The Week in Breach News: 06/07/23 – 06/13/23

This week: More companies fall victim to Cl0p due to the MOVEit exploit, trouble for government agencies around the world and why cyber insurance is so hard to get (and what to do about it).

Find out how Datto EDR helps with Health Insurance Portability and Accountability Act (HIPAA) compliance. GET INFO>>

Ascension Seton
https://www.kut.org/health/2023-06-07/ascension-seton-austin-hospital-data-breach
Exploit: Hacking
Ascension Seton: Healthcare System

Risk to Business: 1.886 = Severe
Austin’s Ascension Seton hospital system has announced that two of its websites have experienced a data breach. In a statement last Tuesday, the healthcare provider said that two of its legacy websites Seton.net and DellChildrens.net were breached on March 1 and 2, 2023. Both sites were operated by the technology service provider Vertex. Some users’ personal details, such as name, address, Social Security number, credit card numbers and insurance information may be at risk if they were entered through Seton.net or DellChildrens.net. Ascension Seton has replaced the hacked sites with new sites that it is hosting in-house.
How It Could Affect Your Customers’ Business: The combination of the incident on two websites plus any data loss fines will be very expensive.
Kaseya to the Rescue: Develop an effective, efficient incident response plan with the tips in our guide How to Build an Incident Response Plan. GET YOUR GUIDE>>


Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>


Canada – The Government of Nova Scotia
Exploit: Hacking
The Government of Nova Scotia: Regional Government







Risk to Business: 1.876 = Severe
The government of Nova Scotia announced last week that an estimated 100 million records containing people’s personally identifiable information were stolen in a cyberattack identified last week. A wide variety of people have been impacted including 55,000 records of past and present teachers in the province, records of 26,000 students over the age of 16 and records of 5,000 short-term housing accommodations owners, 3,800 people who applied for jobs with Nova Scotia Health, about 1,400 Nova Scotia pension recipients and 1,085 people who have been issued parking tickets in Halifax have been identified as potential victims so far. Current and past employees of Nova Scotia Health, the IWK Health Centre and the provincial civil service may also be impacted. The attack came as the result of ransomware gang Cl0p’s exploitation of the MOVEit file transfer protocol. The incident remains under investigation, with a strong possibility of more victims being uncovered.
How It Could Affect Your Customers’ Business Many exploits can be avoided by regularly patching and updating software and systems.
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET IT>>


Get the scoop on 5 of the worst email-based attacks plus tips to protect businesses from them. GET INFOGRAPHIC>>

Jamaica – The Ministry of National Security (MNS)
https://www.jamaicaobserver.com/latest-news/jamaicaeye-hit-by-cyber-attack-security-ministry/
Exploit: Hacking
The Ministry of National Security (MNS): Government Agency


Risk to Business: 2.769 = Moderate
The Ministry of National Security (MNS) disclosed that a cyberattack has affected access to the JamaicaEye website. The popular website came about as a result of the island’s National Closed-Circuit Television Surveillance Programme. Launched in 2018, citizens and business owners with cameras pointing in the public space have been able to voluntarily input their feeds into the national system. MNS has not commented on whether or not any data was stolen about camera owners who participate in the program. A team from the ministry, the Jamaica Constabulary Force and the Major Organised Crime & Anti-Corruption Agency are investigating the incident.
How It Could Affect Your Customers’ Business: There has been an increase in hacking of security and surveillance cameras.
Kaseya to the Rescue: Get more information about cybersecurity and cyber threat trends in the Kaseya Security Insights Report 2022. DOWNLOAD IT>>


Learn how managed SOC gives you big security expertise on call 24/7without the big price tag. LEARN MORE>>


South America – Argentina’s National Securities Commission (CNV)
Exploit: Ransomware
Argentina’s National Securities Commission (CNV): Government Agency







Risk to Business: 2.149 = Severe
A ransomware group named Medusa is behind the cyberattack on Argentina’s National Securities Commission (CNV). The gang has demanded $500,000 within a week, threatening to leak the purported 1.5 terabytes of the commission’s confidential records, files, documents and databases that it stole in the incident. The incident is under investigation.
How It Could Affect Your Customers’ Business: Records like these are highly desirable on the dark web because the data can be used to facilitate many cybercrimes.
Kaseya to the Rescue: BullPhish ID + Graphus together give companies powerful protection against phishing and email-based cybercrime. LEARN MORE>>


Learn about SMB attitudes toward cybersecurity and other growth opportunities for MSPs. GET INFOGRAPHIC>>


Russia – Infotel JSC
Exploit: Hacking (Nation-State)
Infotel JSC: Telecommunications Company


Risk to Business: 1.337 = Extreme
A Ukrainian hacking team known as the Cyber.Anarchy.Squad has claimed responsibility for a cyberattack that took down Russian telecom provider Infotel JSC last Thursday evening. That attack sent shockwaves through the Russian banking world. Infotel JSC is a Moscow-based provider of connectivity services between the Russian Central Bank and other Russian banks, stores and credit institutions. Reports say that multiple Russian banks were hamstrung after the attack. The telecom had admitted that the attack took place and noted that some of its network equipment was damaged in the incident. As proof of their success, the Ukrainian hackers released screenshots of a diagram of Infotel’s network and a compromised email account.
How it Could Affect Your Customers’ Business: The conflict between Russia and Ukraine has featured a flurry of hacking.
Kaseya to the Rescue: Explore how security awareness training helps organizations defend against today’s most dangerous cyber threats in this infographic. DOWNLOAD IT>>
Germany – Pflegia
https://securityaffairs.com/147227/security/pflegia-leaks-sensitive-job-seeker-info.html
Exploit: Misconfiguration
Pflegia: Healthcare Recruiter







Risk to Business: 1.826 = Severe
Researchers have identified a leaking Amazon Web Services (AWS) bucket as belonging to German Healthcare recruiting company Pflegia. The leaky cloud instance contained over 360,000 files about German job seekers. Data exposed may include a job seeker’s full name, date of birth, occupation history, home address, phone number and email address. The bucket has since been reconfigured to stop the data leak.
How it Could Affect Your Customers’ Business: Employee data handling and security mistakes can be just as costly and difficult to clean up as a cyberattack.
Kaseya to the Rescue: Security awareness training makes employees more conscientious about how their actions impact security overall. GET TRAINING TIPS>>
UK – Ofcom
https://therecord.media/ofcom-cyberattack-uk-regulator-moveit-vulnerability
Exploit: Hacking
Ofcom: Communications Regulator







Risk to Business: 1.607 = Severe
Ofcom, Britain’s communications regulator, admitted on Monday that confidential information about the companies it regulates was stolen in a cyberattack. The attack involved exploiting the MOVEit file transfer protocol by the busy cybercrime gang Cl0p. The gang claims to have hit hundreds of organizations using the exploit. Ofcom said that information about companies it regulates as well as the personal data of 412 Ofcom employees, was downloaded during the attack. The incident is under investigation.
How it Could Affect Your Customers’ Business: Intrusions like this are good sources of multiple types of valuable data for bad actors.
Kaseya to the Rescue: Learn how Datto EDR satisfies most cyber insurance requirements for endpoint protection and endpoint detection and response (EDR). GET INFORMATION>>


Learn more about how the Kaseya Security Suite helps MSPs & their customers thrive in a dangerous world. GET BRIEF>>


Australia – FIIG Securities
Exploit: Ransomware
FIIG Securities: Bond Brokerage







Risk to Business: 1.783 = Severe
A cyberattack on Australian bond broker FIIG Securities late last week was the work of the notorious cybercrime gang BlackCat. The group said that they snatched 385 gigabytes of data. FIIG Securities began contacting clients to inform them that their personal data including their names, addresses, birth dates, driver’s license information, passport scans, bank accounts and tax file numbers might have been compromised in the attack. No ransom information was available at press time. The incident has been reported to the Office of the Australian Information Commissioner.
How it Could Affect Your Customers’ Business: Te combination of financial data as well as PII makes this a profitable data score for BlackCat and an expensive nightmare for FIIG Securities.
Kaseya to the Rescue: Learn more about defending against often email-based cyberattacks like ransomware in our eBook A Comprehensive Guide to Email-Based Cyberattacks GET EBOOK>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>




Check Out The New Graphus & ID Agent Integration with Autotask
Customer billing just got easier for managed service providers (MSPs) with the new integration between Dark Web ID and Autotask PSA, an IT business management platform commonly used by MSPs. In addition to the long-standing ticketing integration between Dark Web ID and Autotask, the new billing integration feeds MSPs’ Dark Web ID client usage and licensing data into Autotask, helping partners automate customer invoice creation, save time and ensure their clients are always accurately billed for the protection they are receiving.
In addition to Dark Web ID, Autotask now has billing integrations with other Kaseya Security and Audit & Compliance products, including Graphus, Passly, RocketCyber, Network Detective Pro and Compliance Manager GRC. The integrated billing eliminates hours of back-office work at the end of the month to reconcile usage and create client invoices. DOWNLOAD THE FEATURE SHEET>>
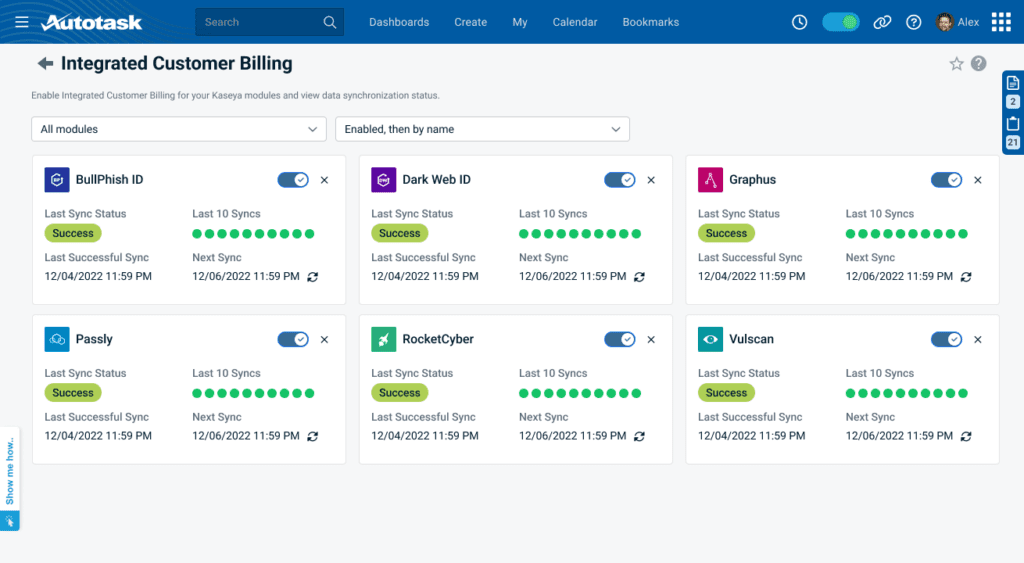

Note that you must have subscriptions to both Dark Web ID and Autotask to enable this integration. Please visit the Knowledge Base to learn how to configure this functionality.
If you’re not an Autotask customer, learn how Autotask can provide the insights needed to grow your business and the automation to increase profits by requesting a demo.


This infographic helps IT professionals get the most out of a security awareness training solution. DOWNLOAD IT>>


Datto EDR HIPAA Compliance
Learn how Datto EDR helps protect patient information and helps ensure that appropriate security measures are in place to comply with the Health Insurance Portability and Accountability Act (HIPAA) regulations in an easy-to-read two-page report. DOWNLOAD IT>>
Did you miss…The Characteristics of a Successful Security Solution checklist? DOWNLOAD IT>>






Why Is Cyber Insurance So Hard to Get and What to Do About It?
Today, organizations of all sizes find that obtaining and maintaining cyber liability coverage has become increasingly costly, complex and confusing. Premiums skyrocketed by over 50% in 2022, following 73% premium growth in the prior year. Moreover, experts predict a 25 to 100% increase in cyber insurance premiums in 2023. At the same time, the policy coverage limits are shrinking while the incident recovery costs continue to grow.
Organizations are increasingly frustrated by the stringent qualification process, with an ever-expanding amount of application paperwork and hundreds of questions to answer. Cyber insurance companies require, as part of intense underwriting scrutiny, that applicants adhere to specific cybersecurity frameworks and have controls and audits in place to assure compliance. As a result, the application and approval process is taking much longer than before.


Learn how a new integration between BullPhish ID & Graphus saves time & money. SEE THE DETAILS>>
The likelihood of a cyberattack occurring at some point makes a cyber liability policy an absolute necessity. However, the protections organizations have in place greatly influence their ability to purchase and maintain cyber insurance coverage.
Most cyber insurance policies today require having endpoint detection and response, managed detection and response (i.e., Managed SOC) and security awareness training services in place, in addition to other commercially reasonable security tools, such as antivirus and firewalls.
Because organizations need multiple security tools to qualify for cyber insurance, IT teams have to work with multiple vendors to procure all necessary solutions. Dealing with numerous bills, support teams, release schedules and other hassles of having multiple vendors results in “vendor fatigue,” wasted time and higher costs.


See why EDR is the perfect investment to make in your future right now in our buyer’s guide. DOWNLOAD IT>>
At Kaseya, we address these considerable challenges in two ways. First, we offer multiple cybersecurity solutions that cover all vulnerability areas and are technically and commercially integrated with one another. This ensures comprehensive protection, streamlines your IT operations, eliminates vendor fatigue and lowers your overall cybersecurity spend by as much as 30% compared to other vendors in the marketplace.
Kaseya, in partnership with Cysurance, now offers Cyber Insurance Fast Track, a first-of-its-kind program that provides pre-qualified cyber liability coverage for MSPs, MSP clients and businesses that utilize Kaseya’s Security stack.
The five required security solutions to qualify for the program are:
- Dark Web ID (dark web monitoring)
- BullPhish ID (security awareness training)
- Graphus or SaaS Defense (email security)
- Datto EDR (endpoint detection and response)
- Managed SOC powered by RocketCyber (managed detection and response)
Businesses that have all five products deployed for securing their environment can immediately qualify for $1.5 million in cyber coverage at prices up to 50% below the prevailing market rates through Cysurance. MSPs can immediately qualify as well.


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>
If you are already insured, the Kaseya Cyber Insurance Fast Track program can augment your existing policy by $1.5 million.
There are two ways to apply for the Fast Track program:
1. If you are a Kaseya customer enrolled in the KaseyaOne portal and already have all five required Security products, log into your KaseyaOne account, click on the Fast Track menu item on the left and complete the application form.
2. If you haven’t registered for KaseyaOne yet or need to purchase additional Security products to complete the required stack, please contact your Account Manager, who can help you obtain the portal access credentials, add any missing products from the Security stack and apply for the program.


See how Managed SOC gives businesses an essential edge against cyberattacks. DOWNLOAD INFO SHEET>>


June 14: Kaseya + Datto Connect Local Chicago Security for IT Professionals Series REGISTER NOW>>
June 15: Kaseya + Datto Connect Local Chicago Security & Compliance Track REGISTER NOW>>
June 20: Kaseya + Datto Connect Local Tampa REGISTER NOW>>
June 22: Kaseya + Datto Connect Local Atlanta REGISTER NOW>>
June 26-28: Kaseya DattoCon Europe in Dublin REGISTER NOW>>
July 11: Kaseya + Datto Connect Local Anaheim REGISTER NOW>>
July 18: Kaseya + Datto Connect Local Boston REGISTER NOW>>
July 20: Kaseya + Datto Connect Local Baltimore REGISTER NOW>>
July 21: Kaseya + Datto Connect Local Baltimore IT Professionals Series REGISTER NOW>>
August 3: Kaseya + Datto Connect Local Doral Miami REGISTER NOW>>
August 15: Kaseya + Datto Connect Local Detroit REGISTER NOW>>
August 17: Kaseya + Datto Symposium Long Branch REGISTER NOW>>
August 22: Kaseya + Datto Connect Local Kansas City REGISTER NOW>>
August 29: Kaseya + Datto Connect Local San Diego REGISTER NOW>>
September 14: Kaseya + Datto Connect Local San Antonio REGISTER NOW>>
September 21:Kaseya + Datto Connect Local Nashville REGISTER NOW>>
October 2 – 4: Kaseya DattoCon in Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!