Supply Chain Attacks Rise While Other Breaches Dip Slightly

The Supply Chain Attack Problem Just Keeps Getting Worse
Every IT professional dreads their company suffering a data breach. However, in today’s volatile cybercrime landscape, many companies find themselves in that unenviable position every year. Plus, the cost of a data breach rises every year as well, reaching a record $4.35 million in 2021. In 2022, supply chain attacks grew in prominence, opening businesses up to new avenues of danger. But there was some good news: while more people than ever before were impacted by a data breach in 2022, the total number of recorded data breaches dipped slightly.

See how security awareness training stops the biggest security threats! GET INFOGRAPHIC>>
Data breach numbers are down but the victim count is up
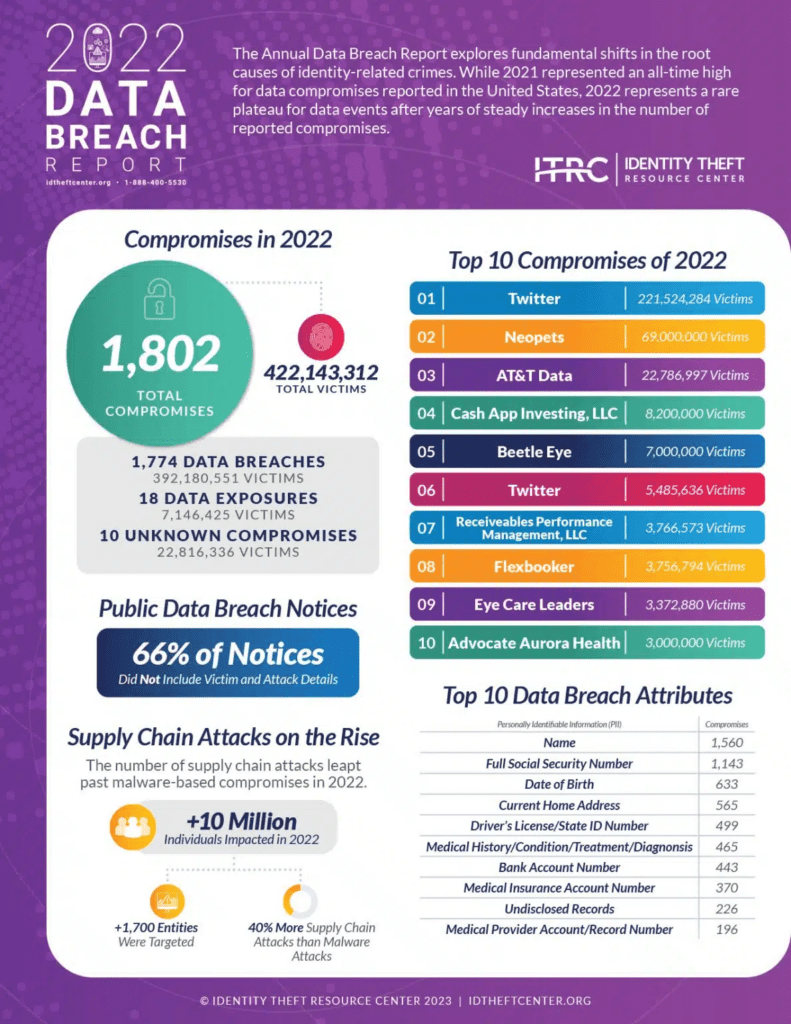
According to the 2022 Data Breach Report by the Identity Theft Resource Center, there were 1802 data compromise incidents in 2022, 60 less than the previous all-time high of 1862 set in 2021. But fewer breaches doesn’t translate into fewer data breach victims. The estimated number of people who became victims of a data breach in 2022 has increased sharply compared to 2021, up more than 40% to 422.1 million people. Here are some notable stats in the report.

Learn about SMB attitudes toward cybersecurity and other growth opportunities for MSPs. GET INFOGRAPHIC>>
Key Findings Indicate Some Breach Risks Are Growing
Data breaches surged during the second half of 2022
According to ITRC, the first half of 2022 was relatively quiet on the data breach front for organizations compared to the latter half of the year. The analysts in this report attribute this decline in data compromise numbers to the conflict in Eastern Europe between Russia and Ukraine. As Russia-based cybercriminal groups were distracted or disbanded due to the war, there was an overall drop in ransomware and other data compromise incidents.
However, the second half of 2022 witnessed a 21% increase in security incidents, spoiling what would have been an excellent year for organizations in terms of cyber incidents. The cyberattack on Twitter, where information of 221 million Twitter users was made available in dark web markets, was the most significant contributor to this rise. During the same period, identity impersonation scams also surged remarkably, contributing to the increase in cyberattack figures.

Learn how managed SOC gives you big security expertise on call 24/7without the big price tag. LEARN MORE>>
Lack of transparency in information sharing
In 2003, the Breach Notification Law was enacted to help individuals and businesses understand the relative risk of a security breach and the required steps to protect themselves against similar attacks. However, in the last few years, companies have grown apathetic toward sharing comprehensive data breach information on public forums. From conglomerates like Samsung to SMBs like LastPass, many businesses have decided to include little or no detail about what happened and who was impacted in their mandated breach notices. According to the ITRC report, 66% of companies that disclosed a data breach in 2022 shared very little information on the data breach. Experts point at a desire to protect their company against lawsuits as a likely factor.
A rise in supply chain attacks
Malware-related cyberattacks have typically topped the charts due to a high degree of popularity among cybercriminals thanks to their generally high success rate when compared to other cyberattack methods. However, that’s not the avenue of attack that is growing the most. Instead, supply chain attacks surpassed the number of malware-based attacks by almost 40% in 2022. While malware-related attacks impacted 4.3 million people, more than 10 million were impacted by supply chain attacks targeting 1,743 entities.

What worries security pros? The Kaseya Security Insights Report 2022 tells you. GET YOUR REPORT>>
Large data breaches show the rising tide of breaches in the second half of 2022
These data breach incidents were cited in the ITRC reports as particularly impactful in 2022.
In December 2022, many hackers and cybersecurity researchers announced more than 400 million accounts attached to an estimated 221 million users of Twitter were on sale on various dark web forums. It is believed that cybercriminals exploited a software vulnerability, which Twitter allegedly fixed earlier. Twitter did not confirm the attack that impacted more than 221 million people around the globe.
AT&T
In August 2022, cybersecurity experts found 22.8 million unique email addresses and 23 million unique Social Security numbers on a popular dark web site that was believed to be related to customers of AT&T. The breach allegedly exposed the data of more than 22 million people. Although AT&T acknowledged that the stolen data “may be tied to a previous data incident at another company,” it denied the information was stolen from its systems.
LastPass
In August 2022, LastPass announced that cybercriminals gained access to their source code and software development information but reported that they failed to access customer information. However, in December the company retracted its earlier announcement and said that cybercriminals had indeed gained access to customer information using the information stolen in August. The exact scope of this data breach is still unknown.
Kaseya’s Security Suite Can Protect Businesses from Adversaries
Take action now to avoid trouble (and regrets) later. These solutions work together to provide a robust defense against cyberattacks for any business without breaking the bank.
Security Awareness Training
BullPhish ID is the perfect solution to use to make that happen!
- A huge library of security and compliance training videos with 4 new lessons added a month!
- Choose from plug-and-play or customizable phishing training campaign kits
- Automation makes training painless for everyone
Dark Web Monitoring
Dark Web ID is the answer.
- 24/7/365 monitoring using real-time, analyst-validated data
- Monitoring of business and personal credentials, including domains, IP addresses and email addresses
- Gain priceless peace of mind about dark web dangers
Identity and Access Management (IAM)
Passly is the perfect multi-tool for IAM packing four essentials into one affordable package
- Get two-factor authentication (2FA), single sign-on, secure password vaults with one solution
- Simple, intuitive remote management
- Roll it out in a snap with easy deployment and seamless integration with common business applications
Automated, AI-powered Antiphishing Email Security
Graphus AI-enabled, automated email security that catches 99.9% of sophisticated phishing threats and offers amazing benefits.
- Forget old-fashioned safe sender lists. Graphus analyzes the content of messages using more than 50 points of comparison to suss out fakes fast.
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- 3 layers of powerful protection at half the cost of competing solutions
- Don’t waste time on fussy configurations or adding threat reports. AI does that for you, getting everything up and running with just a few clicks and minimal maintenance.
Managed SOC
Get the top Managed SOC that leverages our Threat Monitoring Platform to give you access to an elite team of security veterans hunt, triage and work with your team when actionable threats are discovered
- Detect malicious and suspicious activity across three critical attack vectors: Endpoint, Network & Cloud
- Patent-pending cloud-based technology eliminates the need for on-prem hardware
- Discover adversaries that evade traditional cyber defenses such as Firewalls and AV

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!