Are Your Users Anti-Phishing Crusaders?

See How to Empower Your Users to Outsmart the Bad Guys
Did you know that over 90% of data breaches are caused by human error? Yet 45% of employees receive no security awareness training at all from their employer. Worse yet, in our Datto SMB Cybersecurity Survey for MSPs, cybersecurity training was an investment priority for just 43% of our survey respondents, coming in fifth on the list of possible investments in the next 12 months. This is a big mistake. While cybersecurity training can seem costly and time-consuming, especially for lean IT teams with limited budgets, it is absolutely essential to keep businesses safe from cybercrime, and especially phishing-based cyberattacks.
Excerpted in part from our eBook Security Awareness Upgraded: Enter the Simulation DOWNLOAD IT>>
Train employees to become anti-phishing crusaders
To solve this problem, it’s time to take a page out of a different playbook: a comic book. How do superheroes train to fight their most deadly foes (without leveling entire city blocks during the learning process)? With simulated attacks, they can fight in real time. In these simulations, the stakes feel real but don’t do lasting damage. The virtual attackers are automated, and for added utility, the simulation collects data on how well the heroes fought, to suggest what they can improve on for next time. A robust security awareness training program creates a simulation of your own to strengthen your employees’ superhero skills without putting your organization at risk.
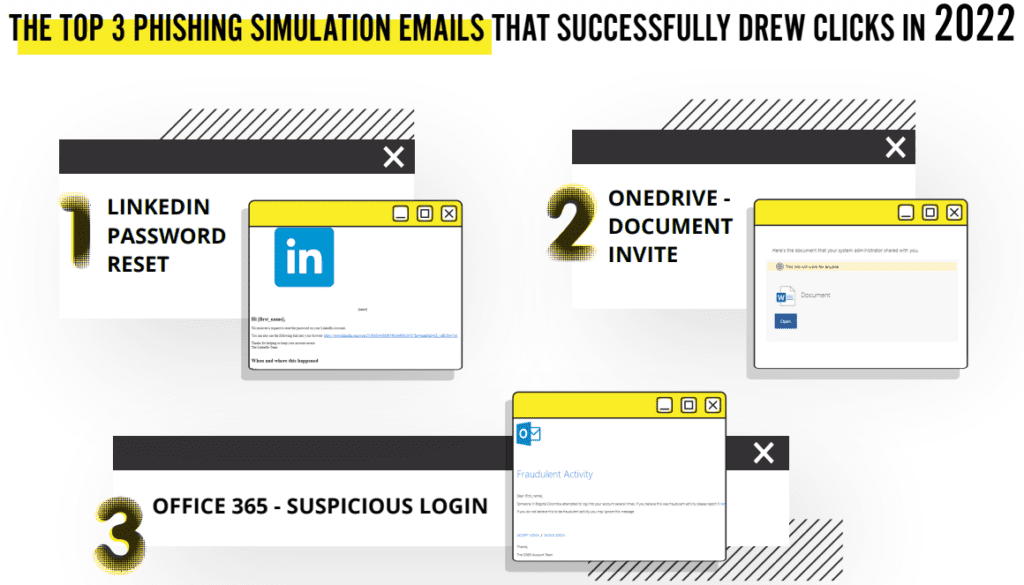
Source: ID Agent

What cybercriminal tricks do employees fall for in phishing simulations? Find out in this infographic. GET IT>>
5 Best practices for a successful phishing simulation
A good simulation is more than just a “gotcha.” It informs, educates and promotes vigilance. Use these five best practices as a guide to creating a more effective simulation:
- Enhance threat recognition and response skills. The simulation should use common phishing “tells” like suspicious email addresses and spoofed domains.
- Demonstrate social engineering techniques. The emotional appeal of a phishing email is what makes it effective. Your simulation should sound urgent and prey on emotion.
- Use tools that are used in your particular business setting. If your organization’s employees use Microsoft 365 or DropBox, the simulation should mimic these tools.
- Reinforce best practices. The post-simulation training should illustrate how best practices can prevent an attack, with follow-up to restate and reinforce them.
- Gathering data for improvement. The results from one simulation should help understand which employees present a risk and need more training and help optimize the next exercise.

See what the biggest cybersecurity challenges are right now in our Mid-Year Cyber Risk Report 2023. DOWNLOAD IT>>
Truth, justice and secure email: why focus on phishing?
A good training simulation focuses on the biggest threats our heroes might face. After all, hours spent chasing virtual muggers won’t prepare a superhero team for a superpowered alien invasion. A comprehensive security awareness training program includes elements like password hygiene and best practices for data privacy and security. However, when it comes to the human element of cybersecurity, phishing is one of the biggest potential vulnerabilities. Unlike a DDoS attack or a virus, phishing preys on human emotions. The only way to harden security against phishing is to educate your employees and inoculate them against falling for these manipulative attacks. Research shows that 1 in 3 employees are likely to click links in phishing emails — and it only takes one misguided click to cause a potentially catastrophic breach.
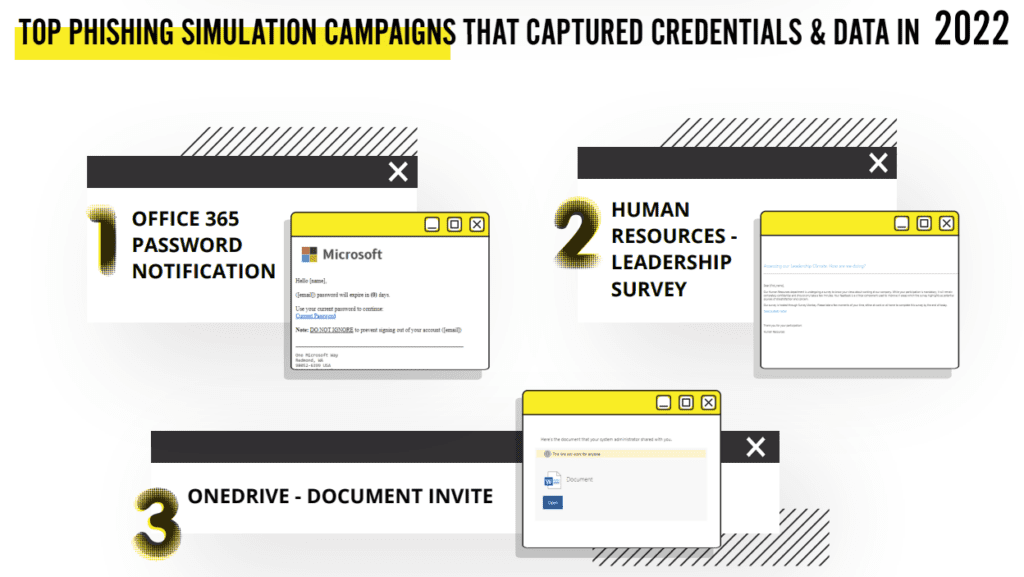
Source: ID Agent

See the path from a cyberattack to a defensive success with managed SOC in this infographic. GET IT>>
Constant threats need constant vigilance
Users are vulnerable to phishing attacks because people are naturally trusting, are unfamiliar with the limitations of the computer and network systems they use, and are unaware of how pervasive the threat is. When we walk through a bad, poorly lit neighborhood at night, we try to be more alert. We might put our wallet in our front pocket or clutch our purse tighter. We are acutely aware of possible threats and our vulnerabilities in those situations. Security awareness training helps to show that when you are online, you are always in a bad neighborhood. A distant country like Russia, home of many hacker groups, is only 130 milliseconds away from the United States via the internet.
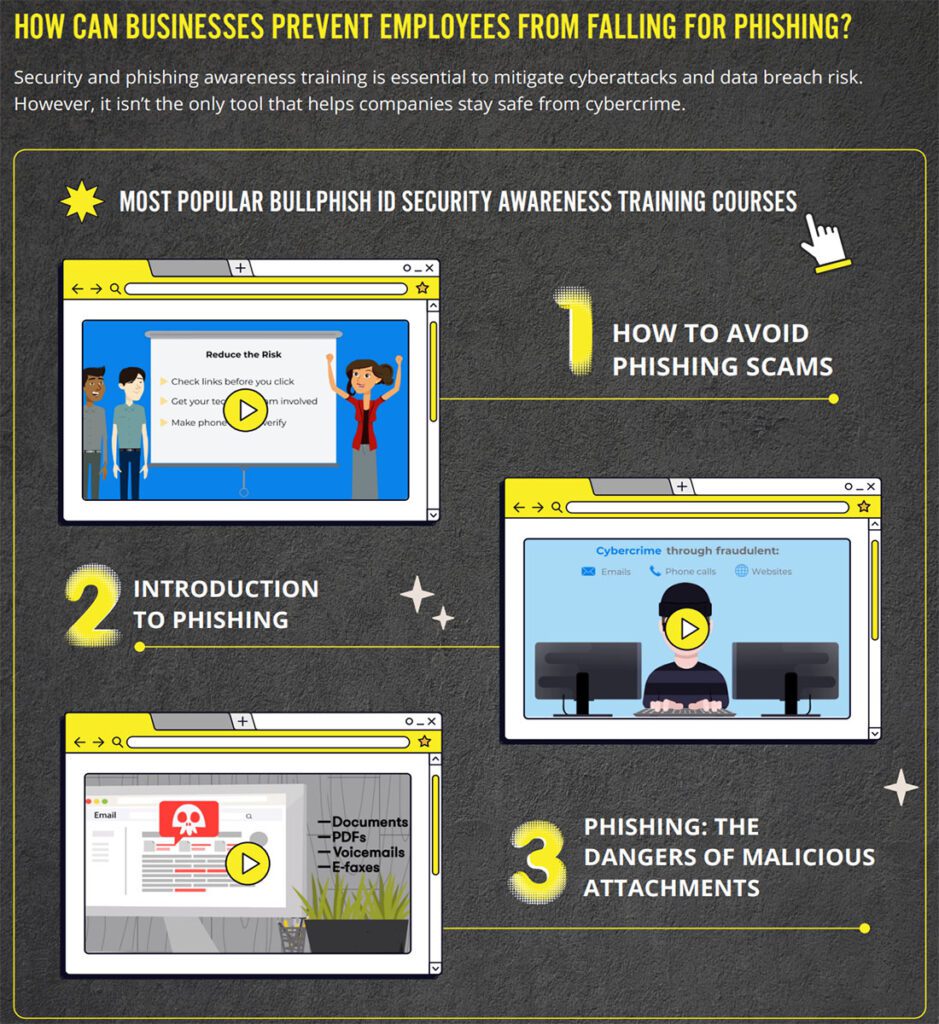
Source: ID Agent

See why EDR is the perfect investment to make in your future right now in our buyer’s guide. DOWNLOAD IT>>
The high cost of a successful phish
When a superhero loses a battle, there’s always heavy damage to handle in the wake of that loss. It’s important to understand what’s at stake in the fight and work to avoid a catastrophic defeat. In IBM’s Cost of a Data Breach 2023, analysts determined that the most common initial attack vector for a data breach is phishing, and the average cost of a phishing-related breach is $4.76 million. But a data breach isn’t all that businesses have to worry about if it’s successfully hit by a phishing attack. That simple phishing attack could be the opening gambit in a devastating ransomware or business email compromise (BEC) attack.
The costs businesses can face after a phishing-related cyberattack can include:
- Money paid to hackers (which may be illegal)
- Downtime and lost productivity
- Regulatory penalties
- Reputational damage
- Lost revenue

See the keys to selecting a Managed SOC to find the perfect one for your clients & your MSP. GET CHECKLIST>>
BullPhish ID is the Ideal Security Training & Simulation Solution
Security awareness training is a low-cost, highly effective way to reduce an organization’s exposure to cyber risk as well as improve compliance. Starting or retooling a security and compliance awareness training program doesn’t have to be complicated or expensive. BullPhish ID makes undertaking security awareness training painless for everyone involved.
Here’s what sets BullPhish ID apart from the competition:
- New training videos with quizzes and fresh phishing kits are added every month to keep training current
- Satisfy requirements for cyber liability insurance purchase or renewal by having strong cybercrime protections — like a user security awareness training program — in place
- Automate training campaigns and reporting for effortless, set-it-and-forget-it training that gets results
- Train your way and on your schedule with plug-and-play phishing simulation kits or customizable content that can be tailored to fit your industry’s unique threats
- Access training in eight languages: English, Dutch, French, German, Italian, Portuguese, Spanish (Iberian/European) and Spanish (Latin)
- Leverage in-lesson quizzes and simple, easy-to-read reports to prove the value of training and know who needs additional support.
- Make training easy and convenient for every employee with a personalized user portal.
- Automatically generate and send reports to stakeholders
Want to learn more about security awareness training and how BullPhish ID can help secure your company and save you money? Explore the benefits of training with BullPhish ID today.
Or, book a demo and see BullPhish ID in action!

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!