The Week in Breach News: 01/04/23 – 01/10/23

14 UK schools were hit by Vice Society, a hack at a business services firm impacts 400 U.S. regional and municipal governments and a look at the new Passly – BullPhish ID integration plus see why business email compromise (BEC) is the threat to watch right now.

This handy checklist of smart security practices helps businesses kick off the new year right! GET CHECKLIST>>


Five Guys
https://www.jdsupra.com/legalnews/five-guys-enterprises-llc-announces-3894616/
Exploit: Hacking
Five Guys: Restaurant Chain



Risk to Business: 2.776 = Moderate
Quick service burger chain Five Guys has disclosed a data breach. The company filed data breach notifications in Texas, Massachusetts and Montana. Five Guys said that on September 17, 2022, they learned that “an unauthorized party” may have gained access to its computer system. Five Guys later determined that some of the compromised files contained sensitive information belonging to individuals who had previously applied for a job with the company. Exposed information varies depending on the individual and may include names, Social Security numbers, driver’s license numbers and financial account information.
How It Could Affect Your Customers’ Business: This could end up being an expensive incident for Five Guys even with such a small number of folks impacted because of the sensitivity of the data.
ID Agent to the Rescue: The Cybersecurity Risk Protection Checklist helps businesses make sure that they’re covering all of their security bases. GET CHECKLIST>>
SAIF
Exploit: Hacking
SAIF: Insurer






Risk to Business: 2.201 = Severe
SAIF, a not-for-profit organization that serves as Oregon’s leading provider of workers’ compensation coverage, has experienced a data breach. The organization maintains that some of the information was at least two decades old, according to the organization, but some who filed claims in September and October may have had medical information compromised. SAIF has notified impacted parties by mail and offered them free ID theft and monitoring service for a year. SAIF said its breach occurred on October 24, 2022, and it notified customers on December 8, 2022.
How It Could Affect Your Customers’ Business: Insurers are juicy targets for the bad guys because they hold so much valuable data.
ID Agent to the Rescue: Learn more about the security challenges that businesses face in the Kaseya Security Insights Report 2022. READ THE REPORT>>
Cott Systems
https://www.bankinfosecurity.com/cyberattack-on-records-vendor-affects-scores-us-counties-a-20856
Exploit: Hacking
Cott System: Business Services


Risk to Business: 1.227 = Extreme
Cott Systems, a company that handles records management for more than 400 U.S. local and regional governments, has experienced a data breach. The company was forced to shut down its servers which hold government data including public records, land records and court cases. That resulted in hundreds of local governments being forced to resort to manual processes, slowing down the processing of birth certificates, marriage licenses and real estate transactions. Cott Systems says that it has no indication that data has been compromised.
How It Could Affect Your Customers’ Business: This is a disaster for many governments that could severely damage Cott Systems’ government contracting future.
ID Agent to the Rescue: See the biggest risks that different sectors face today and get a look at what businesses will be facing tomorrow in The Global Year in Breach 2022. DOWNLOAD IT>>
Robins & Morton Group
https://www.jdsupra.com/legalnews/the-robins-morton-group-files-notice-of-5035278/
Exploit: Hacking
Robins & Morton Group: Construction Company



Risk to Business: 2.981 = Moderate
Alabama-based construction firm Robins & Morton, a major construction operation in the Southeastern U.S., has disclosed that it has experienced a data security incident in which unauthorized parties accessed its data. The company said that the event took place on October 16, 2022, and that the intruders were able to continue accessing the network until the following day. Some of the files that were compromised contained confidential information belonging to certain consumers. The company said that it sent data breach notifications to affected parties in December 2022.
How It Could Affect Your Customers’ Business: Infrastructure-related companies like construction firms have been hard hit by cybercrime for the last two years.
ID Agent to the Rescue: A strong security culture reduces the risk of an incident. Build one with The Building a Strong Security Culture Checklist! DOWNLOAD IT>>


See how security awareness training stops the biggest security threats! GET INFOGRAPHIC>>


United Kingdom – Pates Grammar School
https://www.devonlive.com/news/devon-news/devon-school-hit-cyber-attack-8000342
Exploit: Ransomware
Pates Grammar School: Educational Institution






Risk to Business: 1.643 = Severe
The BBC reports that 14 UK schools, including Pates Grammar School, have fallen victim to a spate of cyberattacks by the Vice Society ransomware group. The attack on Pates took place on September 28, 2022. The gang obtained sensitive data about students including children’s SEN information, child passport scans, staff pay scales and contract details from students enrolled in 2021 & 2022. BBC writers say that they’ve seen data from 14 UK primary and secondary schools purportedly snatched by Vice Society. The incidents are still under investigation.
How it Could Affect Your Customers’ Business: The education sector has been a favored target of ransomware groups since the start of the COVID-19 pandemic and they’re not slowing down.
ID Agent to the Rescue: Identity and Access Management (IAM) helps stop cyberattacks. Our Complete IAM Checklist helps you find the right solution for your needs. GET CHECKLIST>>
France – Deezer
Exploit: Hacking
Deezer: Streaming Platform






Risk to Business: 1.603 = Severe
France-based music-streaming platform Deezer has experienced a data breach that has potentially compromised the information of over 220 million users. The company said that the breach took place in November 2022. “The data in question had been handled by a 3rd party partner that we haven’t worked with since 2020, and it was this partner that experienced the breach. Deezer’s security systems remain effective, and our own databases are secure,” Deezer said in a statement. Exposed user data includes basic information such as first and last names, date of birth and email addresses.
How it Could Affect Your Customers’ Business: Consumers aren’t going to want to become users of a platform that can’t keep their data safe.
ID Agent to the Rescue: Security awareness training helps employees avoid ransomware traps. Learn to create a great program with How to Build a Security Awareness Training Program. DOWNLOAD IT>>


Australia – Queensland University of Technology (QUT)
Exploit: Ransomware
Queensland University of Technology (QUT): Institution of Higher Learning






Risk to Business: 1.904 = Severe
The Royal ransomware gang is responsible for a ransomware attack on the Queensland University of Technology. QUT disclosed the cyberattack on January 1st, 2023, warning students and academic staff of inevitable service disruptions resulting from the security incident. The HiQ website, ‘Digital Workplace’, ‘eStudent’, and Blackboard systems are unavailable. Many other systems are also unavailable like network drive folders, including ‘U Drive’ and the printing network. Access via VPN using Cisco AnyConnect have been disabled until further notice. QUT said that it did not believe that any data was stolen, but Royal has leaked a variety of data like HR files, email and letter communications, ID cards and documents, and financial and administrative documents.
How it Could Affect Your Customers’ Business: Education is a time-sensitive industry, making it especially attractive to ransomware gangs.
ID Agent to the Rescue: This infographic illustrates just how easy it is for a company to end up on The Ransomware Road to Ruin. GET INFOGRAPHIC>>


What worries security pros? The Kaseya Security Insights Report 2022 tells you. GET YOUR REPORT>>


India – Toyota Kirloskar Motor (TKM)
https://gbhackers.com/toyota-discloses-data-breach/
Exploit: Employee Mistake
Toyota Kirloskar Motor (TKM): Carmaker






Risk to Business: 2.103 = Severe
Toyota Motor Corporation has revealed a data breach that may have compromised the personal information of its customers by its Toyota Kirloskar Motor (TKM) division in India. Toyota said that the breach occurred because of an error by a website development subcontractor who mistakenly uploaded part of the source code to their public GitHub account. The company disclosed that the incident might have exposed the personal information TKM’s customers. An estimated 296,000 users of T-Connect who signed up between July 2017 and September 2022 may have had data exposed.
How it Could Affect Your Customers’ Business: Employee mistakes are the cause of so many expensive disasters that security awareness training can help prevent.
ID Agent to the Rescue: See the dollars and cents benefits of security awareness training in our eBook The Business Case for Security Awareness Training. DOWNLOAD EBOOK>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Don’t miss the industry’s best event, Connect IT Global April 24 – 27, 2023, in Las Vegas! REGISTER NOW>>


See how today’s biggest threats may impact businesses in our security blogs.
- 9 Cybersecurity Predictions You Must See
- The Worst Phishing Attacks in History
- 7 Things to Know About the State of the MSP
- Register Now for Connect IT Global & Other Must-Attend 2023 Events
- The Week in Breach News: 12/28/22 – 1/03/23


Set businesses on the zero trust path with the 6 Tips for Implementing Zero Trust Security infographic! GET IT>>


BullPhish ID-Passly Integration Facilitates Customer Onboarding, Campaign Management
The Passly and BullPhish ID teams are excited to announce a new integration that streamlines customer onboarding and campaign management in BullPhish ID. This new workflow integration advances the Kaseya IT Complete vision by making our product modules work efficiently together to simplify the lives of our customers.
What it is:
Leveraging Passly’s sync capabilities with Azure Active Directory and on-premise Active Directory, BullPhish ID MSPs can quickly onboard organizations onto BullPhish ID and create campaigns with always up-to-date lists of targets. Passly will serve as “the user store” for BullPhish ID, so any personnel changes in Active Directory will sync from Passly to BullPhish ID, ensuring an always-accurate list of training targets.
Why you’ll love it:
In order to conduct effective employee training campaigns and phishing simulations, businesses need to have a current, accurate list of employees to be trained. The new integration with Passly ensures that the targets and groups within BullPhish ID are always up to date, greatly simplifying the new SMB organization setup and ongoing campaign management.
How it works:
Note: customers must have subscriptions to both Passly and BullPhish ID to enable the integration.
- First, customers log in to their Passly account, navigate to the Integration Manager section, generate an API key for BullPhish ID and copy.
- Next, they log in to their BullPhish ID account, navigate to Targets & Groups, then Directories. Click the + Add Directory Sync button to create a sync between an organization and a Passly directory.
- For detailed instructions on enabling the integration, refer to this guide.


Learn how to spot and stop malicious insiders and educate users with this handy infographic! GET IT>>


3 Key Checklists to Make Sure You’re Covering Every Angle
These three checklists help ensure that you’re making smart security choices.
Is Your Company Protected from These Risks? This handy checklist helps ensure that you’ve got every base covered. DOWNLOAD IT>>
6 Tips for Implementing Zero Trust Security Are you progressing on a journey toward a zero-trust security future? These tips can help you make progress. DOWNLOAD IT>>
Can Your Email Security Solution Do These 10 Things? This checklist helps you evaluate your email security solution to see if it’s time for an upgrade. DOWNLOAD IT>>
Did you miss…? Our How to Build a Security Awareness Training Program eBook DOWNLOAD EBOOK>>


It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>




You Should Be Worried About This Game-Changing BEC Evolution
What’s the biggest cyber threat that businesses face? It isn’t ransomware, even though that tends to grab all of the headlines. It’s business email compromise (BEC). Sometimes called email account compromise (EAC), BEC can lead to potentially devastating business losses. BEC is the number one threat on Forbes Magazine’s 5 Scams to Watch for in 2023 list. Unfortunately, BEC’s chameleon-like nature makes it tricky for most victims to spot. That’s a serious problem because this attack can do massive damage to a company’s revenue, reputation and productivity quickly. This look inside the complicated world of BEC will help you develop and maintain a strong defensive posture against today’s most expensive cyber threat.
Excerpted in part from The Comprehensive Guide to Avoiding Business Email Compromise DOWNLOAD IT>>



This handy checklist of smart security practices helps businesses kick off the new year right! GET CHECKLIST>>
What does BEC look like today?
Business email compromise (BEC) is a cyberattack that cybercriminals use to utilize seemingly legitimate (or freshly stolen) email accounts from one organization to fraudulently trick employees of another business into giving them credentials, money, personal information, financial details, payments, credit card numbers or other sensitive data. More than 70% of companies experienced a BEC attack in 2021. These scams also target companies that use wire transfers, foreign suppliers and other invoice transactions. Forbes reports that payroll scams are an up-and-coming BEC threat. BEC practitioners are also concentrating their efforts on infrastructure targets, especially if those sectors are under stress. The massive supply chain troubles leftover from the COVID-19 crisis opened new avenues for BEC groups. he U.S. Federal Bureau of Investigation (FBI) recently released a warning that BEC scammers are targeting the Food and Agriculture sector, sometimes attempting to divert entire food shipments.
5 things to know about BEC right now
- BEC attacks account for losses that are 64x worse for businesses than ransomware
- BEC is the second most expensive vector for a data breach and for large organizations, a BEC-related data breach carries an average cost of $4.69 million.
- A data breach that is caused by BEC has the second-highest mean time to identify and contain the intrusion at 308 days.
- Large companies spend an estimated $6 million yearly on BEC recovery, including just over $1 million in illicit payments stolen by attackers.
- Gartner estimates that BEC attacks will double each year, cresting $5 billion in impact in 2023.


Learn how a new integration between BullPhish ID & Graphus saves time & money. SEE THE DETAILS>>
The Newest Player in BEC: Ransomware Gangs
Cybercrime is ever-evolving, but certain factors in the environment can push those changes to happen a bit faster. One of the biggest reasons for the massive growth in BEC attacks right now is the huge pool of resources available to cybercriminals. The cybercrime-as-a-service market is booming, and often phishing-based cyberattacks like BEC and can be largely automated or farmed out to phishing specialists. Compounding the issue, increased law enforcement scrutiny around ransomware has also driven cybercrime groups that have in the past primarily pursued ransomware attacks to turn their attention to BEC operations. It’s easy for a ransomware gang to quickly pivot to BEC. The two cyberattacks share enough functional similarities that a major ransomware gang can simply utilize its existing resources to start conducting BEC attacks without making many changes to its personnel or operating structure.
The FBI’s Internet Crime Complaint Center (IC3) annual report offers a wealth of data that illustrates the explosive and dangerous growth of BEC. IC3 says that BEC is the cyberattack that cost victims the most money in 2021. The BEC/EAC category showed that complainants to IC3 suffered $2,395,953,296 in losses in 2021, 28% higher than 2020’s record total of $1,866,642,107, with 3% more total BEC complaints. BEC was far and away more expensive than its nearest peers.
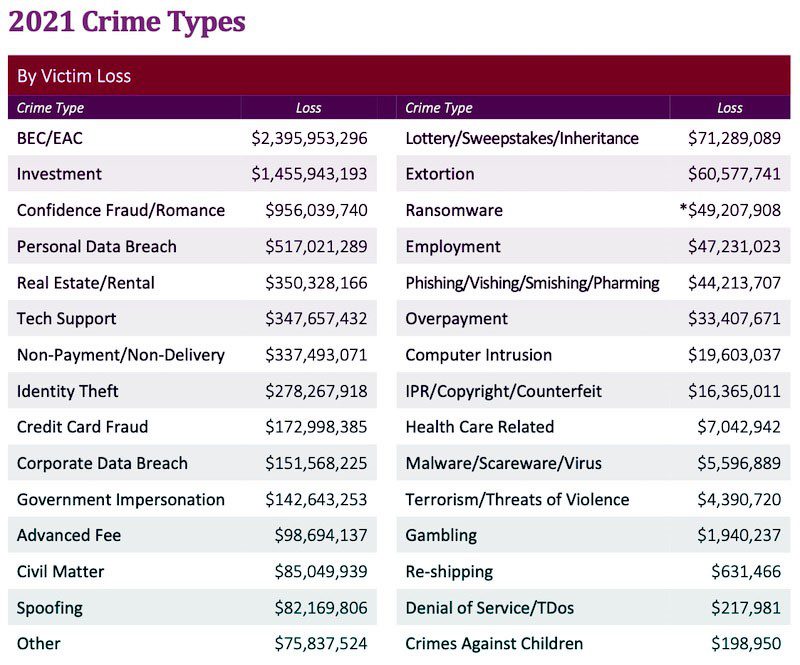

Source: FBI IC3


Be the hero that defeats a company’s security threats to declare victory over cybercriminals! GET THE GUIDE>>
The flood of phishing makes BEC threats worse
Businesses fear phishing with good reason. Phishing is the most likely way that a BEC threat will enter a company’s environment, and employees are dealing with a deluge of phishing daily. An estimated 80% of reported security incidents are phishing-related these days. In the Kaseya Security Insight Report 2022, more than half of the business IT pros that we surveyed pointed to phishing and email fraud as the primary security threat facing their organization. Ransomware held the second spot, with nearly one-quarter of businesses saying they worry about it the most.
What is the primary security threat to your organization?
| Security Threat | % of Respondents |
| Phishing/email fraud | 55% |
| Ransomware | 23% |
| Password compromise | 15% |
| Account takeover (ATO) | 6% |
| Other | 2% |
Source: Kaseya


Drill down to the bottom line to see why security & compliance awareness training is a smart investment. GET IT>>
More than one-third of businesses have experienced a cyberattack like BEC
Businesses have been dealing with a steadily increasing stream of cyberattacks, and that pressure has resulted in some unpleasant security outcomes. While about half of our survey respondents have yet to endure a cyberattack, the other half of respondents weren’t so fortunate. Almost one-quarter of the businesses that we surveyed (19%) said that they’d endured a cyberattack or security breach within the past 12 months. The percentage rises to a little over one-third (34%) when expanded to a three-year span. With so many of the organizations that we surveyed having experienced at least one cyberattack hit or data disaster, it’s easy to see that it’s no longer a question of “how” or “if” but “when” a company will fall victim to a cyberattack. As threats evolve and security challenges mount, strengthening a company’s cyber defenses including email security must be a top priority.
Has your organization experienced a successful cyberattack or security breach?
| Timeframe | Responses |
| Never | 26% |
| Within the past 6 months | 16% |
| Within the past year | 22% |
| Within the past 3 years | 24% |
| Over 3 years ago | 12% |
Source: Kaseya


Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>
Our security solutions help businesses mitigate threats like BEC
Our security solutions can help keep businesses out of trouble effectively and affordably.
Security awareness and compliance training plus phishing simulation
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size. This powerhouse is the channel leader in phishing simulations.
- An extensive library of security and compliance training videos in eight languages
- Plug-and-play or customizable phishing training campaign kits
- New videos arrive 4x per month and new phishing kits are added regularly
Dark web monitoring
Dark Web ID offers best-in-class dark web intelligence, reducing credential compromise risk.
- 24/7/365 monitoring using real-time, machine and analyst-validated data
- Fast alerts of compromises of business and personal credentials, including domains, IP addresses and email addresses
- Live dark web searches find compromised credentials in seconds
- Create clear and visually engaging risk reports
Automated, AI-powered antiphishing email security
Graphus AI-enabled, automated email security that catches 99.9% of sophisticated phishing threats and offers amazing benefits.
- Forget old-fashioned safe sender lists. Graphus analyzes the content of messages using more than 50 points of comparison to suss out fakes fast
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- 3 layers of powerful protection at half the cost of competing solutions
- Don’t waste time on fussy configurations or adding threat reports. AI does that for you, getting everything up and running with just a few clicks and minimal maintenance
Managed SOC
Get the top Managed SOC that leverages our Threat Monitoring Platform to give you access to an elite team of security veterans hunt, triage and work with your team when actionable threats are discovered
- Detect malicious and suspicious activity across three critical attack vectors: Endpoint, Network & Cloud
- Patent-pending cloud-based technology eliminates the need for on-prem hardware
- Discover adversaries that evade traditional cyber defenses such as Firewalls and AV


See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>


January 17: Kaseya + Datto Connect Local Tampa, FL REGISTER NOW>>
January 19: Kaseya + Datto Connect Local Los Angeles, CA REGISTER NOW>
January 23 – 25, 2023: Schnizzfest in Phoenix, AZ REGISTER NOW>>
January 25: Q1 Security Suite Product Update: BullPhish ID, Dark Web ID, Passly & Graphus REGISTER NOW>>
January 31: Kaseya + Datto Connect Local Dallas REGISTER NOW>>
February 7: Kaseya + Datto Connect Local Orlando REGISTER NOW>>
February 9: Kaseya + Datto Connect Local Washington D.C. REGISTER NOW>>
February 14: Kaseya + Datto Connect Local Atlanta REGISTER NOW>>
February 16: Kaseya + Datto Connect Local Miami REGISTER NOW>>
February 21 – 22: Kaseya + Datto Connect Local Charlotte REGISTER NOW>>
February 23: Kaseya + Datto Connect Local Phoenix (Glendale) REGISTER NOW>>
April 24 – 27, 2023: Connect IT Global in Las Vegas REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!