Today’s Booming Dark Web Economy Heightens Ransomware Risk

Pop quiz: where will you find the world’s third-largest economy? If you answered “the dark web”, you’re right. Cybercrime is a thriving growth industry with no ceiling in sight. Cybersecurity Ventures estimates that cybercrime raked in $6 trillion in 2021. Cybercrime is responsible for one of the most significant shifts in economic wealth in history, and the dark web is the marketplace for cybercrime activity. That makes trends in dark web markets an important indicator of the rise and fall of threats that businesses face today as well as the threats of tomorrow.

Considering a new dark web monitoring solution? This eBook helps you find the right one for your organization. GET EBOOK>>
The Growth of Cybercrime Never Stops
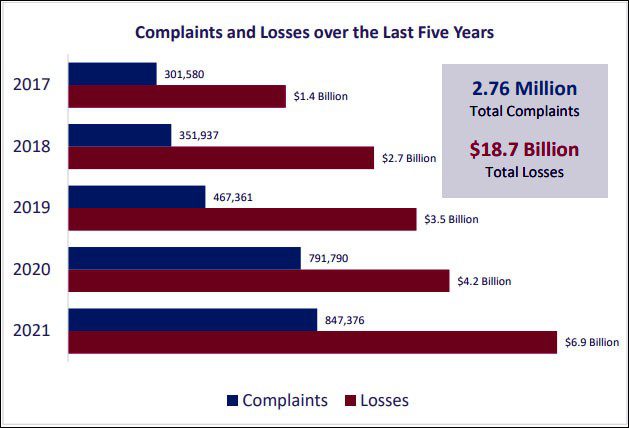
The U.S. Federal Bureau of Investigation Internet Crime Complaint Center recently released IC3 2021 Internet Crime Report breaks down the cybercrime the Bureau recorded in 2021 to shed a little light on the growth or change in cybercrime in general in the U.S. And what a year it was, easily destroying 2020’s totals. IC3 received a record number of complaints in 2021. The total of 847,376 reported complaints, wasn’t so much larger than the year prior, just a 7% increase from 2020. But the money total is a stunner. The total amount of loss reported hit a new record high in 2021 of $6.9 billion. That’s a whopping 48% increase over 2020.

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>
Hiring a Cybercrime Specialist is All Too Simple
Just like any other business, cybercriminals know that hiring specialists and service providers makes good business sense. Thanks to the rise of a booming Cybercrime-as-a-Service (CaaS) market on the dark web, outsourcing cybercrime is both easy and cheap for the bad guys. A vast array of varied cybercrime specialists are jockeying to sell their services on dark web message boards, Discord servers and Telegram channels. A galaxy of cybercriminal organizations from sophisticated nation-state threat actors to run-of-the-mill ransomware outfits are more than happy to keep them gainfully employed.
Most of the major cybercrime groups work with affiliates and freelancers for everything from software to phishing operations. These days operating or deploying malware isn’t complicated. Plug-and-play malware complete with a user manual is widely available. Distributing that malware is also something that the big dogs can subcontract through a Phishing-as-a-Service specialist. According to Microsoft researchers, a PhaaS group’s subscription prices vary dependent on a host of factors, but in general, the service can cost about $800 per month. Many of these operators offer what amounts to a one-stop shop for phishing. featuring everything from DIY kits to full-service contracting.
An estimated 300,000 thousand new pieces of malware are created daily. Malware-as-a-Service (MaaS) and its offshoot Ransomware-as-a-Service (RaaS) are successful cybercrime business models that offer bad actors everything from the usage of ‘pay-and-use’ malware for conducting cybercrime to full-service outsourcing of complete malware deployment operations. Of course, Ransomware-as-a-Service is a highly successful branch of that industry. Think of it as adopting the ‘software as a service’ revenue model, only the software is malicious. CaaS and its attendant specialties have a bright future. Cybersecurity Ventures predicts that we’ll see a 15% increase in revenue for cybercrime in the next three years, resulting in a whopping $10.5 trillion by 2025.

The right dark web monitoring could be the difference between security success or failure. This checklist helps you find it GET IT>>
Ransomware Risk Spikes in Time-Crunched Sectors
The growth of cybercrime services is a major contributor to the rapid acceleration of cyberattack risk, especially for industries that are under stress. Easy access to specialists and tools has made it a snap for bad actors to conduct successful cybercrime operations quickly, and that’s very bad news for businesses, especially when it comes to ransomware attacks. The US has incurred a 127% year-to-date increase in the number of ransomware attacks while the UK has seen a 233% surge in ransomware infections – and unfortunately, many of those attacks are strategically targeted at critical infrastructure.
A good example of this is the recent Private Industry Notification released by the FBI regarding elevated ransomware risk for organizations in the Food and Agriculture sector. Why? It is planting season in the U.S., and cybercriminals are savvy about timing attacks to take advantage of time pressures and other stressors in infrastructure sectors in order to maximize their chance to score a big, quick ransom payment. The FBI broke down the possible result of successful ransomware attacks against agriculture targets right now noting that, “A significant disruption of grain production could impact the entire food chain since grain is not only consumed by humans but also used for animal feed. In addition, a significant disruption of grain and corn production could impact commodities trading and stocks. An attack that disrupts processing at a protein or dairy facility can quickly result in spoiled products and have cascading effects down to the farm level as animals cannot be processed.”

Drill down to the bottom line to see why security & compliance awareness training is a smart investment. GET IT>>
Ransomware is a Constant Menace to Infrastructure
In this alert, the FBI also included a few examples of ransomware attacks in the Food and Agriculture sector in the last year that have had a significant impact, including attacks against six grain cooperatives during the fall 2021 harvest and two attacks in early 2022.
- March 2022: A multi-state grain company falls victim to a Lockbit 2.0 ransomware attack. In addition to grain processing, the company provides critically needed services during the planting season including seed, fertilizer and logistics.
- February 2022: A company providing feed milling and other agricultural services reported not one but two incidents during which an unauthorized actor gained access to some of its systems and used that access to attempt a ransomware attack. Those attacks were detected and stopped before encryption occurred.
- September – October 2021: Six grain cooperatives experienced ransomware attacks including New Cooperative & Crystal Valley Cooperative. Attackers used a variety of ransomware variants like Conti, BlackMatter, Suncrypt, Sodinokibi, and BlackByte. New Cooperative and Crystal Valley Cooperative were both hit by BlackMatter. Some cooperatives were crippled, halting operations during the critical harvest season.

Learn 5 red flags that could indicate a malicious insider is at work in your organization! DOWNLOAD INFOGRAPHIC>>
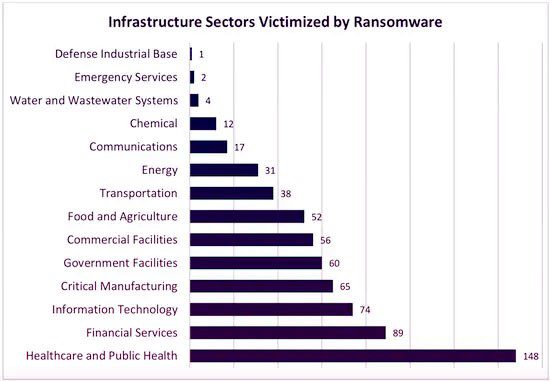
14 of 16 Infrastructure Sectors Were Hit with Ransomware in 2021
The 2021 IC3 report also paints a clear picture of the larger picture of ransomware attacks against infrastructure targets. Food and Agriculture is one of 16 critical infrastructure sectors designated by The U.S. Cybersecurity & Infrastructure Security Agency (CISA). IC3 also reported that 14 of those 16 critical infrastructure sectors were hit with ransomware attacks in 2021. Agriculture was the seventh most attacked critical infrastructure sector in the U.S. in 2021. The sectors that faced the most ransomware attacks were Healthcare & Public Health (148), Financial Services (89) and Information Technology (74). Only two sectors, the Nuclear Reactors, Materials and Waste Sector and the Dams Sector did not experience any reported ransomware attacks in 2021.

Be the hero that defeats a company’s security threats to declare victory over cybercriminals! GET THE GUIDE>>
Reduce Mounting Risk from the Dark Web
Get the clear, actionable insight that you need to make all the right security moves with Dark Web ID, the Channel leading dark web monitoring platform trusted by organizations worldwide.
- 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses
- Uncover compromised credentials in Dark Web markets, data dumps and other sources, and get fast alerts to new ones
- An easy-to-use, automated monitoring platform that deploys in minutes and gets to work immediately, with SaaS or API options available
Schedule your demo of Dark Web ID today. BOOK IT>>

Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!