Incident Response Planning Reduces Nation-State Cybercrime Risk

Here’s How to Boost Security Against Nation-State Threats Quickly & Cheaply
Today’s volatile security landscape is made even darker by the specter of nation-state cyberattacks. Those attacks are happening to a much wider array of targets than they used to as well, and every organization is at risk. An estimated 90% of Advanced Persistent Threat Groups (APTs) regularly attack organizations outside of the government or critical infrastructure sectors. That’s why it’s critical that organizations are ready to roll up their sleeves and get to work when trouble strikes with a solid, tested incident response plan.

Stop cyberattacks & save money: See why security awareness training is your best investment. DOWNLOAD NOW>>
Why Should My Organization Have an Incident Response Plan?
Cybercrime risk was high for businesses before the latest round of nation-state attacks in the Russia/Ukraine conflict. A whopping 94% of executives say their firms have experienced a business-impacting cyber-attack or compromise within the past 12 months. So it would seem logical that companies have already taken care of their incident response planning to ensure that they’re in a strong position if disaster strikes. Unfortunately, that’s not the case. But 1 in 3 businesses still don’t have an incident response plan, and that’s flirting with disaster.
It’s also a huge security blunder. Having a formal, tested incident response plan has game-changing benefits to a company’s security right away. IBM researchers determined that 39% of organizations with a formal, tested incident response plan experienced an incident, compared to 62% of those who didn’t have a plan. That’s an impressive reduction in risk just from being prepared. It’s also a power move when it comes to defending against typical nation-state cyberattacks like ransomware. This benefit doesn’t just spawn after you have an incident. Your company benefits right away and keeps benefiting even if you never use your incident response plan.

Is it time to update your security awareness training policy – or create one? These 6 tips can help! DOWNLOAD NOW>>
Tips on How to Build Your Incident Response Plan
Creating an incident response plan can be daunting. Here’s our best advice for making one that fits most companies.
Prepare Your People for Trouble
One of the first and most important steps in creating an incident response plan is putting together the team that will carry it out. A common expert-recommended method is to establish a Computer Security Incident Response Team (CSIRT). Your CSIRT isn’t just the people in IT; it is everyone in your organization who needs to be involved, from your IT teams to your communications shop. This is the group of folks who will also handle aspects of incident response in their specialty areas.
Choosing people with a diverse skill set in their specialty and plenty of institutional knowledge is beneficial. Set this group’s responsibilities, hierarchy, succession and capabilities, then assign people to fill these roles:
- Management
- Technical lead
- Legal support
- Communications
- Interface to the security committee
- Security officer
Source: Science Direct

Is someone’s behavior suspicious? Learn to spot trouble fast with 5 Red Flags That Point to a Malicious Insider at Work. DOWNLOAD IT>>
What Would an Incident Response Look Like for Me?
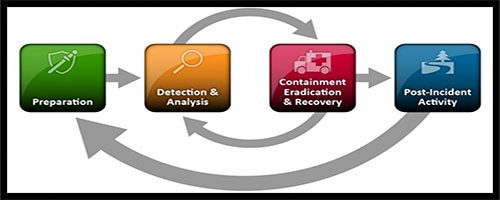
The generally accepted industry best practice for cybersecurity incident response is to follow the US National Institute of Standards and Technology (NIST) Incident Response Cycle, which divides incident response into four distinct steps that take you from start to finish and fit any cybersecurity incident.
The NIST Incident Response Cycle
- Preparation
- Detection & Analysis
- Containment, Eradication & Recovery
- Post Incident Activity

Can you spot a phishing email? This infographic shows you how to detect one! DOWNLOAD IT>>
Implementing the Cycle
Preparation
This may be the hardest step because it’s easy to rush through it. But this is also the most important step. Having the right people on the team will make all of the difference.
Create the Clean Up Team
When disaster strikes, like a malware incident or hacking, who gets the first call? Who do they call? Who has access to the things that are needed to triage the problem? Who is empowered to make tough calls? In an emergency, you need to be able to answer those questions quickly and definitively. That’s why every business should start its incident response planning with establishing a CSRIT.
Lay Out Your Framework
The framework of your plan will be customized to fit your company’s unique structure, resources and capabilities. Establish the parameters of your planning framework, then use that framework to create your response plan.
Detection and Analysis
The first step to fixing the problem (and mitigating the damage) is to figure out the problem. This is the step where your security personnel investigate the cause, extent and location of the damage, then report it to the CSRIT.
Containment, Eradication and Recovery
Containment
In this step, your CSRIT will decide how to minimize the damage from the incident and keep the business running. If worse comes to worst, this may also be a place where you’ll need to know what can be sacrificed if necessary and who is empowered to make those decisions.
Eradication
This is the step where your CSRIT decides what the most expedient and effective way of eliminating the problem is for your company. Every business had unique needs and capabilities, so this step may vary dependent on the systems and data affected. You may want to include multiple options that account for each variable that affects the choices that your team will encounter here.
Recovery
This is the step that requires the most pre-planning. Restoring your business to full operations may be impossible without secure backup and recovery options for your data. You may also need to bring in specialists to handle PR or compliance issues,
Post-Incident Activity
An after-action report is a must. It pays to immediately analyze the performance of your incident response plan and your CSRIT. Finding weaknesses in the plan or process and addressing them immediately will help you create a better plan for the future. Then, spend some time determining what you can do to reduce the chance of this being a problem for your company in the future.

Are you ready to slay the Monsters of Cybersecurity? This checklist tells you what you’ll need to succeed! GET CHECKLIST>>
Ignoring the Risk Won’t Make It Go Away
Companies can’t keep their heads in the sand about incident response, especially with threats like nation-state cybercrime hanging over them. Not thinking about what to do if you have an incident won’t prevent one from happening. But far too many companies are doing just that – 23% of the IT security managers say their company doesn’t have any protocols in place to report a suspected cyberattack and 33% say their companies don’t have a formal cybersecurity incident response plan at all. Don’t make the same mistake – spend time now on your incident response planning to reap great rewards later.
Unlock A Stronger Defense with Security Awareness Training
BullPhish ID is the perfect solution to use to make that happen!
- A huge library of security and compliance training videos with 4 new lessons added a month!
- Choose from plug-and-play or customizable phishing training campaign kits
- Automation makes training painless for everyone1
Watch Out for Dark Web Danger
Cybercriminals can do a lot with a compromised credential, like steal data and deploy ransomware. Compromised credentials are easy to obtain on the dark web and they open so many doors. An estimated 60% of data breaches involved the improper use of credentials in 2021.
Dark Web ID is the answer.
- 24/7/365 monitoring using real-time, analyst validated data
- Monitoring of business and personal credentials, including domains, IP addresses and email addresses
- Gain priceless peace of mind about dark web dangers
Are your credentials out there right now? CHECK YOUR PASSWORD >>

Get ready to pack your bags for Connect IT 2022! Join us June 20-23 in Las Vegas for the industry’s premier event! REGISTER NOW>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!