The Week in Breach News: 11/30/22 – 12/06/22

This week: Credential stuffing sticks DraftKings with a $300K loss, a bevy of Canadian breaches, a new holiday infographic plus more resources and what to do about elevated ransomware risk this holiday season.

This handy checklist of smart security practices helps businesses kick off the new year right! GET CHECKLIST>>

LastPass
https://blog.lastpass.com/2022/11/notice-of-recent-security-incident/
Exploit: Hacking
LastPass: Software Company

Risk to Business: 1.106 = Extreme
LastPass has experienced a second data breach. The company disclosed in its blog that hackers used information obtained in the August 2022 LastPass breach to access customer information in third-party cloud storage shared with its corporate partner GoTo. LastPass specified that customers’ passwords it stores were unaffected and remain safely encrypted. It is unclear as whether or not clients of GoTo and LogMeIn were affected by this incident. All the brands involved said that the incident is under investigation and LastPass specified that it has engaged Mandiant as part of that effort. No specifics as to what information was exposed were available at press time.
How It Could Affect Your Customers’ Business: Multiple breaches in one year can cause customers to lose faith in a company.
ID Agent to the Rescue: See the biggest risks that different sectors face today and get a look at what your clients will be facing tomorrow in The Global Year in Breach 2022. DOWNLOAD IT>>
U.S. Immigration and Customs Enforcement (ICE)
https://www.businessinsider.com/more-than-6000-immigrants-affected-ice-data-leak-hours-2022-11
Exploit: Misconfiguration
U.S. Immigration and Customs Enforcement (ICE): Federal Government Agency

Risk to Business: 2.121 = Severe
Personal information about more than 6,000 potential immigrants applying for refuge from possible torture or political persecution in the U.S. was exposed by ICE in a misconfiguration error. The data breach was first discovered by immigrant advocacy group Human Rights First. After the group reported the problem to ICE the leak was quickly corrected, but not before information about people seeking refuge from countries around the world including China, Iran and Russia was left unprotected and available to anyone for more than five hours. The agency determined that the data had been exposed accidentally as part of a website update. Unfortunately, the availability of the information may have exposed threatened people to danger.










Individual Risk: 2.207 = Severe
In this incident, immigrants’ names, case status, detention locations, and other information was published on a page where ICE regularly publishes detention statistics.
How It Could Affect Your Customers’ Business: This configuration error exposed very sensitive data and potentially put people at risk of harm.
ID Agent to the Rescue: Security awareness training prevents employee mistakes. These 10 tips help you ensure that you and your clients are getting the most out of your training program. GET TIPS>>
Rackspace
Exploit: Ransomware
Rackspace: Cloud Solutions Provider










Risk to Business: 1.652 = Severe
A ransomware attack forced Virginia-based cloud solutions provider Rackspace was forced to shut down its Hosted Exchange servers on December 2. The company disclosed that Rackspace’s Hosted Exchange service began experiencing problems on December 2 and told customers that the shutdown was the result of a security incident on December 3 that was later identified as ransomware. The company told customers to shift to Microsoft 365 for email services and is offering them free access. Rackspace gave no estimated timeline for the restoration of its Exchange services but cautioned customers that the outage was expected to be extended. A company statement said that the attack was confined to its Hosted Exchange servers. The incident is under investigation but Rackspace said that it is too early to tell if any data was accessed by the threat actors.
How It Could Affect Your Customers’ Business: IT service providers have been experiencing extraordinarily high levels of ransomware as bad actors perpetrate supply chain attacks.
ID Agent to the Rescue: Go over the Cybersecurity Risk Protection Checklist with your clients to make sure that they’re covering all of their security bases. GET CHECKLIST>>


Go inside BEC scams & get tips to keep businesses safe from today’s most expensive cyberattack. DOWNLOAD EBOOK>>


Durham District School Board
Exploit: Hacking
Durham District School Board: Regional Education Authority










Risk to Business: 2.107 = Severe
A school system in the greater Toronto area has experienced a major technical outage after a hacking incident. Durham District School Board said that the incident disrupted online learning for students and left schools without access to phone or email services as well as emergency contact information. The district the board oversees is responsible for public education across 136 elementary and secondary schools in the eastern Toronto area serving an estimated 74,000 students with over 7,000 teaching and educational services staff.
How it Could Affect Your Customers’ Business: School systems and universities have been high on cybercriminal hit lists because bad actors know they can’t afford downtime.
ID Agent to the Rescue: See what the hottest topics are in business security and explore the challenges SMBs face today in The Kaseya Security Insights Report 2022. DOWNLOAD IT>>


See how security awareness training stops the biggest security threats! GET INFOGRAPHIC>>


Colombia – Keralty
Exploit: Ransomware
Keralty: Healthcare Provider










Risk to Business: 1.882 = Severe
Multinational healthcare group Keralty has disclosed that it has experienced a ransomware attack that has impacted the company and its subsidiaries EPS Sanitas and Colsanitas. The attack has disrupted IT operations including the scheduling of medical appointments and its websites. Reports say that patients were left waiting in lines for more than 12 hours to obtain treatment. The RansomHouse ransomware group has claimed responsibility. The cybercrime group claims to have snatched data in the incident but that is unconfirmed.
How it Could Affect Your Customers’ Business: Not only does a cyberattack disrupt the business of a healthcare provider, it also dangerously impacts patient care.
ID Agent to the Rescue: Security awareness training helps employees avoid ransomware traps. Learn to create a great program with How to Build a Security Awareness Training Program. DOWNLOAD IT>>


How good is your identity and access management? Use this checklist to see if it’s really getting the job done. GET IT>>


Belgium – Zwijndrecht Police Department
Exploit: Ransomware
Zwijndrecht Police Department: Law Enforcement Agency










Risk to Business: 1.604 = Severe
The Zwijndrecht Police Department in Belgium has confirmed that it has experienced a data breach after an attack by the Ragnar Locker ransomware group. In an interesting twist to this story, the group initially posted to its dark website that it had successfully attacked the municipality of Zwijndrecht, but it turned out that the attack has actually been perpetrated against the city’s police department. The stolen data is reported to include thousands of car number plates, fines, crime report files, personnel details and investigation reports. No specifics about any demanded ransom were available at press time.
How it Could Affect Your Customers’ Business: Law enforcement organizations hold some especially sensitive data and need especially strong protection against a data breach.
ID Agent to the Rescue: Learn more about how to defend businesses from ransomware with the resources in our Deep Dive into Ransomware bundle! GET BUNDLE>>


What’s next for MSPs? Find out in the Datto Global State of the MSP Report: Looking Ahead to 2023 DOWNLOAD IT>>


Australia – AGL Energy
Exploit: Hacking
AGL Energy: Energy Company










Risk to Business: 1.717 = Severe
The latest company victimized in the recent rash of cyberattacks o Australian companies is AGL Energy, Australia’s largest electricity provider. The company reported detecting suspicious activity on its platform on December 1. AGL said in a statement that it believed the incident was the result of bad actors obtaining reused customer credentials that had been stolen in other incidents. The energy provider disclosed that an estimated 6,00 customer accounts may have been impacted in this incident. Impacted customers were informed by mail and that federal government and relevant cyber security bodies have been notified of the incident.
How it Could Affect Your Customers’ Business: Making a continuity plan is a smart move that will help Guadeloupe get out from under this disaster quickly.
ID Agent to the Rescue: Learn more about how to defend businesses from ransomware with the resources in our Deep Dive into Ransomware bundle! GET BUNDLE>>
New Zealand – Accuro
https://www.insurancebusinessmag.com/nz/news/cyber/accuro-hit-by-cyberattack-429430.aspx
Exploit: Hacking
Accuro: Health Insurance Provider










Risk to Business: 2.801 = Severe
A cyberattack on New Zealand health insurer Accuro has compromised its access to several of its core systems. The not-for-profit insurer says it has not yet determined if customer data was stolen in the incident. Accuro pointed to a cyberattack on its unnamed IT services provider as the root cause of the trouble and said that systems may be down for a protracted period. The company has notified the relevant regulatory authorities, including the Office of the Privacy Commissioner and CERT NZ.










Risk to Business: 2.665 = Severe
The company has notified the relevant regulatory authorities, including the Office of the Privacy Commissioner and CERT NZ.
How it Could Affect Your Customers’ Business: Companies in Australia and New Zealand have been experiencing a flood of cyberattacks recently.
ID Agent to the Rescue: A strong security culture reduces the risk of an incident. Help your clients build one with The Building a Strong Security Culture Checklist! DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident



Don’t miss the industry’s best event, Connect IT Global April 24 – 27, 2023, in Las Vegas! REGISTER NOW>>


See how today’s biggest threats may impact your MSP and your customers in our security blogs.
- What’s for Sale on the Dark Web?
- These 5 Surging Ransomware Attacks Could Doom Your Organization
- 4 Reports to Read Before You Finish Your 2023 Growth Plan
- 7 Answers to Burning Questions About the State of the MSP
- The Week in Breach News: 11/23/22 – 11/29/22


Set businesses on the zero trust path with the 6 Tips for Implementing Zero Trust Security infographic! GET IT>>


6 New Lessons Added to BullPhish ID
Six new training videos with quizzes have been added to the BullPhish ID library. Start training employees with these lessons now:
- Safe Web Browsing Domain spoofing website forgery
- Social Media Phishing
- Phishing Scams: Cryptocurrency, Military, and Romance
- Ransomware/Malware Malicious Links and Websites
- Insider Risk: Spotting Malicious Insiders
- CMMC Level 1: Compliance
Learn more about these videos and other updates in the BullPhish ID Release Notes.


Learn how to spot and stop malicious insiders and educate users with this handy infographic! GET IT>>


Two Holiday-Themed Infographics for Your Customers
Make Smart Cybersecurity New Year’s Resolutions
Help your clients kick off the new year right with this helpful infographic that outlines smart cybersecurity practices, offering them guidance into the steps that they can take to bolster their defense against cybercrime. DOWNLOAD IT>>
12 Days of Tips to Help Businesses Reduce Holiday Cyber Risk
The holiday season is a time of elevated cyber risk for businesses. These 12 tips can help businesses ensure that they don’t receive the unwanted gift of a cyberattack or data breach this holiday season. DOWNLOAD IT>>
Did you miss… Security Awareness Training: How It Prevents the Biggest SMB Security Threats. DOWNLOAD IT>>


It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>




4 Threats You & Your Clients Need to Know About This Holiday Season
These Threats Are Going Around Right Now
As the holiday season kicks into high gear, bad actors are kicking their cybercrime schemes into high gear too. Morgan Stanley says that nearly 75% of Americans experienced at least one type of holiday scam in 2021. Every year, cybercriminals increase the pace of attacks, flooding businesses and consumers with phishing attacks, ransomware-laden emails, business email compromise attempts (BEC) and other nasty cyberthreats. These four threats are at the top of the list right now. You and your clients need to know what to watch out for and how to reduce the risk of a holiday disaster.
Holiday Cybercrime Facts
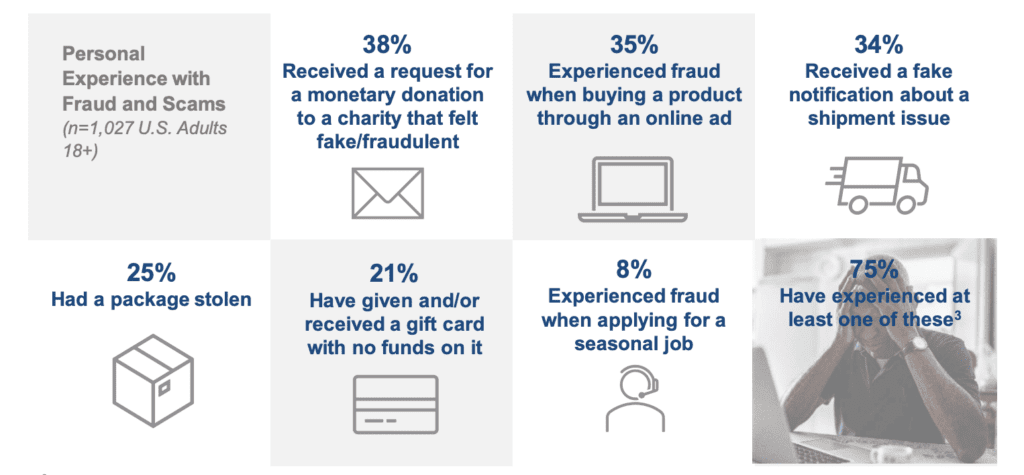

Source: AARP


Make sure cybercriminals don’t give you the unwelcome gift of a cyberattack with these 12 tips to reduce holiday risk. GET TIPS>>
Be Alert to These Risks Right Now
These four risks are especially dangerous right now.
Brand Impersonation
Brand impersonation and spoofing are a threat all year round, but that threat amps up during the winter holiday shopping season. Throughout the year, employees encounter this threat frequently – 25% of all branded emails that companies receive are spoofed or brand impersonation attempts. One scam that has been making the rounds is a phishing scheme in which bad actors attempt to lure in victims by imitating the luxury brand Louis Vuitton. In this scenario, targets received an email with a subject line reading “Black Friday Sale. Starts at $100. You’ll Fall In Love With Prices.” The victims were directed to a fake website that looked convincingly like the real Louis Vuitton website.
This is not the only Louis Vuitton brand impersonation scam rolling around this holiday season. A report in Business News This Week cites four similar scam domains that were registered at the same time to conduct brand impersonation of Louis Vuitton. But luxury brands aren’t the only brands that cybercriminals impersonate during the holidays. Amazon saw fraud attempts by cybercriminals impersonating its brand more than double during the holiday shopping season in 2021.


Learn how a new integration between BullPhish ID & Graphus saves time & money. SEE THE DETAILS>>
Phishing
The holiday season spawns holiday-themed phishing of all sorts. Cybercriminals are launching a variety of phishing scams that target online shoppers. This is relevant for businesses because many employees shop at work or on work devices this time of year, putting their company networks at risk. One of the biggest phishing dangers that employees will encounter is emails containing links that take them to fraudulent websites. According to Amazon, they have already initiated takedowns of more than 20,000 phishing websites and 10,000 phone numbers associated with impersonation schemes this year.
However, phishing emails that leverage holiday sentiment aren’t always shopping-related. Some emails promoting fraudulent websites are about shipping, coupons, travel, even recipes. Last year, phishing websites ballooned by more than 200% during the winter holiday season. But cybercriminals don’t have to think up their holiday phishing scams on their own. They can readily purchase holiday-themed phishing kits on the dark web.



Don’t miss the industry’s best event, Connect IT Global April 24 – 27, 2023, in Las Vegas! REGISTER NOW>>
Malware & Ransomware
If any of your clients sell goods or services online, they need to be ready for an influx of risk. As we reported last week, ransomware risk climbs by about 70% during the winter holiday season. Bad actors are especially keen to plant malware like skimmers on eCommerce sites. Researchers say that cybercriminals have stepped up their pace of malware attacks on eCommerce sites this year with 38% of Magento 2 and Adobe Commerce websites actively being targeted by the attackers.
A prominent malware attack on eCommerce sites this holiday season attack, dubbed TrojanOrders, exploits an Adobe mail template vulnerability (CVE-2022-24086) that many retailers may not have patched. In this scenario, bad actors create an account at an online store’s website and place a fake order. When inputting their fake order on the retailer’s website, they’ll drop malicious template code in the name, VAT or other form fields. Once their malicious code locks into the site, bad actors can install a remote access trojan (RAT) or create their own backdoor to gain permanent access to that site.


What worries security pros? The Kaseya Security Insights Report 2022 tells you. GET YOUR REPORT>>
Business Email Compromise (BEC)
Tis the season for business email compromise too. While many online and email scams target consumers, they’re not the only ones at risk during the holiday season. According to the U.S. Bureau of Investigation (FBI), the two most prominent holiday scams that cybercriminals perpetrate are also common BEC scams: non-delivery and non-payment scams. The FBI Internet Crime Complaint Center (IC3) received more than 44,220 complaints with losses over $276 million for the period through October 2022, but that number is expected to climb substantially in November and December 2022.
Non-delivery scams also often include elements of brand impersonation. According to Amazon, more than 50% of the impersonation scams its customers report are fake order confirmations. The Detroit Free Press reported on one variation of a shipping scam that is tripping up victims this year. In this version, victims are sent a notification via text or email that a package addressed to them is undeliverable because the shipping address isn’t accurate. The victim is directed to go to a website to “correct” the information using a link in the email. But the website is a fake, and bad actors can do things like steal information or infect the victim’s computer with malware.


Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>
Resources to help you keep your clients safe from holiday cybercrime
These resources can help you educate your clients about holiday season risk and keep them out of trouble.
- The U.S. Cybersecurity and Infrastructure Security Agency has tips available to help reduce the risk of trouble related to holiday shopping.
- The Better Business Bureau has partnered with Amazon to release a new online scam reporting and prevention tool, the BBB Scam Tracker.
- Our 12 Days of Tips to Help Businesses Reduce Holiday Risk infographic includes steps that businesses can take to mitigate risk this holiday season and all year round.
- Help your clients kick off the new year on the right foot with our new Make Smart Cybersecurity New Year’s Resolutions infographic.


Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>
Cybercriminals never take a day off and neither do our security solutions
Kaseya’s security solutions can help you keep your clients safe from holiday cyberattacks quickly and easily at a price you’ll both love.
Security awareness and compliance training plus phishing simulation
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size. This powerhouse is the channel leader in phishing simulations.
- An extensive library of security and compliance training videos in eight languages
- Plug-and-play or customizable phishing training campaign kits
- New videos arrive 4x per month and new phishing kits are added regularly
Dark web monitoring
Dark Web ID offers best-in-class dark web intelligence, reducing credential compromise risk.
- 24/7/365 monitoring using real-time, machine and analyst-validated data
- Fast alerts of compromises of business and personal credentials, including domains, IP addresses and email addresses
- Live dark web searches find compromised credentials in seconds
- Create clear and visually engaging risk reports
- Automated, AI-powered antiphishing email security
Email security
Graphus AI-enabled, automated email security that catches 99.9% of sophisticated phishing threats and offers amazing benefits.
- Forget old-fashioned safe sender lists. Graphus analyzes the content of messages using more than 50 points of comparison to suss out fakes fast
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- 3 layers of powerful protection at half the cost of competing solutions
- Don’t waste time on fussy configurations or adding threat reports. AI does that for you, getting everything up and running with just a few clicks and minimal maintenance
Managed SOC
Get the top Managed SOC that leverages our Threat Monitoring Platform to give you access to an elite team of security veterans hunt, triage and work with your team when actionable threats are discovered
- Detect malicious and suspicious activity across three critical attack vectors: Endpoint, Network & Cloud
- Patent-pending cloud-based technology eliminates the need for on-prem hardware
- Discover adversaries that evade traditional cyber defenses such as Firewalls and AV


See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>




Meet Kaseya Leaders at Connect IT Local – Ft. Lauderdale Next Week
Kaseya’s top leaders will be in Fort Lauderdale on Tuesday, December 13th to discuss how the IT Complete vision can help you be more efficient, better defended and further connected. We are just under one week away from our South Florida Executive Symposium, so register today and join us at Seminole Hard Rock Hotel and Casino in Hollywood, FL.
This is your last chance in 2022 to meet face-to-face with our executive leadership, including our CEO Fred Voccola. Kaseya CISO Jason Manar will also be hosting a one-of-a-kind panel with fellow CISOs – you don’t want to miss out! This is a free half-day event where you’ll get to learn and network over complimentary lunch and drinks. You’ll also have an opportunity to win an Oculus Quest 2!
Only a few seats remain so secure yours today
December 8: Connect IT Local – Miami REGISTER NOW>>
December 8: Datto & Kaseya Connect IT Local – Reading, UK REGISTER NOW>>
December 8: Cyber Insurance Changes and You REGISTER NOW>>
December 13: Connect IT Local – Ft. Lauderdale REGISTER NOW>>
December 13: Executive Roadshow REGISTER NOW>>
December 15: Connect IT Local – Washington DC REGISTER NOW>>
January 23 – 25, 2023: Schnizzfest in Phoenix, AZ REGISTER NOW>>
April 24 – 27, 2023: Connect IT Global in Las Vegas, NV REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!