MOVEit Exploit Cyberattacks Hit Over 500 Companies

Take a Deep Dive into This Cautionary Tale of Third-Party & Supply Chain Risks
In what will surely be one of the biggest cyberattack stories of 2023, the ransomware attack by Cl0p on MOVEit Transfer has ripped through the business cybersecurity landscape like nothing else. The unfortunate incident serves as the perfect example to showcase just how relentless cybercriminals can be if they find a zero-day exploit or flaws in an organization’s IT architecture. Taking a deep dive into how this vulnerability has impacted over 500 organizations and more than 34 million people can offer insight into protecting businesses against future trouble.

What cybercriminal tricks do employees fall for in phishing simulations? Find out in this infographic. GET IT>>
What is MOVEit?
MOVEit Transfer is an extremely popular managed file transfer (MFT) solution developed by Progress that is built to facilitate automated and secure transfers of sensitive enterprise data. The file transfer service was HIPAA compliant and widely used by organizations in myriad sectors including big names like Shell, Deutsche Bank and the U.S. Department of Energy. Trusted by some of the largest organizations and connected to a global network, MOVEit Transfer was the ideal target for cybercriminals, and the discovery of a zero-day exploit associated with it has been an unmitigated disaster for everyone else.
Many major companies from a variety of sectors are on the MOVEit casualty list. Here’s a sample of some that were added to the list just this week:
- Deloitte
- Chuck E. Cheese
- The Hallmark Channel
- 1st Source Corp
- Estée Lauder

See the path from a cyberattack to a defensive success with managed SOC in this infographic. GET IT>>
How CL0P began the attack on MOVEit
Also known as TA505, Cl0p is an active Ransomware-as-a-Service gang widely suspected to be operating out of Russia. It is a top-tier cybercrime group that specializes in ransomware, and it has been very successful. Cl0p communicates its agendas across dark web forums, using the platform to state its demands and inform the public of its intentions with the data it holds for ransom. And concerning the attack on MOVEit Transfer, the gang claims full responsibility.
The cybercriminal gang breached Progress’s IT environment via a previously unknown SQL injection vulnerability called CVE-2023-34362. TA505 was able to discover a zero-day vulnerability in the MOVEit Transfer solution and consequently exploit it. The vulnerability scored 9.8 out of 10 on the severity rating.
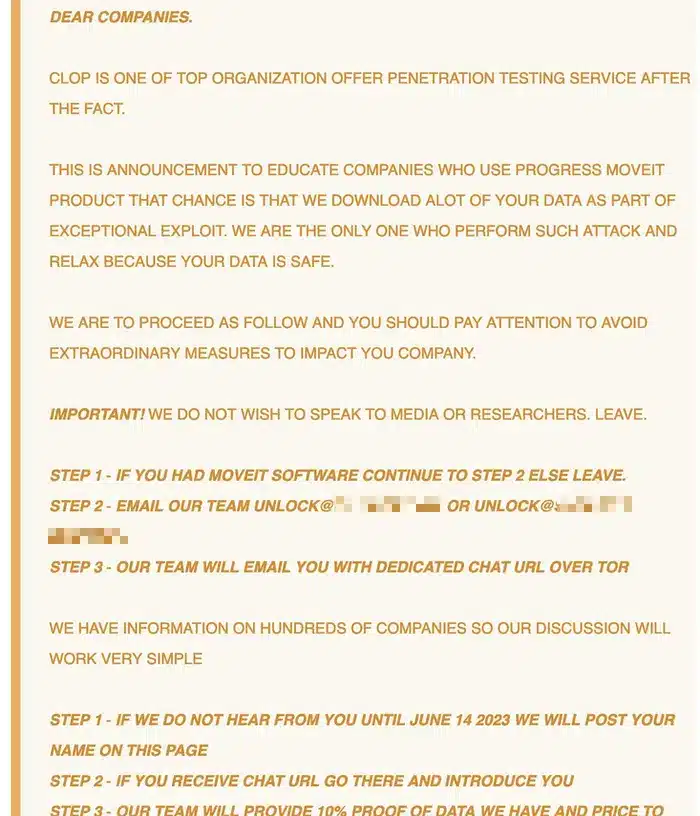
Example of a Cl0p ransom note
Since MOVEit Transfer’s processes heavily rely on the internet, Cl0p was able to infect the software with a malicious script — known as a web shell — named LEMURLOOT. It was used to harvest data from MOVEit Transfer’s databases. It also granted the bad actors unauthorized access to client environments. Cl0p targets companies with high turnover and access to digital supply chain networks. More interestingly, the group often launches their attacks during nationwide holidays.It also adopts a ‘steal, encrypt and leak’ approach to its ransomware attacks. After which, the group promises to delete all the stolen data as soon as its ransom is met. It will not disclose any information on its data leak site, like organization names and private addresses.
A ransomware-related data breach is an expensive nightmare for any organization. According to IBM’s Cost of a Data Breach 2023 report, data breaches disclosed by the attackers, as is typically the case in a ransomware attack, are 16% more expensive than an average data breach, clocking in at an average cost of $5.23 million. As of the time of this report, experts estimate that Cl0p is on the verge of extorting over $75 million from its victims.

Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>
When did the attack start?
There are many reports dating the launch of the attack to the first week of June. However, the actual vulnerability exploit began over Memorial Day weekend, when one of Progress’s customers raised an issue regarding some unusual activity in their MOVEit Transfer application. Progress grew wary of the vulnerability and disclosed it, strongly urging all MOVEit Transfer users to take the necessary security precautions immediately. This included conducting comprehensive IT risk assessments across the network to identify data theft and other cyber risks.
Progress believed the issue was resolved after releasing patches for both cloud and on-prem versions of the software but, on June 1, the U.S. government and several cybersecurity researchers raised a few alarms concerning the security flaw. The Cybersecurity and Infrastructure Security Agency (CISA) quickly added the vulnerability to its Known Exploited Vulnerabilities Catalog and stated that such “vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.”

See why EDR is the perfect investment to make in your future right now in our buyer’s guide. DOWNLOAD IT>>
Sevice providers were early targets
By June 5, the MOVEit hack had gained international renown. Zellis, a payroll and HR solutions company based out of the United Kingdom, was at the heart of one of the early instances of the vulnerability being exploited at a service provider. Zellis works with numerous Financial Times Stock Exchange (FTSE) 100 companies and maintains access to the financial and personally identifiable information (PII) of thousands of employees within each client organization. Cl0p leaked information like employee names, dates of birth, home addresses, salaries, and worst of all, banking information.
Cl0p was able to exploit Zellis’s huge supply chain network, which includes companies like the BBC and British Airways. While these two companies have confirmed that their employee data was leaked, more of Zellis’s clients, like Jaguar Land Rover and Dyson, are suspected of having suffered privacy breaches as well. A successful attack like this one on a service provider can have an ongoing cascade effect.

Find out how Datto EDR helps with Health Insurance Portability and Accountability Act (HIPAA) compliance. GET INFO>>
Other organizations were quickly caught in Cl0p’s net
The MOVEit Transfer attack highlights the very real danger of supply chain and third-party risks when it comes to managing cybersecurity. For instance, the Teachers Insurance and Annuity Association of America (TIAA) was also breached, which further enabled Cl0p to creep into over 30 colleges and universities across the U.S. including Trinity College and Middlebury College, who ultimately confirmed that their employee data in TIAA’s possession had been leaked.
The Minnesota Education Department has stated that hackers accessed 24 files that contained the names, dates of birth and county of placement of nearly 95,000 students in the foster care system. Students from other institutions also had details of their parents and social security numbers exposed as well.

Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>
How companies are handling the threat
Cl0p set a very short deadline for all its victims (July 16) to pay the ransom. Since then, it has consistently been disclosing company and employee information on its dark web data leak site, creating quite a stir in the business world and attracting fresh attention from regulatory authorities and cybersecurity professionals.
Agencies like The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the U.S. Federal Bureau of Investigation (FBI) initially offered a $10 million reward for any information that would help take the ransomware gang down but to no avail. The reward is still up for grabs.
A handful of victims paid Cl0p to delete their data, but many companies followed the recommended guidance from experts and did not pay the extortionists. Ofcom, for instance, said they had been advised by the Nation Cyber Security Centre (NCSC) to not make any payments. ComReg, Ireland’s communications regulator, has not made any comments regarding the same. However, it’s interesting to note that both these agencies have been removed from the leak site. No one has any clear answers as to how or why this happened.
The affected businesses are scrambling to get back on their feet and most are working with their respective governments and private cybersecurity agencies to investigate and remediate the incident. Considering that the number of organizations willing to pay a ransom is declining, as is the case with all ransomware attacks, the MOVEit Transfer vulnerability attack may hopefully be on its last legs, although more victims will undoubtedly emerge in the next few months.

Get the scoop on 5 of the worst email-based attacks plus tips to protect businesses from them. GET INFOGRAPHIC>>
Kaseya’s Security Suite helps protect businesses from sophisticated cyberthreats
Ransomware attacks cannot be taken lightly because all it takes is one slip-up from you or a third-party vendor to set off a domino effect that affects every organization in the supply chain. Today’s sophisticated threats call for a layered, defense-in-depth cybersecurity approach. Get powerful protection and must-have tools for keeping businesses out of cybersecurity trouble with Kaseya’s Security Suite.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection with 24/7/365 human- and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents cyberattacks and reduces an organization’s chance of experiencing a cybersecurity disaster by up to 70%.
Graphus — Graphus is a cutting-edge, automated email security solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
Kaseya Managed SOC powered by RocketCyber — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require.
Book your demo of our security suite solutions today!

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!