The Week in Breach News: 05/24/23 – 05/30/23

This week: Ransomware puts the brakes on production at Suzuki Motorcycle, BlackByte demands $400 million from beleaguered Augusta, Georgia, a fresh integration between Graphus and Datto SaaS Protection and what you need to know about dangerous activity by Chinese threat actors Volt Typhoon.

Find out how Datto EDR helps with Health Insurance Portability and Accountability Act (HIPAA) compliance. GET INFO>>

Casepoint
https://techmonitor.ai/technology/cybersecurity/casepoint-ransomware-blackcat
Exploit: Ransomware
Casepoint: Legal Technology Platform

Risk to Business: 1.886 = Severe
BlackCat has claimed responsibility for a ransomware attack impacting Casepoint, a legal technology platform used by the Securities and Exchange Commission and the Department of Defense as well as major brands. The bad actors claim to have stolen 2TB of company data including sensitive files like attorney notes, publishing what appears to be an ID scan and a certificate as proof of the hack. No information about a ransom amount had been released at press time.
How It Could Affect Your Customers’ Business: Law firms handle all kinds of sensitive data that could be used by cybercriminals in blackmail schemes.
Kaseya to the Rescue: Data is a commodity on the dark web. Learn more about the dark web risks that businesses face in The IT Professional’s Guide to the Dark Web. DOWNLOAD IT>>
Managed Care of North America (MCNA) Dental
Exploit: Hacking
Managed Care of North America (MCNA) Dental: Insurer





Risk to Business: 1.876 = Severe
Managed Care of North America (MCNA) Dental, one of the biggest government-sponsored (Medicaid and CHIP) dental care and oral health insurance providers in the U.S., has announced a data breach that could impact nine million people. MCNA noted that it became aware of unauthorized access to its computer systems on March 6th, 2023. Patient data that may have been exposed in this incident includes a patient’s full name, address, date of birth, phone number, email, Social Security number, driver’s license number, government-issued ID number, health insurance (plan information, insurance company, member number, Medicaid or Medicare ID numbers), plans of care for teeth or braces (visits, dentist name, doctor name, past care, x-rays/photos, medicines, and treatment), bills and insurance claims information.
How It Could Affect Your Customers’ Business: Information about dental care is still protected health data, making this an expensive mess to clean up.
Kaseya to the Rescue: Develop an effective, efficient incident response plan with the tips in our guide How to Build an Incident Response Plan. GET YOUR GUIDE>>
SimpleTire
https://www.infosecurity-magazine.com/news/database-error-leaks-one-million/?&web_view=true
Exploit: Misconfiguration
SimpleTire: Tire Retailer




Risk to Business: 2.769 = Moderate
Philadelphia-based tire retailer SimpleTire is in hot water after a database configuration error led to the exposure of 1TB of records. Internet researchers uncovered a non-password protected database that was publicly accessible to anyone with an internet connection for at least three weeks before finally being locked down. The SimpleTire database contained over 2.8 million records, including nearly 1.2 million order confirmation PDFs. Possibly exposed data for customers includes customer names, phone numbers and billing addresses as well as partial credit card numbers and expiration dates.
How It Could Affect Your Customers’ Business: Employee mistakes lie misconfiguring a database can be just as dangerous and expensive to handle as a cyberattack.
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET IT>>
The City of Augusta, Georgia
https://www.theregister.com/2023/05/26/blackbyte_augusta_malware/?&web_view=true
Exploit: Ransomware
The City of Augusta, Georgia: Municipal Government





Risk to Business: 1.719 = Severe
The BlackByte ransomware gang has claimed responsibility for a ransomware attack that has impacted the city of Augusta, Georgia. The ransomware attack took down city websites that are being slowly restored. BlackByte also claims to have snatched sensitive data, leaking a sample of 10GB of data as proof. The data sample posted contains payroll information, contact details, personally identifiable information (PII), physical addresses, contracts and city budget allocation data. BlackByte appears to be demanding a ransom of $400,000.
How It Could Affect Your Customers’ Business: Governments and government agencies at every level have been prime targets for cyberattacks in the last few years.
Kaseya to the Rescue: Learn more about defending against often email-based cyberattacks like ransomware in our eBook A Comprehensive Guide to Email-Based Cyberattacks GET EBOOK>>
Fresh Del Monte Produce
https://www.jdsupra.com/legalnews/fresh-del-monte-produce-notifies-8673018/
Exploit: Hacking
Fresh Del Monte Produce: Agriculture Company




Risk to Business: 2.781 = Moderate
Fresh Del Monte Produce has filed a data breach notification saying that some employee information may have been stolen in a data security incident. The data breach occurred in January 2023, when Fresh Del Monte first noticed unauthorized activity on its network. The breached information varies depending on the individual, it may include current and former employees. The information exposed includes the employee’s name, Social Security number, driver’s license number, passport number, financial account information and protected health information.
How it Could Affect Your Customers’ Business: Employee data is a treasure trove for bad actors that often nets them PII and financial information.
Kaseya to the Rescue: Explore how security awareness training helps businesses defend against today’s most dangerous cyber threats in this infographic. DOWNLOAD IT>>
Apria Healthcare
https://www.theregister.com/2023/05/23/apria_healthcare_breach/?&web_view=true
Exploit: Hacking
Apria Healthcare: Medical Equipment Company





Risk to Business: 1.826 = Severe
Apria Healthcare has disclosed that a data security incident in its network may have led to data exposure for two million people. In a strange twist, Apria said that it discovered the intrusion in late 2021 and it is just informing people who were affected now. Apria also said that it didn’t believe any of the exposed data had been misused. Instead, Apria’s data breach letter to people potentially impacted stated that Apra “believes the purpose of the unauthorized access was to fraudulently obtain funds from Apria and not to access personal information of its patients or employees.” Exposed patient data includes personal, medical, health insurance and financial information, financial information including bank account and credit card numbers in combination with security codes, access codes, passwords and account PINs and Social Security numbers.
How it Could Affect Your Customers’ Business: Waiting so long to tell customers that their data had been exposed isn’t a good look and may impact this company’s reputation.
Kaseya to the Rescue: Learn how Datto EDR satisfies most cyber insurance requirements for endpoint protection and endpoint detection and response (EDR). GET INFORMATION>>


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>


India – Insurance Information Bureau of India (IIB)
Exploit: Ransomware
Insurance Information Bureau of India (IIB): Insurance Analyst




Risk to Business: 2.807 = Moderate
The Insurance Information Bureau of India (IIB), an industry repository of data and analytics, has been hit by a ransomware attack. The attack took place between March 30 and April 3, 2023, and first came to light in April. Compromised administration accounts enabled bad actors to deploy ransomware, knock out IBB’s website and encrypt its data. No group has claimed responsibility, but news outlets are reporting that a $250,000 ransom has been demanded.
How it Could Affect Your Customers’ Business: compromised credentials are the bane of every IT department and a hacker’s best friend.
Kaseya to the Rescue: Email is the most likely way for employees to encounter cyberattacks like ransomware. This checklist helps companies strengthen their email security. GET CHECKLIST>>
India – Suzuki Motorcycle
Exploit: Ransomware
Suzuki Motorcycle: Motorcycle Factory


Risk to Business: 1.386 = Extreme
Suzuki Motorcycle has experienced an operational disruption as the result of a successful ransomware attack. Production of bikes and scooters at Suzuki Motorcycle’s Indian plant has ground to a halt resulting in a loss of an estimated 20,000 vehicles. The company has also postponed its annual supplier conference, likely as a result of the attack. No group has claimed responsibility and no ransom demand has been made public. Suzuki says that the incident is under investigation.
How it Could Affect Your Customers’ Business: This loss in productivity is a disaster for Suzuki and the revenue will be hard to recoup.
Kaseya to the Rescue: This infographic can help businesses and MSPs create a comprehensive security awareness training policy that supports a strong training program. GET INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>




A New Integration Lets You See Graphus Threat Counts Across All SaaS Protection Clients
The Graphus and Datto SaaS Protection teams are excited to announce a new workflow integration between their products which allows you to see which client domains are protected and how many threats were quarantined by Graphus on your SaaS Protection Status page.
You can now see whether Graphus is protecting your domains or clients, and for the protected clients, how many email threats were quarantined.
Rapidly Deploy Graphus to Unprotected SaaS Protection Clients
If a client’s domain is not yet protected and you want to activate Graphus for it, or you want to investigate a quarantined threat, you will be directed to the appropriate page within Graphus to do so.
Connect your SaaS Protection account with your Graphus account and the Graphus API will push real-time data to your SaaS Protection Status page in the Datto Partner Portal. Together with Graphus, SaaS Protection clients now have a better way to prevent data loss from occurring in Microsoft 365 or Google Workspace with an extra layer of protection.
Learn more about this integration here.


This infographic helps IT professionals get the most out of a security awareness training solution. DOWNLOAD IT>>


Datto EDR HIPAA Compliance Whitepaper
Learn how Datto EDR helps protect patient information and helps ensure that appropriate security measures are in place to comply with the Health Insurance Portability and Accountability Act (HIPAA) regulations.
Did you miss…? EDR + Managed SOC is a Game-Changer DOWNLOAD IT>>






Chinese Threat Actor Volt Typhoon Menaces Infrastructure
On May 24, the United States National Security Agency (NSA), the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the U.S. Federal Bureau of Investigation (FBI), the Australian Signals Directorate’s Australian Cyber Security Centre (ACSC), the Communications Security Establishment’s Canadian Centre for Cyber Security (CCCS), the New Zealand National Cyber Security Centre (NCSC-NZ) and the United Kingdom National Cyber Security Centre (NCSC-UK) released a joint advisory (alert number AA23-144a) about an emerging threat from Volt Typhoon, a People’s Republic of China (PRC) state-sponsored threat actor. Our expert analysts at Datto EDR reviewed the advisory and determined how our customers might encounter Volt Typhoon and how security solutions like Datto EDR can help combat this kind of activity.


Learn how Datto EDR satisfies cyber insurance requirements for endpoint protection & EDR. DOWNLOAD REPORT>>
Who is at risk and why?
So far, this actor has only targeted entities within the U.S. critical infrastructure sector. On May 28, the United States Navy confirmed that it had been impacted by cyberattacks by Volt Typhoon. The New York Times noted that the first actions by Volt Typhoon appear to have been concentrated on telecommunications networks in Guam. Volt Typhoon has hit organizations in a wide variety of sectors including the communications, manufacturing, utility, transportation, construction, maritime, government, information technology and education sectors.
Experts believe that Volt Typhoon’s goal is to facilitate espionage over time and potentially lay the groundwork for attacks to further other political objectives. Microsoft noted that Volt Typhoon has been at work since mid-2021. In that time, the threat actor has primarily targeted critical infrastructure organizations in Guam and elsewhere in the United States. The New York Times reports that U.S. intelligence officials have expressed concern about Volt Typhoon’s motives because of Guam’s strategic importance to the United States, especially in relation to any potential future Chinese military action against Taiwan.


Get the scoop on 5 of the worst email-based attacks plus tips to protect businesses from them. GET INFOGRAPHIC>>
What are some Tactics, Techniques and Procedures (TTPs) used by Volt Typhoon?
Volt Typhoon leverages highly stealthy TTPs. They do not use much malware and instead rely almost exclusively on living-off-the-land techniques and hands-on-keyboard activity while often routing their outbound C2 traffic from compromised endpoints through compromised small office and home office network devices (SOHO) they have throughout the world. These SOHO devices, manufactured by ASUS, Cisco, D-Link, NETGEAR and Zyxel, allow the owner to expose HTTP or SSH management interfaces to the internet and are used by the actor to receive C2 communications. What this means Is that traffic will look like its’ going to other small businesses and not a country destination like China.
Living off the land methodologies use built-in network administration tools on the victim networks. These TTPs allow the actor to blend in with normal Windows system and network activities. Some of the built-in tools this actor uses are: wmic, ntdsutil, netsh and PowerShell.
Volt Typhoon Attack Diagram
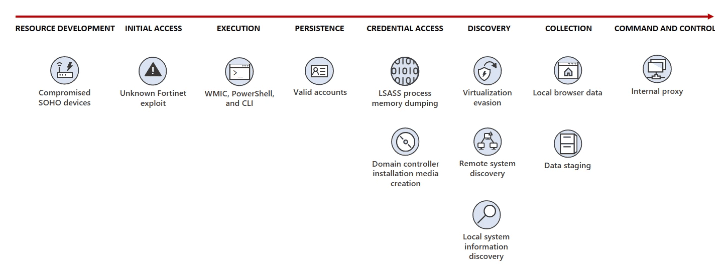

Source: Microsoft


Get tips & advice to help you build a smart incident response plan in our guide. GET YOUR GUIDE>>
How do you detect adversaries like Volt Typhoon in your environment?
Endpoint detection and response (EDR) solutions are necessary to detect the misuse of these living-off-the-land utilities. Basic antivirus, app allow-listing, and endpoint protection versions will be ineffective. Several techniques will be somewhat noisy so you should not expect very many individual techniques to trigger high priority alerts: instead, multiple events should be correlated together to identify these and alert on them. Datto EDR’s correlation engine does this automatically and will provide sufficient visibility.
What are some of Datto EDR’s capabilities in this instance?
Datto EDR analysts assessed our analytics and found existing detection coverage sufficient to detect over a half dozen behavioral techniques used by this actor.
Example: All of this actor’s techniques for credential access and password stealing have confirmed analytic coverage.


Image: Command run by threat actor to dump password storage in memory
For this command, you will see a high severity alert that reads: “(Credential Access-T1003) Process memory dump via ComsvcsDLL detected”
In addition, we are also reviewing opportunities for new analytics and rules to detect actors like this based off the reports.
Novel or interesting properties of these attacks:
The use of vulnerable and compromised SOHO routers in remote networks to route traffic is very interesting but does not present a good detection opportunity for defenders so we’ll have to rely on EDR telemetry as network-based detection will be difficult.
New Credential Access Technique: The use of the command-line tool Ntdsutil.exe to create installation media from domain controllers, while not the first actor to do it, is rare and interesting. This technique makes the domain controller store several domain controller password hashes with the installation media so takes the place of using a typical/known Credential Access technique or tool. New analytic rules are being tested for Datto EDR now and will be deployed shortly.


See why EDR is the perfect investment to make in your future right now in our buyer’s guide. DOWNLOAD IT>>
Stop cyberattacks fast with Datto EDR
Datto and Kaseya offer a range of security solutions that can help you prevent, detect, respond and recover from malicious activity like this like Datto EDR.
Datto EDR – Endpoint Detection Made Easy
Datto EDR empowers IT teams to detect and respond to advanced threats quickly and efficiently. An easy-to-use cloud-based EDR solution that’s purpose-built for Managed Service Providers (MSPs), Datto EDR defends all endpoints: desktops, notebooks and servers, across Windows, MacOS and Linux operating systems and integrates seamlessly with Managed SOC and Datto RMM.
- Patented deep memory analysis ensures that you’re informed of even the most elusive threat actors.
- Take action against advanced threats right from your alert dashboard to isolate hosts, terminate processes, delete files and more without wasting precious seconds.
- Alerts are mapped to the MITRE ATT&CK framework to provide context and helpful clarity to your team.


Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>


Learn How to Gain True Protection from Phishing Attacks
A phishing threat can quickly escalate to a disastrous security incident if just one employee falls for scammers’ tricks. Join us on June 13 at 2 PM ET / 11 AM PT for an informative webinar where our Channel Development Manager, Miles Walker, will discuss how you can gain comprehensive protection from phishing attacks with BullPhish ID and Graphus. REGISTER NOW>>
June 8: Kaseya + Datto Connect Local Belgium REGISTER NOW>>
June 8: Kaseya + Datto Connect Local Toronto REGISTER NOW>>
June 13: Kaseya + Datto Connect Local Philadelphia REGISTER NOW>>
June 14: Kaseya + Datto Connect Local Chicago Security for IT Professionals Series REGISTER NOW>>
June 15: Kaseya + Datto Connect Local Chicago Security & Compliance Track REGISTER NOW>>
June 20: Kaseya + Datto Connect Local Tampa REGISTER NOW>>
June 22: Kaseya + Datto Connect Local Atlanta REGISTER NOW>>
June 26-28: Kaseya DattoCon Europe in Dublin REGISTER NOW>>
July 11: Kaseya + Datto Connect Local Anaheim REGISTER NOW>>
July 18: Kaseya + Datto Connect Local Boston REGISTER NOW>>
July 20: Kaseya + Datto Connect Local Baltimore REGISTER NOW>>
July 21: Kaseya + Datto Connect Local Baltimore IT Professionals Series REGISTER NOW>>
October 2 – 4: Kaseya DattoCon in Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!