6 Ways Insecure Passwords Can Damage Your Organization

See Why Dark Web Monitoring is a Powerful Weapon Against Insider Threats
Does your organization have compromised credentials floating around? Chances are that the answer is yes. An estimated 60% of data breaches involved the improper use of credentials in 2021. Credential compromise is a major cyberattack and breach risk for every organization that grows daily as more and more data makes its way to the dark web. That data includes an abundance of stolen usernames and passwords. Cybercriminals can easily scoop up big lists of passwords in dark web markets or dumps. They can also buy credentials straight from malicious employees. There are myriad ways that credentials could be your company’s Achilles heel.

Security and compliance training pays amazing dividends. Get tips to run an effective program with our how-to guide! GET GUIDE>>
Dark Web Credential Compromise Risk is Rising
From SMBs to giant multinationals, it doesn’t matter how high-flying a company is either. Password problems will still plague them. A trove of exposed data about Fortune 1000 companies on the dark web was uncovered by researchers earlier this year, including passwords for 25.9 million Fortune 1000 corporate user accounts. Digging deeper, they also unearthed an estimated 543 million employee credentials from Fortune 1000 companies circulating on commonly used underground hacking forums, a 29% increase from 2020. Altogether, they were able to determine that 25,927,476 passwords that belong to employees at Fortune 1000 companies are hanging out on the dark web. That’s an estimated 25,927 exposed passwords per Fortune 1000 company, marking a 12% increase in password leaks from 2020.
Looking at the pharmaceutical sector as an example of the danger of exposed credentials, it’s easy to see that the password problem is growing worse every year. In a recent study, researchers identified more than 4.5M exposed records in an approximate 10K breaches and leakages that exposed the corporate credentials of employees from the top 20 Fortune 500 pharmaceutical companies between 2018 and 2021. In a sample analysis of credential exposure for 78 executives from top pharma companies, researchers discovered that 58% of executives have had their corporate credentials including privileged passwords exposed in a third-party breach or leakage since 2018. Illustrating rising danger, researchers also discovered that approximately 59% of total breaches and 76% of total exposed records identified in the report occurred since 2020.
User credentials are the key that unlocks the door to an organization’s systems and data. Unfortunately, it’s far too easy for bad actors to get a copy of that key on the dark web.
- An estimated 15 billion unique logins are circulating on the dark web right now.
- The average organization is now likely to have 17 sets of login details exposed on the dark web.
- The credentials of 133,927 C-level Fortune 1000 executives are accessible in dark web markets.
- There has been a 429% increase in the number of corporate login details with plaintext passwords exposed on the dark web since 2020.

Credential Compromise is More Frequent Than You Think
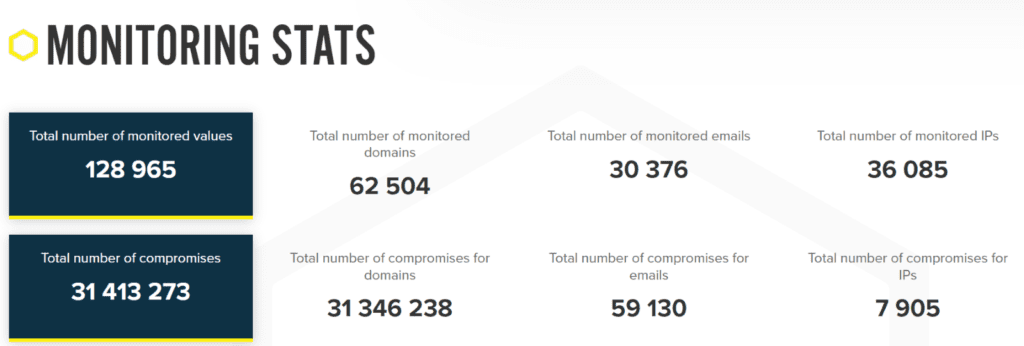
This is what our analysts observed through Dark Web ID in 2021. The number of credential compromises that we discover just keeps getting bigger as time goes on, and the likelihood of a nasty credential compromise-related surprise is constantly increasing for companies of every size in every sector.

Considering a new dark web monitoring solution? This eBook helps you find the right one for your organization. GET EBOOK>>
People Never Stop Making Passwords That Are Easily Compromised
Always a security bugbear, people just cannot stop making bad passwords. Research by the UK’s National Cyber Security Centre (NCSC) shows that employees will choose memorability over security when making a password every time. Their analysts found that 15% of people have used their pet’s name as their password at some point, 14% have used the name of a family member,13% have used a significant date, such as a birthday or anniversary and another 6% have used information about their favorite sports team as their password. U.S. companies aren’t any better off. In fact, their bad password problems are just a little bit worse. 59% of Americans use a person’s name or family birthday in their passwords, 33% include a pet’s name and 22% use their own name.
The 20 Most Common Passwords Found on the Dark Web
- 123456
- 123456789
- Qwerty
- Password
- 12345
- 12345678
- 111111
- 1234567
- 123123
- Qwerty123
- 123456789
- 1q2w3e
- DEFAULT
- 000000
- Abc123
- 654321
- 123321
- Qwertyuiop
- Iloveyou
- 666666
Source: CNBC

Drill down to the bottom line to see why security & compliance awareness training is a smart investment. GET IT>>
Password Reuse and Recycling is A Bad Practice That’s Getting Worse
The average organization is now likely to have about 17 sets of login details available on the dark web for malicious actors to enjoy, and they’re making the most of those resources. An estimated 60% of passwords that appeared in more than one breach in 2020 were recycled or reused, a factor that every company should keep in mind when creating and setting password security policies. The average adult has an estimated 100 passwords floating around that they’re using, and every one has the potential to be a problem if they recycle them. Employees aren’t making the mistake of reusing passwords from ignorance either. Over 90% of participants in a password habits survey understood the risk of password reuse but that didn’t stop them because 59% admitted to doing it anyway.
That disconnect is a huge problem for businesses everywhere and a fast path to trouble. These 3 password reuse and recycling corollaries bring added complications.
Password Sharing
Employees are also sharing their passwords with other people at an alarming rate, including folks who don’t work at the same company. Over 30% of respondents in a Microsoft study admitted that their organization had experienced a cybersecurity incident as a result of compromised user credentials that had been shared with people outside their companies.
- 43% of survey respondents have shared their password with someone in their home
- 22% of employees surveyed have shared their email password for a streaming site
- 17% of employees surveyed have shared their email password for a social media platform
- 17% of employees surveyed have shared their email password for an online shopping account
Malicious Insiders
Credentials are a hot commodity on the dark web. While most username and password pairs hit the market through data breaches, it pays for organizations to remember that bad actors don’t always come from outside. Malicious insider actions like selling credentials result in an estimated 25% of data breaches. Legitimate credentials for even a small company can sell for a pretty penny, and the top motivator for malicious insiders to act is money. An average legitimate employee credential can go for over $3,000. But that is far from the top price a really useful, privileged password can fetch in the booming dark web data markets, like executive and administrator credentials. Those types of credentials can go for as much as $120,000 and it’s an investment that cybercrime gangs are more than happy to make.
Zombie Accounts
Don’t overlook the possibility that a former employee still has a working password that allows them to access systems, accounts and data. Companies that aren’t careful about removing access and permissions from departing employee accounts can get burned by both dark web credential exposure and unauthorized user activity. In a 2021 study, researchers determined that after their employment ended, many former workers still had access to the systems, tools and solutions that they used at their former job including old email accounts (35%), work-related materials on a personal account (35%), social media (31%), software accounts (31%) or shared files or documents (31%). Many also retained access to things like accounts with a third-party system (29%), another employee’s account (27%), a backend system (25%) and the company’s financial information (14%).

Learn 5 red flags that could indicate a malicious insider is at work in your organization! DOWNLOAD INFOGRAPHIC>>
Prevent Dark Web Credential Compromise Disasters with Dark Web ID
Dark web monitoring with the award-winning Dark Web ID helps organizations find and fix credential compromises before the bad guys have a chance to strike.
- 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses
- Uncover compromised credentials in Dark Web markets, data dumps and other sources, and get fast alerts to new ones
- An easy-to-use, automated monitoring platform that deploys in minutes and gets to work immediately, with SaaS or API options available
- Schedule your demo of Dark Web ID today. BOOK IT>>

Are your users ready to handle all of the risks they face daily? Make sure you’ve covered all the bases! GET A CHECKLIST>>
Innovation Matters to Stay a Step Ahead of the Bad Guys
You can’t rely on the same technology to provide the same protection year after year. Strong, effective security requires solutions that don’t just rest on their laurels but keep moving forward, refining and evolving their technology to meet the current and future needs of the market. Dark Web ID has been an industry leader for years because we never stop innovating to keep businesses out of credential compromise trouble.
Get the clear, actionable insight that you need to make all the right security moves with Dark Web ID, the dark web monitoring platform trusted by organizations worldwide.
- 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses
- Uncover compromised credentials in Dark Web markets, data dumps and other sources, and get fast alerts to new ones
- An easy-to-use, automated monitoring platform that deploys in minutes and gets to work immediately, with SaaS or API options available
Schedule your demo of Dark Web ID today. BOOK IT>>

Get ready to pack your bags for Connect IT 2022! Join us June 20-23 in Las Vegas for the industry’s premier event! REGISTER NOW>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!