The Week in Breach News: 05/11/22 – 05/17/22

Data security trouble has emerged in government agencies and healthcare organizations around the U.S., nation-state-related cyberattacks keep popping up in Europe and why all of your clients need dark web monitoring right now.

Set businesses on the zero trust path with the 6 Tips for Implementing Zero Trust Security infographic! GET IT>>

Omnicell
https://www.securityweek.com/healthcare-technology-provider-omnicell-discloses-ransomware-attack
Exploit: Ransomware
Omnicell: Healthcare Technology

Risk to Business: 1.944 = Severe
Omnicell revealed that its internal systems were impacted by a ransomware attack on May 4, 2022, in an SEC filing. The company further explained that it expected the attack to have an impact on some of its products and services, but it did not specify which ones. Omnicell says that it is in the early stage of an investigation, but the attack has been contained and appropriate authorities have been informed.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business: Everything in the healthcare sector has been under siege since the start of the global pandemic and pressure isn’t easing up.
ID Agent to the Rescue: Learn to mitigate your clients’ ransomware risk and protect them from trouble with the resources in our Deep Dive Into Ransomware bundle! GET BUNDLE>>
Texas Department of Insurance (TDI)
https://www.texastribune.org/2022/05/16/texas-insurance-data-breach/
Exploit: Misconfiguration
Texas Department of Insurance (TDI): Regional Government Agency










Risk to Business: 1.804 = Severe
A routine audit discovered that a misconfigured server at the Texas Department of Insurance has been leaking information for three years. The report disclosed that the personal information of an estimated 1.8 million Texas workers who have filed compensation claims between March 2019 and January 2022 has been exposed. TDI says that the problem has been corrected and that its investigation found no evidence that the information had been stolen or used unlawfully.










Risk to Individual: 1.923 = Severe
The personal information of 1.8 million workers who have filed compensation claims in Texas was exposed including Social Security numbers, addresses, dates of birth, phone numbers and information about workers’ injuries.
How It Could Affect Your Customers’ Business Misconfiguration errors are common and just as costly and problematic as many cyberattacks.
ID Agent to the Rescue: Find and slay dastardly vulnerabilities in your clients’ security strategy and emerge victorious with The Cybersecurity Monster Hunter’s Checklist! GET IT>>
The Oregon Elections Division
https://www.securityweek.com/hackers-hit-web-hosting-provider-linked-oregon-elections
Exploit: Supply Chain Risk
The Oregon Elections Division: Regional Government Agency



Risk to Business: 2.702 = Moderate
The Oregon Elections Division has announced that it has informed an estimated 1,100 people that their information may have been exposed in a data breach after the online system where campaign finance records are published was hit by a ransomware attack at its web hosting provider. The Oregon Elections Division said it was informed by C&E systems, a campaign finance firm that its web hosting provider Opus Interactive was the victim of a ransomware attack. Through that incident, C&E’s database was compromised, which includes their client’s log-in credentials for ORESTAR accounts. C7E disputes the number of affected accounts, placing it closer to 300. This attack has no impact on the voting or elections process outside campaign finance.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business:
ID Agent to the Rescue: Security threats are around every corner in today’s volatile landscape. Learn to quickly identify and mitigate your clients’ risks in the Deep Dive Into Cybersecurity Bundle. GET BUNDLE>>
Oklahoma City Indian Clinic (OKCIC)
https://www.infosecurity-magazine.com/news/oklahoma-city-indian-clinic-data/
Exploit: Hacking
Oklahoma City Indian Clinic (OKCIC): Healthcare Provider










Risk to Business: 2.302 = Severe
Oklahoma City Indian Clinic (OKCIC) this week announced that it experienced a data breach exposing personally identifiable information (PII) on May 12 when unauthorized parties obtained access to its data and systems. A third-party forensic firm has been brought in to investigate. So far, the investigation has confirmed that an unauthorized party accessed and may have retained sensitive customer information.










Risk to Individual: 2.327 = Severe
At present, 38,239 individuals are reportedly impacted by the breach. The compromised files include a patient’s name, date of birth, treatment information, prescription information, medical records, physician information, health insurance policy numbers, phone numbers, Tribal ID numbers, Social Security numbers and driver’s license numbers.
How it Could Affect Your Customers’ Business: Government and quasi-governmental agencies have been popular targets for cybercriminals looking for big stores of data.
ID Agent to the Rescue: Help your clients strengthen their security today and tomorrow with the tips found in our Building a Strong Security Culture Checklist. DOWNLOAD CHECKLIST>>
Illinois Gastroenterology Group (IGG)
https://www.illinoisgastro.com/articles/notice-of-security-incident
Exploit: Hacking
Illinois Gastroenterology Group (IGG): Healthcare Provider










Risk to Business: 1.917 = Severe
Illinois Gastroenterology Group (IGG) announced that it has experienced a data security problem that potentially impacted 227,943 individuals. IGG disclosed that it had discovered unusual network activity on October 22, 2021, and that it believed that information may have been stolen. IGG also said it had no evidence of related identity theft or fraud.










Risk to Individual: 1.929 = Severe
The stolen data includes patient names, birth dates, Social Security numbers, driver’s license numbers, passport information, financial account information, addresses, payment card information, biometric data, employer-assigned identification numbers and medical information.
How it Could Affect Your Customers’ Business This type of incident is expensive in more ways than one and will spin out into a long, draining regulatory nightmare.
ID Agent to the Rescue Cybersecurity horrors lurk around every corner, lying in wait for unwary organizations. Learn how to defeat them in our eBook Monsters of Cybersecurity. DOWNLOAD IT NOW>>


Learn how to spot and stop malicious insiders and educate users with this handy infographic! GET IT>>


Top Aces
https://therecord.media/top-aces-ransomware-attack-lockbit/
Exploit: Ransomware
Top Aces: Flight Training Company










Risk to Business: 1.733-Severe
Montreal-based company Top Aces, a provider of fighter jets for airborne training exercises, has been hit with a ransomware attack by the LockBit group. The company says that it is the exclusive adversary air provider to the Canadian and German armed forces. LockBit says it stole 44 GB of data and has given Top Aces a deadline of May 15 to pay them and avoid publication of the stolen data. No ransom amount is available.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Defense industry contractors and military-adjacent service providers are tempting targets for cybercriminals looking for back doors.
ID Agent to the Rescue Get an in-depth look at how ransomware is evolving and who profits from it in our hit eBook Ransomware Exposed. GET THIS EBOOK>>


Learn to unleash the power of checklists and other downloads in your marketing efforts! WATCH WEBINAR>>


Italy – Senato della Repubblica (Senate of the Republic)
Exploit: Nation-State
Senato della Repubblica (Senate of the Republic) – Governing Body










Risk to Business: 2.096 = Severe
Pro-Russian hacking group Killnet has claimed responsibility for a cyberattack that briefly interrupted business in Italy’s Senate. The group also targeted the National Health Institute (ISS) and the Automobile Club d’Italia. A tweet by the Speaker of the Senate disclosed that there was no significant damage in the Senate attack.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Unexpected nation-state danger is always just around the corner for government agencies, legislative bodies and government-related entities.
ID Agent to the Rescue Nation-state cybercrime risk is escalating for businesses in every sector. Learn the basics of nation-state cybercrime and how to protect your clients. GET EBOOK>>
Russia – SOCAR Energoresource
https://securityaffairs.co/wordpress/131264/hacktivism/anonymous-oprussia-updates.html
Exploit: Nation-State (Hacktivism)
SOCAR Energoresource: Oil Company



Risk to Business: 2.776 = Moderate
SOCAR Energoresource, a company partially owned by the State Oil Company of Azerbaijan Republic (SOCAR), has been hit in a cyberattack by the Anonymous Collective. The company operates the Antipinsky Refinery and several oilfields in Russia. The hacktivist group released a 130 GB archive via DDoSecrets that contains nearly 116,500 emails. Other Russian organizations also felt the sting of an attack by Anonymous in the last week or so including the Polar Branch of the Russian Federal Research Institute of Fisheries and Oceanography, the Achinsk City Government and the Port and Railway Projects Service of JSC UMMC.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Hacktivism isn’t only a factor in nation-state cybercrime and could impact all kinds of businesses and institutions.
ID Agent to the Rescue Take action now to reduce your clients’ nation-state cybercrime risk with our Are You Doing These 5 Things to Protect Your Clients from Nation-State Cybercrime? checklist. GET IT>>


Get 10 tips to help you build a strong security culture & reduce your risk of cybersecurity trouble! GET INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Go Inside the Ink to see how today’s biggest threats can impact your MSP and your customers in our blog.
- 7 Factors That Influence Phishing Risk
- The Secret to Building a Great Security & Compliance Awareness Training Program
- The Nuts and Bolts of Dark Web Monitoring + How It Stops Insider Threats
- 10 Facts About Nation-State Cybercrime That Impact Businesses
- The Week in Breach News: 05/04/22 – 05/10/22


Just getting started in cybersecurity? This resource bundle will help you get up to speed to protect your clients fast! GET IT>>


Fresh Resources
A Trio of Profitable Webinars is Here
Watch these webinars to see how you can increase your revenue and sell more security!
Dark Web ID & Passly Product Update: Explore the feature and function updates ahead for Dark Web ID and get an update on Passly. WATCH NOW>>
BullPhish ID & Graphus Product Update: Learn about innovations that will improve your client’s security and your team’s quality of life. WATCH NOW>>
The Tools and Techniques for MSPs to Close More New Clients: Learn the secret to closing more new deals and overcoming objections fast! WATCH NOW>>
Did you miss… Our 6 Tips for Implementing Zero Trust Security infographic? DOWNLOAD IT>>


Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>




3 Reasons Why Dark Web Monitoring is a Must-Have for Every Client
Plus 3 Tips to Help You Choose the Right Solution
The dark web is where some of the nastiest existential threats to organizations get their start including ransomware, hacking and phishing. It’s also the marketplace that bad actors use to source assets for cyberattacks like credentials and malware. In a world of economic uncertainty, cybercrime is a sector that’s booming, and that isn’t good news for anyone but the bad guys. Take a look at a few compelling reasons why keeping an eye on potential risks emerging from the dark web is a must in today’s volatile threat landscape.


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>
Why Do All of Your Clients Need Top-Notch Dark Web Monitoring?
The dark web is bigger and busier than ever, with the brisk pace of trade in dark web markets, an abundance of stolen data, growth in the skilled labor pool and innovation in cybercrime tools brewing up a storm of risk.
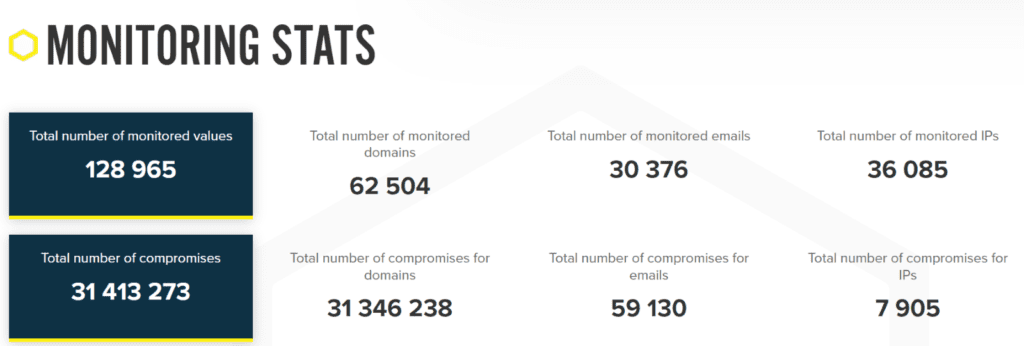
We See Danger Growing with Dark Web ID
Here’s a snapshot of the escalating dark web compromise danger that our analysts observed when monitoring dark web-related compromises in 2021 with Dark Web ID.



Dive into how to reduce your client’s risk of phishing fast with the tips in The Phish Files. DOWNLOAD NOW>>
Increasing Pools of Stolen Data on the Dark Web Make Recycled & Reused Passwords an Ever-Increasing Source of Danger
There has been a 429% increase in the number of corporate login details with plaintext passwords exposed on the dark web since 2020. Adding fuel to the fire, people just will not stop reusing and recycling passwords, frequently reusing the same ones between their business and personal accounts. A whopping 82% of workers admitted sometimes reusing the same passwords and credentials. That propensity to reuse passwords increases credential compromise risk for their employers, because every reuse is an opportunity for that password to become compromised. An estimated 60% of passwords that appear in more than one breach are recycled or reused.
The 20 Most Common Passwords Found on the Dark Web
- 123456
- 123456789
- Qwerty
- Password
- 12345
- 12345678
- 111111
- 1234567
- 123123
- Qwerty123
- 1q2w3e
- 1234567890
- 000000
- DEFAULT
- Abc123
- 654321
- 123321
- Qwertyuiop
- Iloveyou
- 666666
Source: CNBC


Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>
More Skilled Labor & Better Cybercrime Tools Create Fertile Ground for Cybercrime Growth
Cybersecurity Ventures estimates that cybercrime raked in $6 trillion in 2021, in large part because of the growing Cybercrime-as-a-Service (CaaS) economy on the dark web. Cybercrime specialists are everywhere, selling their services in all of the places where cybercriminals congregate like message boards, Discord servers and Telegram channels. Demand is high for skilled hackers. Major players in the cybercrime world, from nation-state threat actors to the biggest ransomware outfits are also major players in the cybercrime-as-a-service economy, and they’re more than happy to outsource parts of their operations or hire specialist freelancers to get the job done.
Many of those specialists are into software development. An estimated 300,000 thousand new pieces of malware are created daily. Those new resources become part of the Malware-as-a-Service (MaaS) and its offshoot Ransomware-as-a-Service (RaaS) ecosystem. This growing cybercrime industry is a business model that offers the usage of ‘pay-and-use’ malware for conducting cybercrime, maintained by developers just like any other software. The bad guys can also subcontract for phishing through a Phishing-as-a-Service specialist. According to Microsoft researchers, a PhaaS group’s monthly subscription prices vary dependent on a host of factors, but in general, the service can cost about $800 per month. Many of these operators offer what amounts to a one-stop shop for phishing. featuring everything from DIY kits to full-service contracting.


Find the right dark web monitoring solution for your customers & your MSP with this checklist! DOWNLOAD IT>>
3 Tips for Choosing the Right Dark Web Monitoring Solution
Surging cybercrime comes with surging dark web risk. You and your clients deserve to have the confidence that comes from knowing that you’ve got the right solutions in place for a strong defense to keep that risk from stressing you out. These 3 tips can help you find the right dark web monitoring solution.
Integrating a quality dark web monitoring solution should be simple
Adding dark web monitoring to your client’s defensive buildout or upgrading your client’s current solution is easy these days. Today’s high-quality dark web monitoring solutions set up quickly and get to work immediately with features like:
- Automation that powers deployment in minutes
- SaaS or API options available
- No additional hardware or software to install
- Out-of-the-box integrations with popular PSA platforms
- Monthly and quarterly Digital Risk Review reports that prove the ongoing value of monitoring to your clients, helping you renew contracts
Get more for your money when you choose a partner that’s invested in you too
Along with a best-in-class solution for you to offer to your customers, a fantastic partner enablement program from the vendor that you’re partnering with is a must-have. You’ll benefit from accessing a wealth of resources like complete, brandable marketing campaigns for your MSP and ongoing sales education for your team – even sales experts to assist with hands-on help to close important deals.
Innovation matters to stay a step ahead of the bad guys
You can’t rely on the same technology to provide the same protection year after year. Strong, effective security requires solutions that don’t just rest on their laurels but keep moving forward, refining and evolving their technology to meet the current and future needs of the market. Offer your clients a dark web monitoring solution with a proven track record of successful innovation.


Get a step-by-step guide to building an effective security and phishing awareness training program. GET GUIDE>>
You and Your Clients Deserve the Satisfaction and Peace of Mind That Comes from Teaming Up with a Winner
Dark Web ID has been an industry leader for years and we’re still the top dog because we never stop innovating to keep businesses out of dark-web-related credential compromise trouble.
- Get the clear, actionable insight that you need to make all the right security moves with Dark Web ID, the dark web monitoring platform trusted by organizations worldwide.
- 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses
- Uncover compromised credentials in Dark Web markets, data dumps and other sources, and get fast alerts to new ones
- An easy-to-use, automated monitoring platform that deploys in minutes and gets to work immediately, with SaaS or API options available
Schedule your demo of Dark Web ID today. BOOK IT>>
Join the over 4,000 MSPs who are prospering as an ID Agent Partner and you’ll gain access to the best sales enablement program in the business through Kaseya Powered Services.


See how security awareness training grows your MRR + get tips for selling it! WATCH NOW>>


May 19: Channel-Sec: The Security Event for the European IT Channel REGISTER NOW>>
May 19: Building a Foundation of Security: Identify & Assess REGISTER NOW>>
May 24: Phish & Chips Demo Webinar (EMEA) REGISTER NOW>>
May 24-25: ASCII MSP Success Summit – Boston REGISTER NOW>>
May 26: Building a Foundation of Security: Protect & Train REGISTER NOW>>
Jun 2: Building a Foundation of Security: Document REGISTER NOW>>
Jun 6 – 7: ChannelPro SMB Forum 2022: Southwest (Dallas) REGISTER NOW>>
Jun 6 – 8: IT Nation Secure 2022 REGISTER NOW>>
Jun 9: Building a Foundation of Security: Backup & Recover REGISTER NOW>>
Jun 20-23: Connect IT Global in Las Vegas REGISTER NOW>>


It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>


Dark Web Danger is Mounting
The dark web is a major economic engine. If it was measured as a country, the dark web would have the world’s third-largest economy, after the U.S. and China. That’s great news for cybercriminals but not very good news at all for businesses.
That makes it critical that businesses be sure that they’ve got strong defenses in place that can help them mitigate the risk of trouble from the dark web like dark web monitoring to prevent unpleasant surprises caused by compromised credentials.
Don’t wait until the bad guys are on your doorstep with a compromised credential in hand that’s going to get them inside your company’s environment. Talk to your MSP about making sure that you’ve got your organization’s credentials protected with dark web monitoring.


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this post (in part or in its entirety) When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!