The Week in Breach News: 10/11/23 – 10/17/23

This week: An $80 million ransom demand from LockBit, a disruptive cyberattack nails Simpson Manufacturing, U.S. federal agencies warn against a novel ransomware attack and a new integration between Autotask and RocketCyber.

Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>

Simpson Manufacturing Company
https://www.constructiondive.com/news/simpson-manufacturing-cyberattack-construction/696408/
Exploit: Hacking
Simpson Manufacturing Company: Construction Materials Fabricator

Risk to Business: 1.403 = Extreme
Construction materials giant Simpson Manufacturing has revealed that it was hit by a disruptive cyberattack The California-based company said in its filing with the U.S. Securities and Exchange Commission (SEC) that it discovered malicious activity in its network infrastructure and immediately took systems offline to limit the damage. The company expects continued snags to its operations in the wake of the attack.
How It Could Affect Your Customers’ Business: Bad actors have been heavily targeting critical infrastructure targets, with attacks on manufacturers rising.
Kaseya to the Rescue: Every company needs to be ready for trouble with an incident response plan in place to minimize downtime and speed up recovery. This checklist can help. DOWNLOAD CHECKLIST>>
First Judicial Circuit Court of Florida
Exploit: Ransomware
First Judicial Circuit Court of Florida: State Court System

Risk to Business: 1.603 = Severe
The ALPHV/BlackCat ransomware group has claimed responsibility for a ransomware attack on Florida’s First Judicial Circuit Court. The court confirmed that it had experienced a successful cyberattack on October 2. That attack has resulted in major disruptions in the operations of the court system. A statement from the court said that the Circuit is prioritizing essential court proceedings but will cancel and reschedule other proceedings and pause related operations for several days, beginning October 2. No ransom demand has been made public.
How It Could Affect Your Customers’ Business: Bad actors have been putting pressure on government agencies and institutions like court systems and agencies with ransomware.
Kaseya to the Rescue: See how the solutions in Kaseya’s Security Suite help IT professionals minimize risk, avoid cyberattacks and build a cyber-savvy workforce. WATCH THE WEBINAR>>
CDW
https://therecord.media/cdw-investigates-ransomware-gang-claim
Exploit: Ransomware
CDW: Technology Services



Risk to Business: 1.873 = Moderate
CDW, a major supplier of technology services to businesses and the U.S. federal government, has been added to the LockBit ransomware group’s leak site. The company confirmed that it had experienced a cyberattack but noted that the attack was limited to a few servers dedicated solely to the internal support of Sirius Federal, a subsidiary of CDW’s government services arm CDW-G. CDW was quick to reassure customers that the affected servers are non-customer-facing and isolated from CDW’s main network and other CDW-G systems. LockBit has demanded a whopping $80 million in ransom, one of the largest ransom demands ever publicly released. LockBit published a small amount of the stolen data as proof of its hack, including images of employee badges, audit data, commission payout data and other account-related information.
How It Could Affect Your Customers’ Business: This kind of data is highly sensitive and cybercriminals could use it to spear phish or facilitate blackmail
Kaseya to the Rescue: What cyberattacks are the most popular this year, and what should you be preparing for in 2024? This webinar tells you everything. WATCH WEBINAR>>
Morrison Community Hospital
https://securityaffairs.com/152486/cyber-crime/alphv-ransomware-morrison-community-hospital.html
Exploit: Ransomware
Morrison Community Hospital: Medical Center


Risk to Business: 1.710 = Severe
Morrison Community Hospital has been the victim of a ransomware attack. The ALPH-V/BlackCat ransomware gang has added the medical center to its dark web leak site. The group said that it stole 5TB of data including patients’ and employee’s information, backups and PII documents. The group has published a sample of the data on its leak site. In a twist, BlackCat stated that the hospital has not responded, threatening to begin contacting patients.
How It Could Affect Your Customers’ Business: Ransomware has been heavily used in attacks against healthcare targets like hospitals and clinics.
Kaseya to the Rescue: Explore how security awareness training helps organizations defend against today’s most dangerous cyber threats like employee errors in this infographic. DOWNLOAD IT>>
Walmart
https://www.jdsupra.com/legalnews/walmart-inc-files-notice-of-data-breach-8481333/
Exploit: Hacking
Walmart: Retailer





Risk to Business: 1.673 = Severe
One of the world’s largest retailers has informed the U.S. Department of Health and Human Services Office for Civil Rights that is has experienced a data breach. Walmart did not specify what type of data was stolen but the nature of the filing offers insight, pointing to the exposed data being protected health information. Walmart said that this data breach affected 85,952 individuals.
How it Could Affect Your Customers’ Business: Fines and penalties for a breach of protected health information will be expensive even for a massively profitable business like Walmart,
Kaseya to the Rescue: Learn more about ransomware risk and the ways that IT professionals can keep companies out of trouble in our eBook Ransomware 101 DOWNLOAD IT>>


Learn more about growing supply chain risk for businesses and how to mitigate it in a fresh eBook. DOWNLOAD IT>>


Spain – Air Europa
Exploit: Hacking
Air Europa: Airline





Risk to Business: 1.612 = Severe
Spanish air carrier Air Europa is informing customers that they have suffered a data breach. The breach of customer credit card details resulted from exposure through Air Europa’s online payment system. The airline emailed customers whose credit card details were exposed. Air Europa did not specify the number of customers affected. The company said no other information had been exposed, and it has informed the relevant authorities.
How it Could Affect Your Customers’ Business: Credit card data can be very lucrative for bad actors, making it a hot commodity.
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET THE FACT SHEET>>
France – LDLC ASVEL Villeurbanne
https://cybernews.com/news/tony-parker-asvel-data-breach/
Exploit: Ransomware
ASVEL: Basketball Team



Risk to Business: 2.802 = Moderate
A ransomware group is claiming to have snatched data from LDLC ASVEL Villeurbanne, a Euro League basketball team owned by the former NBA star Tony Parker. The gang NoEscape has added ASVEL to its dark web leak site, claiming that they stole 32GB of data. That data supposedly includes players’ passports and IDs, ASVEL’s financial and tax data, team non-disclosure agreements (NDAs), player scouting contracts and other confidential information.
How it Could Affect Your Customers’ Business: Ransomware attacks are primarily email-based and businesses need advanced email security that can quickly detect threats like ransomware.
Kaseya to the Rescue: This checklist can help businesses determine if they’re making all the right moves to prevent email-based cyberattacks. DOWNLOAD IT>>
France – Shadow PC
https://techcrunch.com/2023/10/13/shadow-data-breach-hacked/
Exploit: Hacking
Shadow PC: Cloud Gaming Support Provider





Risk to Business: 1.716 = Severe
PC gaming cloud services provider Shadow PC has confirmed that the company has experienced a cyberattack that led to the exposure of half a million customers’ data. The company said that one of its employees had fallen victim to a social engineering attack that began on the Discord platform. An employee apparently downloaded malware in the guise of a game on the Steam platform. The stolen data includes full customer names, email addresses, dates of birth, billing addresses and credit card expiration dates. Passwords and payment data were not impacted.
How it Could Affect Your Customers’ Business: It’s essential to teach employees to resist social engineering lures with security awareness training.
Kaseya to the Rescue: See how security awareness training helps keep cybersecurity threats from becoming cybersecurity disasters. DOWNLOAD INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident



Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>




A new time-saving integration between RocketCyber and Autotask is here!
A fresh integration between Autotask and RocketCyber empowers IT professionals to resolve RocketCyber incidents by simply closing or completing the relevant AutoTask ticket. This new function is available to RocketCyber users under the integrations tab. Just scroll down to AutoTask and you’ll see the status for tickets. To resolve a task in both solutions from an Autotask ticket, click the complete button at the top of the page and follow the prompts in the drop-down menu.
LEARN MORE ABOUT ROCKETCYBER>>


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


New eBook: “When Email Attacks: How To Develop Your Employees’ Phishing Defense Superpowers”
Transforming mild-mannered employees into security superheroes is a major asset for businesses. Our latest guide can help you reduce cyberattack risk, run effective training exercises and create a culture of security. Download our new eBook now to find:
- Four crucial components of security awareness training
- How to maintain a culture of security, even with remote workers
- Expert advice from cybersecurity influencers
- DOWNLOAD IT>>
Did you miss…The 2023 edition of The Comprehensive Guide to Third-party and Supply Chain Risk? DOWNLOAD IT>>



Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>




Feds Issue New Attack Advisory Amid Ransomware Surge
Companies need to be ready to ride out today’s ransomware surge, especially organizations that are high on the priority list of ransomware gangs. Last week, U.S. federal officials raised the alarm about new tactics and targets for one prominent ransomware gang. Plus, new data has just been released showing just how majorly ransomware attack trends have been shooting upward. What does all of that mean? It means that every organization of every size may be in bad actors’ crosshairs, and businesses need to bolster their cyber resilience to handle the increased pressure from novel ransomware attacks.



What cybercriminal tricks do employees fall for in phishing simulations? Find out in this infographic. GET IT>>
Feds Warn: New Targets and Procedures Endanger Infrastructure
The U.S. Federal Bureau of Investigation (FBI) and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) have just released a joint Cybersecurity Advisory (CSA) about the AvosLocker ransomware group. In the advisory, the agencies share data about known indicators of compromise (IOCs), techniques, tactics and procedures (TTPs) and detection methods associated with AvosLocker based on data gleaned from FBI investigations as recently as May 2023. The advisory also warns that AvosLocker has compromised organizations in several critical infrastructure sectors, raising the stakes.
The FBI and CISA offered some insight into how AvosLocker group operates. AvosLocker is a group that follows the ransomware-as-a-service (RaaS) model. According to officials, AvosLocker affiliates have compromised organizations across multiple critical infrastructure sectors in the United States, affecting Windows, Linux and VMware ESXi environments. The CSA went on to say that AvosLocker affiliates aim to compromise organizations’ networks through the use of legitimate software and open-source remote system administration tools. Once inside a company’s cybersecurity perimeter, AvosLocker affiliates then use exfiltration-based data extortion tactics with threats of leaking and/or publishing stolen data.


Find out how Datto EDR helps with Health Insurance Portability and Accountability Act (HIPAA) compliance. GET INFO>>
AvosLocker exploits open-source tools
AvosLocker affiliates use legitimate software and open-source tools during ransomware operations, which include exfiltration-based data extortion. Specifically, affiliates use:
- Remote system administration tools—Splashtop Streamer, Tactical RMM, PuTTy, AnyDesk, PDQ Deploy, and Atera Agent—as backdoor access vectors
- Scripts to execute legitimate native Windows tools such as PsExec and Nltest.
- Open-source networking tunneling tools Ligolo[ and Chisel
- Cobalt Strike and Sliverfor command and control (C2)
- Lazagne and Mimikatz for harvesting credentials
- FileZilla and Rclone for data exfiltration.
- Notepad++, RDP Scanner, and 7zip.
- FBI has also observed AvosLocker affiliates:
- Custom PowerShell and batch (.bat) scripts for lateral movement, privilege escalation, and disabling antivirus software.
- Custom webshells to enable network access



Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>
AvosLocker isn’t the only gang to worry about
There are an array of gangs using a wide variety of ransomware variations that are on the scene at any given time. Law enforcement does catch and bust up groups frequently, as seen in the fall of the once-leading ransomware group REvil. But that doesn’t stop gangs and ransomware variants from proliferating. These active groups are also constantly adjusting their TTPs in an attempt to stay a step ahead of defenders, and sometimes they succeed all too well.
In early October, the FBI issued a warning about a rising ransomware trend. The bureau revealed in a Private Industry Notification that a new type of ransomware attack has been hitting organizations: dual ransomware attacks. In this scenario, separate attacks are conducted just hours or days apart. The FBI noted that the majority of dual ransomware attacks that they’ve recorded occurred within 48 hours of each other. Sometimes, attackers will use different ransomware variants between the two attacks. The bureau said that ultimately, this use of dual ransomware variants resulted in a combination of data encryption, exfiltration and financial losses from ransom payments for victims.


See why EDR is the perfect investment to make in your future right now in our buyer’s guide. DOWNLOAD IT>>
Ransomware spiked in September 2023
Businesses have been able to celebrate some good news about ransomware in recent years. Cyber insurer Corvus recently reported that they’d noted a 52% reduction in ransomware claims over the full year in 2022. IT professionals could also feel encouraged by the information that Corvus saw a 62% decline in ransomware claims from Q1 2021 to Q4 2022. This downward trend was encouraging. Some of the factors that helped create this downturn were better threat intelligence becoming widely available for IT professionals and defensive techniques against ransomware, innovation in security solutions and a rise in businesses investing in cybersecurity.
Unfortunately for businesses, that all changed in 2023. Corvis reported that recorded ransomware attacks rose for the eighth consecutive month in September, climbing by about 5% in September. The news only gets worse from there. All told Corvus noted an almost 80% increase in ransomware attacks year-over-year.
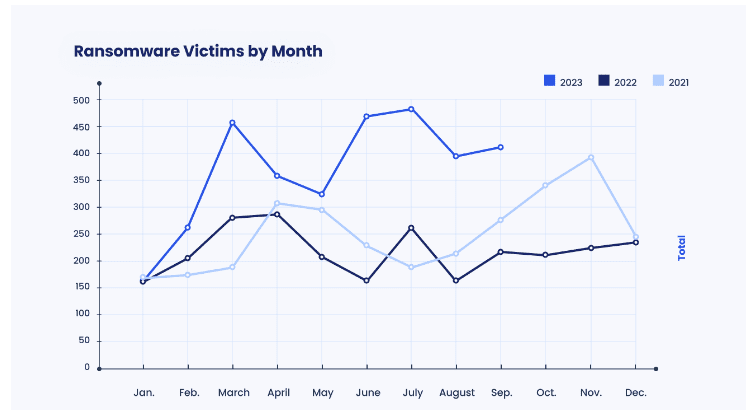

Source: Corvus


Follow the path to see how Managed SOC heroically defends businesses from cyberattacks. GET INFOGRAPHIC>>
Bolstering a company’s defenses and cyber resilience right away pays off
Businesses need to take action now to ensure that they’re ready to withstand this troubling flood of risk. CISA recommends that companies take a variety of precautions including:
- Securing remote access tools in a variety of ways including placing strict limits on the use of RDP and other remote desktop services.
- Disabling file and printer-sharing services. If these services are required, use strong passwords or Active Directory authentication.
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location (e.g., hard drive, storage device, or the cloud).
- Requiring all accounts with password logins to comply with the standards recommended by the U.S. National Institute for Standards in Technology (NIST) for developing and managing password policies.
- Ensuring that they are capable of identifying, detecting and investigating abnormal activity including lateral movement activity. CISA notes that endpoint detection and response (EDR) tools are particularly useful for detecting lateral connections
- Adding an email banner to emails received from outside of an organization. The primary vector of ransomware attacks against businesses is email. Increased email security can go a long way toward preventing a ransomware nightmare.
- Keeping all operating systems, software and firmware up to date. According to CISA, regular, timely patching is one of the most efficient and cost-effective steps an organization can take to minimize its exposure to cybersecurity threats.
SEE CISA’S LIST OF PRECAUTIONS>>



Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>
Get must-have tools for mitigating ransomware risk with Kaseya’s Security Suite.
This surge of ransomware attacks is a reminder to IT professionals that the risk of a business falling victim to a cyberattack like ransomware risk is always present and can surge at any time. Taking smart precautions now prevents expensive trouble later.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents employee mistakes and reduces a company’s risk of being hit by a cyberattack.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection around with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
Graphus — Automated email security is a cutting-edge solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
Kaseya Managed SOC powered by RocketCyber — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).
Vonahi Penetration Testing – How sturdy are your cyber defenses? Do you have dangerous vulnerabilities? Find out with vPenTest, a SaaS platform that makes getting the best network penetration test easy and affordable for internal IT teams.



What cybercriminal tricks do employees fall for in phishing simulations? Find out in this infographic. GET IT>>


The New Security Paradox: Offensive vs Defensive AI
November 1, 2023 | 1:00 PM ET/10 AM PT
AI and machine learning technologies have been around for many years, however, in the past year they’ve taken a whole new evolutionary leap. With the seemingly daily rollouts of new AI chatbots and tools, there is a race underway to use AI in novel ways which presents both challenges and opportunities for cybersecurity professionals. Join us for a deep dive into the current and future cybersecurity AI landscape and explore how we use AI at Graphus to protect our customers from cyberattacks.
October 18: Kaseya + Datto Connect Local South Africa REGISTER NOW>>
October 19: Kaseya + Datto Connect Local Vancouver REGISTER NOW>>
October 24: Kaseya + Datto Connect Local Seattle REGISTER NOW>>
October 14: Cybersecurity Roundtable Series: State of the MSP Webinar REGISTER NOW>>
October 26: Kaseya + Datto Connect Local San Francisco REGISTER NOW>>
November 2: Kaseya + Datto Connect Local New York REGISTER NOW>>
November 7: Kaseya + Datto Connect Local New York REGISTER NOW>>
November 7: Kaseya + Datto Connect Local London REGISTER NOW>>
November 9: Kaseya + Datto Connect Local Manchester REGISTER NOW>>
November 14: Kaseya + Datto Connect Local Montreal REGISTER NOW>>
November 14 – 16: Kaseya DattoCon APAC REGISTER NOW>>
November 16: Kaseya + Datto Connect Local Pittsburgh REGISTER NOW>>
November 30: Kaseya + Datto Connect Local Long Beach REGISTER NOW>>
December 5: Kaseya + Datto Connect Local Orlando REGISTER NOW>>
December 7: Kaseya + Datto Connect Local Symposium Miami REGISTER NOW>>
December 12: Kaseya + Datto Connect Local Arlington TX (Dallas Area) REGISTER NOW>>
December 14: Kaseya + Datto Connect Local New Orleans REGISTER NOW>>
December 19: Kaseya + Datto Connect Local St. Petersburg, FL REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!