Who Are Today’s Dark Web Users?

Explore the demographics of the dark web
The dark web is a bustling place, and many people from many walks of life utilize it every day. Some people do use the dark web for legitimate purposes, like journalists in countries with strict censorship laws, government and military agencies or cybersecurity researchers. Only approximately 6.7% of global users use the dark web for illicit activities such as sharing malware, distributing child abuse content, or selling illegal substances or weapons. Of course, many regular users of the dark web are selling dangerous, stolen or illegal items and many are also engaged in cybercrime. Learning more about who is using the dark web can help security professionals better defend businesses against dark web threats.
Excerpted in part from our eBook The IT Professional’s Guide to the Dark Web DOWNLOAD IT>>
What does the dark web look like these days?
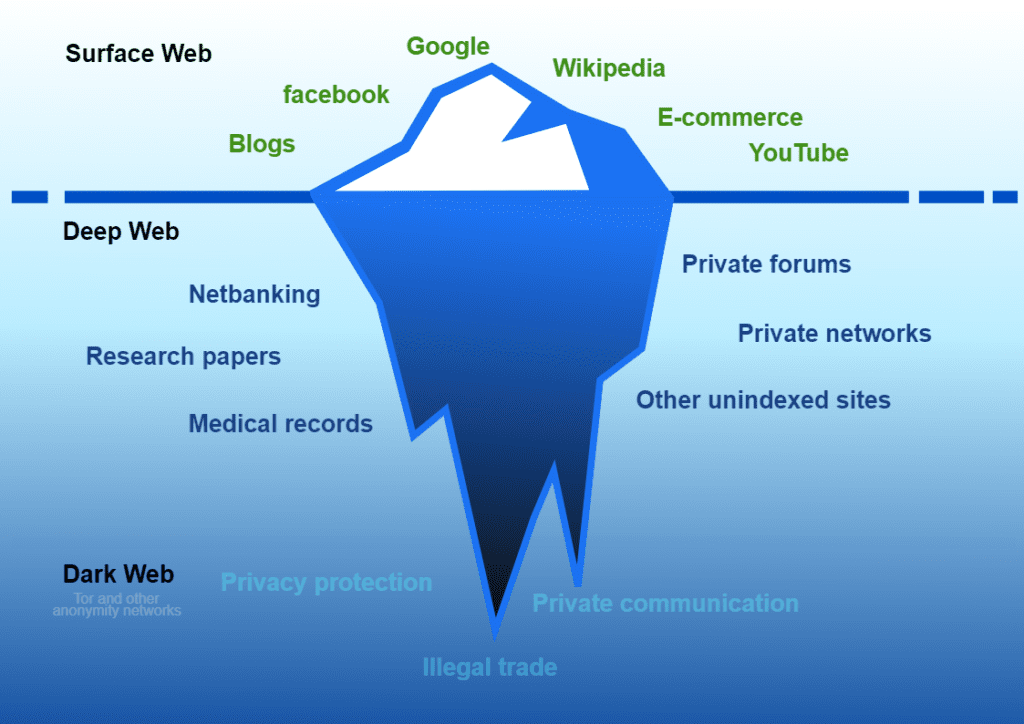
The internet as we know it has three distinct layers, and the dark web is by far the smallest. the
The surface web is what most of us access in our regular, day-to-day activity. It is available to the general public using standard search engines. The shopping sites, social media platforms, streaming services, news organizations and other websites people commonly visit are on the surface web. It can be accessed using standard web browsers that do not require any special configuration, such as Mozilla Firefox, Microsoft Edge and Google Chrome. The surface web seems vast, but it is in fact just about 4% of the overall web.
The deep web is the largest portion of the web. It is not indexed or searchable by ordinary search engines. A specific URL or IP address is required to access these websites or services. Some sites are part of the deep web because they block search engines from identifying them or do not use common top-level domains (TLD). Sites on the deep web are often used to store data and content stored in databases that support services like social media sites, insurance companies or banks. The deep web is 400 to 500 times the size of the surface web.
The dark web is a less accessible subset of the deep web that relies on peer-to-peer connections. Specialized software or tools are required to access the dark web. The Tor browser is the most widely used method of accessing the dark web, but other communications platforms like Signal can also be used. The dark web percentage in the total space of the deep web is approximately 0.01%.
Source: Wikimedia Commons

Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>
What are the most popular ways for dark web users to log on?
Over two million users access the Tor platform daily. While many of them use it for legitimate purposes, like getting around censorship, for example, many others use Tor for nefarious purposes. One-quarter of the world’s population has used the Tor browser to connect to the dark web at some point. Tor users connect to the dark web in two ways:
Bridge: A bridge is a private server in the Tor network that can provide access for blocked clients, often in combination with pluggable transports, that registers itself with the bridge authority. This method of connection is often chosen in countries that regulate or suppress internet access. The three countries from which users most frequently connect to Tor this way are Iran, Russia and the United States.
Relay: A relay is a publicly listed server in the Tor network that forwards traffic on behalf of clients and registers itself with the directory authorities. This is the most common way for someone to connect to Tor.

Get tips & advice to help you build a smart incident response plan in our guide. GET YOUR GUIDE>>
Dark Web Demographics
So, who uses the dark web regularly? While data is limited about dark web users thanks to the anonymity using the dark web brings, we can look at a little data pulled from studies and the demographics provided by the Tor Project website. In a recent survey of dark web users, researchers determined that 84.7% of dark web users identified as male, and only 9.4% of the users surveyed identified as female. In the same study, researchers determined that as many as 23.5% of dark web users were 36–45 years old, 11.8% were 18–25 years old with 5.9% (only one subject) were 46–55 years old.
These 10 countries have the most users connecting through Tor daily via relay.
| Country | Mean daily users |
| United States | 467,982(19.69 %) |
| Germany | 283,997(11.95 %) |
| India | 102,554(4.32 %) |
| Indonesia | 92,715(3.90 %) |
| France | 91,667(3.86 %) |
| Russia | 89,891(3.78 %) |
| Finland | 85,092(3.58 %) |
| Netherlands | 69,416(2.92 %) |
| United Kingdom | 61,458(2.59 %) |
| Egypt | 50,612(2.13 %) |
Source: TOR Metrics

See how security awareness training stops the biggest security threats! GET INFOGRAPHIC>>
Who are the major cybercrime players on the dark web?
The dark web is constantly evolving and growing, as is the technology that powers the wide variety of cyberattacks that emanate from the dark web. An estimated 30,000 hidden websites exist on the dark web. Cybercrime and its related industries is a booming sector and unlike many of the world’s economies, the dark web economy is strong and growing. All sorts of nefarious characters are dark web users, and a wide array of shady goods and services are sold on dark web sites, exchanged on dark web forums, peddled in the marketplaces or deposited in data dumps.
Here are some of the major cybercrime players on the dark web.
- Hackers of all sorts retailing their goods and services
- Malicious employees of companies dealing in passwords or information
- Initial access brokers selling access to compromised networks
- Specialists offering Cybercrime-as-a-Service (CaaS) including Ransomware-as-a-Service (RaaS) and Phishing-as-a-Service (PhaaS) practitioners.
- Cybercrime gangs, like ransomware groups, recruiting affiliates to join their crime network and conduct cyberattacks
- Hacktivists, like Anonymous, releasing data obtained from organizations or governments that they oppose politically or morally
- Nation-state threat actors and advanced persistent threat (APT) groups conducting operations that fund their activities or harm other nations.

Learn how a new integration between BullPhish ID & Graphus saves time & money. SEE THE DETAILS>>
How can I protect my organization from dark web threats?
It pays for businesses to take smart precautions against dark web threats. Fortunately, mitigating dark web risk is easy and affordable thanks to dark web monitoring. It’s an essential part of any organization’s defensive strategy because it enables IT teams to find out about their users’ compromised credentials quickly (before dark web users who are cybercriminals do). With dark web threat intelligence, IT professionals gain an edge against dark web exposure threats that helps them act to protect the organization immediately, reducing its chance of a cyberattack. A dark web monitoring solution can keep an eye on credentials in a variety of configurations that can typically be customized to fit your organization’s needs.
Common types of credentials that can be monitored include:
- Employee credentials
- Privileged user credentials
- Personal credentials
- Domains
- IP addresses
- Sensitive personal email addresses of executives
- Privileged users’ email addresses

Get 10 tips to help you build a strong security culture & reduce your risk of cybersecurity trouble! GET INFOGRAPHIC>>
Dark web monitoring is easy and affordable with Dark Web ID
Dark web monitoring helps companies ensure that there aren’t any nasty surprises waiting for them because of dark web data exposure. Dark Web ID offers best-in-class dark web intelligence, about compromises of business and personal credentials, including domains, IP addresses and email addresses delving into every corner of the dark web, including:
- Hidden chat rooms
- Unindexed sites
- Private websites
- P2P (peer-to-peer) networks
- IRC (internet relay chat) channels
- Social media platforms
- Black market sites
- 640,000+ botnets
- 24/7/365 monitoring using real-time, machine- and analyst-validated data.
- Live dark web searches that find compromised credentials in seconds.
- Clear and visually engaging risk reports.
- Enjoy seamless integration with popular PSA platforms, including Kaseya BMS, Autotask and ConnectWise.
- Easy integration with your security operations center (SOC) and other alerting and remediation platforms with available APIs.
Schedule a demo of Dark Web ID>>

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!