The Week in Breach News: 01/24/24 – 01/30/24

This week: Ransomware floods two water utilities, HPE gets hit by Russian threat actors, a rare happy ending for a business email compromise (BEC) story and a deep dive into whether it is a financially sound idea for a managed services provider (MSP) to set up their own Security Operations Center (SOC).

See the challenges companies face & how they’re overcoming them in our Kaseya Security Survey Report 2023 DOWNLOAD IT>>

The GALA Hispanic Theatre
https://therecord.media/washington-dc-theater-whole-again-hack
Exploit: Business Email Compromise
The GALA Hispanic Theatre: Theater

Risk to Business: 1.437 = Extreme
In a rare happy outcome for a business email compromise (BEC) story, The GALA Hispanic Theatre in Washington, DC is breathing a sigh of relief. The theater experienced a business email compromise attack that cost them more than $250,000. The January 11 attack kicked off a nightmare after the certified accountant for the theater initiated a standard wire transfer of $965 to a set designer for an upcoming show. When the transaction completed, a screen popped up telling them that they’d been locked out of their account. Bad actors then drained the theater’s CitiBank account. The transfer went to a Bank of America account belonging to a fake company called Infinity Source LLC. After filing complaints with Citi and Bank of America, the theater began working with law enforcement. The theater also launched a whirlwind fundraising effort to ensure that it was still able to stage its upcoming show, raising $70k. Fortunately, the theatre received a much more pleasant surprise – CitiBank informed them that the $255,000 stolen from their account would be returned to them by the bank.
How It Could Affect Your Customers’ Business: It’s incredibly unusual for a BEC story to have a fairytale ending, and companies need to be ready for trouble.
Kaseya to the Rescue: Get practical information about mitigating BEC in The Comprehensive Guide to Business Email Compromise. DOWNLOAD THE EBOOK>>
Hewlett Packard Enterprise (HPE)
https://thehackernews.com/2024/01/tech-giant-hp-enterprise-hacked-by.html
Exploit: Hacking
Hewlett Packard Enterprise (HPE): Technology Company






Risk to Business: 1.691 = Severe
A Russian state-sponsored group known as APT29 (AKA BlueBravo, Cloaked Ursa, Cozy Bear, Midnight Blizzard/ Nobelium) is thought to be behind an intrusion into Hewlett Packard Enterprise (HPE). This is the same group that recently hit Microsoft. The threat actors gained access to HPE’s cloud email environment to exfiltrate mailbox data. HPE said the threat actor exfiltrated data from some mailboxes belonging to employees in their cybersecurity, go-to-market and business segments. HPE said it was notified of the incident on December 12, 2023. HPE also said the incident has not had any material impact on its operations. HPE has not commented on the specifics of the email information that was accessed.
How It Could Affect Your Customers’ Business: Government-aligned threat actors are incredibly dangerous and capable of extremely sophisticated hacking.
Kaseya to the Rescue: See how security awareness training helps keep cybersecurity threats from becoming cybersecurity disasters. DOWNLOAD INFOGRAPHIC>>
Veolia North America
Exploit: Ransomware
Veolia North America: Water Technology






Risk to Business: 1.643 = Severe
Water technology provider Veolia North America has disclosed that it fell victim to a ransomware attack. The company said that the attack impacted systems in its Municipal Water division and disrupted its bill payment systems. Veolia said that it had immediately implemented defensive measures, temporarily taking some systems offline to contain the breach. The company said that its back-end systems and servers are now back online and customers’ payments will not be affected. Water and wastewater treatment operations weren’t interrupted. Veolia said that a limited number of individuals may have had their personal information exposed in the breach.
How It Could Affect Your Customers’ Business: Cybercriminals have been constantly increasing the pressure on utility companies, endangering the public.
Kaseya to the Rescue: Learn about the growing list of cybersecurity challenges that organizations face in the Kaseya Security Survey Report 2023. DOWNLOAD IT>>
The Government of Bucks County, Pennsylvania
https://therecord.media/local-governments-across-us-dealing-with-ransomware
Exploit: Ransomware
The Government of Bucks County, Pennsylvania: Regional Government



Risk to Business: 1.462 = Extreme
The Government of Bucks County, Pennsylvania is grappling with a cybersecurity incident that has knocked out services and communication systems including the Emergency Communications Department’s computer-aided dispatch (CAD) system. Operators were reduced to using pen and paper to take calls but were still able to respond to emergencies effectively. The system holds a myriad of sensitive data. The Pennsylvania National Guard has been called in to assist. Court proceedings were also snarled because of the incident.
How It Could Affect Your Customers’ Business: A cyberattack on a city or regional government can have dangerous consequences when it impedes the operation of emergency services.
Kaseya to the Rescue: Ransomware is often an email-based cyberattack that can lead to disaster. Our Preventing Email-Based Cyberattacks Checklist helps businesses stay out of trouble. DOWNLOAD IT>>
Jason’s Deli
Exploit: Credential Stuffing
Jason’s Deli: Restaurant Chain






Risk to Business: 1.702 = Severe
Texas-based chain Jason’s Deli has begun informing customers that they have had data exposed in a credential stuffing attack. The restaurant chain says that hackers obtained credentials of member accounts from other sources and used them to conduct a credential stuffing attack on December 21, 2023. A variety of customer data was snatched including a customer’s full name, address (including all saved delivery addresses), phone number, birthday, preferred Jason’s deli location, house account number, deli dollar points, redeemable amounts and rewards, truncated credit card numbers (only the last four digits are visible) and truncated gift card numbers.
How it Could Affect Your Customers’ Business: Credential stuffing is a dark web-fueled cybercriminal favorite that can lead to big trouble for a business.
Kaseya to the Rescue: Learn more about the trade in data and credentials on the dark web and how bad actors make a profit in our infographic 5 Ways the Dark Web Endangers Businesses. DOWNLOAD IT>>


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>


UK – Caravan and Motorhome Club (CAMC)
https://www.theregister.com/2024/01/24/major_it_outage_at_caravan/
Exploit: Hacking
Caravan and Motorhome Club (CAMC): Association


Risk to Business: 2.736 = Moderate
Members of the UK’s Caravan and Motorhome Club (CAMC) aren’t happy campers after a mysterious outage of the group’s website and mobile app. The site and app originally said that they were down for maintenance, but later changed to acknowledge that there was a problem and that external teams were involved in bringing its systems back to working order. The outage has left members unable to book future holidays and disgruntled with CAMC’s customer service. CAMC has more than 1 million members.
How it Could Affect Your Customers’ Business: Members aren’t going to be happy when they can’t use the services an association provides.
Kaseya to the Rescue: An endpoint detection and response solution can help businesses stop the spread of a cyberattack fast. This checklist helps you find the right one. DOWNLOAD IT>>
UK – Southern Water
Exploit: Ransomware
Southern Water: Utility






Risk to Business: 1.736 = Serious
The Black Basta ransomware group has claimed responsibility for an attack on UK utility Southern Water. The private utility company collects and treats wastewater in Hampshire, the Isle of Wight, West Sussex, East Sussex and Kent as well as providing water to many homes in the region. The group claims to have nabbed 750 gigabytes of sensitive data, including users’ personal documents and corporate documents. Black Basta ransomware group added Southern Water to the list of victims on its Tor data leak site, threatening to leak the company’s stolen data on February 29, 2024. It provided scans of passports, ID cards and personal information of some employees as proof of the hack.
How it Could Affect Your Customers’ Business: Infrastructure continues to be a priority target for ransomware groups looking to profit from an industry that cannot afford downtime.
Kaseya to the Rescue: Every organization needs to be ready for trouble with an incident response plan in place. This checklist can help. DOWNLOAD CHECKLIST>>
The Netherlands – Microbe & Lab
https://www.bankinfosecurity.com/medical-lab-database-exposed-13m-records-covid-test-info-a-24168
Exploit: Misconfiguration
Microbe & Lab: Medical Laboratory






Risk to Business: 1.602 = Severe
The unsecured database of a medical lab owned by Microbe & Lab of Amsterdam has resulted in the exposure of patient records, including personal data and COVID test results. The database, which lacked password protection, contained approximately 1.3 million exposed records including 118,441 certificates, 506,663 appointments, 660,173 testing samples and an assortment of proprietary data. The leaked records contain patient names, nationality, passport number and test results, as well as the price, location and type of test conducted.
How it Could Affect Your Customers’ Business: Medical data, including research and laboratory data, is a typically profitable cybercriminal favorite.
Kaseya to the Rescue: Learn how Datto EDR with Ransomware Rollback helps organizations including medical centers recover from ransomware faster. REGISTER NOW>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>




BullPhish ID offers a new option to enforce log in with KaseyaOne
The new “Require Log in with KaseyaOne” feature forces users to log in with their KaseyaOne credentials to access BullPhish ID. When the feature is enabled by an organization, users can no longer log in to BullPhish ID locally with their BullPhish ID credentials.
You can select which users you want to provide an exception to this requirement. The selected users will be able to log in to BullPhish ID with their BullPhish ID credentials while still having the option to log in using the KaseyaOne login method
The Require Log in with KaseyaOne feature is available on the Organizations > Settings page. KaseyaOne Unified Login must be enabled to activate the Require Log in with KaseyaOne feature.
Learn more in the Release Notes. READ IT>>


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


Download the New “How to Use MITRE ATT&CK to Create a Smarter SOC” eBook
A security operations center (SOC) gives defenders a big advantage against cybercrime. But not all SOCs are the same. In this eBook, we’ll show you why a smart SOC that makes the most of automation and is mapped to the MITRE ATT&CK framework is a game changer.
Did you miss: A Comprehensive Guide to Third-Party and Supply Chain Risk? DOWNLOAD IT>>


Learn how managed SOC gives you big security expertise on call 24/7without the big price tag. LEARN MORE>>




MSPs: Should You Build an In-House SOC?
The pressure on managed service providers (MSPs) to deliver the best security services in today’s highly advanced threat landscape continues to build as cybercriminals grow ever more aggressive and successful. That’s why many consider building an in-house security operations center (SOC). However, as attractive as it may seem, the associated costs in attempting to do so can be daunting. This white paper aims to help MSPs by analyzing the total cost of ownership (TCO) of establishing and operating an in-house SOC, highlighting the hidden expenses and complexities involved.
Excerpted in part from: The Cost of Creating a SOC: A Total Cost Analysis DOWNLOAD IT>>
The cost conundrum of an in-house SOC
A SOC is fast becoming a must-have in today’s rapidly evolving cyber threat landscape. However, building and maintaining your own SOC is not simply a matter of acquiring technology. It requires significant investment in:
- Infrastructure: Servers, storage, network devices and security appliances.
- Personnel: Highly skilled security analysts, engineers and managers. Training and skill development: Continuous upskilling for your SOC team.
- Utilities and maintenance: Ongoing upkeep of infrastructure and software.
- Software and tools: SIEM solutions, incident response platforms and threat intelligence feeds.
- Compliance and insurance: Maintaining regulatory and insurance compliance.


Don’t miss the fun & fabulous prizes at Cybersecurity Jeopardy! Next Wednesday, February 7, 1 PM ET/10 AM PT. REGISTER NOW>>
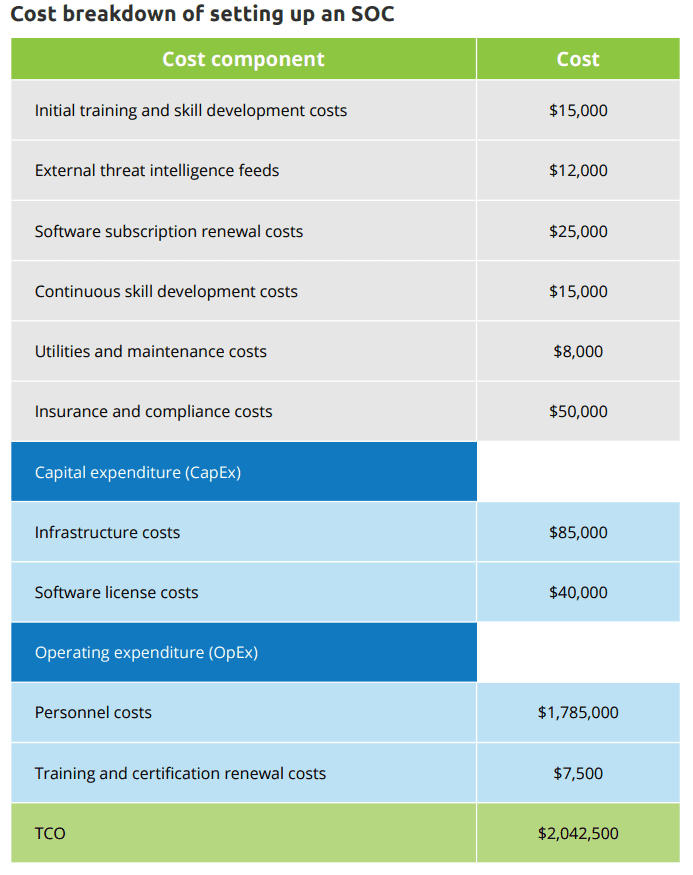
What is the cost breakdown of setting up an in-house SOC?
We’ve mapped out an example of the cost an MSP may be looking at to set up an in-house SOC, and they’re significant. For this analysis, we made the following projections about MSP X.
MSP X:
- Has a client base of 50-100 clients.
- Intends to operate its SOC 24/7/365 with a team of 10 security analysts, two security engineers and one security manager.
- Will use security information and event management (SIEM) and incident response tools from leading vendors.
- Will subscribe to external threat intelligence feeds from multiple sources.
- Manages 4,000 endpoints.



Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>
Don’t overlook the hidden costs of establishing a SOC
The hidden costs of an in-house SOC must also be considered. Beyond the initial CapEx, ongoing OpEx can quickly spiral. Recruiting and retaining skilled cybersecurity professionals is a constant challenge, often leading to higher salaries and benefits. Software subscriptions, training programs and maintenance costs add to the burden. Furthermore, managing an in-house SOC demands significant time and resources, diverting attention from your core MSP services.
Unfortunately for MSPs, the cybersecurity talent shortage makes it very difficult to recruit the talent needed to run a 24/7/365 in-house SOC. Plus, experienced security talent is an expensive addition to the payroll. However, an MSP doesn’t need a big staff with extensive security knowledge to deliver world-class security services to small businesses if it has access to a high-quality managed security operations center (SOC).


Learn how Datto EDR satisfies cyber insurance requirements for endpoint protection & EDR. DOWNLOAD REPORT>>
Don’t miss out on these 5 big benefits of a managed SOC
The advantages of choosing to invest in a managed SOC rather than building your own don’t stop with the dollars and cents. These five benefits are also worth considering:
1. Expert threat detection in real-time
Bad actors never attack when you expect them to. To stay ahead of cyberattacks, a managed SOC is full of security veterans who are on the job 24/7/365, identifying potential threats across the three key attack pillars — endpoint, network and the cloud environment — before they escalate. Our expert cybersecurity analysts receive real-time alerts about suspicious activities, enabling swift response to minimize the impact of cyber risks. Plus, managed SOC combined with EDR is a security game-changer.
2. Automated threat hunting and ransomware detection
A smart managed SOC automatically conducts threat hunting, searching for potential breaches while veteran SOC analysts actively monitor the network in parallel.️ Plus, a constant influx of intelligence managed by experts gives MSPs and advantage against new and evolving threats. Look for a solution that includes automatic ransomware isolation and termination to stop threats quickly.
3. Swift incident response
With a managed SOC, an MSP gains access to a seasoned team of analysts who investigate each alert. In addition, those experts can triage alerts to produce tickets for an MSP’s PSA system, along with remediation details, enabling MSPs to do more without having to hire additional staff. In the event of a cyber incident, a managed SOC provides a swift and coordinated response due to its 24/7/365 operation.
5. Comprehensive security insights
Reliable threat intelligence and security insight is key for keeping businesses out of security trouble. When you choose a managed SOC, you’ll have access to a dashboard that offers you a quick view of where security events are being detected. A quality managed SOC will offer built-in reporting capabilities that make it a snap to send clients and stakeholders a populated executive report on key metrics around security incidents and network activity, proving the worth of the service. Get an even better picture of your clients’ risks and security weaknesses with affordable, automated penetration testing.
5. Augment your IT team effortlessly
The right managed SOC is like an extension to your existing MSP’s IT team, immediately expanding your capabilities to detect and respond to threats around the clock through our cybersecurity veterans. This comes without the financial burdens and complexities of creating your own SOC and with the benefit of enterprise-level expertise. Plus, a managed SOC is easily scaleable to the evolving needs of your business and clients.


RocketCyber Managed SOC is the smart choice
RocketCyber Managed SOC is the perfect cost-effective alternative to building your own SOC to significantly boost your security service capabilities. RocketCyber is the smarter managed SOC option, enabling you to go beyond just safeguarding your MSP and your clients. You’ll have the tools and expertise that you need to proactively tackle cyber threats. Plus, you will benefit from instantly augmenting your IT team and solidifying your MSP’s services portfolio with RocketCyber’s Managed SOC.
It all starts with the multi-tenant cloud architecture fueled with integrated threat intelligence, a built-in app store with purpose-built threat detection apps, providing 24/7 threat monitoring and visibility across 3 attack pillars: endpoint, network and cloud.
What does RocketCyber Managed SOC bring to the table?
- 24/7 Continuous Monitoring: Always on threat detection in real-time with security expertise at your fingertips.
- An Enhanced Security Stack: RocketCyber is the developer of all technologies leveraged in our default SOC Platform configuration
- No Hardware Requirement: Our SOC is powered by the RocketCyber Cloud Platform requiring no hardware!
Book a demo of RocketCyber Managed SOC today! BOOK A DEMO>>


In The Educator’s Guide to Cybersecurity, see the cyber threats that schools face & how to mitigate them. DOWNLOAD IT>>


February 6: Kaseya + Datto Connect Local Houston REGISTER NOW>>
February 7: Cybersecurity Jeopardy! REGISTER NOW>>
February 8: Kaseya + Datto Connect Local Dallas REGISTER NOW>>
February 20: Kaseya + Datto Connect Local Atlanta REGISTER NOW>>
February 22: Kaseya + Datto Connect Local Tampa REGISTER NOW>>
April 29 – May 2: Kaseya Connect Global (Las Vegas) REGISTER NOW>>
June 11 – 13: Kaseya DattoCon Europe (Dublin) REGISTER NOW>>
October 28 – 30: Kaseya DattoCon (Miami) REGISTER NOW>>
November 12 – 14: Kaseya DattoCon APAC (Sydney) REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!