The Week in Breach News: 09/07/22 – 09/13/22

This week we’re checking in from DattoCon 2022 with news about upcoming innovations, a tale of NATO hacking, the new Comprehensive Guide to Business Email Compromise and making the dollars and cents case for security and compliance awareness training.

Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>


Nelnet Servicing (Nelnet)
Exploit: Hacking
Nelnet Servicing (Nelnet): Student Loans Servicer






Risk to Business: 2.026 = Severe
A data breach of student loan servicer Nelnet Servicing (Nelnet) has affected over 2.5 million student loan borrowers throughout the United States. The breach affected borrowers whose student loans are serviced by the Oklahoma Student Loan Authority (OSLA) and Edfinancial Services (Edfinancial). The company disclosed that the PII of 2.5 million student loan borrowers was accessible by an unknown actor who gained access to the network in July 2022.






Risk to Business: 2.406 = Severe
The exposed data includes names, addresses, email addresses, phone numbers and Social Security numbers of borrowers who had loans serviced by the affected institutions.
How It Could Affect Your Customers’ Business: Service providers like this one are highly at risk for trouble thanks to the combination of valuable data and access to companies that they offer bad actors.
ID Agent to the Rescue: See the biggest risks that businesses in different sectors face today and get a look your clients will be facing tomorrow in The Global Year in Breach 2022. DOWNLOAD IT>>
Baker & Taylor
Exploit: Ransomware
Baker & Taylor: Book Distributor






Risk to Business: 1.647 = Severe
A ransomware attack at leading library book distributor Baker & Taylor has resulted in an outage that impacted the company’s phone systems, offices, and service centers. Those systems were out for a week. No ransomware group claimed responsibility, nor did Baker & Taylor disclose a ransom demand. The company said that they were able to restore their systems from backups and the incident remains under investigation.
How It Could Affect Your Customers’ Business: Cybercriminals have been concentrating their fire on suppliers and service providers, elevating risk for them.
ID Agent to the Rescue: Security awareness training can help companies prevent costly disasters like this. Learn how to make it happen in How to Build a Security Awareness Training Program. GET IT>>
Los Angeles Unified School District
https://techcrunch.com/2022/09/06/los-angeles-unified-school-district-ransomware/
Exploit: Ransomware
Los Angeles Unified School District: Regional Education Authority



Risk to Business: 1.427 = Extreme
A cyberattack against the Los Angeles Unified School District added complications to the start of the new school year. The ransomware attack hit on the Sunday before schools were scheduled to open for the new year. The district was able to overcome the digital shutdown to open schools on schedule the following Tuesday. However, the personal data of an estimated 400,000 students may have been accessed by cybercriminals. Federal, state and local authorities are investigating the incident. The Vice Society ransomware group has claimed responsibility for the attack, saying that they snatched more than 500GB of unspecified data.
How It Could Affect Your Customers’ Business: Educational institutions have been high on cybercriminal priority lists, and the time pressure here made this attack an attractive prospect for the bad guys.
ID Agent to the Rescue: See the reasons why an AI-driven automated email security solution is the answer to email security challenges like this. DOWNLOAD INFOGRAPHIC>>
Savannah College of Art and Design
https://therecord.media/ransomware-attack-on-leading-georgia-art-college-leads-to-data-leak/
Exploit: Ransomware
Savannah College of Art and Design: Institution of Higher Learning


Risk to Business: 2.712 = Moderate
Savannah College of Art and Design (SCAD) has revealed that a hacker gained access to SCAD’s information network systems, exposing data on an estimated 15,00 students. The school said that an unspecified “limited” number of files containing data about students and employees was accessed by bad actors. The AvosLocker ransomware group added SCAD to its leak site, but no ransom specifics have been released. AvosLocker may have taken at least 69,000 files that contained student information, personnel files and business data. No specifics have been released about what data was taken.
How it Could Affect Your Customers’ Business: Education has been a sector under siege, especially attractive to ransomware groups as the school year opens.
ID Agent to the Rescue: Sell clients on the benefits of security and compliance training with the bottom line data in The Business Case for Security Awareness Training. DOWNLOAD IT>>


Learn to identify and mitigate fast-growing supply chain risk with this eBook. DOWNLOAD IT>>


United Kingdom – InterContinental Hotels Group (IHG)
https://www.infosecurity-magazine.com/news/holiday-inn-hotels-cyber-attack/
Exploit: BEC
InterContinental Hotels Group (IHG): Hotel Operator






Risk to Business: 1.809 = Severe
InterContinental Hotels Group (IHG) has confirmed that they’ve had a security incident impacting the Holiday Inn hotels chain. A cyberattack downed its booking systems and mobile apps. Although ITG did not reveal the nature of the attack in its public statement, tech experts point to ransomware. The incident is under investigation, and no information about what if any data was stolen or the group responsible was mentioned.
How it Could Affect Your Customers’ Business: Hospitality organizations rely heavily on their IT systems, and outages lead to disasters.
ID Agent to the Rescue: Are you offering the right training solution to help your clients avoid risks like this? Find out with the Security Awareness Training: Buyer’s Guide for MSPs DOWNLOAD IT>>


See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>
United Kingdom – Go-Ahead
https://cities-today.com/major-uk-bus-operator-hit-by-cyber-attack/
Exploit: Hacking
Go-Ahead: Bus Company






Risk to Business: 1.723 = Severe
Go-Ahead, a major UK public transport operator disclosed that it is a cyberattack after finding unauthorized activity within its IT systems. The company said that many of its IT systems have been affected by this cybersecurity incident, including the system used to allocate drivers to bus services, with minimal delays expected. Some restoration has taken place using backups, and the incident remains under investigation.
How it Could Affect Your Customers’ Business: Major transportation providers are juicy targets for bad actors because those services cannot afford disruptions, making them likely to pay ransoms.
ID Agent to the Rescue: A strong security culture reduces the risk of an incident. Help your clients build one with The Building a Strong Security Culture Checklist! DOWNLOAD IT>>
Portugal – Armed Forces General Staff agency of Portugal (EMGFA)
https://securityaffairs.co/wordpress/135480/data-breach/nato-docs-stolen-from-portugal.html
Exploit: Hacking
Armed Forces General Staff agency of Portugal (EMGFA): Government Agency



Risk to Business: 1.361 = Extreme
Classified NATO documents belonging to the Armed Forces General Staff agency of Portugal (EMGFA) were spotted for sale on the dark web, leading the agency to discover that it had experienced a data breach. First spotted by US Information Services, hundreds of sensitive documents have apparently been snatched by bad actors. The documents were exfiltrated from systems in the EMGFA, in the secret military (CISMIL) and in the General Directorate of National Defense Resources. Investigators determined that security rules for the transmission of classified documents had been broken, and threat actors were able to access the Integrated System of Military Communications (SICOM) and receive and forward classified documents.
How it Could Affect Your Customers’ Business: This problem could have been prevented by simple adherence to security rules and compliance with security policies.
ID Agent to the Rescue: The infographic 6 Tips for Creating a Security Awareness Training Policy can help you and your clients draft strong security policies that prevent disasters like this. DOWNLOAD IT>>


See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


See how today’s biggest threats may impact your MSP and your customers in our security blogs.
- 5 Overlooked Ways a Ransomware Attack Impacts a Company’s Bottom Line
- These 2 Cyberattacks Are Today’s Nastiest Threats Against Businesses
- Blizzard of HHS Warnings Underlines Healthcare Cyberattack Danger
- Almost Three-Quarters of Cyberattacks Have Something in Common: Phishing
- The Week in Breach News: 08/31/22 – 09/06/22


Solve five of the most exhausting remote and hybrid security problems fast with this handy infographic! DOWNLOAD IT>>


A Postcard from DattoCon 2022
DattoCon 2022 took place earlier this week from September 11 – 13, in Washington DC, and it was a blast! So much great energy and information was shared to bring the next year of innovation into focus. We’ll be publishing in-depth reporting on this awesome event in our blogs this week, but we wanted to offer you a sneak preview of some of the data shared and what’s next in security.
Fun facts
- DattoCon 2022 had more than 2700 attendees from 29 countries
- With Datto onboard, Kaseya is now the largest MSP=focused software company on the planet
- More than 85% of small businesses say that they’re making digital transformation a top priority in the next few years
- About 50% of technician time is wasted on processes that could be automated
- Today’s MSP utilizes an average of 17 solutions, up from 8 in 2015
BullPhish ID Innovation Preview
Advanced User Synchronization with IT Glue & Passly
•Improve customer onboarding and management by importing SMB organization data from IT Glue into BullPhish ID.
•Improve customer onboarding and management by importing end users and groups from Passly intoBullPhish ID. Utilize Passly integration with Azure or Physical Active Directory.
Dark Web ID Innovation Preview
Active User Compromise Filtering
•Don’t want to receive compromises for deactivated users or employees who no longer work at your client companies? We hear you! We are implementing the ability to filter compromises by active user.
•Simply choose CSV or AD filtering option, set up the filter and you will no longer receive compromises for employees or emails outside of that list!
•Eliminates “background noise” and prevents you from receiving old, unwanted alerts!
Graphus Innovation Ahead
Simplified Organization Management with IT Glue
•Simplify and speed up customer onboarding and management by importing SMB organization data from IT Glue into Graphus
Introducing Datto Managed SOC Powered by RocketCyber
We’re always trying to make life easier for MSPs, and we’re bringing that energy to Managed Detection and Response (MDR). Datto Managed SOC Powered by RocketCyber was built with that aim in mind, featuring multi-tenant cloud architecture fueled with integrated threat intelligence and backed by our team of elite security experts delivering 24/7 threat monitoring across your entire infrastructure.
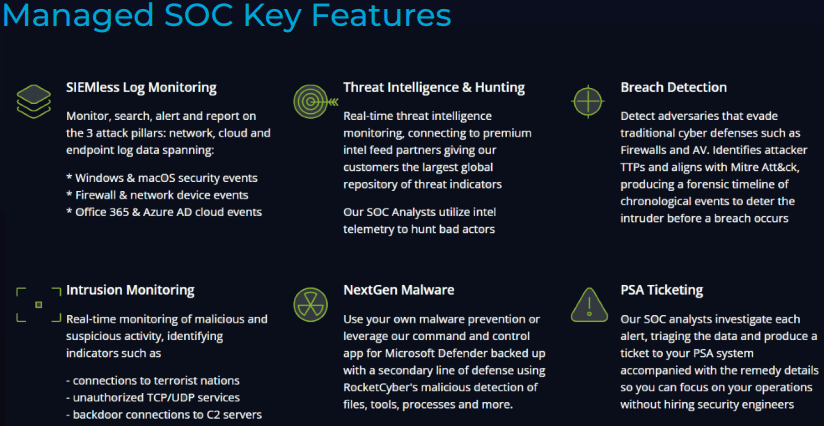

Learn more about this innovative solution now!
Backup Suite Innovations
Datto Windows Agent (DWA) 3.0, available now, has achieved all-time highs in backup success rate & screenshot success rate.
Highly readable MSP Reports including Daily Backup Success Reports for SaaS and Hero Reports for BCDR are available now
Coming soon: Datto SaaS Protection for Microsoft Teams private channels easily configured by auto-add using Azure AD groups.
Fresh features
- Backup – Multivolume support
- Recovery – Client self-service file restores for co-managed environments
- Ease-of-use features – Agent Information API
- Plus, major gains in product quality across backups, verifications & restores.
SIRIS 5
Performance
- 4x local virtualization performance
- Next-gen enterprise-grade drives for faster backup & transfer speed
Reliability
- Hardware RAID for OS drive
- Advanced burn in testing
Simplicity
- Streamlined SIRIS models from 22 to 13
RMM Innovations
Webhook notifications
- Get Alerts in Microsoft Teams, Slack or Power Automate
- Add custom actions and links
Web Remote
Web Remote is the #1 support tool
Web remote chat
- Chat before control
- Multi-tech support
- Chat history
NEW! Web shell (coming in Q4)
- PowerShell, Bash
- Tab-completion, shortcuts and RMM variable support
- Access from anywhere!
NEW! IT Glue integration (coming in Q4)
- Documentation available everywhere!
- Password injection
PSA Innovations
Autotask PSA
New Features
- Co-managed IT – Onboard co-managed IT users with a new streamlined user experience
- Inventory restructure – Better track your inventory products from receipt to delivery
- Ticket boards – Manage your technician workload with a visual ticketing drag-and-drop interface
Near-term roadmap
- User interface refresh – New color palette, simplified themes, top menu navigation and repositioned search
- Enhancement requests – Over 50 community-driven features this year addressing functionality, usability and productivity items
- Workflow integrations – IT Glue at your technician’s fingertips, asset synchronization from
Datto Networking, integrated payment processing & more
Datto Commerce
New Features
- Autotask integration – 10 new enhancements to improve
your quoting workflows - Supplier integrations – 12 new supplier integrations, plus direct-to manufacturer with Lenovo
- Enhancement requests – Over 40 community-driven features this year addressing functionality, usability and productivity
Near-term roadmap
- Notification center -Get notified about critical events such as insufficient stock on your open quotes
- Autotask integration – Deeper workflow integration to support labor & projects, plus increased visibility and direct access to Commerce from Autotask
- Email templates – New email template editor to fully customize and brand your emails
Networking Innovations
Available now! WiFi-6 access points – Reliable, secure, performant wireless that’s simple to deploy and manage.
Coming soon
- PoE+ on all ports
- 10G uplinks
- Layer 3 features
- Multigig capabilities
Coming in October 2022
Datto Secure Edge: SASE made simple
- Improve & secure access to data and applications stored anywhere, wherever the employee works
- Purpose-built for MSPs
- Incredibly easy to deploy and simple to consume
IT Documentation Innovations
Available Now!
Microsoft Intune
- Asset management through Intune
- User management through Active Directory (on-prem & cloud)
- Licenses management through M365
- Password management through OTP at your fingerprints
Datto Continuity Backup status in IT Glue
- Single view of critical backup status & backup time information
- Visibility for everyone
- Auto-documentation of SIRIS Appliance
- Backup system integrity at-a-glance
Coming Soon
Offline Password Access – Business continuity through 24/7 passwords access
1-Click Active Directory password rotation
- Rotate your local AD passwords on-demand from IT Glue
- Save time by reducing steps
- Enhance security by retaining IT Glue-level permissions for critical passwords
- Scheduled rotation to be added soon!
Suggested IT Glue documentation in Autotask PSA
- Recommended SOPs and passwords right inside the ticket
- Reduce ticket resolution time
- Improves operational efficiency of your business


The Comprehensive Guide to Business Email Compromise
In The Comprehensive Guide to Business Email Compromise, you’ll learn the ins and outs of this dangerous cyberattack including:
- The types of BEC that you may encounter and how attacks spawn
- Walkthroughs of common BEC attack scenarios
- How AI-driven, automated security helps you mount a strong defense against phishing-related cybercrime like BEC
Did you miss this? Clobber Phishing Risk with This Dynamic Duo Webinar WATCH NOW>>


Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>




Making the Dollars and Cents Case for Security Awareness Training
Your clients’ businesses are under siege by a never-ending barrage of cyberattacks, and the situation is only growing worse. They’re relying on you to help them prevent expensive security disasters like a data breach or a ransomware incident. Unfortunately, those disasters are often caused by employees making bad security decisions because many employees are unable to recognize security threats on their own. That’s a big reason why security awareness training is a necessity for every client. From teaching data handling best practices to preventing an employee from downloading a ransomware-laden attachment, security awareness training is the key to helping your clients build a strong defense against today’s biggest cybersecurity threats – and your clients are relying on you to provide the right solution to get the job done.
Excerpted in part from our Security Awareness Training: Buyer’s Guide for MSPs



Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>
Why Is Security Awareness Training Important for My Clients?
Organizations of every size are being flooded by a rising tide of cybercrime risk. The U.S. Federal Bureau of Investigation Internet Crime Complaint Center (FBI IC3) 2021 report offers an excellent snapshot of the danger that your clients are facing. IC3 received a record 847,376 complaints from U.S. businesses impacted by cybercrime in 2021, a 7% increase over 2020. But the total amount of loss is the real stunner, at a new record high of $6.9 billion in 2021, a whopping 48% increase over 2020.
Drilling deeper, these statistics help illustrate the recent surging growth of cyberattack risk.
- 84% of businesses were the victims of a successful phishing attack in 2021, a 15% increase over the same 12-month period in 2020.
- The U.S. has incurred a 127% year-to-date increase in the number of ransomware attacks while the U.K. has seen a 233% surge in ransomware infections.
- The average cost of a breach is estimated at $ 4.2 million per incident, 10% higher than in 2020 and the highest recorded in 17 years.


Get tips from experts in our webinar MSP Cybersecurity Roundtable: How to Improve Your Incident Response Plan WATCH NOW>>
Regular Training Transforms Employees into Security Assets
Security and compliance awareness and phishing simulation training is an extremely affordable and effective way to mitigate the risks that your client’s employees encounter daily. The more training employees receive, the more adept they get at spotting and avoiding security risks, reducing your client’s risk of a cybersecurity incident.
Researchers in a U.K. study discovered that the improvement in employee behavior that companies see when they engage in security awareness training is stark.
- At the beginning of the study, as many as 40% to 60% of the employees surveyed were likely to open malicious links or attachments.
- After about six months of security awareness training, the percentage of employees who took the bait dropped to 20% to 25%.
- When the employees completed three to six months more of security awareness training, only 10% to 18% of them fell for phishing messages.
Ongoing security and compliance awareness training is essential for your client’s organization to receive benefits like these. According to Accenture, each employee should receive 11 sessions per year.


Get 10 tips to help you build a strong security culture & reduce your risk of cybersecurity trouble! GET INFOGRAPHIC>>
Security Awareness Training Delivers an Amazing ROI
Every client is budget-conscious, and they’ll want hard data that proves the value of an investment in security and compliance awareness training before sealing the deal. Fortunately, it’s easy to demonstrate that it’s one of the best IT investments an organization can make with an impressive ROI.
IT Security Costs Before & After Training
| Before training 50 – 999 employees | Before training 1000+ employees | After training 50 – 999 employees | After training 1000+ employees | |
| Annual IT payroll hours spent disinfecting workstations, networks | 760.0 | 137.3 | 565.5 | 120.5 |
| Annual misc. incident remediation cost per email user | $29.23 | $5.28 | $21.75 | $4.63 |
| Annual IT security costs per email user | $7.51 | $28.11 | $0.75 | $2.81 |
| Cost of employee time spent in SAT | $21.11 | $27.83 | ||
| Estimated annual costs per email user (including IT payroll costs) | $249.39 | $455.41 | $24.94 | $45.54 |
Source: Osterman Research, The ROI of Security Awareness Training
Total ROI for Security Awareness Training
Small and midsize businesses (SMB, 50 to 999 employees): 69% ROI
Large businesses (1,000+ employees): 562% ROI
Source: Osterman Research, The ROI of Security Awareness Training


Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>
Security awareness training works
While training may sound nebulous or frivolous, it’s not. Instead, the benefits of security and compliance awareness training have been scientifically proven. Researchers in a U.K. study discovered that the improvement in employee behavior that companies see when they engage in security awareness training is stark.
- At the beginning of the study, as many as 40% to 60% of the employees surveyed were likely to open malicious links or attachments.
- After about six months of security awareness training, the percentage of employees who took the bait dropped to 20% to 25%.
- When the employees completed three to six months more of security awareness training, only 10% to 18% of them fell for the phishing messages.
These cold, hard facts clearly demonstrate the dangers of untrained employees facing security and compliance choices. However, many of these problems can be resolved through security and compliance awareness training.


This MSP-focused guide gives you insight into finding the ideal dark web monitoring solution. GET THE GUIDE>>
Reduce Your Clients’ Cyberattack Risk Fast
Reducing your clients’ risk of a cyberattack is an ongoing battle, but these solutions can help ensure that you’re using the best weapons to fight back against cybercrime and putting safeguards in place that are ready to handle the next generation of cyber threats.
Security awareness and compliance training plus phishing simulation
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size. This powerhouse is an award winner and the channel leader in phishing simulations.
- An extensive library of security and compliance training videos in eight languages
- Plug-and-play or customizable phishing training campaign kits
- New videos arrive 4x per month and new phishing kits are added regularly
- Easy, automated training delivery through a personalized user portal
Dark web monitoring
Dark Web ID offers best-in-class dark web intelligence, reducing credential compromise risk.
- 24/7/365 monitoring using real-time, machine and analyst-validated data
- Fast alerts of compromises of business and personal credentials, including domains, IP addresses and email addresses
- Live dark web searches find compromised credentials in seconds
- Create clear and visually engaging risk reports
Automated, AI-powered antiphishing email security
Graphus AI-enabled, automated email security that catches 99.9% of sophisticated phishing threats and offers amazing benefits.
- Forget old-fashioned safe sender lists. Graphus analyzes the content of messages using more than 50 points of comparison to suss out fakes fast.
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- 3 layers of powerful protection at half the cost of competing solutions
- Don’t waste time on fussy configurations or adding threat reports. AI does that for you, getting everything up and running with just a few clicks and minimal maintenance.
Click here to watch a video demo of Graphus now.


Make sure your clients have all the bases covered with the Computer Security To-Do Checklist! GET IT>>


September 20: Dark Web ID: The Leading Dark Web Monitoring Program REGISTER NOW>
September 16: Cybersecurity Summitt in Charlotte REGISTER NOW>>
September 28-30: SpiceWorld 2022 REGISTER NOW>>
October 6-7: ASCII MSP Success Summit 2022 – Dallas REGISTER NOW>>
October 13: Cybersecurity Summit in Scottsdale REGISTER NOW>>
October 25-26: Southwest US Summit REGISTER NOW>>
November 2-3: ChannelPro SMB Forum 2022: Los Angeles REGISTER NOW>>
December 6: Connect IT Local – Atlanta REGISTER NOW>>
December 8: Connect IT Local – Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!