The Week in Breach News: 05/17/23 – 05/23/23

This week: Ransomware snarls operations at two tech companies, a bank in Indonesia gets caught trying to gloss over a ransomware attack, a big breach at a medical debt collector and a look at the over 30% rise in business email compromise attacks.

Learn how Datto EDR satisfies cyber insurance requirements for endpoint protection & EDR. DOWNLOAD REPORT>>

Credit Control Corporation
https://www.hackread.com/credit-control-corporation-data-breach/
Exploit: Hacking
Credit Control Corporation: Debt Collector

Risk to Business: 1.281 = Extreme
Credit Control Corporation (CCC), a Virginia-based debt collection company that primarily handles medical debt, has admitted that it suffered a data breach in March 2023 that resulted in the exposure of personal information for 286,699 people. The company told the Maine Attorney General’s Office that an unauthorized party gained access to its network between March 2 and March 7, 2023, and illegally copied some files. The unauthorized party stole data including consumers’ names, addresses, and Social Security numbers as well as data related to the individual’s accounts with CCC business partners, such as account numbers, account balances and dates of service. CCC says it is working with law enforcement to resolve the investigation.
How It Could Affect Your Customers’ Business: This will be an expensive nightmare for CCC to endure with the combination of medical and financial data stolen.
Kaseya to the Rescue: Data is a commodity on the dark web. Learn more about the dark web risks that businesses face in The IT Professional’s Guide to the Dark Web. DOWNLOAD IT>>
ScanSource
Exploit: Ransomware
ScanSource: Technology Company



Risk to Business: 1.592 = Severe
U.S.-based SaaS connectivity and network communications provider ScanSource says that it has been the victim of a ransomware attack that has impacted its systems, business operations and customer-facing portals. ScanSource confirmed that the attack hit on May 14, taking down customer portals and websites. The company warns that there will be delays in the provision of services to customers in North America and Brazil. ScanSource also said that it has enlisted the help of a third-party forensics firm and law enforcement in its investigation. No group had claimed responsibility at press time.
How It Could Affect Your Customers’ Business: Technology companies are often service providers, making them attractive targets that can offer both profit and access to other businesses.
Kaseya to the Rescue: Learn more about defending against often email-based cyberattacks like ransomware in our eBook A Comprehensive Guide to Email-Based Cyberattacks GET EBOOK>>
The Illinois Department of Healthcare and Family Services (HFS)
Exploit: Hacking
The Illinois Department of Healthcare and Family Services (HFS): Regional Government Agency





Risk to Business: 2.769 = Moderate
The Illinois Department of Healthcare and Family Services (HFS) has disclosed that it has experienced a data breach that has exposed data for residents. HFS said that the data breach occurred in the State of Illinois Application for Benefits Eligibility (ABE) system’s Manage My Case (MMC) portal, a system also used by the Illinois Department of Human Services (IDHS). The ABE system is used to determine the eligibility of applicants for medical and poverty relief programs including Medicaid, the Supplemental Nutrition Assistance Program (SNAP) and Temporary Assistance for Needy Families (TANF). The agency said that the exposed data includes names, social security numbers, recipient identification numbers, addresses, phone numbers and income information for program applicants.
How It Could Affect Your Customers’ Business: Hackers favor government agencies and systems because they tend to hold a wide variety of data in large quantities.
Kaseya to the Rescue: Develop an effective, efficient incident response plan with the tips in our guide How to Build an Incident Response Plan. GET YOUR GUIDE>>
Uintah Basin Healthcare
https://www.bankinfosecurity.com/uintah-basin-healthcare-data-breach-affects-over-100000-a-22066
Exploit: Hacking
Uintah Basin Healthcare: Health System



Risk to Business: 1.719 = Severe
Utah’s Uintah Basin Healthcare has disclosed that a data breach has led to the exposure of data for some 100,000 patients who have been treated within the system in the last 10 years. Uintah Basin Healthcare began notifying patients last week that it experienced unusual activity on its network in November 2022 that resulted in data exposure for 103,974 patients treated between March 2012 and November 2022. The rural health system said that the stolen data includes clinical information, diagnoses, medications and test results.
How It Could Affect Your Customers’ Business: This will be a punishingly expensive problem for this small rural health system to handle.
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET IT>>


Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>


France – La Malle Postale
Exploit: Misconfiguration
La Malle Postale: Transportation Service





Risk to Business: 2.781 = Moderate
A data leak on La Malle Postale’s system has exposed the personal data of an estimated 90K of their clients. A research team reported uncovering a publicly accessible database with more than 4GB of personal data belonging to the company’s clients, including more than 13,000 SMS messages sent between the company and its customers. The leaked personal data included the names, emails and phone numbers of nearly 90K customers along with lightly secured passwords and employee credentials. The company appears to have since secured the data.
How it Could Affect Your Customers’ Business: Failure to properly secure data can be just as costly to handle as having data stolen.
Kaseya to the Rescue: Explore how security awareness training helps businesses defend against today’s most dangerous cyber threats in this infographic. DOWNLOAD IT>>
France – Lacroix
https://www.infosecurity-magazine.com/news/lacroix-shuts-three-factories-week/
Exploit: Ransomware
Lacroix: Electronics Manufacturer





Risk to Business: 2.866 = Moderate
French electronics manufacturer Lacroix said that it has experienced a cyber-attack on its operations at sites in France, Germany and Tunisia. The company said that it was forced to temporarily shut down several online systems to contain the attack and assess the damage. Lacroix said that it is implementing backups and conducting analysis to identify any exfiltrated data. Based on reports of the attack encrypting some local infrastructure at Lacroix’s sites along with data exfiltration, experts say this is likely a ransomware attack. Lacroix is expected to resume full operations at the shut down sites this week and the company said that it does not anticipate any significant impact on the overall performance projected for the group in 2023.
How it Could Affect Your Customers’ Business: Manufacturers are prime targets for ransomware because of the time-sensitive nature of their business.
Kaseya to the Rescue: Email is the most likely way for employees to encounter cyberattacks like ransomware. This checklist helps companies strengthen their email security. GET CHECKLIST>>
Latvia – airBaltic
Exploit: Internal Error
airBaltic: Airline





Risk to Business: 1.883 = Severe
Latvia’s airBaltic has begun informing customers that they may have had personal data exposed after an internal error led to some customers being sent other customers’ flight information erroneously. The airline said that only “a small number” of customers had data exposed. That exposed information may have included the passengers’ full names, birth dates, itinerary and email addresses. airBaltic was quick to reassure customers that no financial or payment data was involved. However, the PNR/reservation number for the impacted passengers was exposed and that could allow the recipient to make changes to the itinerary. The airline said that it will change the number for any customer who requests it.
How it Could Affect Your Customers’ Business: A mistake like this doesn’t look good to customers who are concerned about the security of their personal data.
Kaseya to the Rescue: These 10 tips can help you implement an effective security awareness training program that reduces the chance of employee data handling mistakes. GET TIPS>>


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>


Indonesia – Bank Syariah Indonesia
https://www.bankinfosecurity.com/lockbit-leaks-15tb-data-stolen-from-indonesias-bsi-bank-a-22110
Exploit: Ransomware
Bank Syariah Indonesia: Bank



Risk to Business: 1.386 = Extreme
The LockBit ransomware group has published 1.5TB of data that it claims to have snatched from Indonesia’s largest Islamic bank, Bank Syariah Indonesia. The published records include the personal and financial information of about 15 million of the state-owned bank’s customers and employees. Up until now, the bank had claimed that widespread service outages in the last few weeks were the result of maintenance, but it was forced to admit that the problems were actually the result of a cyberattack. Bank Indonesia, the country’s central bank, said last Thursday that it had helped Bank Syariah Indonesia restore its real-time gross settlement, national clearing system and Bank Indonesia Fast Payment services. ATMs and bank branch services became available last week. Screenshots of ransom negotiations released by LockBit show that the bank dangled the possibility that it would pay the gang $10 million to recover its stolen data, but LockBit demanded $20 million before the negotiations broke off.
How it Could Affect Your Customers’ Business: The financial services sector has been the hardest hit by ransomware gangs in the last few years.
Kaseya to the Rescue: This infographic can help businesses and MSPs create a comprehensive security awareness training policy that supports a strong training program. GET INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>




The New Powered Services Pro Campaign Explains AI to Your Clients
Get the tools to explain the basics of AI and how it can benefit their business (and their security) to your customers in a new Powered Services Pro Campaign.
AI: Artificial Intelligence – What It Is & Why It Matters
MSP Value Proposition:
There’s a lot of buzz and opinions around artificial intelligence, but one thing’s for sure: it’s not going away anytime soon. Help clients and prospects understand the basics of AI, including common business applications, key considerations and potential implications, so they can make informed decisions for their organization.
End Buyer Value Proposition:
As artificial intelligence becomes more mainstream and widespread, organizations of all sizes continue to find innovative, meaningful, and cost-effective ways to incorporate AI and improve business operations and efficiencies.
Log into your Powered Services Pro account to get this campaign!


This infographic helps IT professionals get the most out of a security awareness training solution. DOWNLOAD IT>>


Meet Your New Secret Weapon: EDR + Managed SOC
Are you taking advantage of the amazing benefits you get when you combine Managed SOC with Datto EDR? Each of these technologies is great on its own, but when you combine them, you gain an unbeatable advantage against cyberattacks.
Get our 2-page explainer that shows you exactly why EDR + Managed SOC is a winning combination. DOWNLOAD IT>>
Did you miss…the 5 Reasons Why You Should Offer Managed SOC Services infographic? DOWNLOAD IT>>






Business Email Compromise Attacks Are Up by 38%
Business email compromise (BEC) is the most dangerous and damaging cyberattack businesses face. This potentially devastating attack can quickly cause massive financial and reputational damage to a business. Unfortunately, BEC’s chameleon-like nature makes it tricky for most victims to spot, and cybercriminals are constantly evolving their tactics to trick people into falling for their scams. New reports from Microsoft and the U.S. Federal Bureau of Investigation detail some of the nefarious tactics that bad actors are using to perpetrate BEC today as well as the massive damage that BEC can do. It’s essential that businesses take action now to bolster their defenses against BEC.


Get tips & advice to help you build a smart incident response plan in our guide. GET YOUR GUIDE>>
BEC places second on the list of cyber frauds
BEC was the second most expensive cyber fraud complaint received by the FBI Internet Crime Complaint Center (IC3) in 2022, racking up an astonishing $2.7 billion in losses last year according to IC3’s 2022 Internet Crime Report. The FBI was able to claw some of that money back for the victims. IC3’s Recovery Asset Team (RAT) initiated what it calls the Financial Fraud Kill Chain (FFKC) on 2,838 BEC complaints involving domestic-to-domestic transactions inside the U.S. with potential losses of over $590 million, successfully placing a hold on approximately $433 million.
FBI IC3: Most Financially Damaging Cybercrimes in 2022
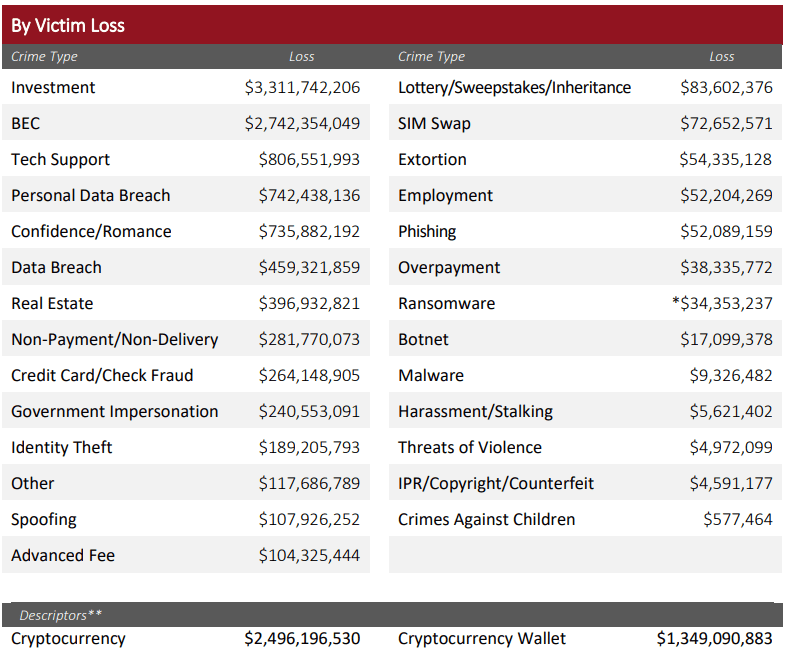

Source: FBI IC3


Insider risk is up by 40%. Help your clients stay out of trouble with The Guide to Reducing Insider Risk GET IT>>
BEC is constantly evolving
The IC3 report noted that BEC has evolved from simple hacking or spoofing of business and personal email accounts and a request to send wire payments to fraudulent bank accounts to more complex scams to using tricks like compromised vendor emails, requests for W-2 information, and gift card scams. The IC3 report highlighted several sophisticated BEC tactics that bad actors used in 2022. Phone spoofing was one of those emerging tactics. In that scam, cybercriminals spoofed legitimate business phone numbers to confirm fraudulent banking details with victims. One example cited victims reporting that they called a real estate title company using a known phone number to confirm banking information in a real estate transaction, only to find out later that the phone number has been spoofed and cybercriminals now had their financial data.
Fraudsters are also increasingly turning to cryptocurrency-related scams. This year’s report points out that bad actors are increasingly utilizing custodial accounts held at financial institutions for cryptocurrency exchanges, or luring victims into sending funds directly to cryptocurrency platforms where they can quickly snatch them up. The report also noted that IC3 saw a slight increase in schemes that targeted victims’ investment accounts instead of traditional banking accounts. Investment scams were the most expensive financial crime of 2022.


Learn how managed SOC gives you big security expertise on call 24/7without the big price tag. LEARN MORE>>
Microsoft reports surge in BEC with new tactics
FBI IC3 isn’t the only organization noticing an evolution in BEC scams. Microsoft also just released a new installment of Cyber Signals detailing an uptick in BEC and new tactics that BEC perpetrators are using to evade security measures and get to victims quickly. In the report, Microsoft says that it has observed a significant uptick in BEC attackers’ use of platforms like BulletProftLink to disguise the origin of their messages. BulletProftLink is a popular platform for creating industrial-scale malicious mail campaigns, just one of many goods and services that drive the Cybercrime-as-a-Service (CaaS) economy. Cyber Signals explained that using services like BulletProftLink makes it easier for bad actors to evade “impossible travel” alerts which are used to identify and block anomalous login attempts and other suspicious account activity.
Cybercriminals have been utilizing Phishing-as-a-Service (PhaaS) providers for several years to make the process of conducting cyberattacks faster and easier. Evil Proxy, Naked Pages and Caffeine are popular platforms that bad actors use to deploy phishing campaigns and obtain compromised credentials. BulletProftLink is a step beyond those services. It uses a decentralized gateway design, which includes Internet Computer public blockchain nodes to host phishing and BEC sites. Microsoft points out that this creates a decentralized web offering that’s much more complex and harder to disrupt by distributing these sites’ infrastructure across public blockchains.


Get the scoop on 5 of the worst email-based attacks plus tips to protect businesses from them. GET INFOGRAPHIC>>
BEC of all kinds is on the rise
According to Microsoft, BEC of all kinds is escalating. Their researchers have noted a 38% rise in BEC over the last four years. The Cyber Signals story says that the top targets for BEC are executives and other senior leadership. Other staffers with access to a means to pay bills or sensitive data are also high on the hit list including finance managers and human resources staffers who have access to employee records that include Social Security numbers, tax statements or other PII. New employees are also likely targets because they’re less likely to be comfortable taking the time to verify unfamiliar email requests. The top trends Microsoft researchers noted in targeted BEC attacks include payroll, invoice, gift card and business information scams.
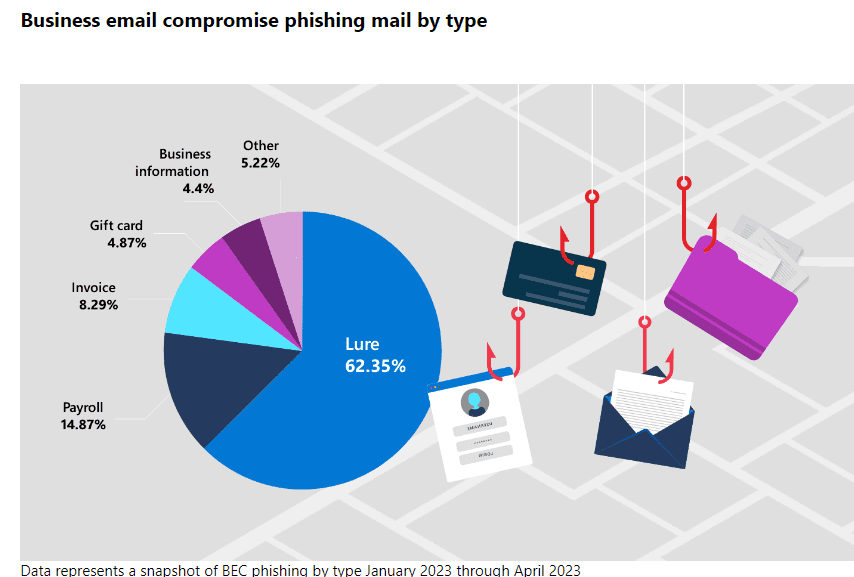

Source: Microsoft


Explore SMB cybersecurity pain points and spending plans in the Datto SMB Cybersecurity for MSPs Report. READ IT>>
Protect businesses from email-based threats like BEC with Graphus
Graphus offers businesses strong protection against phishing-based cyberattacks like BEC through the power of AI and machine learning that drives advanced automated anti-phishing software. Graphus puts three powerful shields between businesses and BEC.
- TrustGraph automatically detects and quarantines malicious emails so the end user never interacts with harmful messages. TrustGraph accomplishes this by instantly analyzing 50+ characteristics of incoming messages and comparing them to what’s typical for this company and this recipient.
- EmployeeShield alerts recipients of a potentially suspicious message that they may not notice by placing an interactive warning banner at the top that allows users to quarantine or mark the message as safe with a single click.
- Phish911 empowers employees to proactively report suspicious and unwanted emails for IT to investigate, reducing your exposure to potential disaster.
AI makes Graphus a defensive game-changer against threats like BEC
Graphus uses AI driven by a patented algorithm. The software can detect the most advanced phishing threats, including zero-day attacks and new BEC scams. It catches 99.9% of sophisticated malicious messages.
Why is AI so effective against email threats?
AI is incredibly effective against social engineering attacks like BEC for many reasons including:
- AI can effectively mimic human behavior using extensive data from past examples of similar behavior. That enables technology like TrustGraph to make decisions without human input and take actions like adjudicating the safety and authenticity of an incoming email or quarantining a suspicious message.
- AI doesn’t have human weaknesses, so it is immune to social engineering. It’s not going to fall for faked indicators of authenticity or scare tactics, removing human error and cybercriminal trickery from the equation. Every incoming message is compared to the baseline using dozens of points of comparison.
- AI will spot deviations from a company’s normal communication pattern that people might miss. That technology powers EmployeeShield to warn users of unusual messages. If users reject a message through EmployeeShield or Phish911, it is placed in quarantine to keep it away from other employees until it can be reviewed by an IT team member.
- AI-driven email security doesn’t wait for new threat intelligence to be uploaded by a tech to evolve a company’s protection. Also, it won’t quickly become obsolete like other email security technologies because it never stops learning.
Gain peace of mind with powerful protection from BEC with Graphus
Put Graphus to work for you and gain powerful protection from phishing-based threats. Employees can’t click a phishing email that they don’t receive, and you can feel confident that your smart, automated guardian will stop malicious messages effectively. Even better, automated email protection from Graphus fits every budget putting a powerful defense against today’s nastiest cyberattacks within reach for every organization.


Learn how a new integration between BullPhish ID & Graphus saves time & money. SEE THE DETAILS>>
BullPhish ID and Graphus work together with a key workflow integration
The Drop-a-Phish integration between BullPhish ID and Graphus can help you quickly deploy phishing simulation exercises and security awareness training campaigns by eliminating the need for domain whitelisting. The Graphus API allows BullPhish ID to drop phishing and training emails directly into end-user inboxes, saving hours of whitelisting time and ensuring 100% deliverability of training exercises.
Learn more about the amazing benefits you get from combining Graphus and BullPhish ID here.


Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>


May 25: Kaseya + Datto Connect Local Austin REGISTER NOW>>
May 30: Kaseya + Datto Connect Local Washington DC REGISTER NOW>>
June 8: Kaseya + Datto Connect Local Belgium REGISTER NOW>>
June 13: Kaseya + Datto Connect Local Philadelphia REGISTER NOW>>
June 15: Kaseya + Datto Connect Local Chicago Security & Compliance Track REGISTER NOW>>
June 20: Kaseya + Datto Connect Local Tampa REGISTER NOW>>
June 22: Kaseya + Datto Connect Local Atlanta REGISTER NOW>>
June 26-28: Kaseya DattoCon Europe REGISTER NOW>>
October 2 – 4: Kaseya DattoCon in Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!