The Week in Breach News: 03/30/22 – 04/05/22

The Conti ransomware gang focuses on Shutterfly, an incident sours business at Japanese confectioner Morinaga, Anonymous continues its pressure on Russian organizations and Lapsus$ is back plus 10 key takeaways you need to see from the FBI IC3 2021 Report.

Get ready to pack your bags for Connect IT 2022! Join us June 20-23 in Las Vegas for the industry’s premier event! REGISTER NOW>>

The Partnership HealthPlan of California (PHC)
Exploit: Ransomware
The Partnership HealthPlan of California (PHC): Health Insurer

Risk to Business: 2.227 = Severe
The Hive ransomware group says that they’re responsible for a ransomware attack on The Partnership HealthPlan of California (PHC), claiming to have snatched 400 GB of data including 850,000 unique records. PHC has been experiencing computer system disruptions and the organization said that it is working to investigate and recover from the attacks with support from third-party forensic specialists. The stolen data is known to include names, Social Security numbers, and addresses of current and past PHC members.
How It Could Affect Your Customers’ Business: Healthcare data is an especially popular commodity for bad actors and incidents like this are expensive disasters for the institutions that have them.
ID Agent to the Rescue: Learn why high cyber resilience is the ticket to a safer future for your clients (plus more MRR for you) and what you can do to help them build it. GET THIS EBOOK>>
The New York City Department of Education
https://www.k12dive.com/news/data-breach-exposes-820k-new-york-city-students-information/621352/
Exploit: Supply Chain Risk
The New York City Department of Education: Government Agency



Risk to Business: 2.829 = Moderate
The New York City Department of Education has discovered that the personal information of an estimated 850,000 students was exposed in a supply chain service provider data breach in January. That incident occurred at Illuminate Education, a California-based company that provides software to track grades and attendance. An agreement that the vendor had with NYC Schools called for the data to be encrypted, but it was discovered to not have occurred at the time of the breach. The incident is under investigation by New York state officials.
Individual Impact: No information about the student data or any consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business A security failure at a supplier can lead to a headache like a data breach for any organization.
ID Agent to the Rescue: Help your clients navigate the tricky straits of third party and supply chain risk with great ways to mitigate the danger and stay safe in a dangerous world. GET EBOOK>>
United States – Shutterfly
Exploit: Ransomware
Shutterfly: Photography Retail Platform



Risk to Business: 2.735 = Moderate
Shutterfly has disclosed a data breach that exposed employee information in a ransomware attack by the Conti group. Shutterfly disclosed that its network was breached on December 3rd, 2021, and threat actors gained access to employee information. The company went on to disclose that documents stolen during the attack may have contained employees’ personal information, including names, salary and compensation information and FMLA leave or workers’ compensation claims. Shutterfly is offering two years of free credit monitoring from Equifax for those affected.
How It Could Affect Your Customers’ Business: Personal data is a hot ticket item, and big companies often have a storehouse of it in their employee records.
ID Agent to the Rescue: Cybersecurity horrors lurk around every corner, lying in wait for unwary organizations. Learn how to defeat them in our eBook Monsters of Cybersecurity. DOWNLOAD IT NOW>>


Solve five of the most exhausting remote and hybrid security problems fast with this handy infographic! DOWNLOAD IT>>


Argentina – Globant
https://thehackernews.com/2022/03/lapsus-claims-to-have-breached-it-firm.html
Exploit: Ransomware
Globant: IT and Software Development







Risk to Business: 1.969 = Severe
Cybercrime outfit Lapsus$ is back in the saddle, claiming responsibility for a successful ransomware attack against IT powerhouse Globant. The company confirmed the incident. Lapsus$ posted images that it claims are of extracted data and credentials belonging to the company’s DevOps infrastructure on its Telegram channel. They also shared a torrent file that they claims holds around 70GB of Globant’s source code as well as other data including administrator passwords associated with the firm’s Atlassian suite, including Confluence and Jira, and the Crucible code review tool. One unusual detail: Lapsus$ pointed out the fact that a number of the stolen passwords had been reused several times and were compromised before they got ahold of them, chiding the company for weak password security.
How it Could Affect Your Customers’ Business The Information Technology sector was the third most impacted sector for ransomware in 2021.
ID Agent to the Rescue: Get an in-depth look at how ransomware is evolving and who profits from it in our hit eBook Ransomware Exposed. GET THIS EBOOK>>


See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>


Germany – Nordex Group
https://www.nasdaq.com/articles/nordex-impacted-by-cyber-security-incident
Exploit: Hacking (Nation-State)
Nordex Group: Wind Turbine Manufacturer







Risk to Business: 2.017 = Severe
The Nordex Group, a major manufacturer of wind turbines, has announced that it has been experiencing systems outages since March 31, 2022, due to an unnamed cyberattack. The company claims to have detected the attack in its early stages and successfully moved to contain it, going on to say that the outage may impact employees, customers and stakeholders. This is the second hit on a German wind turbine company since the start of the Russia/Ukraine conflict and early reports say that this may be a nation-state incident.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Nation-state cybercriminals are all about infrastructure attacks, as illustrated in the run-up to the Russia/Ukraine conflict.
ID Agent to the Rescue Security and compliance training is a cost-effective defense against all types of cybercrime. Show your clients why with Security Awareness Training: Your Best Investment. GET EBOOK>>
Spain – Iberdrola
Exploit: Hacking (Nation-State)
Iberdrola: Energy Company







Risk to Business: 2.017 – Severe
Spanish power company Iberdrola has disclosed a cyberattack that exposed data for an estimated 1.3 million customers. Iberdrola said that the attack was part of a pattern of attacks on utility and infrastructure targets in Spain and Europe that are suspected to be related to the Russia/Ukraine conflict. The incident is under investigation by the National Cryptology Centre. Exposed customer data includes ID numbers, addresses, phone numbers and email addresses, but not bank account details, credit card numbers or information about the clients’ use of energy.
How it Could Affect Your Customers’ Business The US government recently warned infrastructure operators to expect a fresh wave of attacks by nation-state actors aligned with Russia.
ID Agent to the Rescue Find and slay dastardly vulnerabilities in your clients’ security strategy and emerge victorious with the Cybersecurity Monster Hunter’s Checklist! GET IT>>
Russia – Marathon Group
https://securityaffairs.co/wordpress/129713/hacktivism/anonymous-hacked-marathon-group.html
Exploit: Nation-State (Hacktivism)
Marathon Group: Investment Firm







Risk to Business: 2.176 = Severe
Anonymous announced that it has hacked into the Marathon Group, releasing 62,000 company emails (a 52GB archive) through DDoSecrets. Reports identify the Marathon Group as a Russian investment firm owned by EU-sanctioned oligarch Alexander Vinokuro, the son-in-law of Russian Foreign Minister Lavrov. The firm and its owner are suspected of financing Russian government activities.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Anonymous has been hard at work hacking assets that belong to Russia and its allies after the Collective announced it was siding with Ukraine.
ID Agent to the Rescue Ransomware is the preferred weapon of nation-state threat actors. Get tips and expert advice to guide you through securing your clients effectively in Ransomware 101. READ IT>>


Our partners typically realize ROI in 30 days or less. See why nearly 4,000 MSPs in 30 countries choose to grow with ID AGENT solutions and support. BECOME A PARTNER>>


Japan – Morinaga
Exploit: Hacking
Morinaga: Confectioner







Risk to Business: 2.176 = Severe
Candy company Morinaga has announced that it has had a data breach impacting its online store. The incident has potentially exposed the personal information of more than 1.6 million customers who bought products from the candy maker between May 1, 2018, and March 13, 2022. The company also disclosed that their initial investigation confirmed that several of their servers had been subjected to unauthorized access “and that access to some data had been locked,” although there has been no clarification as to whether or not this was a ransomware attack. The confectioner also noted that there may be minor production impacts.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Manufacturers of all kinds have been high on the cybercriminal hit list in recent months.
ID Agent to the Rescue Help your clients develop a security and compliance awareness training program by sending them the 6 Tips for Creating a Security Awareness Training Policy infographic. GET IT>>


A good security and compliance training program pays amazing dividends. Learn how to run one with our how-to guide! GET GUIDE>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a wide range of factors related to the assessed breach.


Go Inside the Ink to see how today’s biggest threats can impact your MSP and your customers in our blog.
- 3 Times Security Awareness Training Would Have Saved the Day
- Cybercrime Losses Explode, Up 48%
- Don’t Overlook Security When Offboarding Employees
- Malicious Insider Threats Are More Complex Than You Think
- The Week in Breach News: 03/23/22 – 03/29/22


Just getting started in cybersecurity? This resource bundle will help you get up to speed to protect your clients fast! GET IT>>


Fresh Resources
Do you have all of your clients’ bases covered when it comes to nation-state risks? Use this new checklist “Are You Doing These 5 Things to Protect Your Clients from Nation-State Cybercrime?” to make sure. GET CHECKLIST>>
Give These 3 Essentials to Your Clients to Solve Major Security Challenges
Help them get started with security and compliance training (provided through you of course) by giving them the NEW eBook “How to Build a Security Awareness Training Program” DOWNLOAD EBOOK>>
Show them why Dark Web ID is the perfect dark web monitoring choice with the checklist “10 Things to Look for as You Shop for a Dark Web Monitoring Solution” GET THE CHECKLIST>>
Start a conversation that will be profitable to you both with the NEW infographic “Top 5 Nation-State Cybercrime Risks for Businesses” (perfect for social sharing) GET INFOGRAPHIC>>
Did you miss this? Bolster your MRR with the tips in the webinar “Critical Components of a Profitable and Effective Security Awareness Program” WATCH NOW>>


See how cyber insurance is changing and how to protect your clients from trouble. WATCH NOW>>




10 Things MSPs Need to Know from the FBI IC3 Report
These Key Takeaways Will Help You Protect Your Customers
The yearly report on cybercrime activity from the U.S. Federal Bureau of Investigation Internet Crime Complaint Center (FBI IC3) always offers invaluable insight into how cybercrime is trending and how expensive it has grown to be. The IC3 2021 Internet Crime Report was recently released, and it offers MSPs some important clues as to what risks their clients might be facing today and tomorrow. The report also includes the kind of concrete data from a respected source that may prove beneficial for MSPs to use when starting or continuing conversations about the need for powerful, innovative solutions with their clients and prospects. These ten insights clearly show why strengthening cybersecurity should be high on every organization’s priority list.


Learn the secret to conjuring up amazing stress-free marketing campaigns in 5 Ways to Make Marketing Magic! GET IT>>
- Cybercrime losses surged by 48%
2021 was a very good year for cybercriminals, and a very bad year for everyone else who was trying to avoid falling victim to one of their schemes. IC3 received another record number of complaints in 2021. The total of 847,376 reported complaints wasn’t so much larger than the year prior, just a 7% increase from 2020. But the money total is a stunner. The total amount of loss reported hit a new record high in 2021 of $6.9 billion. That’s a whopping 48% increase over 2020’s 4.2 billion.
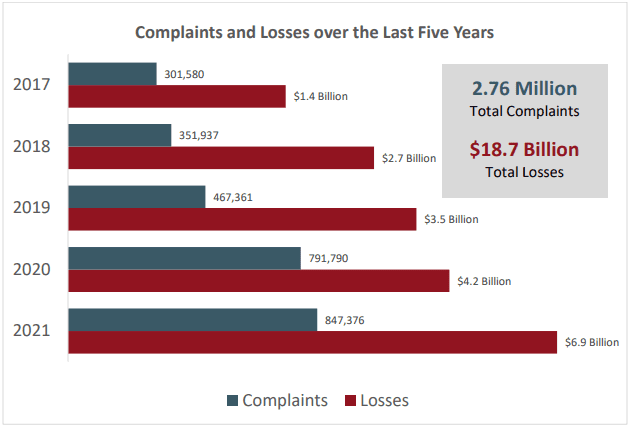

Source: FBI IC3
- BEC is still the biggest threat to a company’s profits
Business email compromise (BEC) is still the attack that costs organizations the most, and the total loss amounts for BEC reached painful new heights in 2021. While there was only a 3% growth in BEC complaints, there was 28% growth in BEC losses between 2020 and 2021. The BEC/EAC category clocked in at a painful $2,395,953,296 in losses. That’s an average loss of $120,000 per victim, compared to last year’s $96,700 per victim. Investment scams rolled in in second place, up an astonishing 333% over 2020.
- Cryptocurrency-related cybercrime has exploded onto the scene
One of the biggest stories of this report was the emergence of cryptocurrency schemes as a major security risk. In fact, they became so prevalent that they received their own focus section. In 2021, IC3 received 34,202 complaints involving the use of some type of cryptocurrency. While the actual number of complaints dropped slightly from 35,229 recorded in 2020, the total loss amount for those complaints exploded. Cryptocurrency-related losses increased nearly seven-fold, from 2020’s reported amount of $246,212,432 to a total reported loss of more than $1.6 billion in 2021.


Insider risk is swamping your clients. Learn to mitigate it quickly & profitably. WATCH WEBINAR>>
- Healthcare, Financial Services & Information Technology got walloped by ransomware
While organizations of every stripe suffered under the pressure of an unprecedented wave of ransomware attacks in 2021, a few sectors had it just a bit harder than others. Healthcare was hit with the most ransomware attacks in 2021, enduring 148. The Financial Services landscape came in second, experiencing 89 ransomware attacks in the measured period. Information technology took third place, notching 74 attacks in 2021. That put it just a bit above the next closes sectors, Critical Manufacturing and Government facilities
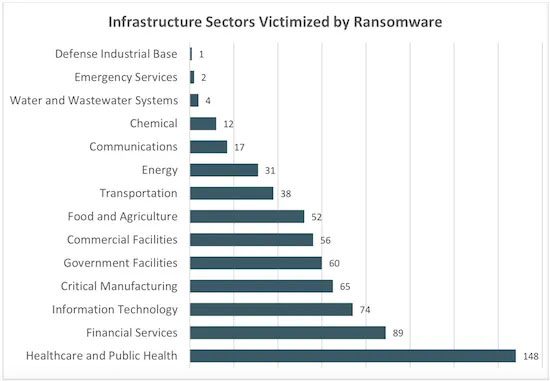

Source: FBI IC3
- 14 of 16 critical infrastructure sectors were hit with ransomware
The report noted that in June 2021, IC3 began tracking infrastructure ransomware attacks where the victim fit one of the 16 critical infrastructure categories designated by the US Cybersecurity & Infrastructure Security Agency (CISA). IC3 defines organizations that make up critical infrastructure as those whose “assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on our security, national economy, public health or safety, or any combination thereof.” In their measurement, organizations in 14 of 16 critical infrastructure sectors experienced at least one ransomware attack in 2021.
- Ransomware losses grew by 69%
Ransomware is always a big headline maker, and it’s easy to see why. Cybercriminals waged an unprecedented number of successful attacks and raked in an unprecedented amount of money from ransomware in 2021. IC3 received 3,729 complaints identified as ransomware in 2021, a 51% increase over 2020’s 2474. Those complaints also cost victims a lot more money than in previous years. Ransomware victims suffered losses of more than $49.2 million. That’s a 69% increase over the $29,157,405 recorded in 2020. The report is careful to note that its ransomware loss amount numbers do not include estimates of lost business, time, wages, files or equipment or any third party remediations sources the victim may contract.


Take a deep dive into ransomware and learn to protect your clients affordably with this resource bundle! GET IT>>
- Cybercriminals are using virtual meetings for BEC
A pandemic-era twist has emerged in BEC: schemes that leverage virtual meetings. This scheme typically starts with bad actors compromising an executive’s email, like a CEO or CFO. The bad guys then use that email to invite the victim company’s employees to participate in virtual meetings. Once the trap is set, the bad actors use a combination of impersonation, social engineering and deep fakes to get the job done. In some scenarios, cybercriminals capitalize on the unreliability of connections and software for virtual meetings, just using a photo of the executive whose account has been compromised in order to impersonate them with no video or audio, claiming they’re having technical difficulties. Sometimes the bad guys even create audio deep fakes to facilitate the scheme, with the goal of obtaining money directly or access to sensitive data.
- Cybercrime is a growth industry
Cybercrime has been on the rise for the last five years, and that trend looks set to continue. Three of the cybercrimes on the Top 5 Cybercrimes chart grew in 2021. Phishing had a solid 29% growth, rising from 241,342 in 2020 to 323,972. There were a few bright spots, including a huge drop in extortion, down 64% in 2021, dropping to 39,360 from 76,741 complaints in 2020. However, there may be other variances with reported cybercrime rates since the data reflected in this report is only from cybercrime that was formally reported to law enforcement.
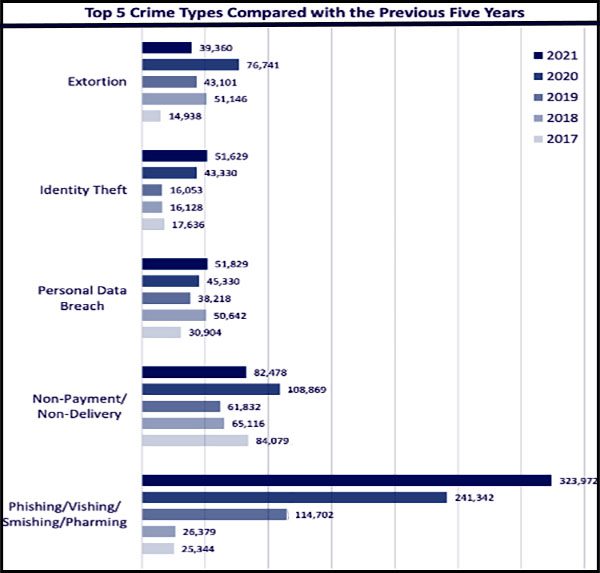

Source: FBI IC3
- Phishing and exploitation of software vulnerabilities or RDP are top ransomware causes
Phishing is still the king of ransomware risks. The report notes that ransomware attacks are growing more sophisticated saying that “phishing emails, Remote Desktop Protocol (RDP) exploitation, and exploitation of software vulnerabilities remained the top three initial infection vectors for ransomware incidents reported to the IC3”, going on to say that these vectors are expected to remain popular for cybercriminals as remote work continues. Your clients can reduce their risk of trouble by improving their protection against phishing through security awareness training and automated anti-phishing email security as well as making sure they patch regularly.
- Ransomware, phishing and BEC losses have grown every year for the last 3 years
When looking at the pattern of cybercrimes, it’s easy to see that losses have mounted in the last three years, especially for heavy hitters like ransomware. While losses for some cyberattacks like non-ransomware malware, one of last year’s biggest growth spots, have decreased, down just over 20% in 2021, others are on a solidly upward trajectory that doesn’t promise anything good for businesses.
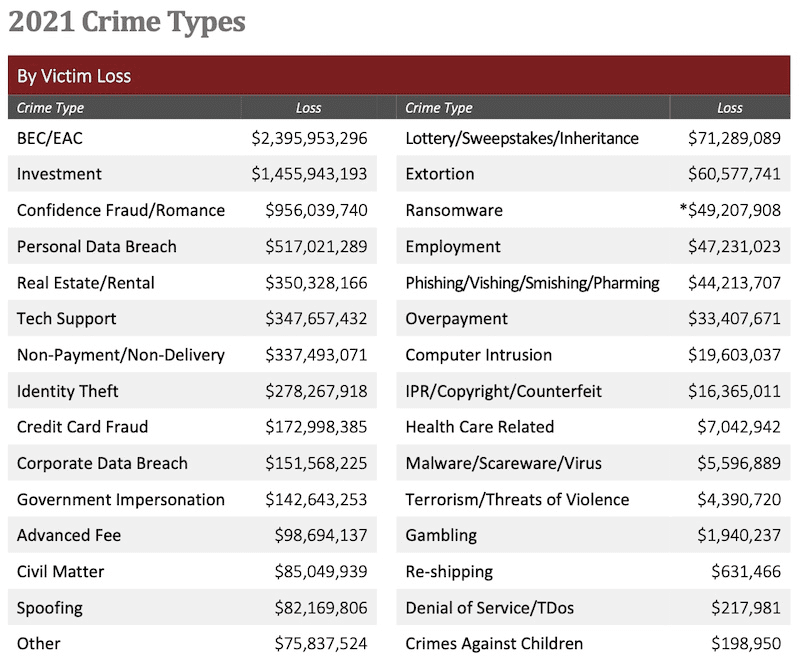

Source: FBI IC3


It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>
The ID Agent Digital Risk Protection Platform Can Keep Your Clients Safe from Risks Like These
The innovative solutions in the ID Agent digital risk protection platform provide strong security for your clients at a price you’ll both love.
Identity and Access Management
Passly packs all of the features you need to provide strong, secure identity and access management into one affordable package.
- Two-Factor Authentication (2FA) is the most powerful weapon that you can deploy against cybercrime, blocking 99% of cyberattacks on its own.
- Single sign-on makes controlling permissions, onboarding and offboarding users a breeze while also speeding incident response times
- Secure shared password vaults – Centralize password storage in one central, secure repository
Security and Compliance Awareness Training
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size with an array of training options that enable you to provide the right training for each client’s individual business needs painlessly.
- A huge library of security and compliance training videos in 8 languages – and 4 new video lessons are added a month!
- Plug-and-play or customizable phishing training campaign kits with new kits released regularly
- Easy, automated training delivery through individual user portals
Dark Web Monitoring
Dark Web ID makes it easy for you to offer your clients best-in-class protection from dark web credential compromise risk that could be a fast pass to a data breach. An estimated 60% of data breaches involved the improper use of credentials in 2021.
- 24/7/365 monitoring using real-time, analyst validated data
- Fast alerts to compromises of business and personal credentials, including domains, IP addresses and email addresses
- Channel-leading performance and innovation
Plus, partnering with ID Agent gives you access to the best sales enablement program in the industry through Kaseya Powered Services. Learn more!
Schedule your demo of Passly, Dark Web ID and BullPhish ID now.
Don’t just take our word for it, see what these MSPs have to say: https://www.idagent.com/case-studies/


See how security awareness training grows your MRR + get tips for selling it! WATCH NOW>>




Apr 06: GlueTalks: Sales & Marketing REGISTER NOW>>
Apr 07: Human Error: Are YOU the Reason for the Next Breach? REGISTER NOW>>
Apr 07: 5 Red Flags That Will Help Your Clients Identify a Malicious Insider REGISTER NOW>>
Apr 12: How Nation-State Cybercrime Affects Your Business REGISTER NOW>>
Jun 20-23 – Connect IT Global in Las Vegas REGISTER NOW>>


Cybercrime is More Expensive Than Ever Before
Cybercrime losses are up 45% according to a newly released report from the U.S. Federal Bureau of Investigation’s Internet Crime Complaint Center (FBI IC3), making 2021 the most expensive year on record for U.S. cybercrime.
That massive surge in the cost of cybercrime can be attributed to upticks in several common cyberattacks that organizations face daily including business email compromise, phishing and ransomware. These cybercrimes have been steadily growing every year for the last five years, making cybercrime a growth industry.
That’s one trend that you don’t want your company to have anything to do with. Now is the time to sit down with your MSP and review your security buildout to ensure that you’ve got the right defenses working for your organization. Any expenditure on new solutions now will be less of a hit to your budget than the response and recovery that you’ll face in the wake of a successful cyberattack could be later.


Do you have comments? Requests? News tips? Compliments? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this post (in part or in its entirety) When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!