The Week in Breach News: 08/23/23 – 08/29/23

This week: A huge data breach rocks London’s Metropolitan Police, CloudNordic takes a potentially deadly blow after ransomware encrypts all its clients’ data irretrievably and learn more about the new integration between BullPhish ID and BMS.

See what the biggest cybersecurity challenges are right now in our Mid-Year Cyber Risk Report 2023. DOWNLOAD IT>>

Ohio History Connection
Exploit: Ransomware
Ohio History Connection: Historical Society

Risk to Business: 2.276 = Moderate
The Ohio History Connection has disclosed that it fell victim to a cyberattack in late July that led to data exposure for an estimated 7,600 people. The non-profit said that names, addresses and Social Security numbers of some current and former employees from 2009 to 2023 may have been breached. Cybercriminals may have also accessed W-9 forms revealing information about vendors. The bad actors demanded an unspecified ransom, and the Ohio History Connection admitted that it made an offer, but that offer was refused, and data has begun to leak. There is an ongoing investigation by state and federal law enforcement.
How It Could Affect Your Customers’ Business: Non-profits are just as at risk for cybersecurity trouble as any other organization and they must be ready for it.
Kaseya to the Rescue: Phishing is a security risk for non-profits too. Learn about different types of phishing attacks in our eBook and get defensive tips to protect any organization. DOWNLOAD IT>>
Mom’s Meals
Exploit: Ransomware
Mom’s Meals: Meal Delivery Service

Risk to Business: 1.832 = Severe
Mom’s Meals, a medical meal delivery service for self-paying customers or people eligible for government assistance through the Medicaid and Older Americans Act programs, has announced a data breach after a successful ransomware hit. The company said that it identified suspicious activity on its networks on February 22, 2023, and determined files on its systems had been encrypted by ransomware. Interestingly, the incident stayed quiet until March 2023, when an anonymous Mom’s Meals employee tipped off an Iowa news outlet to the company’s “internet issue” that had caused the employee to miss work and pay for a week. July 10, 2023, confirming the hackers had accessed the following data: a customer’s name, date of birth, driver’s license, state identification number, financial account information, payment card information, medical record number, Medicare and Medicaid identification, health information, treatment information, diagnosis code, meal category and cost, health insurance information, patient ID number and some Social Security numbers. The company said that 1,237,681 customers have been impacted by this incident.
How It Could Affect Your Customers’ Business: Businesses that hold a variety of data can be prime targets for data thieves looking to score a quick profit.
Kaseya to the Rescue: Every company needs to be ready for trouble with an incident response plan in place to minimize downtime and speed up recovery. This checklist can help. DOWNLOAD CHECKLIST>>
University of Minnesota
https://www.fox9.com/news/university-of-minnesota-investigating-potential-data-breach
Exploit: Hacking
University of Minnesota: Institution for Higher Learning

Risk to Business: 1.673 = Severe
The University of Minnesota has admitted that it has suffered a major data breach that impacts an estimated 7 million alumni involving data going back to the 1980s. University officials said that they became aware of a possible breach after a cybercrime group claimed to have snatched data from the university in late July 2023. The unnamed hacker claimed to have stolen a database containing seven million Social Security numbers. Officials said that their preliminary investigation showed that the stolen data was collected in 2021 or earlier. The incident remains under investigation.
How It Could Affect Your Customers’ Business: Schools at every level have been under siege by bad actors hoping to score a quick ransomware payment.
Kaseya to the Rescue: Explore how security awareness training helps organizations defend against today’s most dangerous cyber threats in this infographic. DOWNLOAD IT>>


See the path from a cyberattack to a defensive success with managed SOC in this infographic. GET IT>>


United Kingdom – Metropolitan Police
https://www.bbc.com/news/uk-england-london-66631386
Exploit: Supply Chain Attack
Metropolitan Police: Law Enforcement Agency

Risk to Business: 1.310 = Extreme
London’s Metropolitan Police is facing a storm after a data breach at a contractor led to the exposure of sensitive data for an estimated 47,000 personnel. The contractor handled printing warrant cards and staff passes. A range of sensitive data was exposed, including personnel names, photographs, ranks, vetting levels and identification numbers. However, officials were quick to note that personal details like home addresses, phone numbers and financial information belonging to police personnel were not accessed. The National Crime Agency (NCA) was called in to investigate and other government agencies.
How It Could Affect Your Customers’ Business: Supply chain attacks are escalating, and just one attack on a supplier can be a big problem that brings big bills for any organization.
Kaseya to the Rescue: See how the solutions in Kaseya’s Security Suite help IT professionals minimize risk, avoid cyberattacks and build a cyber-savvy workforce. WATCH THE WEBINAR>>
France – Pôle emploi
Exploit: Supply Chain Attack
Pôle emploi: Government Agency




Risk to Business: 1.673 = Severe
France’s unemployment registration and financial aid agency Pôle emploi has announced that it had experienced a data breach thanks to a service provider being caught up in the ongoing MOVEit exploit spree. An estimated 10 million people had personal information exposed in this incident, the second largest single incident population so far in the MOVEit saga. The exposed data includes a citizen’s full name and social security number. The agency said that email addresses, phone numbers, passwords, and banking data were not compromised.
How it Could Affect Your Customers’ Business: Governments of every size and government agencies have been high on cybercriminal hit lists.
Kaseya to the Rescue: Our eBook How to Build a Security Awareness Training Program helps IT professionals design and implement an effective training program quickly. DOWNLOAD IT>>
Denmark – CloudNordic
Exploit: Ransomware
CloudNordic: Cloud Hosting Company



Risk to Business: 1.012 = Extreme
Danish cloud hosting company CloudNordic is facing an existential crisis after an August 18 ransomware attack wiped out all of its clients’ stored data. Its sister cloud host, AzeroCloud is also in the same boat. CouldNordic said that widespread encryption has resulted in client data becoming inaccessible. The attackers hacked into network-linked cloud servers used by both companies during a migration to another data center. This enabled the hackers to gain wide access to backup systems and entire data storage silos, leading to near-complete encryption. The hackers have demanded a ransom of approximately $150,000.
How it Could Affect Your Customers’ Business: One successful ransomware attack can be enough to deal a company a blow that they may not be able to recover from.
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET THE FACT SHEET>>


Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>


Australia – Pareto Phone
Exploit: Hacking
Pareto Phone: Telemarketing Firm



Risk to Business: 1.302 = Extreme
Many charities that used Pareto Phone for some of their fundraising efforts are finding out that their donors may have had data exposed after the company admitted to a data breach. Some of the charities impacted include The Cancer Council, Canteen, Australian Conservation Foundation and Fred Hollows Foundation. Some of the charities are saying that Pareto retained their donors’ information without their knowledge, including information that was up to nine years old. That donor information has now been released on the dark web. Canteen said that its donors’ full names, date of birth, addresses, email addresses and phone numbers had been released, but not financial information. More than 70 charities may have been impacted in the incident.
How it Could Affect Your Customers’ Business: This expensive disaster will be even worse if the company has improperly held or failed to destroy data as required by Australia’s privacy rules.
Kaseya to the Rescue: Follow the path to see how Managed SOC defends businesses from cyberattacks efficiently and effectively without breaking the bank in a handy infographic. GET IT>>


What cybercriminal tricks do employees fall for in phishing simulations? Find out in this infographic. GET IT>>


Japan – Seiko
Exploit: Ransomware
Seiko: Watchmaker




Risk to Business: 1.682 = Severe
The BlackCat/ALPHV ransomware gang has claimed responsibility for a ransomware attack on renowned Japanese watchmaker Seiko. The company disclosed on August 10 that an unauthorized party had gained access to its network. BlackCat has begun posting samples of the stolen data including production plans, employee passport scans, new model release plans, specialized lab test results, technical schematics and Seiko watch designs. Seiko said that it has commissioned a team of external cybersecurity experts to investigate the incident and apologized to its customers.
How it Could Affect Your Customers’ Business: Bad actors aren’t just looking for personal or financial data, they’re happy to steal a company’s intellectual property and research data too.
Kaseya to the Rescue: Learn the basics about different types of ransomware attacks and follow the path of a ransomware attack in our eBook Ransomware 101. DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>




BullPhish ID Billing Integration with Kaseya BMS Saves Time, Streamlines MSP Billing
Customer billing just got easier for managed service providers (MSPs) with the new BullPhish ID integration with Kaseya BMS PSAs — an IT business management platform commonly used by MSPs.The new billing integrations feeds MSPs’ BullPhish ID client usage and licensing data into the PSAs, helping partners automate customer invoice creation, save time and ensure their clients are always accurately billed for the security awareness training and phishing simulation services they receive. LEARN MORE>>



How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


Two resources to help you ensure business continuity
Every business needs to be prepared for a ransomware attack. Datto EDR now includes a Ransomware Rollback feature that helps businesses get back to work faster by returning them to the state they were in before the attack. Learn more from these two resources.
- How Datto EDR with Ransomware Rollback Helps You Recover Fast from a Ransomware Attack Infographic GET IT>>
- Ransomware Rollback Feature Sheet DOWNLOAD IT>>
Did you miss… our How Managed SOC Defends Against Cyberattacks infographic? DOWNLOAD IT>>



Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>




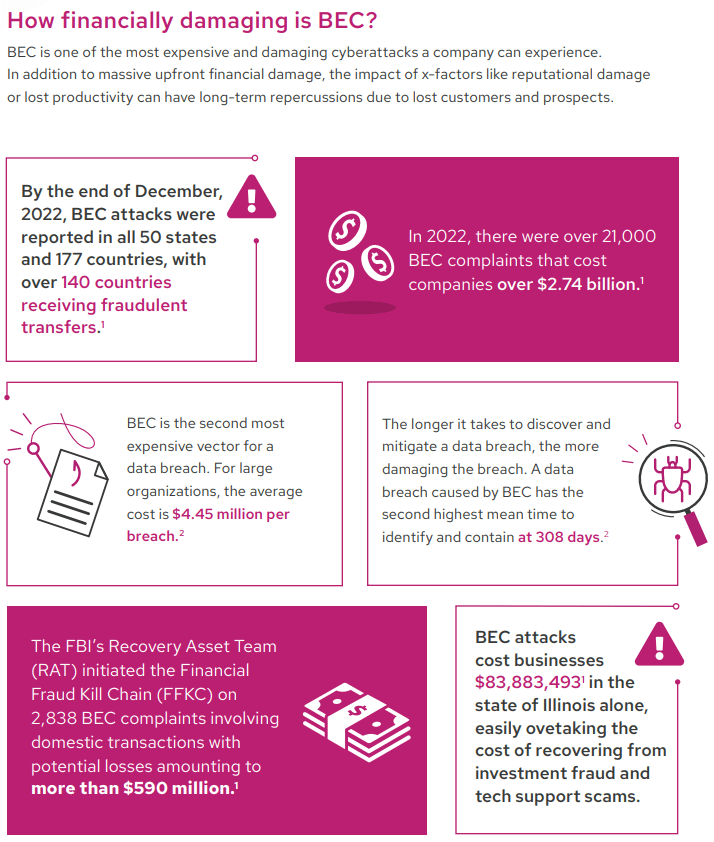
5 BEC Scenarios Businesses Need to Be Ready For
What’s the biggest cyberthreat that businesses face? It isn’t ransomware, even though it tends to grab all of the headlines. It’s a business email compromise (BEC). Sometimes called email account compromise (EAC), BEC can lead to potentially devastating business losses. Unfortunately, BEC’s chameleon-like nature makes it tricky for most victims to spot. These types of attacks can quickly inflict massive damage on a company’s revenue, reputation and productivity, making it a serious problem. This look inside the complicated world of BEC will help you develop and maintain a strong defensive posture against today’s most expensive cyberthreat.
Excerpted in part from the 2023 edition of The Comprehensive Guide to Avoiding Business Email Compromise DOWNLOAD IT>>
What is BEC?
Business email compromise (BEC) is a cyberattack that cybercriminals use to utilize seemingly legitimate (or freshly stolen) email accounts from one organization to fraudulently trick employees of another business into giving them credentials, money, personal information, financial details, payments, credit card numbers or other sensitive data. BEC attacks rose by 84% per inbox in 2022.

Source: Kaseya


Learn how Datto EDR satisfies cyber insurance requirements for endpoint protection & EDR. DOWNLOAD REPORT>>
BEC attack scenarios
BEC is a slippery foe because it can take so many forms. The following scenarios will show you what the most common types of BEC attacks look like in action, along with examples of what happened to unlucky organizations that fell victim to these attacks.
Urgent payment required or invoice scams
The most common variety of BEC attack is the invoice or urgent payment required scam. In this scenario, bad actors pose as representatives of a company or government agency and tell the victim that an invoice must be paid immediately to avoid a negative consequence, like the interruption of their phone service. Usually, they ask for a wire transfer to a fraudulent bank account, but sometimes bad actors will request payment via a gift or money card.
According to Forbes’s recent Financial Professional Census, the estimated cost of invoice scams to mid-sized enterprises tallies around $280,000 every year. Bad actors begin by infiltrating an organization’s network as illegitimate vendors and presenting invoices for fairly negligible amounts that don’t raise any alarms. By repeating the process over and over again, cybercriminals are able to scam the business for hefty amounts.
Cautionary tale
Both Facebook and Google fell victim to invoice scams perpetrated by the same cybercriminals that resulted in around $121 million in collective losses. Lithuanian national Evaldas Rimasauskas and associates formed a fake company that used the name of a real hardware supplier, “Quanta Computer.” The group then presented Facebook and Google with fraudulent invoices, which they promptly paid — straight into bank accounts controlled by the bad guys.


Get the scoop on 5 of the worst email-based attacks plus tips to protect businesses from them. GET INFOGRAPHIC>>
Executive impersonation scams
Bad actors may pose as an executive at the victim’s company or another organization to entice the victim into downloading a malicious document, sending them money, providing them with sensitive information like financial data or helping them access restricted systems and data.
Cautionary tales
- At toy manufacturer Mattel, cybercriminals posing as executives of a Chinese company duped an executive into approving a $3 million offshore payment to their fake firm in China. The executive soon found out that the Chinese firm didn’t exist, and that they had transferred that money to cybercriminals.
- Pathé, a French cinema company, experienced a BEC attack in which cybercriminals impersonated the company’s CEO. Bad actors misrepresented themselves to the executives in the company’s Dutch division using an email address similar to the company’s legitimate domain pathe.com. The fraudsters convinced executives to transfer funds to a “new” (fraudulent) bank account to pay for the supposed takeover of a company in Dubai, ending in a loss of $21 million.


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>
Misrepresentation scams
In a misrepresentation scenario, bad actors target employees in certain departments with the intent to trick them into providing sensitive information or payments. They may pose as government officials or even executives and colleagues within the target’s organization.
Cautionary tales
- The charity Save the Children lost $1 million to BEC. In that scam, the attacker managed to gain access to an employee’s email account and then used it to send fake invoices and other documents to the charity’s accounting department claiming that the money was needed to pay for non-existent solar panels for a clinic in Pakistan. The accounting department didn’t suspect anything because the invoices came from a trusted address.
- In an incident at Snapchat, bad actors contacted a privileged employee in the company’s human resources department. By pretending to be the CEO requesting information for a routine business purpose, cybercriminals were able to trick the employee into sending them sensitive financial data, including payroll details for current and former employees.
- Security researchers report that a fairly new cybercriminal gang specializing in launching BEC attacks has been active since 2021. So far, the group has run around 350 BEC campaigns, where over 100 multinational corporations became victims. The gang would first contact targets as an important executive, generally the CEO, and explain that their organization is secretly acquiring another business. However, to complete the merger, an initial payment would be required. Once hooked, the gang would then contact targets as an external entity, like an attorney or Mergers & Acquisitions professional, to validate the legitimacy of the payment. It may sound simple, but the scam has helped the group make hundreds of thousands of dollars.



How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>
Gift card scams
Urgency is a hallmark of BEC gift card scams. Bad actors scare their victims, for example, by telling them that their company’s electricity will be cut off for non-payment unless they pay their bill by gift card immediately. The U.S. Federal Trade Commission provides several examples of gift card scam scenarios that they’ve encountered.
Cautionary tales
- The target receives an email purporting to be from a government agency, often the U.S. Internal Revenue Service or the Social Security Administration. They claim that the victim or the victim’s company must pay taxes or a fine and will face dire consequences if it isn’t paid immediately. A cybercriminal sends a message pretending to be from Apple or Microsoft tech support, saying there’s something wrong with the company’s systems or services and the victim must pay to have it fixed.
- In a common, scary gift card scam, bad actors falsely represent themselves as representatives of a utility like a power company, threatening to cut off service if the victim doesn’t pay immediately. Cybercriminals pretend to be customers who claim they’ve sent an incorrect payment and are owed money, sometimes threatening legal action if the “overpayment” isn’t returned quickly.



Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>
Credential or information fraud
A credential compromise BEC scam starts with bad actors asking the victim to provide credentials on the pretense that they’ve misplaced credentials they’d already been given or weren’t given the right ones to complete a task. Both variants lead to the same result — a bad actor tricks an employee into giving them access to systems, accounts and data that they shouldn’t have.
Cautionary tale
Twitter fell victim to a BEC attack. In this incident, bad actors pretending to be repair contractors contacted Twitter employees. They convinced a Twitter employee that there had been a mix-up, and they hadn’t received the right credentials to access a system that required repairs. After obtaining access credentials from the gullible employee, cybercriminals were able to take over accounts belonging to celebrities, including Donald Trump and Elon Musk, and use them for nefarious purposes.


This infographic helps IT professionals get the most out of a security awareness training solution. DOWNLOAD IT>>
Kaseya’s Security Suite Offers IT Professionals the Tools for Security Success
Get powerful protection and must-have tools for keeping businesses out of cybersecurity trouble with Kaseya’s Security Suite.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents employee mistakes and reduces a company’s risk of being hit by a cyberattack.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection around with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
Graphus — Automated email security is a cutting-edge solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
Kaseya Managed SOC powered by RocketCyber — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).


See how Managed SOC gives businesses an essential edge against cyberattacks. DOWNLOAD INFO SHEET>>


Must-have Security Tools For 2023 And Beyond
Rapid-fire Demos of the Kaseya Security Suite
Wednesday, September 13th |1 pm ET / 10 am PT
To actively combat the ever-advancing threat landscape of 2023 and beyond, you must consistently reimagine cybersecurity. It sounds like quite the challenge. Well, with the right tools, it doesn’t have to be. Join our cybersecurity experts on September 13 at 1 PM ET / 10 AM PT to learn how our innovative cybersecurity products — Graphus, Dark Web ID, BullPhish ID and Managed SOC — elevate your cybersecurity practices to the next level and protect you from some of the most advanced cyberattacks till date. Register today and discover how you can significantly bolster your IT security. REGISTER NOW>>
August 31: Kaseya + Datto Connect Local Sweden REGISTER NOW>>
September 7: Kaseya + Datto Connect Local Netherlands REGISTER NOW>>
September 14: Kaseya + Datto Connect Local San Antonio REGISTER NOW>>
September 21: Kaseya + Datto Connect Local Nashville “Building the Business” Series REGISTER NOW>>
September 26: Kaseya + Datto Connect Local Sugarland Sales & Marketing Series REGISTER NOW>>
September 28: Kaseya + Datto Connect Local Charlotte REGISTER NOW>>
October 2 – 4: Kaseya DattoCon in Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!