaS platform that makes getting the best network penetration test easy and affordable for internal IT teams.


See why EDR is the perfect investment to make in your future right now in our buyer’s guide. DOWNLOAD IT>>


Proactive Security: Unleash the Full Power of Network Pen Testing
February 7 | 2:00 PM EST
Discover the power of network penetration testing! We’ll show you how proactive network pen testing is critical in safeguarding sensitive data and explore the difference between pen testing and vulnerability scanning. Plus, you’ll get expert guidance on adapting to evolving threats, unleashing the power of automation and implementation best practices. REGISTER NOW>>
Emerging Cybersecurity Threats for 2024
February 13 | 1 PM ET / 10 AM PT
Join us as we explore the emerging threats SOC analysts have encountered and gain valuable insights on fortifying your defenses against cyber adversaries. Cybersecurity veteran Chris Gerritz will take you inside a SOC for a look at the daily challenges faced by SOC analysts, the threats they combat, winning remediation strategies and the dynamic world of cybersecurity. REGISTER NOW>>
February 7: Cybersecurity Jeopardy! REGISTER NOW>>
February 8: Kaseya + Datto Connect Local Dallas REGISTER NOW>>
February 20: Kaseya + Datto Connect Local Atlanta REGISTER NOW>>
February 22: Kaseya + Datto Connect Local Tampa REGISTER NOW>>
April 29 – May 2: Kaseya Connect Global (Las Vegas) REGISTER NOW>>
June 11 -13: Kaseya DattoCon Europe (Dublin) REGISTER NOW>>
October 28 – 30: Kaseya DattoCon (Miami) REGISTER NOW>>
November 12 – 14: Kaseya DattoCon APAC (Sydney) REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!