The Week in Breach News: 06/01/22 – 06/07/22

Ransomware hits Foxconn, more cyberattack trouble for governments around the world and data about the results of a year’s worth of phishing simulations in The Global Year in Breach 2022.

See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>

City of Portland, OR
https://therecord.media/cybercriminal-scams-city-of-portland-ore-for-1-4-million/
Exploit: Business Email Compromise
City of Portland, OR: Municipal Government

Risk to Business: 1.726 = Severe
Bad actors struck the city of Portland, Oregon in an audacious business email compromise attack that resulted in a $1.4 million fraudulent transaction with city funds in April. City officials say that cybercriminals obtained the money after gaining access to a city email account illegally. The compromise was detected in May when the same account attempted another transfer of funds. The incident is under investigation by the FBI, U.S. Secret Service and the Portland Police Bureau.
How It Could Affect Your Customers’ Business: From municipalities to major national agencies, government targets have been a favorite of cybercriminals in the last few years.
ID Agent to the Rescue: A strong security culture reduces the risk of an incident. Help your clients build one with The Building a Strong Security Culture Checklist! DOWNLOAD IT>>
City of Alexandria, LA
https://therecord.media/louisiana-authorities-investigating-ransomware-attack-on-city-of-alexandria/
Exploit: Ransomware
City of Alexandria, LA – Municipal Government




Risk to Business: 2.733 = Moderate
The AlphV ransomware gang has added the city of Alexandria, Louisiana to its list of victims. Officials confirmed that the city of 50,000 had fallen victim to a ransomware attack. They don’t believe that any sensitive data was stolen, and city operations will proceed as normal. This is the 22nd reported incident affecting a local government in the U.S. this year.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business Governments have been high on the cybercriminal’s shopping list since they tend to have big data stores.
ID Agent to the Rescue: Learn to mitigate your clients’ ransomware risk and protect them from trouble with the resources in our Deep Dive Into Ransomware bundle! GET BUNDLE>>


Get 10 tips to help you build a strong security culture & reduce your risk of cybersecurity trouble! GET INFOGRAPHIC>>

Mexico – Foxconn
https://www.securityweek.com/ransomware-group-claims-have-breached-foxconn-factory
Exploit: Ransomware
Foxconn: Electronics Manufacturing


Risk to Business: 1.349 = Extreme
A major factory for Foxconn located in Tiajuana, Mexico near the California border was hit by a ransomware attack in late May that resulted in a shutdown. The plant specializes in the production of medical devices, consumer electronics and industrial operations. The operators of LockBit have claimed responsibility for the attack.
How It Could Affect Your Customers’ Business: Manufacturers have been popular targets for cybercriminals, ranking number one for ransomware attacks in 2021.
ID Agent to the Rescue: Find and slay dastardly vulnerabilities in your clients’ security strategy and emerge victorious with The Cybersecurity Monster Hunter’s Checklist! GET IT>>
Costa Rica – Costa Rican Social Security Fund (CCSS)
Exploit: Ransomware
Costa Rican Social Security Fund (CCSS): Government Agency







Risk to Business: 1.872 = Severe
The Costa Rican Social Security Fund (CCSS)was forced to shut down its digital record-keeping system last week due to a ransomware attack, affecting some 1,200 hospitals and clinics. Officials say that 30 of 1500 of its servers were impacted and they saw no evidence that a critical database or system was compromised. For weeks, Costa Rica has been under siege by ransomware, with a parade of government agencies taking big hits.
How it Could Affect Your Customers’ Business: Costa Rica has been continually having problems with cyberattacks to the point that it is having an effect on the government’s stability.
ID Agent to the Rescue: Make sure you’re offering your clients the right protection against dark web risks like this with The Dark Web Monitoring Buyer’s Guide for MSPs. DOWNLOAD IT>>


Learn how to spot and stop malicious insiders and educate users with this handy infographic! GET IT>>



Switzerland – Novartis
Exploit: Ransomware
Novartis: Pharmaceutical Company




Risk to Business: 2.717 = Moderate
Novartis has been the victim of an attack by the Industrial Spy data-extortion gang. Last week, the group began selling data allegedly stolen from Novartis on their Tor extortion marketplace for $500,000 in bitcoins. The threat actors claim that the data that they have for sale is related to RNA and DNA-based drug technology and tests from Novartis. The drug company says that no sensitive information was taken. Bleeping Computer reports that the data being sold consists of 7.7 MB of PDF files, which all have a timestamp of 2/25/2022 04:26, likely when the data was stolen.
How it Could Affect Your Customers’ Business Cybercriminals aren’t just hunting for PII, they’re also in the market for proprietary data, formulas, research and information about operational technology
ID Agent to the Rescue Get an in-depth look at how ransomware is evolving and who profits from it in our hit eBook Ransomware Exposed. GET THIS EBOOK>>



It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>



Russia – Rustam Kurmaev and Partners
https://www.hackread.com/anonymous-hacktivists-leak-1tb-russia-law-firm-data/
Exploit: Hacking
Rustam Kurmaev and Partners: Law Firm




Risk to Business: 2.733-Moderate
The Anonymous hacktivists collective claims to have struck another Russian organization. The group leaked approximately 1TB of data from a leading Russian law firm identified as Rustam Kurmaev and Partners (RKP Law). The firm works with major banking, media, oil, and industrial firms and state interests. This incident follows on the heels of another incident two days before in which the collective snatched hundreds of gigabytes of data from the servers of Russia’s largest media holding with over 100 regional radio stations, Vyberi Radio.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Anonymous and its’ associates have been continually hammering at Russian targets in opposition to the Russian invasion of Ukraine.
ID Agent to the Rescue Help your clients be ready for cybercrime trouble and keep their data safe with The Computer Security To-Do List. DOWNLOAD IT>>


Learn to unleash the power of checklists and other downloads in your marketing efforts! WATCH WEBINAR>>


Australia – iCare
Exploit: Insider Risk (Employee Error)
iCare: Insurer







Risk to Business: 1.780 = Severe
State insurer iCare is in the hot seat after an employee mistakenly shared the details of almost 200,000 injured workers with 587 employers and insurance brokers after sending the incorrect cost of claims analysis reports to the wrong recipients. The employee information was contained in spreadsheets that were mistakenly sent as attachments to the wrong employers. The company sent impacted workers an apology for the incident in May 2022.







Risk to Individual: 2.263 = Severe
The missent cost of claims reports included a summary of workers’ claims history, their name, date of birth and injury category, workers’ policy number, a breakdown of weekly payments, claim costs and gross amounts paid, but no banking or contact details.
How it Could Affect Your Customers’ Business Employee mistakes can be just as dangerous, damaging and expensive as many cyberattacks.
ID Agent to the Rescue Get tips for helping your clients identify potential insider risks like employee mistakes or malicious actors with The Guide to Insider Risk. DOWNLOAD IT>>
Australia – ACY Securities
https://www.hackread.com/australian-trading-giant-acy-securities-exposed-data/
Exploit: Misconfiguration
ACY Securities: Financial Services







Risk to Business: 1.871 = Severe
A misconfigured database owned by ACY Securities is to blame for the exposure of personal and financial data of users and businesses. An estimated 60GB worth of data was left exposed and accessible on the web without any security authentication. The data has since been secured.







Risk to Individual: 2.643 = Severe
Spirit Super says that the information potentially exposed includes client names, addresses, ages, email addresses, telephone numbers, member account numbers and member balances. The company was quick to assure members that the exposed data doesn’t include dates of birth, government identification numbers or any bank details.
How it Could Affect Your Customers’ Business This will be a very expensive employee mistake that could have far-reaching effects and regulatory complications.
ID Agent to the Rescue Learn more about the damage employee errors can do and how to mitigate risk in our webinar Human Error: Are You The Reason For The Next Breach? WATCH NOW>>


See why security awareness training is a security and revenue superstar that you & your clients need to invest in now. GET EBOOK>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Go Inside the Ink to see how today’s biggest threats can impact your MSP and your customers in our blog.
- 7 Cybercrime Trends That Impact 2022 Security
- 4 Big Benefits of Security & Compliance Awareness Training
- Do You Really Need Dark Web Monitoring?
- Here’s What the Path to a Ransomware Attack Might Look Like & the Consequences
- The Week in Breach News: 05/25/22 – 05/31/22


Just getting started in cybersecurity? This resource bundle will help you get up to speed to protect your clients fast! GET IT>>


Fresh Resources
The Global Year in Breach
Our signature annual report is packed with data and analysis that you can use to make all the right security moves for your clients. Plus, see concrete data from BullPhish ID and Dark Web ID showing the results of phishing simulations and credential compromise numbers.
You’ll see:
- Exactly which phishing simulations employees fell for the most in 2021
- The worst passwords people use and credential compromise data
- A look at what influences today’s cybercrime trends and what’s next
DOWNLOAD THE GLOBAL YEAR IN BREACH NOW>>
Did you miss… The MSP Cybersecurity Roundtable: How Infrastructure Attacks Can Hurt Every Business webinar recording! WATCH NOW>>


Set businesses on the zero trust path with the 6 Tips for Implementing Zero Trust Security infographic! GET IT>>




See the Phishing Simulations That Employees Failed & Explore Credential Compromise Challenges
Get the Intelligence You Need to Secure Your Customers in The Global Year in Breach 2022
Last week, we looked at data from The Global Year in Breach 2022 that pointed to some of the future challenges that MSPs and their clients can expect to see in 2022 and beyond. This week, we’re focusing on how the actions taken by employees around security when it comes to phishing and passwords can negatively impact an organization’s security. Take a look at this data gathered by BullPhish ID and Dark Web ID to see what actions employees are taking that could damage your clients’ security and what you can do to head them off at the pass. The Global Year in Breach 2022 is available now!


Get a step-by-step guide to building an effective security and phishing awareness training program. GET GUIDE>>
Employees Fall for Phishing Using Common Brands
Phishing has been the reigning champion of data breach risks for three consecutive years because it’s versatile, cheap for cybercriminals to run and highly effective. CISCO’s 2021 Cybersecurity threat trends report shows that at least one person clicked a phishing link in around 86% of the organizations studied. Phishing using common brands is a go-to technique for cybercriminals, including the ever-increasing use of spoofed messages in brand impersonation phishing attempts.
The Verizon Data Breach Investigations Report illustrates the danger, that businesses face from the rapid rise of brand impersonation. Called Misrepresentation in this instance, brand fraud clocked in 15 times higher than it did in 2020. The DBIR notes that this growing category is an aspect of social engineering and a direct precursor to business email compromise attacks. Continued reliance on email as remote work continues and increasing sophistication of phishing messages is a powerful combination for trouble from brand impersonation scams. Employees encounter this threat frequently – 25% of all branded emails that companies receive are spoofed or brand impersonation attempts.
The new champion at the end of 2021 was DHL, the star of about 23% of all phishing attacks. Microsoft clocked in at number two at 20%, followed by WhatsApp at 11% and Google at 10%. A few steps off the leaderboard finds other common brands that cybercriminals favor: WhatsApp (11%), Google (10%), LinkedIn (8%), Amazon (4%), Roblox (3%), FedEx (3%), PayPal (2%) and Apple (2%). Facebook (now Meta) dropped out of the list.


See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>
Here Are the Scams Employees Fell for Last Year
Our award-winning security and compliance awareness training solution BullPhish ID is used by organizations of all sizes in a wide variety of industries. Analyzing the results of thousands of phishing resistance training sessions and phishing simulations with BullPhish ID illustrates the degree to which phishing is an ongoing challenge to conquer.
2021 BullPhish ID Phishing Resistance Training Totals
- Total number of training campaigns created – 81,484
- Total number of phishing simulation emails sent – 2,424,762
- Total number of clicks on phishing simulation emails – 106,670
Top 3 Security Awareness Training Courses of 2021
- Phishing: Introduction to Phishing – 150,163 created trainings
- How to Avoid Phishing Scams – 129,666 created trainings
- Phishing: The Dangers of Malicious Attachments – 100,265 created trainings
Top Phishing Simulation Campaigns That Successfully Drew Employee Interaction
- Office 365 – Suspicious Login – 10,879 clicked
- FedEx – Package Delivery – 6,535 clicked
- Google Docs – Invitation to Edit – 4,492 clicked
Top Phishing Simulation Campaigns That Captured Credentials & Data
- FedEx – Package Delivery – 2,056 captures
- Office 365 – Suspicious Login – 1,736 captures
- COVID-19: SharePoint Webinar – 1,440 captures
Top 10 Industries Where Employees Failed a Phishing Simulation and Supplied Their Credentials
- High-Tech & IT — 3,755
- Medical & Healthcare — 3,504
- Other — 4647
- Manufacturing — 1,801
- Non-Profit Organization — 1,758
- Education & Research — 1,522
- Finance & Insurance – 1,239
- Business & Professional Services – 1,144
- Retail & Ecommerce — 1,046
- Legal — 704


Is it time to update your security awareness training policy – or create one? These 6 tips can help! DOWNLOAD NOW>>
Credential Compromise is an Ongoing Challenge
IT professionals are faced with the struggle against credential compromise every day. People are just bad at making passwords. For businesses, that includes employees at every level. Research by the UK’s National Cyber Security Centre (NCSC) shows that employees will choose memorability over security when making a password every time. Their analysts found that 15% of people have used their pet’s name as their password at some point, 14% have used the name of a family member,13% have used a significant date, such as a birthday or anniversary and another 6% have used information about their favorite sports team as their password. User credentials are the key that unlocks the door to an organization’s systems and data. Unfortunately, it’s far too easy for bad actors to get a copy of that key on the dark web.
- An estimated 15 billion unique logins are circulating on the dark web right now.
- The average organization is now likely to have 17 sets of login details exposed on the dark web.
- Credentials of 133,927 C-level Fortune 1000 executives are accessible in dark web markets.
- There has been a 429% increase in the number of corporate login details with plaintext passwords exposed on the dark web since 2020.
- An estimated 60% of data breaches involved the improper use of credentials in 2021.


Drill down to the bottom line to see why security & compliance awareness training is a smart investment. GET IT>>
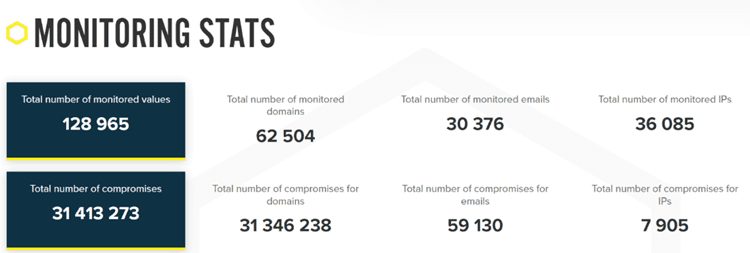
Dark Web ID Reveals Credential Compromise Danger
Dark Web ID safeguards organizations from dark web trouble with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses. Dark Web ID reaches into every shadowy corner of the dark web to find compromises that endanger businesses — and it found plenty of them in 2021

The 20 Most Common Passwords Found on the Dark Web
- 123456
- 123456789
- Qwerty
- Password
- 12345
- 12345678
- 111111
- 1234567
- 123123
- Qwerty123
- 1q2w3e
- 12345678910
- DEFAULT
- 000000
- Abc123
- 654321
- 123321
- Qwertyuiop
- Iloveyou
- 666666
Dark Web ID enables you to get a clear picture of your clients’ credential compromise threats from dark web sources. Our 24/7/365 always-on monitoring alerts businesses to credentials appearing on the dark web that may have been stolen or phished to mitigate the risk of bad actors using a stolen password to gain access to your systems and data. Automated alerts and reporting mean that your team doesn’t need to spend time staring at a dashboard or pulling reports.
BullPhish ID improves your staff’s security awareness and increases phishing resistance. But they’ll learn about much more than just phishing including compliance, password safety, security hygiene and more, giving every employee a solid grounding in cybersecurity pitfalls and best practices. Choose from our plug-and-play complete training modules and phishing simulations or customize the content to reflect the unique industry risks those employees face daily.
Contact our solutions experts today to learn how your business can benefit from strong, affordable security and receive a personalized demonstration.
Join the over 4,000 MSPs who are prospering as an ID Agent Partner and you’ll gain access to the best sales enablement program in the business through Kaseya Powered Services.


This MSP-focused guide gives you insight into finding the ideal dark web monitoring solution. GET THE GUIDE>>


Jun 6 – 8: IT Nation Secure 2022 REGISTER NOW>>
Jun 7: WEBINAR – Business Case for Security Awareness Training REGISTER NOW>>
Jun 9: WEBINAR – Building a Foundation of Security: Backup & Recover REGISTER NOW>>
Jun 14: WEBINAR – MSP Cybersecurity REGISTER NOW>>
Jun 15: From the Crown on Down: Why CXO Buy-In is Critical to Effective Security Awareness Programs REGISTER NOW>>
Jun 20-23: Connect IT Global in Las Vegas REGISTER NOW>>



It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>


Are Your Users Falling for Phishing?
Phishing is one of the biggest cyber threats that any organization faces today. It’s the most common gateway to a data breach – 90% of security incidents that start with a phishing email message end in a data breach.
It’s critical to ensure that every employee is on the lookout for phishing messages. One effective way to do that is through phishing simulations. By running believable “phishing campaigns” of your own, you can gain a better understanding of what risks employees may fall for and who needs more training to avoid being caught by phishing lures.
Training that helps employees avoid phishing is one of the smartest investments that a business can make. Phishing simulations can often be run through a security and compliance awareness training solution. Sometimes, simulation kits also offer the option to customize the content to reflect the industry-specific threats that employees may face.
Don’t wait – set up phishing simulations now and take action to prevent phishing and reduce cyberattack risk today and tomorrow.


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this post (in part or in its entirety) When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!