The Week in Breach News: 06/28/23 – 07/04/23

Breaches abound at government and quasi-government agencies, an unrest-related communications cyberattack in Russia and how businesses plan to overcome 5 big cybersecurity challenges.

See the keys to selecting a Managed SOC to find the perfect one for your clients & your MSP. GET CHECKLIST>>

Wealth Enhancement Group
https://www.jdsupra.com/legalnews/wealth-enhancement-group-notifies-6520334/
Exploit: Credential Compromise
Wealth Enhancement Group: Financial Services

Risk to Business: 1.886 = Severe
Minnesota-based financial services firm Wealth Enhancement Group has reported a data breach to regulators in Maine. The company said that it detected that an unauthorized individual had gained access to one of its servers through credential compromise in early April. Stolen data may include clients’ full names, Social Security numbers, addresses, dates of birth, phone numbers, email addresses, driver’s license numbers, state identification numbers and financial account numbers. Data breach letters were sent on June 28 to impacted clients.
How It Could Affect Your Customers’ Business: Protecting an organization’s credentials from compromise has never been more critical.
Kaseya to the Rescue: Credential com[promise isn’t the only risk that businesses face from the dark web. Learn about five dark web dangers for businesses in this infographic. GET INFOGRAPHIC>>
U.S. Department of Health and Human Services (HHS)
https://www.cnn.com/2023/06/29/politics/us-health-department-cyberattack/index.html
Exploit: Supply Chain
U.S. Department of Health and Human Services (HHS): Federal Agency





Risk to Business: 1.876 = Severe
The U.S. Department of Health and Human Services (HHS) has notified Congress of a data breach that may have exposed sensitive data for 100,000 people. HHS said that an unnamed contractor had been caught up in the flood of cyberattacks around the MOVEit exploit. HHS said that none of its own systems or data were accessed by cybercriminals and its network remains safe. Several other federal agencies have been hit by the MOVEit exploit either directly or through a supplier/contractor.
How It Could Affect Your Customers’ Business Supply chain risk is high and climbing for every organization. Businesses should take action now to reduce it.
Kaseya to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET THE FACT SHEET>>
U.S. Patent and Trademark Office (USPTO)
https://www.cshub.com/attacks/news/iotw-us-patent-and-trademark-office-suffers-years-long-data-leak
Exploit: Misconfiguration
U.S. Patent and Trademark Office (USPTO): Federal Government Agency



Risk to Business: 1.469 = Severe
The U.S. Patent and Trademark Office (USPTO) has disclosed that it has experienced a years-long data leak that exposed the location data of thousands of trademark applicants. The leak is estimated to have been ongoing for the past three years; it was active from February 2020 to March 2023. The leak was caused by an error in one of USPTO’s application programming interfaces (APIs). A notice about the breach was sent to affected trademark applicants.
How It Could Affect Your Customers’ Business: Security awareness training isn’t just for cyberattacks, it also helps employees become more conscientious about security overall to limit mistakes.
Kaseya to the Rescue: Our eBook How to Build a Security Awareness Training Program helps IT professionals design and implement an effective training program quickly. DOWNLOAD IT>>


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>


United Kingdom – Barts Health NHS Trust
Exploit: Ransomware
Barts Health NHS Trust: Medical Facility Operator





Risk to Business: 2.149 = Severe
Barts Health NHS Trust has disclosed that it has been the victim of a ransomware attack by the notorious gang ALPHV/BlackCat that exposed the sensitive data of 2.5 million patients. BlackCat claimed to have snatched 7 terabytes of data including unspecified patient data, employees’ personal data and financial information including credit card details last Friday. The incident is under investigation.
How It Could Affect Your Customers’ Business: Healthcare data of all kinds is a valuable commodity for bad actors, and ransomware attacks against healthcare providers are climbing.
Kaseya to the Rescue: Explore how security awareness training helps organizations defend against today’s most dangerous cyber threats in this infographic. DOWNLOAD IT>>
United Kingdom – National Health Service
Exploit: Third Party
National Health Service (NHS): National Government Agency





Risk to Business: 2.637 = Severe
The UK’s National Health Service has disclosed that it may have had sensitive health data pertaining to 1.1 million patients from 200 hospitals after a June 6 cyberattack on research partner The University of Manchester. Initial estimates show that about 250 gigabytes of data was accessed by bad actors in the attack, including data on the university’s backup servers. The data was initially collected for research purposes and some people who had data stolen may not even know that the university had it. The investigation remains ongoing.
How it Could Affect Your Customers’ Business: Supply chain relationships aren’t the only relationships that endanger a company’s data; an attack on a partner can be equally devastating.
Kaseya to the Rescue: Learn more about the dark web economy and see how data like this gets bought and sold on the dark web in The IT Professional’s Guide to the Dark Web. DOWNLOAD IT>>
Ireland – Dublin Airport Authority (DAA)
https://simpleflying.com/dublin-airport-staff-information-compromised-july-2023/
Exploit: Supply Chain
Dublin Airport Authority: Transportation Authority



Risk to Business: 2.766 = Moderate
The Dublin Airport Authority (DAA) has disclosed that sensitive information belonging to approximately 2,000 airport workers was exposed in a cyberattack on pay and benefits service provider Aon. The airport authority did not offer specifics on the type of data stolen beyond saying that some employees’ pay and benefit information was exposed. Aon is another casualty of the MOVEit hack.
How it Could Affect Your Customers’ Business: Attacks using the MOVEit exploit have proliferated in every sector and the number of impacted organizations continues to grow daily.
Kaseya to the Rescue: See how the solutions in Kaseya’s Security Suite help IT professionals minimize risk, avoid cyberattacks and build a cyber-savvy workforce. WATCH THE WEBINAR>>
Russia – Dozor-Teleport CJSC
https://cyberscoop.com/russia-satellite-hack-wagner/
Exploit: Hacking (Nation-State)
Dozor-Teleport CJSC: Telecommunications Company



Risk to Business: 1.307 = Extreme
Russian telecom Dozor-Teleport CJSC has claimed that it is the victim of a cyberattack by supporters of the non-state-aligned PMC Wagner paramilitary group that is currently active in Russia. Dozor-Teleport CJSC is a communications satellite operator that provides internet and other communication services for Russian state agencies including Moscow’s main intelligence agency. Hackers stole nearly 700 files, defaced several websites and launched Wagner-related messages and a video on the company’s site. The damage is expected to take weeks to fix.
How it Could Affect Your Customers’ Business: Cyberattacks, especially ransomware and wiper malware, as well as hacking have become a part of modern warfare
Kaseya to the Rescue: BullPhish ID + Graphus together give companies powerful protection against phishing and email-based cybercrime including ransomware attacks. LEARN MORE>>


Find out how Datto EDR helps with Health Insurance Portability and Accountability Act (HIPAA) compliance. GET INFO>>


Taiwan – Taiwan Semiconductor Manufacturing Company (TSMC)
https://www.cnn.com/2023/06/30/tech/tsmc-supplier-ransomware/index.html
Exploit: Supply Chain
Taiwan Semiconductor Manufacturing Company (TSMC): Semiconductor Manufacturer



Risk to Business: 1.443 = Extreme
Taiwan Semiconductor Manufacturing Company (TSMC), the world’s leading contract chipmaker and one of Apple’s main suppliers, has confirmed that it has experienced a data breach due to a cyberattack on one of its suppliers. TSMC was listed on LockBit’s website as a victim, but TSMC claims that the data was stolen from supplier Kinmax, a system integrator. National Hazard Agency, a subgroup of LockBit, shared screenshots of directory listings of stolen TSMC files on its leak website as well as a demand for a stunning $70 million ransom.
How it Could Affect Your Customers’ Business: With the world already facing a chip shortage, anything that impacts the operations of a chipmaker is problematic.
Kaseya to the Rescue: In today’s volatile cybersecurity landscape, insurers are requiring businesses to have certain solutions in place. See how Datto EDR satisfies insurance requirements. LEARN MORE>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Explore how AI technology helps businesses mount a strong defense against phishing GET INFOGRAPHIC>>




2 New Campaigns from Powered Services Pro
Don’t miss these two new marketing campaigns from Powered Services Pro!
BCDR Essentials
When a disruptive event impacts a business, time is of the essence. Organizations must be prepared to quickly recover critical data, restore IT systems, and resume operations. A comprehensive business continuity and disaster recovery (BCDR) plan can help businesses bounce back quickly and minimize costly downtime.
Outsourced IT: Unlock Business Potential with an IT Service Provider
MSP Value Proposition:
As new technologies continue to emerge and business needs evolve, organizations must adapt and transform to stay secure, compliant, and competitive. Promote the value of outsourcing technology needs to an IT Service Provider who will make sure businesses have the right tools, support, and guidance to boost success and growth.
End Buyer Value Proposition:
In today’s rapidly changing, highly competitive business environment, technology is an essential component of success. Keeping up with technological advances and evolving IT needs can be too costly and challenging to handle on your own. Team up with a reliable IT Service Provider to ensure your business stays ahead of the competition.
Get these campaigns now in the Powered Services Pro Portal. GET THEM>>


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


Get Advice on the Keys to Selecting a Managed SOC Service
Managed SOC is a game-changer for MSPs and their clients. It puts world-class security expertise at your fingertips without a huge price tag. Download this data sheet to learn more about finding the right managed SOC for your clients and your MSP! DOWNLOAD IT>>
Did you miss…The 2023 IT Operations Survey Report? GET YOUR COPY>>


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>




How Will Businesses Overcome 5 Big IT Challenges?
Every business has to be careful about spending and making the right choices to overcome their challenges, especially in our difficult post-COVID difficult economy. Most businesses know that technology isn’t something that they can skimp on. Businesses today face an array of challenges from the need to upgrade legacy systems to taking precautions against the potential cyberattacks that they may face ahead. So how are businesses balancing their IT needs and priorities to make that happen? We looked at business spending and priorities in our 2023 IT Operations Survey and asked IT professionals about their company’s challenges and plans to resolve them. Take a look at what they had to say.


See why EDR is the perfect investment to make in your future right now in our buyer’s guide. DOWNLOAD IT>>
Challenge 1: Strengthening security & upgrading legacy systems
Cybersecurity has evolved over the past few years from an optional IT service to a must-have. On the one hand, businesses invest in enhancing their cybersecurity infrastructure; on the other hand, cybercriminals adapt and evolve their tactics, necessitating ongoing vigilance. Acknowledging that cybercriminals pose a continuous threat, 40% of the respondents recognized cybersecurity and data protection as the foremost IT challenge in 2023. Simultaneously, supporting a growing employee base and effectively managing downtime and service outages becomes increasingly challenging with an outdated technology stack. Therefore, legacy systems hampering growth and innovation are cited as the second biggest challenge by 24% of respondents. Compared to modern IT tools, legacy tools provide poor integration and almost no automation capabilities, becoming a drag on technicians and company budgets
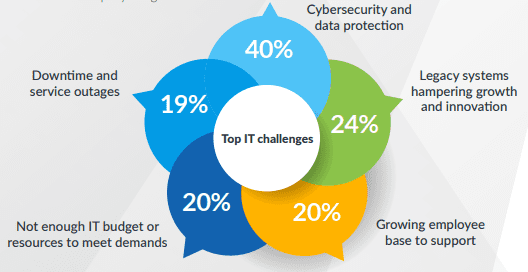

Source: Kaseya


Learn how managed SOC gives you big security expertise on call 24/7without the big price tag. LEARN MORE>>
Challenge 2: Get IT priorities aligned to overcome obstacles
The top IT priorities correspond to the top IT challenges. Organizations that can effectively manage their IT infrastructure and security will have a competitive edge. They will innovate faster, reduce costs and gain a better understanding of their customers. Improving cybersecurity is the primary focus area with businesses recognizing the importance of having a strong defense against devastating cyberthreats. Organizations are also keen on adopting automation since it’s the fuel that boosts productivity and can alleviate IT technicians’ increasing workload.
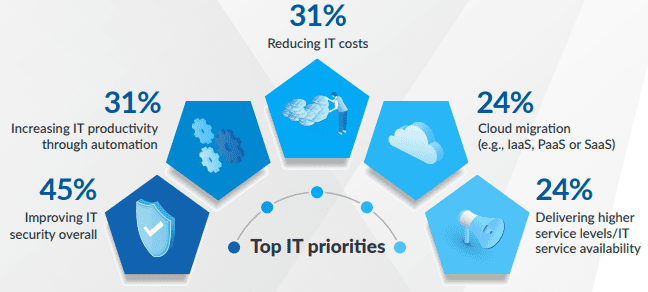

Source: Kaseya


Get tips & advice to help you build a smart incident response plan in our guide. GET YOUR GUIDE>>
Challenge 3: Making smart investments with a small budget
Even the best defenses in the world will fail to protect a company from a cyberattack if employees fail to recognize signs of a breach. Nearly half of the respondents (48%) said they want to invest in security awareness training to empower their employees to become the strongest link in their cybersecurity strategy. To combat the threat of phishing emails, 46% of the respondents expressed their intention to invest in email security measures. Additionally, the survey revealed that 36% of respondents were interested in vulnerability scanning tools that play a critical role in detecting and addressing weaknesses in the IT infrastructure before attackers can exploit them.
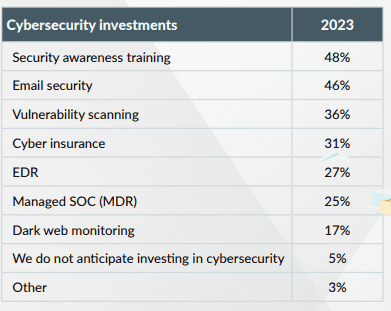

Source: Kaseya


SMBs are looking for advanced security solutions & money savers
Advanced security solutions like EDR are also garnering interest. EDR has become a necessity for security teams with the increase in advanced persistent threats (APTs) and other sophisticated cyberattacks. The role of an EDR solution is to proactively monitor, detect, and remediate or isolate threats on endpoint devices as they happen. For SMBs, building an in-house security team can be expensive and time-consuming, distracting them from their core business. Managed detection and response (MDR) service providers or Managed SOC give security and cost-conscious SMBs top-notch threat detection and remediation service that is nearly impossible to build internally.
Source: Kaseya


See how security awareness training stops the biggest security threats! GET INFOGRAPHIC>>
Challenge 4: Improved integration
Up until recently, each time a business needed to address an IT challenge, such as patching, endpoint management or service ticket remediation, it needed to bring home a new tool. This scenario has led to solution sprawl — a jumble of point solutions that do not integrate well. Technicians also ended up spending more time managing multiple tools, vendor contracts and billing than focusing on their jobs. We asked respondents if their solutions would benefit from better integration, and a staggering 86% of them agreed. Integration between core tools is necessary to streamline processes and create workflows that enable teams to work faster and more efficiently. Busy IT professionals — about 39% of respondents indicated they oversee all IT operations — can leverage integration to maximize productivity, keep different teams on the same page and do more with less effort
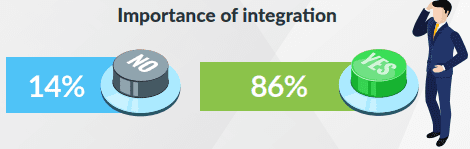

Source: Kaseya


Learn how a new integration between BullPhish ID & Graphus saves time & money. SEE THE DETAILS>>
Businesses value integration capabilities for core tools
Replacing core business tools is a big decision that impacts productivity, profitability and how easily technicians meet service level agreements (SLAs). Undoubtedly, all businesses would like to use solutions that perform better, have more functions and are highly cost-effective. However, one key factor that heavily influences the decision-making process after functionality is the integration capability of the new tool. Integrated systems require less manual effort, can scale based on changing business needs and allow for deeper analysis, which helps with better and faster decision-making. Integration also helps remove the need for overlapping functionalities in separate systems, thus reducing investment in multiple licenses.
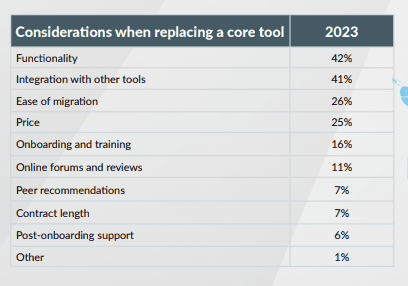

Source: Kaseya


Go inside BEC scams & get tips to keep businesses safe from today’s most expensive cyberattack. DOWNLOAD EBOOK>>
Challenge 5: Find the most beneficial integrations before buying
About a quarter (23%) of respondents highlighted the integration of IT documentation within the endpoint management tool as most beneficial. With easy access to comprehensive documentation, IT personnel can learn from past incidents and quickly solve recurring problems. In a nutshell, respondents want seamless integration between their endpoint management, IT documentation and service desk tools. This three-way integration results in quick diagnoses and remediation of issues, resulting in improved efficiency. Helped by integration, IT teams can promptly provide support for IT tickets and minimize any disruption to the end-user experience.
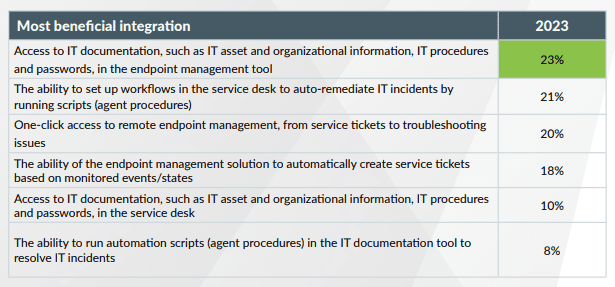

Source: Kaseya


Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>
The Kaseya Security Suite helps IT professionals mitigate cyber risk.
Major protection from today’s most dangerous and damaging cyberattacks doesn’t have to come with a major price tag with Kaseya’s Security Suite.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection around with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents cyberattacks and reduces an organization’s chance of experiencing a cybersecurity disaster by up to 70%.
Graphus — Automated email security is a cutting-edge solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
Kaseya Managed SOC powered by RocketCyber — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).


See how Managed SOC gives businesses an essential edge against cyberattacks. DOWNLOAD INFO SHEET>>


Register Now for the ID Agent & Graphus Q3 Product Innovation Webinar
JULY 18 |10 AM EDT | 7 AM PDT | 2 PM GMT
JULY 19 | 8 AM AEST | 3 PM PDT, 6 PM EDT
Join us at one of two convenient sessions to hear the product managers for BullPhish ID, Dark Web ID, Passly and Graphus highlight the latest product innovations. Learn about new features, integrations and what’s next on our Security roadmap. REGISTER NOW>>
July 11: Kaseya + Datto Connect Local Anaheim REGISTER NOW>>
July 18: Kaseya + Datto Connect Local Boston REGISTER NOW>>
July 18: ID Agent & Graphus Q3 Product Update Webinar REGISTER NOW>>
July 20: Kaseya + Datto Connect Local Baltimore REGISTER NOW>>
July 21: Kaseya + Datto Connect Local Baltimore IT Professionals Series REGISTER NOW>>
August 3: Kaseya + Datto Connect Local Doral Miami REGISTER NOW>>
August 15: Kaseya + Datto Connect Local Detroit REGISTER NOW>>
August 17: Kaseya + Datto Symposium Long Branch REGISTER NOW>>
August 22: Kaseya + Datto Connect Local Kansas City REGISTER NOW>>
August 29: Kaseya + Datto Connect Local San Diego REGISTER NOW>>
September 14: Kaseya + Datto Connect Local San Antonio REGISTER NOW>>
October 2 – 4: Kaseya DattoCon in Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!