
The Secret to Building a Great Security & Compliance Awareness Training Program
See the key element that helps ensure the success of a security and compliance awareness training program.
Read More
See the key element that helps ensure the success of a security and compliance awareness training program.
Read More
These 7 influential factors play a big role in determining an organization’s true phishing risk and finding ways to reduce it.
Read More
Ransomware sprouts at a major US agriculture company, trouble for government agencies, Anonymous is still at it and the state of phishing threats.
Read More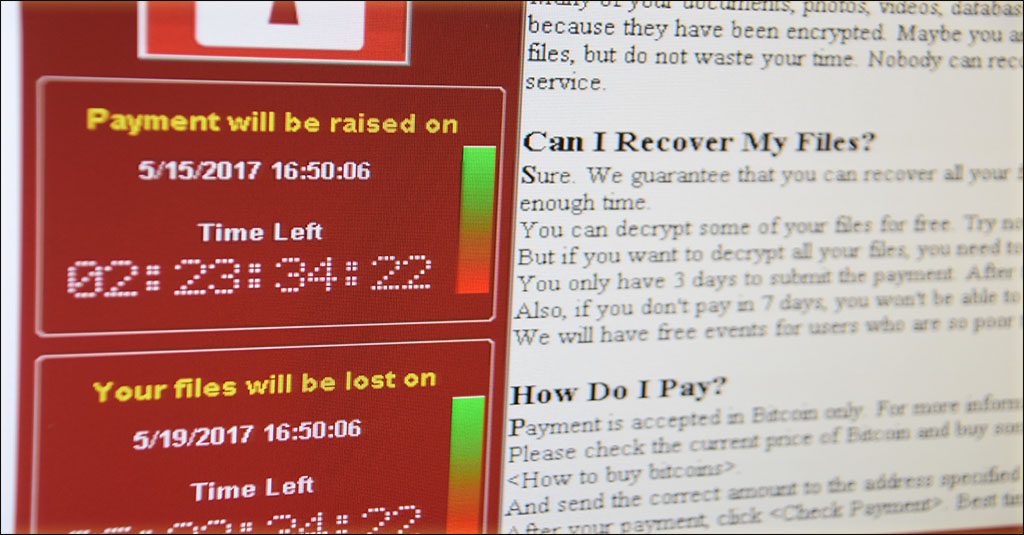

These tips can help you create an employee training program that increases ransomware awareness and reduces cyberattack risk.
Read More

Happy World Password Day. Don’t overlook these 6 ways that dark web related credential compromise endangers businesses.
Read More



2 attacks by new ransomware group Black Basta, trouble in energy and how to build a great security and compliance awareness training program.
Read More

See 10 facts about nation-state cybercrime that businesses need to know and 5 things to be on the lookout for to avoid trouble!
Read More

Learn more about why dark web monitoring is a must-have for every organization & how it’s an unsung hero against malicious insider threats.
Read More



Two big ransomware attacks on governments in Costa Rica & Brazil, dark times for Sunwing Air & the benefits of incident response plans.
Read More

More organizations face nation-state cybercrime threats than ever before. Learn about the players in the space & building a strong defense.
Read More