The Week in Breach News: 09/27/23 – 10/03/23

This week: Ransomware leads to trouble for Johnson Controls and the U.S. Department of Homeland Security, ransomware takes down a German motel chain, six new phishing simulations are available in BullPhish ID and a deep dive into the changes expected in NIST CSF 2.0.

Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>


Progressive Leasing
https://therecord.media/product-leasing-giant-progressive-ransomware
Exploit: Ransomware
Progressive Leasing: Product Leasing Company






Risk to Business: 1.803 = Severe
Progressive Leasing announced that it was the victim of a cyberattack last week that took down the company’s systems. The company told the U.S. Securities and Exchange Commission that bad actors stole data including customers’ personally identifiable information including social security numbers. Progressive said that it has engaged a third-party firm to investigate the incident.
How It Could Affect Your Customers’ Business: Leasing companies can hold a wide variety of valuable personal and financial data from their customers.
Kaseya to the Rescue: Every company needs to be ready for trouble with an incident response plan in place to minimize downtime and speed up recovery. This checklist can help. DOWNLOAD CHECKLIST>>
McLaren Health Care
Exploit: Ransomware
McLaren Health Care: Health System






Risk to Business: 1.603 = Severe
The ALPHV/BlackCat ransomware gang has added McLaren Health Care in Michigan to its list of victims on its dark web leak site. The group claims to have 6TB of data impacting 2.5 million patients. As part of this attack, McLaren was forced to shut down IT systems temporarily at 14 of its facilities. Hospitals in four states were forced to cancel appointments, divert ambulances and use paper records. The incident remains under investigation.
How It Could Affect Your Customers’ Business: The healthcare sector has been a top target for cybercriminals conducting ransomware attacks.
Kaseya to the Rescue: See how the solutions in Kaseya’s Security Suite help IT professionals minimize risk, avoid cyberattacks and build a cyber-savvy workforce. WATCH THE WEBINAR>>


See the keys to selecting a Managed SOC to find the perfect one for your clients & your MSP. GET CHECKLIST>>


BORN Ontario
https://therecord.media/pittsburg-kansas-government-cyberattack
Exploit: Hacking
The Town of Pittsburg, KS: Municipality




Risk to Business: 1.873 = Moderate
A cyberattack has left a small city in Kansas without government email, phone and online payment systems. Officials in Pittsburg, KS, population 20,000, said that the cyberattack was discovered over the weekend. They were quick to reassure citizens that the city’s emergency services and 911 capabilities were not impacted. City officials said that their IT personnel reacted quickly and took proactive measures to protect city data and network systems. The incident remains under investigation.
How It Could Affect Your Customers’ Business: Governments of every size need to be prepared for ransomware attacks because they’re favored targets for bad actors.
Kaseya to the Rescue: What cyberattacks are the most popular this year, and what should you be preparing for in 2024? This webinar tells you everything. WATCH WEBINAR>>
Canadian Flair Airlines
https://securityaffairs.com/151512/data-breach/canadian-flair-airlines-data-leak.html
Exploit: Misconfiguration
Canadian Flair Airlines: Airline




Risk to Business: 1.710 = Severe
Canadian Flair Airlines has suffered a data breach caused by misconfiguration. The company left credentials to sensitive databases and email addresses open for at least seven months on the flyflair.com website. The public .env files revealed the MySQL database credentials and location for the local database, the MySQL database credentials and location for the remote, internet-connected database, the SMTP configuration, including credentials and secret tokens and a Laravel App key. Other stolen data may include a database of customer records that includes a customer’s first and last name, email address, phone number, flight details (destinations, dates, flight numbers, etc.) and other personal information.
How It Could Affect Your Customers’ Business: Employee mistakes are gateways for expensive diasters like a data breach or regulatory trouble.
Kaseya to the Rescue: Explore how security awareness training helps organizations defend against today’s most dangerous cyber threats like employee errors in this infographic. DOWNLOAD IT>>


See what the biggest cybersecurity challenges are right now in our Mid-Year Cyber Risk Report 2023. DOWNLOAD IT>>


Germany – Motel One
https://securityaffairs.com/151732/cyber-crime/alphv-ransomware-motel-one.html
Exploit: Ransomware
Motel One: Motel Chain






Risk to Business: 1.673 = Severe
German motel chain Motel One had suffered a ransomware attack. The chain was added to the dark web leak site of ALPHV/BlackCat. The group claims to have stolen 24,449,137 files amounting to approximately 6 TB of data. The stolen data includes booking confirmations for the past three years as well as customer records including customers’ names, addresses, dates of reservation, payment methods and contact information.
How it Could Affect Your Customers’ Business: Ransomware risk has been steadily rising for businesses in every sector, and all companies should be working to mitigate it.
Kaseya to the Rescue: Learn more about ransomware risk and the ways that IT professionals can keep companies out of trouble in our eBook Ransomware 101 DOWNLOAD IT>>
Ireland – Johnson Controls International
https://www.databreaches.net/building-automation-giant-johnson-controls-hit-by-ransomware-attack/
Exploit: Ransomware
Johnson Controls International: Security Equipment Company






Risk to Business: 1.612 = Severe
A newer ransomware group called Dark Angels is claiming responsibility for a ransomware attack that shut down some of Johnson Controls’ offices. Several subsidiaries of the company in Asia and other areas experienced IT outages as officials took systems offline in response to the attack. The gang has asked for $51 million in ransom. CNN reported that they obtained an internal memo from the U.S. Department of Homeland Security raising alarm about the incident and warning that the attack on Johnson Controls may have “compromised sensitive physical security information such as DHS floor plans.” The gang claims to have snatched 27 TB of data.
How it Could Affect Your Customers’ Business: Companies that contract for government agencies often have sensitive information that requires powerful protection
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET THE FACT SHEET>>
Switzerland – European Telecommunications Standards Institute (ETSI): Regulator
https://therecord.media/etsi-telecommunications-standards-body-hack-database-stolen
Exploit: Hacking
European Telecommunications Standards Institute (ETSI): Regulator




Risk to Business: 2.802 = Moderate
The European Telecommunications Standards Institute (ETSI) announced last week that it had been the victim of a cyberattack that led to a data breach. ETSI said that bad actors stole a database identifying its users. The non-profit said that bad actors were able to take advantage of an unnamed exploit to grab the data. The company said that the problem has since been corrected. ETSI has more than 900 member organizations from over 60 countries.
How it Could Affect Your Customers’ Business: Companies need to be careful to watch out for vulnerabilities and exploits that bad actors could use to penetrate systems
Kaseya to the Rescue: Network penetration testing can help IT professionals find the weak points in their defenses before bad actors do. LEARN MORE>>
Switzerland – The World Baseball Softball Confederation (WBSC)
Exploit: Misconfiguration
The World Baseball Softball Confederation (WBSC): Sports Governing Body






Risk to Business: 1.716 = Severe
A misconfigured server is the culprit in a data breach at The World Baseball Softball Confederation (WBSC). On June 5th, security researchers discovered a misconfigured Amazon Web Services (AWS) bucket belonging to WBSC that contained nearly 48,000 files. Some of those files contained copies of 4,600 peoples’ national passports. The WBSC, headquartered in Switzerland, was established in 2013 and currently has 141 countries as members located in Asia, Africa, the Americas, Europe and Oceania.
How it Could Affect Your Customers’ Business: When employees are trained in proper security procedures they take security more seriously and avoid mistakes.
Kaseya to the Rescue: What are the biggest risks that organizations face right now? Find the answer in our Mid-Year Cyber Risk Report 2023! DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>




6 fresh phishing kits added to BullPhish ID
These six new phishing simulation kits can help teach users to avoid phishing traps. LEARN MORE>>
- Apple National Security Department
- Microsoft Teams: Message Available v2
- UPS – Package Delivered v2
- UPS – Package Delivered v3
- Zoom Missed Call
- Bank of America Account Suspended



How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


3 resources to help keep employees off of phishing hooks
This trio of resources can help you learn about today’s biggest phishing threats and how to mitigate them.
Infographic: What Phishing Tricks Do Employees Fall For? See the results of thousands of training sessions with BullPhish ID GET INFOGRAPHIC>>
eBook: Phishing 101 Learn more about today’s phishing tricks and how businesses can be damaged by phishing. DOWNLOAD EBOOK>>
Webinar: Top Phishing Scams Employees Fall For Dive deep into today’s murky and complex phishing landscape to learn about new and evolving phishing techniques. WATCH WEBINAR>>
Did you miss…the infographic How Datto EDR With Ransomware Rollback Helps You Recover Fast from a Ransomware Attack? DOWNLOAD IT>>


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>




The NIST CSF 2.0 Is Here. Here’s What It Means for Businesses
The Cybersecurity Framework 2.0 (CSF) is finally here, and to say that it’s been a long time coming would be an understatement. The National Institute of Standards and Technology (NIST) released the latest update of its industry-standard CSF for public comment in August 2023, nearly a decade after publishing the CSF widely in use now.
Cherilyn Pascoe, the framework’s lead developer, said, “With this update, we are trying to reflect current usage of the cybersecurity framework and anticipate future usage. The CSF was developed for critical infrastructure like the banking and energy industries, but it has proved useful everywhere, from schools and small businesses to local and foreign governments. We want to make sure that it is a tool that’s useful to all sectors, not just those designated as critical.”
The much-awaited overhaul presents the cybersecurity world with a new list of challenges including significant regulatory and operational changes for the public and private sectors. But before diving into everything you need to know about CSF 2.0, let’s go over what CSF is and what its data security and privacy mandates are.



Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>
The evolution of NIST CSF
The NIST CSF was drafted in 2014, containing a host of stringent guidelines that sought to curb the negative effects of cybercrime. It was a response to the ever-evolving threat landscape. The initial release set up common standards and practices for organizations to follow and minimize the number and severity of cybersecurity risks.
The five functions of CSF 1.1
The NIST CSF 1.1 reflects a flexible, risk-based approach that focuses on five functions, as listed below.
- Identify (ID): The first step in the framework, this function expresses that organizations must thoroughly understand the cybersecurity risks they are subject to in their specific business environment. It involves asset management, carrying out risk assessments, enterprise-wide vulnerability management and building effective IT risk management strategies that cover legal, supply chain and other regulatory aspects. Implemented successfully, businesses will be more aware of their security posture as it pertains to their respective industry and environment.
- Protect (PR): This function focuses on establishing preventative measures to protect an organization’s critical assets and infrastructure against cyberthreats. IT professionals must proactively enforce strict policies around access controls, encryption and cybersecurity awareness training programs. The objective here is to safeguard the integrity of a business’s data and systems while ensuring they are still easily accessible. In short, this Function helps reduce an organization’s attack surface.
- Detect (DE): Identifying, reporting and documenting all cybersecurity events is critical in strengthening enterprise security. The “Detect” function involves setting up processes or controls that ensure continuous monitoring, anomaly detection and incident detection capabilities. When it comes to cyber threats, speed determines how much damage a bad actor can cause. Quicker detection allows for a more rapid and effective response to potential incidents.
- Respond (RS): Just as the name implies, the “Respond” function strives to express the value of a well-defined response to cybersecurity incidents. This step involves many layers of collaboration and strategy. The key elements include creating incident response plans, establishing roles and responsibilities and strengthening communication between every active participant.
- Recover (RC): As the fifth pillar of the NIST CSF, this function instructs organizations on restoring services, operations and the norm after a cybersecurity incident. IT professionals at this step need to develop and implement effective recovery plans, understand what went wrong in the first place and create safeguards to ensure the same incident does not recur. Efficient recovery bodes well for the business by reducing downtime and maintaining continuity.
While all these functions remain in the latest NIST CSF 2.0 draft, one of the biggest amendments in the framework is the addition of a sixth function.


Learn how Datto EDR satisfies cyber insurance requirements for endpoint protection & EDR. DOWNLOAD REPORT>>
Govern: The sixth pillar of the NIST CSF
Back in February 2022, the NIST reached out to the community for insights on the state of cybercrime and how to best go about revising the framework. Considering the fact that CSF 1.1 has been downloaded over two million times since its release, there were many opinions put forth. From those comments, the NIST decided to add “Govern” as the sixth function.
According to the NIST CSF 2.0, “Govern” (GV) guides organizations to establish and monitor their cybersecurity risk management strategy, expectations and policy. This function offers a range of outcomes to help businesses understand how they can achieve and prioritize the desired security outcomes of the other five functions. It supports organizations in improving their cybersecurity practices meticulously within the context of their security goals and stakeholder expectations.
Governance activities empower organizations to implement cybersecurity into their broader enterprise risk management strategy. GV involves understanding specific contexts, setting up strategies, managing supply chain risks, defining roles and responsibilities, establishing policies and overseeing cybersecurity strategy development. It precedes the “Identify” function.
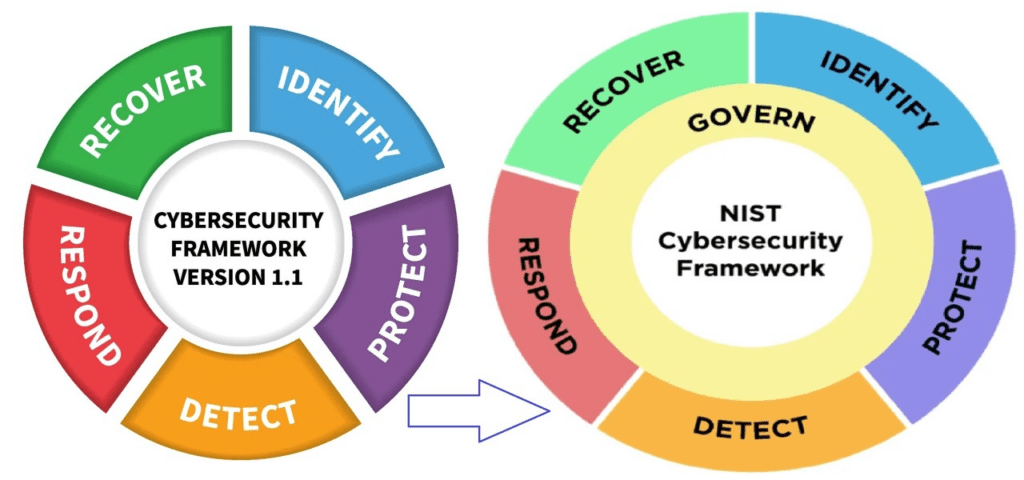

Source: NIST


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>
NIST is looking at more changes
However, the Govern function isn’t the only change that’s being proposed. NIST has deemed several other adjustments necessary to help companies fend off the modern cybercriminal.
Broader scope
For starters, the NIST has recognized the widespread adoption of the CSF and subsequently modified the framework’s scope, narrative and functions to reflect its use by all organizations, regardless of size and industry. Importantly, CSF 2.0 has moved from emphasizing the security of U.S. critical infrastructure to now focusing on businesses globally.
Improved referencing to other frameworks
The NIST’s latest CSF draft now relates to a handful of important frameworks and resources that will play a huge role in helping companies better secure their environments. It includes references to:
- NIST Privacy Framework
- NICE Workforce Framework for Cybersecurity (SP 800-181)
- Secure Software Development Framework (SP 800- 218)
- Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations (SP 800-161r1)
- Performance Measurement Guide for Information Security (SP 800-55)
- Integrating Cybersecurity and Enterprise Risk Management (NIST IR 8286) series
- Artificial Intelligence Risk Management Framework (AI 100-1)
The NIST will also launch an online tool on the CSF website concerning CSF 2.0’s Core, offering human- and machine-readable formats. This tool will let organizations view online connections between the Core and updatable Informative References.


Increased CSF implementation guidance
The NIST CSF has been made more user-friendly by adding real-world implementation examples that best explain how companies can achieve CSF Subcategories. The guidance on Framework Profiles has also been significantly improved, offering clear steps and demonstrating how it can be applied effectively for diverse purposes. This should help streamline an organization’s strategy development for enhanced cyber defense. Additionally, NIST has developed templates to enable companies to create their Profiles and action plans.
To top it all off, the NIST CSF 2.0 will soon release a Reference Tool, allowing users to download and search the CSF 2.0 Draft Core with ease. Stay in the know by accessing this progress update site, where every updated example and CSF Informative Reference can be found.
A new emphasis on supply chain risk management
Under the GV Function, NIST specifies a new category dedicated entirely to helping companies address supply chain risk management — a very large threat in the current landscape. The updated draft carries the NIST’s best practices and guidance that empower organizations to best manage and handle cybersecurity supply chain risks and ensure security for all parties in the value chain.



How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>
The Four Framework Tiers
CSF 2.0 maintains information on the latest cybersecurity assessment practices. On the basis of cybersecurity governance, risk management and third-party risks, the draft better explains the four framework tiers, namely:
- Tier 1: Partial:
Consists of ad hoc cybersecurity practices with limited awareness and understanding of risks. An organization may have basic cybersecurity measures in place but often lacks a solid execution strategy.
- Tier 2: Risk Informed:
Companies at this stage have developed risk management processes but have not yet integrated them into their organizational culture. However, there is an awareness of cyber-risks and their potential impact on the business. Based on their identified priorities, companies are guided to create evolving strategies to address their specific security concerns.
- Tier 3: Repeatable:
Moving towards managing risk, organizations at this stage have established well-defied risk management processes that are integrated into the daily workflow. They are following a proactive approach to discovering and eliminating security risks, guided by effective strategies. Such strategies also involve routine monitoring and modification of cybersecurity measures to adapt to the ever-evolving threat landscape.
- Tier 4: Adaptive:
Continually adapting is the only way to counter the modern cybercriminal. Companies are guided toward fostering a dynamic and flexible approach to cybersecurity that encourages practices like continuous monitoring, scheduled assessments and security awareness training. The result? Businesses can respond to cybersecurity threats and incidents faster, with clear plans of action for any given scenario. The learnings from each event help improve employee training and further bolster an organization’s immunity against cyberattacks.
NIST will be accepting public comment on CSF 2.0 at [email protected] until November 4, 2023


Get the scoop on 5 of the worst email-based attacks plus tips to protect businesses from them. GET INFOGRAPHIC>>
Kaseya’s Security Suite arms IT professionals with the tools they need to mitigate ransomware risk
Get must-have tools for mitigating ransomware risk with Kaseya’s Security Suite.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents employee mistakes and reduces a company’s risk of being hit by a cyberattack.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection around with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
Graphus — Automated email security is a cutting-edge solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
Kaseya Managed SOC powered by RocketCyber — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).
Vonahi Penetration Testing – How sturdy are your cyber defenses? Do you have dangerous vulnerabilities? Find out with vPenTest, a SaaS platform that makes getting the best network penetration test easy and affordable for internal IT teams.


See how Managed SOC gives businesses an essential edge against cyberattacks. DOWNLOAD INFO SHEET>>


ID Agent & Graphus Q4 Product Innovation
October 10 | 10 AM EDT | 7 AM PDT | 2 PM GMT
October 10 | 6 PM EDT | 3 PM PDT | 8 AM AEST (October 11)
Join us to learn about the latest product innovations for BullPhish ID, Dark Web ID, Passly and Graphus. You will learn about new time-saving product integrations and the latest features and enhancements, including mini-demos of the most exciting features and get a look at what’s on the Security products’ roadmaps for Q4 and beyond! REGISTER NOW>>
September 28: Kaseya + Datto Connect Local Charlotte REGISTER NOW>>
October 2 – 4: Kaseya DattoCon in Miami REGISTER NOW>>
October 10: Kaseya + Datto Connect Local Minneapolis REGISTER NOW>>
October 12: Kaseya + Datto Connect Local Chicago REGISTER NOW>>
October 17: Kaseya + Datto Connect Local Columbus REGISTER NOW>>
October 18: Kaseya + Datto Connect Local South Africa REGISTER NOW>>
October 19: Kaseya + Datto Connect Local Vancouver REGISTER NOW>>
October 24: Kaseya + Datto Connect Local Seattle REGISTER NOW>>
October 26: Kaseya + Datto Connect Local San Francisco REGISTER NOW>>
November 2: Kaseya + Datto Connect Local New York REGISTER NOW>>
November 7: Kaseya + Datto Connect Local New York REGISTER NOW>>
November 7: Kaseya + Datto Connect Local London REGISTER NOW>>
November 9: Kaseya + Datto Connect Local Manchester REGISTER NOW>>
November 14: Kaseya + Datto Connect Local Montreal REGISTER NOW>>
November 14 – 16: Kaseya DattoCon APAC REGISTER NOW>>
November 16: Kaseya + Datto Connect Local Pittsburgh REGISTER NOW>>
November 30: Kaseya + Datto Connect Local Long Beach REGISTER NOW>>
December 5: Kaseya + Datto Connect Local Orlando REGISTER NOW>>
December 7: Kaseya + Datto Connect Local Symposium Miami REGISTER NOW>>
December 12: Kaseya + Datto Connect Local Arlington TX (Dallas Area) REGISTER NOW>>
December 14: Kaseya + Datto Connect Local New Orleans REGISTER NOW>>
December 19: Kaseya + Datto Connect Local St. Petersburg, FL REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!