2 Factors Make Data Breaches More Expensive

These Two Factors Raise the Cost of a Data Breach
No organization wants to face a cybersecurity incident that ends in a data breach. The newly released IBM Cost of a Data Breach 2022 report offers a clear picture of just how expensive and damaging an incident like that can be. The cost of a data breach has reached a new high, clocking in at $4.35 million this year, an increase of 2.6% over the cost of a data breach in 2021, a record-setting (at the time) $4.2 million per incident. This surge also represents a major jump in the cost of a breach in a two-year span, up 12.7% from 2020’s $3.86 million, illustrating the constantly rising danger of a data security incident to businesses. However, a few factors can impact that cost, making the picture more complicated.

See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>
Human Error Still Tops the Chart of Data Breach Causes
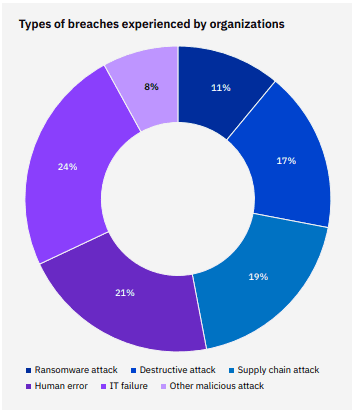
Looking at the breakdown of the types of breaches that organizations experienced, human error remained the top cause of a breach, the cause of just under one-quarter of the breaches analyzed in this report. Ransomware was responsible for 11% of breaches, while destructive attacks were responsible for 17% of breaches. Another 19% of breaches were caused by supply chain attacks, which were breaches caused due to a business partner being initially compromised. There was good news this year about the average mean time that it takes for companies to discover a breach, which has dropped by 3.5% from 287 days in 2021 to 277 days in 2022, a decrease of 10 days. But that doesn’t apply in the case of a successful ransomware attack. A breach caused by ransomware takes 49 days longer to identify and contain than the average data breach.
Source: IBM

Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>
These Two Factors Complicate the Cost of a Data Breach
These two factors add a major increase to the cost of a data breach. Exploring them can help IT professionals gain insight into the data breach landscape.
1. Ransomware & Other Destructive Attacks
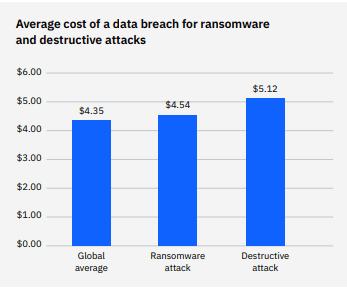
Compared to last year, ransomware breach costs have declined slightly, from $4.62 million to $4.54 million. However, the frequency of ransomware breaches has increased. Ransomware was at the root of 7.8% of breaches in the 2021 report, jumping to 11% in the 2022 study. The average cost of a destructive or wiper attack was $5.12 million, a difference of 16.3%. Digging a little deeper, 11% of breaches in the study were ransomware attacks, an increase from 2021, when 7.8% of breaches were ransomware, for a growth rate of 41%. The average cost of a ransomware attack also dipped slightly, from $4.62 million in 2021 to $4.54 million in 2022. However, ransomware is still slightly more expensive than other data breaches even without factoring in any ransom payment made.
Source: IBM

A Ransomware-Related Breach Takes Longer to Identify and Mitigate Than an Average Breach
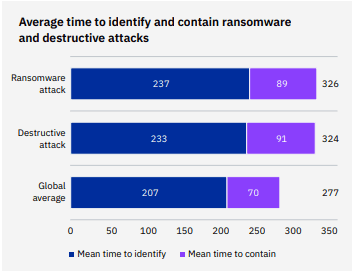
Ransomware and other destructive attacks make it much harder for businesses to handle a data security incident if they fall victim to a cyberattack. The average time to identify and contain a ransomware attack or other destructive attack was significantly higher than the identification and containment time on another kind of data security breach. Researchers determined that a ransomware attack took the businesses that they studied 237 days to identify and 89 days to contain, for a total lifecycle of 326 days. Compared to the overall average lifecycle of 277 days, organizations took 49 days longer to identify and contain a ransomware attack, a difference of 16.3%.
After all, the more time the bad guys have to hang around, the more damage they can do, so a longer dwell time is never a good thing. The average length of time that attackers spend within a victim company’s network before an attack is discovered is called the median dwell time, and that number is rapidly shrinking. In the case of another type of destructive attack, researchers determined that companies took 233 days to identify and 91 days to contain a breach, for a total lifecycle of 324 days. Additionally, organizations took 47 days longer to identify and contain a destructive attack, a difference of 15.6%.
Source: IBM

Be the hero that defeats a company’s security threats to declare victory over cybercriminals! GET THE GUIDE>>
Does Paying the Ransom Make a Difference in the Cost of a Breach?
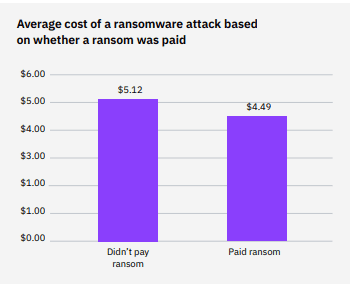
The average cost of a ransomware breach was higher for those that didn’t pay the ransom. The cost of the ransom wasn’t included in the calculation of the cost of a ransomware breach. A ransomware breach’s cost was based on activities, such as detection of the attack and loss of business due to system downtime. For those organizations that didn’t pay the ransom, the average cost of the breach was $5.12 million. For organizations that did pay the ransom, the cost of the breach was $4.49 million. The difference in average cost was $0.63 million, or 13.1%
Source: IBM

The Guide to Reducing Insider Risk can help IT pros stop security incidents before they start! GET IT>>
3. Supply Chain Danger
This is the first year that this report included specific data about supply chain data compromises thanks to a surge in supply chain attacks. Researchers determined that an estimated one-fifth of breaches were caused by a supply chain compromise or about 20% of the breaches that they analyzed. Breaches that resulted from supply chain compromises were also more expensive. The average total cost of a supply chain compromise is $4.46 million, 11 million or 2.5% higher than the average cost of a data breach. Plus, breaches due to supply chain compromises are harder to detect and mitigate. Organizations took an average of 235 days to identify and 68 days to contain a supply chain compromise, for a total lifecycle of 303 days. That average lifecycle was 26 days longer than the overall average data breach lifecycle of 277 days, a difference of 9%.
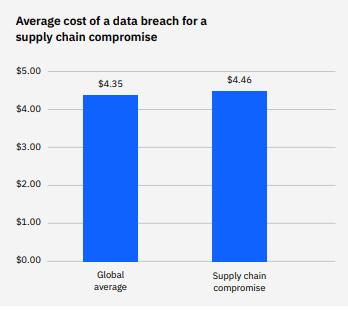
Source: IBM

Get a step-by-step guide to building an effective security and phishing awareness training program. GET GUIDE>>
ID Agent Solutions Help Protect Data & Systems from Danger
No business is ever ready to endure a cyberattack like ransomware or an unpleasant surprise from their supply chain. Reduce the chance of trouble from those sources and mitigate other cyberattack risks with two innovative, powerful and affordable security solutions that you can rely on to keep data and systems safe from cybercrime.
Security Awareness Training
CISA recently recommended that companies step up their security awareness training programs to combat the current flood of ransomware threats. It’s the right move to make – Venture Beat reports that 84% of businesses in a recent survey said that security awareness training has reduced their phishing failure rates, making their employees better at spotting and stopping phishing, the gateway to most of today’s nastiest cyber threats.
BullPhish ID is the perfect solution to use to make that happen!
- A huge library of security and compliance training videos with 4 new lessons added a month!
- Choose from plug-and-play or customizable phishing training campaign kits
- Automation makes training painless for everyone1
Watch Out for Dark Web Danger
Cybercriminals can do a lot with a compromised credential, like steal data and deploy ransomware. Compromised credentials are easy to obtain on the dark web and they open so many doors. An estimated 60% of data breaches involved the improper use of credentials in 2021.
Dark Web ID is the answer.
- 24/7/365 monitoring using real-time, analyst-validated data
- Monitoring of business and personal credentials, including domains, IP addresses and email addresses
- Gain priceless peace of mind about dark web dangers

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!