Business Email Compromise is the Threat You Should Be Worrying About

Don’t Underestimate the Most Expensive Cyberattack of All: BEC
Endless amounts of ink have been spilled to analyze, dissect and report on the flood of ransomware attacks in the last few years. But ransomware is not the nastiest security threat that businesses face. There’s another category of cyberattack that has the potential to cause more trouble and do more damage than ransomware can: business email compromise (BEC). This stealth operator has been quietly thriving in ransomware’s shadow, putting it “out of sight out of mind” for many organizations. However, it should be on every IT professional’s radar because while BEC may not make headlines often, it’s certainly the biggest, baddest threat on the block.

See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>
It Pays to Know the Basics of Business Email Compromise
Business email compromise (BEC) sometimes called email account compromise (EAC)— is a phishing-based cyberattack that utilizes legitimate (or freshly stolen) email accounts from a seemingly trustworthy source to fraudulently acquire money, personal information, financial details, payments, credit card numbers and other data from a business. These scams can target businesses that use wire transfers, foreign suppliers and other invoice transactions. They can also be perpetrated against employees to obtain data, access to assets or money.
What Are Some Business Email Compromise Varieties?
Business email compromise is not a one-size-fits-all proposition. It is especially tricky to spot because it is a scheme that can take many forms.
Urgent payment required scams
Fake invoice scams are the most common BEC variation. In this scenario, someone with the authority to pay vendors in an organization is sent a legitimate-looking invoice from a company that their organization does business with demanding immediate payment to avoid loss of goods or services.
Gift cards and wire transfers
Money is the goal behind BEC. Cybercriminals will often demand that payment for fraudulent reasons be transferred to them via wire transfer, cash app or gift card. This is especially common in CEO fraud scenarios, where an employee is tricked through social engineering into transferring funds to someone posing as an executive of their company electronically or using a gift card. An estimated 62% of BEC scams involve the cybercriminal asking for gift cards, cash app transfers or money cards.
Credential compromise scams
In this BEC variant, fraudsters will ask for the victim to provide credentials for a business account or access to a company’s systems or data, often on the pretense that they’ve misplaced credentials or weren’t given the right ones to complete a task. This is the scenario used in the 2020 Twitter hack, when a bad actor contacted Twitter for system credentials while pretending to be a repair specialist.

Set businesses on the zero trust path with the 6 Tips for Implementing Zero Trust Security infographic! GET IT>>
BEC Happens All the Time
BEC is a constant menace, but it can be tricky to spot because it can take many forms, although employees are most likely to encounter it through phishing. These examples of BEC attacks can help illustrate what a BEC attack might look like in the wild.
- Just this week, we reported on a business email compromise incident that impacted the city of Portland, Oregon. City officials say that cybercriminals gained access to a city email account illegally. The account compromise was detected in May 2022 when the account attempted a transfer of funds. However, major damage had already been done. The bad guys had already shored a nice payday, successfully completed a $1.4 million fraudulent transaction to pay themselves with city funds in April 2022.
- An average employee at an Iowa company received emails that appeared to be from their contact at a legitimate Texas company that the Iowa firm did business with regularly. In these falsified messages, the Texas company billed the Iowa company for a legitimate outstanding invoice that was due for payment. But the message also told the Iowa company that the Texas company’s banking information had changed, and payment needed to be sent to a new account. The Iowa company ultimately made two wire transfers totaling more than $265,000 before anyone at either company discovered that they’d been victimized in a BEC scam.
- The Town of Peterborough, New Hampshire, lost $2.3 million after scammers tricked town employees into sending large payments to the wrong accounts. After the local school system complained that it had not received the funds that had been earmarked for it, investigators discovered that scammers had used spoofed email accounts and forged documents to redirect the town’s payment to accounts under their control. Several other payments to municipal departments and contractors had also been snatched by the same cybercriminals. The total loss to the town was $2.3 million almost 15% of its yearly budget.

Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>
There’s a Good Reason Why BEC is In Vogue
The fact that ransomware has hogged the spotlight isn’t good news for businesses or cybercriminals. Wired magazine recently warned that with heavy scrutiny and high levels of law enforcement action around recent high-profile ransomware attacks, cybercrime gangs will be looking for fresh ways to bring in big money without as much heat, making BEC a very attractive proposition. Experts warn that ransomware gangs could easily bring their skillset to the BEC landscape, creating a higher level of activity and risk for businesses.
Ransomware groups have several major strengths to bring to the table when converting their operations to BEC. Social engineering is a critical component of BEC, and the bad guys have extensive expertise in that area. Ransomware groups also have the skills to easily establish “initial access” because that’s something they already do, including leveraging their previous relationships with initial access brokers and other dark web resources. Plus, the software that they use is designed to be flexible and modular, making it easy for them to assemble the software needed to conduct a successful attack quickly.

Security and compliance training pays amazing dividends. Get tips to run an effective program with our how-to guide! GET GUIDE>>
BEC is 64x Worse Than Ransomware
BEC is not a threat that anyone should underestimate, and it has the potential to do much more damage in many ways than other cyberattacks like ransomware. The potential for huge profit is a big enticement for ransomware gangs to convert their operations to BEC. In fact, the U.S. Federal Bureau of Investigation Internet Crime Complaint Center (FBI IC3) declared that when estimated yearly losses between those two cyberattacks were compared, BEC turned out to be 64x worse than ransomware for a company’s finances.
The 2021 IC3 Internet Crime Report, makes it clear: BEC remains the reigning champion of risks, In the U.S., BEC schemes were the costliest cybercrimes reported to IC3 in 2020 and 2021, and that’s not expected to change in 2022. In fact, BEC rose substantially in 2021. In 2020, BEC clocked in at 19,369 complaints with an adjusted loss of approximately $1.8 billion. But for 2021 those loss numbers climbed significantly. The BEC category showed that complainants to IC3 suffered $2,395,953,296 in losses in 2021, a whopping 28% higher than 2020’s record total of $1,866,642,107, with 3% more total BEC complaints.
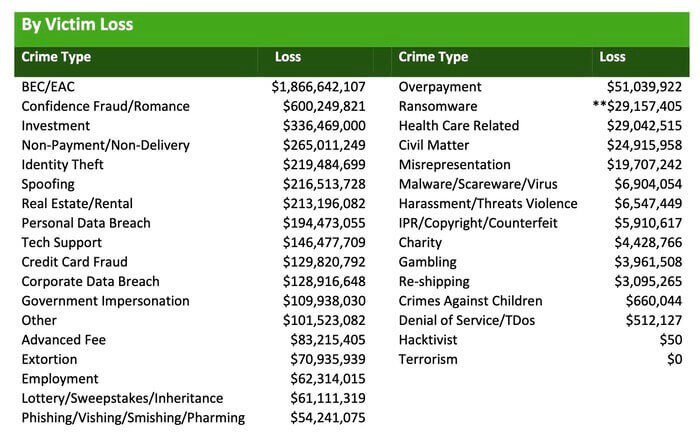
Source: FBI IC3

Drill down to the bottom line to see why security & compliance awareness training is a smart investment. GET IT>>
These Two Powerful Weapons Reduce Business Email Compromise Risk
BEC is one of the biggest cyber risks that businesses face. But by taking a few sensible precautions like putting these strong solutions in place, you can reduce the risk of business email compromise trouble in organizations of any size.
Protection from dark web danger with Dark Web ID gives your security team the confidence that they’ve got credential compromise threats handled.
- Dark web search finds every compromised company credential fast, enabling you to fix them before the bad guys can exploit them
- Monitoring with 24/7/356 human and machine intelligence ensures that your team knows exactly what your company’s dark web exposure risk is in real-time
- Leverage out-of-the-box integrations with popular PSA platforms, for a fast, frictionless alerting and mitigation process, so you never miss a security event.
Rely on BullPhish ID to deliver comprehensive security awareness training that works and reduces your company’s chance of having to use your incident response plan by up to 70%.
- Don’t just train employees about phishing – get them up to speed on threats like ransomware, smart security behaviors and compliance too.
- Make training and tracking a snap with personalized portals for every user, enabling trainers to painlessly track and assign training.
- Use premade plug-and-play kits or customize your training materials to reflect the unique industry threats that employees face daily.
Book a demo of our innovative, affordable solutions today!

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!