The Week in Breach News: 10/25/23 – 10/31/23

This week: Check out a weird twist a cyberattack took on a school system, get all the details of a ransomware attack at Seiko, learn about a new feature in BullPhish ID and explore IoT risk and how to mitigate it.

Learn more about growing supply chain risk for businesses and how to mitigate it in a fresh eBook. DOWNLOAD IT>>

American Family Insurance
https://www.scmagazine.com/brief/cyberattack-related-outages-reported-by-american-family-insurance
Exploit: Hacking
American Family Insurance: Insurer

Risk to Business: 2.227 = Severe
Insurance giant American Family Insurance has admitted that it experienced a cyberattack last week that has disrupted some of its systems. The company said that it detected an intrusion and shut down systems for safety. Customers have reported being unable to pay bills or file claims online. They are instead directed to contact American Family Insurance via phone instead. The incident is under investigation.
How It Could Affect Your Customers’ Business: Companies like this often hold large quantities of valuable data making them attractive targets.
Kaseya to the Rescue: Every company needs to be ready for trouble with an incident response plan in place to minimize downtime and speed up recovery. This checklist can help. DOWNLOAD CHECKLIST>>
Westchester Medical Center Health Network (WMCHealth)
https://healthitsecurity.com/news/cyberattack-on-ny-hospitals-forces-ambulance-diversions
Exploit: Hacking
Westchester Medical Center Health Network (WMCHealth): Healthcare System


Risk to Business: 1.211 = Extreme
Hospitals associated with the Westchester Medical Center Health Network (WMCHealth) in New York were forced to temporarily divert ambulances to other hospitals and shut down their IT systems in response to a cyberattack last week. The impacted hospitals are HealthAlliance Hospital and Margaretville Hospital, both members of the HealthAlliance of the Hudson Valley. WMCHealth had confirmed the cyberattack on October 21. Both HealthAlliance Hospital and Margaretville Hospital remained open but were forced to divert patients.
How It Could Affect Your Customers’ Business: Medical centers cannot afford disruptions like this that can impact patient care.
Kaseya to the Rescue: See how the solutions in Kaseya’s Security Suite help IT professionals minimize risk, avoid cyberattacks and build a cyber-savvy workforce. WATCH THE WEBINAR>>
Clark County School District (CCSD)
Exploit: Ransomware
Clark County School District (CCSD): Education System






Risk to Business: 1.603 = Severe
The fifth-largest school system in the U.S. Clark County School District is in hot water after suffering a massive data breach as the result of a ransomware attack. October 5, 2023, Clark County School District said that it became aware of a cybersecurity incident impacting its email environment on October 5. In a strange twist, parents of CCSD students received emails from the perpetrators, who identified themselves as SingularityMD, informing them that their child’s data had been compromised. The letters included PDF files with stolen data, including student photos, email addresses and student ID numbers. The school system confirmed that it experienced a data breach, saying that some student data had been snatched by hackers in the incident.
How It Could Affect Your Customers’ Business: Contacting parents directly after a ransomware attack on a school is an alarming development.
Kaseya to the Rescue: What cyberattacks are the most popular this year, and what should you be preparing for in 2024? This webinar tells you everything. WATCH WEBINAR>>
Stanford University
https://www.databreaches.net/stanford-university-investigating-cybersecurity-incident/
Exploit: Ransomware
Stanford University: Institution of Higher Learning



Risk to Business: 2.740 = Moderate
The Akira ransomware group has claimed responsibility for a cyberattack on Stanford University within the network of the school’s Department of Public Safety. The threat actors claimed to have stolen 430 GB of data. The university was quick to reassure the public that the attack did not impact the campus police’s ability to respond to emergencies. No specifics were available about the types of data stolen or any ransom demand at press time.
How It Could Affect Your Customers’ Business: Educational institutions at every level have been experiencing elevated cyberthreat levels.
Kaseya to the Rescue: Explore how security awareness training helps organizations defend against today’s most dangerous cyber threats in this infographic. DOWNLOAD IT>>


See the path from a cyberattack to a defensive success with managed SOC in this infographic. GET IT>>


TransForm
Exploit: Hacking
TransForm: Healthcare IT Services Provider






Risk to Business: 1.673 = Severe
Healthcare specialty IT service provider TransForm experienced a cyberattack that disrupted operations at five Canadian hospitals last week. The impacted healthcare facilities included Windsor Regional Hospital, Hotel Dieu Grace, Chatham-Kent Health Alliance, Erie Shores Healthcare and Hospice of Windsor-Essex. Patients were instructed to defer their scheduled appointments as a result of the incident. The company said that there has been no evidence so far that any patient data compromise.
How it Could Affect Your Customers’ Business: Supply chain and third-party risk have ballooned for businesses and it can have devastating results for a company’s customers and partners.
Kaseya to the Rescue: In The Comprehensive Guide to Third Party and Supply Chain Risk, you’ll learn how these risks emerge and what you can do to mitigate them. DOWNLOAD IT>>
Toronto Public Library
https://www.itworldcanada.com/article/toronto-public-library-hit-by-cyber-attack/550985
Exploit: Hacking
Toronto Public Library: Library System






Risk to Business: 1.612 = Severe
The Toronto Public Library, the largest library system in Canada, has fallen victim to a cyberattack. All of the library system’s 100 locations remained open, but the publicly available computers and printing services at every branch were rendered unavailable. Users’ online accounts and the library’s digital collections were also knocked out. Library officials said that the attack began last Saturday. Officials said the library system is working with third-party forensics experts to investigate the attack.
How it Could Affect Your Customers’ Business: Cyberattacks are growing more frequent for institutions in every sector, not just businesses.
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET THE FACT SHEET>>


What cybercriminal tricks do employees fall for in phishing simulations? Find out in this infographic. GET IT>>


Chile – Grupo GTD
Exploit: Ransomware
Grupo GTD: Telecommunications Company






Risk to Business: 2.002 = Severe
Grupo GTD has experienced a cyberattack that has impacted its Infrastructure as a Service (IaaS) platform, disrupting online services. The attack occurred on October 2, and it impacted numerous services, including its data centers, its OTT television system, internet access and Voice-over-IP (VoIP) services. Grupo GTD also said that some public services experienced website outages. The incident is under investigation.
How it Could Affect Your Customers’ Business: Major operational disruptions like this one are disastrous for companies and can have lasting repercussions.
Kaseya to the Rescue: This checklist can help businesses determine if they’re making all the right moves to prevent email-based cyberattacks. DOWNLOAD IT>>


This infographic helps IT professionals get the most out of a security awareness training solution. DOWNLOAD IT>>


Japan – Seiko
Exploit: Ransomware
D-Link: Network Hardware Manufacturer



Risk to Business: 2.716 = Moderate
Major Japanese watchmaker Seiko has admitted that the company suffered a data breach caused by a ransomware attack by the ALPHV/Black Cat ransomware group. The company confirmed that nearly 60,000 items of personal data had been snatched from the systems of several of its business units. Some of the stolen data belonged to consumers who bought from Seiko Watch Corporation. Another tranche belonged to business partners of Seiko Watch Corporation, Seiko Group Corporation and Seiko Instruments Incorporated. Some employee data and job seeker data from employees of Seiko Group Corporation was also stolen.
How it Could Affect Your Customers’ Business: Customers are not bullish on companies that fail to protect their personal data.
Kaseya to the Rescue: See how security awareness training helps keep cybersecurity threats from becoming cybersecurity disasters. DOWNLOAD INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>




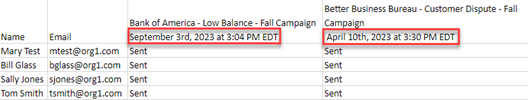
BullPhish ID’s new feature makes timelining training a snap
Now BullPhish ID’s user reports give IT professionals even more information. Each campaign’s start date and time are now conveyed in the phishing and training user reports. The start date and time appear after the phishing kit name/training course and the campaign name.
Also, the campaign’s start date and time indicate the time zone selected when the campaign was created. The time zone is abbreviated (e.g., PST) if an abbreviation exists. If there is not an abbreviation, the full name of the time zone is displayed.



How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


Download The Comprehensive Guide to Third-party and Supply Chain Risk
An attack on a business service provider or supplier can enable bad actors to steal not only data from the victim company but their clients too. It can also provide bad actors a back door into the victim’s clients’ network, enabling them to do damage like deploying ransomware. In this guide, you’ll learn:
- What supply chain risk looks like
- How third-party risk works
- Steps to take to mitigate a company’s risk
Did you miss…The 10 Things to Look for When Buying an EDR Solution Checklist? DOWNLOAD IT>>


Find out how Datto EDR helps with Health Insurance Portability and Accountability Act (HIPAA) compliance. GET INFO>>




9 Tips for Mitigating IoT Risk
In an era where the internet has permeated nearly every aspect of our lives, the Internet of Things (IoT) has emerged as a major change in the way we live and work. This groundbreaking technology connects devices and systems in a new and exciting way. Who doesn’t love not having to get up to turn off the lights or checking in to see what your dog is doing during the day? From smart thermostats and wearable fitness trackers to autonomous vehicles and industrial machinery, IoT technology is everywhere now. However, this digital revolution comes with its own set of challenges and risks, raising questions about security, privacy and reliability.


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>
The IoT boom is a double-edged sword
The rise of IoT has been swift. According to Statista, the number of IoT devices is expected to reach a staggering 75 billion by 2025. These interconnected devices have the power to improve efficiency, enhance convenience and even save lives. For instance, in the healthcare sector, IoT devices can continuously monitor patients’ vital signs, providing instant alerts in the event of an emergency. In agriculture, IoT can optimize resource usage by collecting data on soil quality and weather conditions. Internet-enabled devices are becoming essential in many sectors.
However, the convenience of this new technology comes at a price. IoT devices can open them up to cyber risk. IoT devices in the office can create security vulnerabilities that can be devastating if they’re not addressed. In the work-from-home era, employees are logging in to their company’s systems on the same Wi-Fi network as their fitness tracker, bringing the danger presented by personal IoT devices right to their employer’s door. Smart buildings, medical devices, networking equipment and VoIP phones represent the riskiest IoT device groups for businesses.


Learn how Datto EDR satisfies cyber insurance requirements for endpoint protection & EDR. DOWNLOAD REPORT>>
Security concerns loom large
One of the most pressing challenges associated with IoT is the ever-present specter of security breaches. As more devices become interconnected, the attack surface for cybercriminals grows. Vulnerabilities in IoT devices can open the door to malicious actors who can compromise data privacy, steal sensitive information or even launch destructive attacks on critical infrastructure. Researchers have recorded a more than 400% rise in IoT-related malware incidents year-over-year.
It’s important to remember that IoT devices aren’t just personal things like an Alexa device. Operational Technology (OT) and equipment used to conduct business, like 3D printers, industrial control systems and payment terminals are also IoT devices. Equipment like that sends signals over digital networks just like a smartwatch. In today’s high supply chain risk atmosphere, bad actors are increasingly setting their sights on manufacturers and other forms of industrial technology. Researchers determined that the manufacturing sector now sees an average of 6,000 IoT malware attacks every week, and those attacks can have a serious impact on OT processes even if they don’t land successfully.


Get the scoop on 5 of the worst email-based attacks plus tips to protect businesses from them. GET INFOGRAPHIC>>
IoT devices also create data privacy risk
Another major concern tied to IoT devices revolves around data privacy. IoT devices often collect a vast amount of data, ranging from personal information to usage patterns. That trove of data is highly valuable to both companies and attackers. Unauthorized access to this wide variety of data can enable bad actors to conduct many different malicious operations like identity theft or blackmail. To make matters worse, many IoT devices do not come equipped with robust data protection measures.
The risk of data breaches can be exacerbated by weak encryption or a lack of user awareness regarding data sharing practices. As consumers increasingly adopt IoT devices, it is crucial that they are educated about data privacy issues and empowered to control how their data is collected and shared. It’s also extremely important that companies consider their risk exposure due to IoT devices and take action to mitigate that risk immediately.


Learn how managed SOC gives you big security expertise on call 24/7without the big price tag. LEARN MORE>>
9 tips for mitigating IoT risk
While the risks associated with IoT are substantial, there are proactive strategies and best practices that organizations can employ to mitigate these risks:
Security by Design: Manufacturers should prioritize security during the development of IoT devices. This means implementing strong encryption, secure authentication, and regularly updating firmware to patch vulnerabilities. The use of unique default passwords and mandatory password changes upon device setup can also deter attackers.
Regular Updates and Patch Management: Device manufacturers should provide timely and consistent updates and patches to address security vulnerabilities. Users must be made aware of the importance of keeping their devices up to date and be provided with an easy way to do so.
Network Segmentation: For businesses and individuals with extensive IoT deployments, segmenting IoT devices from critical network infrastructure can minimize the impact of potential breaches. This isolation can prevent unauthorized access to sensitive systems.
Data Encryption and Privacy Controls: IoT devices should employ strong encryption for data transmission and storage. Users should also be given granular control over what data their devices collect and share, ensuring their privacy is respected.


Learn more about how the Kaseya Security Suite helps MSPs & their customers thrive in a dangerous world. GET BRIEF>>
User Education: Consumers should be educated on the importance of securing their IoT devices. This includes regularly changing default passwords, understanding privacy settings, and practicing good cybersecurity hygiene.
Regulatory Frameworks: Governments and regulatory bodies should develop and enforce IoT security standards. These standards should address security, privacy, and reliability across different sectors, providing a framework for manufacturers to follow.
Monitoring and Incident Response: Implementing continuous monitoring and robust incident response plans can help detect and mitigate threats early. Timely responses to breaches can reduce the potential damage and data loss.
Redundancy and Fail-Safe Measures: In critical applications, redundancy and fail-safe mechanisms should be integrated to ensure system resilience. These measures can prevent catastrophic failures if an IoT device or network component malfunctions.
Collaboration and Information Sharing: Private and public sectors should collaborate to share threat intelligence and best practices. Understanding evolving threats and sharing knowledge can help the IoT community stay one step ahead of malicious actors.


See why EDR is the perfect investment to make in your future right now in our buyer’s guide. DOWNLOAD IT>>
Kaseya’s Security Suite provides essential tools for mitigating cyber risk
Kaseya’s Security Suite equips IT professionals to mitigate IoT and other types of cyber risk quickly and affordably while ensuring that they’re ready for the risks of tomorrow.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents employee mistakes and reduces a company’s risk of being hit by a cyberattack.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection around with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
Graphus — Automated email security is a cutting-edge solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
Kaseya Managed SOC powered by RocketCyber — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).
Vonahi Penetration Testing – How sturdy are your cyber defenses? Do you have dangerous vulnerabilities? Find out with vPenTest, a SaaS platform that makes getting the best network penetration test easy and affordable for internal IT teams.


Follow the path to see how Managed SOC heroically defends businesses from cyberattacks. GET INFOGRAPHIC>>


Cybersecurity Jeopardy
November 8 | 1 PM ET / 10 AM PT
Join Us for Cybersecurity Trivia and Prizes!
Are you ready to brush up on your cybersecurity knowledge with experts? Don’t miss the thrilling competition you know and love, with fresh surprises and new opportunities for you to win big! Secure your spot now and register for the ultimate cybersecurity showdown – it’s time to play Cybersecurity Jeopardy! REGISTER NOW>>
November 2: Kaseya + Datto Connect Local New York REGISTER NOW>>
November 7: Kaseya + Datto Connect Local New York REGISTER NOW>>
November 7: Kaseya + Datto Connect Local London REGISTER NOW>>
November 9: Kaseya + Datto Connect Local Manchester REGISTER NOW>>
November 14: Kaseya + Datto Connect Local Montreal REGISTER NOW>>
November 14 – 16: Kaseya DattoCon APAC REGISTER NOW>>
November 16: Kaseya + Datto Connect Local Pittsburgh REGISTER NOW>>
November 30: Kaseya + Datto Connect Local Long Beach REGISTER NOW>>
December 5: Kaseya + Datto Connect Local Orlando REGISTER NOW>>
December 7: Kaseya + Datto Connect Local Symposium Miami REGISTER NOW>>
December 12: Kaseya + Datto Connect Local Arlington TX (Dallas Area) REGISTER NOW>>
December 14: Kaseya + Datto Connect Local New Orleans REGISTER NOW>>
December 19: Kaseya + Datto Connect Local St. Petersburg, FL REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!