The Week in Breach News: 07/20/22 – 07/26/22

A new Twitter hack exposes data for 5.4 million accounts, LockBit scores hits on two municipalities, explore 3 major shifts in the data breach landscape and Powered Services Pro’s new Done-4-U 2.0.

See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>

Exploit: Hacking
Twitter: Social Media Network

Risk to Business: 2.783 = Moderate
Cybercriminals say that they’ve exploited a vulnerability in the Twitter platform to obtain data about 5.4 million accounts. Altogether, bad actors claim to have snatched data from 5.4 million accounts, with the data now up for sale on a hacker forum for $30,000. Twitter was alerted to the exploit in January 2022 and fixed it quickly, but the damage had already been done. The method used to scrape the data was similar to an attack on Facebook in 2021. Twitter has not confirmed or denied the attack as of press time, saying that the incident is under investigation.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business: Cybercriminals are always happy to exploit vulnerabilities and security gaps that allow them to obtain data.
ID Agent to the Rescue: Help your clients make sure they’ve dotted the i’s and crossed the t’s when it comes to security with The Computer Security To-Do List. DOWNLOAD IT>>
AllOne Health Resources, INC.
https://www.jdsupra.com/legalnews/allone-health-resources-inc-discovers-8173610/
Exploit: Business Email Compromise (BEC)
AllOne Health Resources: Insurance Company

Risk to Business: 1.672 = Severe
AllOne Health Resources, Inc. Has experienced a data breach as the result of a business email compromise attack. The company says that an unauthorized party gained access to sensitive consumer data contained on its network after landing the BEC attack. According to AllOne Health, the company discovered the breach after it realized that the company’s finance department had sent several wire transfers to a fraudulently created bank account. That prompted an investigation which revealed that bad actors had gained access to an employee’s email account and snatched sensitive data.











Individual Risk: 1.703 = Severe
Exposed information includes the names, addresses, dates of birth, driver’s license numbers, Social Security numbers and health information of 13,669 individuals.
How It Could Affect Your Customers’ Business A data security disaster in the healthcare sector is extra expensive and damaging after regulators weigh in.
ID Agent to the Rescue: Training helps employees avoid traps like BEC. Learn to build an effective program in How to Build a Security Awareness Training Program. DOWNLOAD IT>>
Blue Cross and Blue Shield (BCBS) of Massachusetts
https://healthitsecurity.com/news/bcbs-of-massachusetts-reports-third-party-vendor-data-breach
Exploit: Supply Chain Risk
Blue Cross and Blue Shield (BCBS) of Massachusetts: Insurance Company











Risk to Business: 1.701 = Severe
Blue Cross and Blue Shield (BCBS) of Massachusetts has filed a notice with the Maine Attorney General’s Office stating that the company had suffered a breach of employee pension data thanks to an insider incident at a vendor, LifeWorks US. BCBS of Massachusetts and BCBS of Massachusetts HMO Blue used the vendor for services related to employee pension plan payments. BCBS says that on May 17, 2022, a now former LifeWorks employee mishandled data by emailing spreadsheets containing identifiable information about BCBS employees to both their personal email address and the personal email address of another former LifeWorks employee.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business: Supply chain risk is an ongoing problem that won’t be going away anytime soon, and cybercrime doesn’t even have to be involved for it to damage a business.
ID Agent to the Rescue: See the biggest risks that businesses face today and get a look at what cyber threats your clients will be facing tomorrow in The Global Year in Breach 2022. DOWNLOAD IT>>
Entrust
Exploit: Ransomware
Entrust: Software Company











Risk to Business: 1.776 = Severe
Digital security software maker Entrust has confirmed that it suffered a cyberattack where threat actors breached its network and stole data from internal systems. Entrust says that about two weeks ago, bad actors penetrated security and gained access to corporate data. The company maintains that data theft does not have an impact on its products and services. No ransomware group has claimed responsibility for the attack as of press time, and no ransom demand has been released.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business: Bad actors aren’t just looking for PII/PHI or financial data, they’re also in the market to steal data about OT and proprietary data.
ID Agent to the Rescue: Get the resources that you need to help you protect clients from complex risks in the Deep Dive Into Cybersecurity Bundle. GET BUNDLE>>
Neopets
Exploit: Hacking
Neopets: Video Game Website











Risk to Business: 2.304 = Severe
Virtual pet website Neopets has suffered a data breach that resulted in the theft of source code and a database containing the personal information of over 69 million members. A hacker on the dark web going by the name TarTarX is selling the source code and database for the Neopets.com website for four bitcoins. Neopets recently launched NFTs that will be an element in an upcoming online Metaverse game.











Individual Risk: 2.215 = Severe
The data includes members’ usernames, names, email addresses, zip code, date of birth, gender, country, an initial registration email and other site/game-related information.
How it Could Affect Your Customers’ Business The bad guys are always hungry for big pools of data, and adding some source code to the mix makes it even better.
ID Agent to the Rescue Training makes everyone more aware of closing security gaps. Learn to build an effective program in How to Build a Security Awareness Training Program. DOWNLOAD IT>>
Gas South, LLC
https://www.securityweek.com/glass-and-metal-packaging-giant-ardagh-group-discloses-cyberattack
Exploit: Hacking
Gas South, LLC.: Natural Gas Company











Risk to Business: 1.929 = Severe
Atlanta, Georgia natural gas provider Gas South has disclosed a data breach that may have exposed consumer data. The company says that an unauthorized party had access to its network between February 13 and February 23, 2022, with access to sensitive consumer data related to 38,000 individuals. Gas South is the largest natural gas provider in the Southeastern United States.











Individual Risk: 2.215 = Severe
The consumer information exposed may have included customers’ Social Security numbers, driver’s license numbers and financial data.
How it Could Affect Your Customers’ Business Utilities and other infrastructure targets have been under the gun for the last year, with 14 of 16 critical infrastructure sectors hit by a cyberattack in 2021.
ID Agent to the Rescue The most likely vehicle for a cyberattack is a phishing message. Help your clients learn to spot phishing red flags with this informative infographic! GET INFOGRAPHIC>>


See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>


Qmunity
https://globalnews.ca/news/9009970/qmunity-cyber-attack/
Exploit: Hacking
Qmunity: Non-Profit











Risk to Business: 2.017 = Severe
Non-profit Qmunity, a 2SLGBTQ+ resource and online community provider, says that its website has been hacked, leading to service disruptions. Cybercriminals injected malicious code into the site, deferring users to download apps and illicit third-party pages. Most website functions have been restored and no client or personal data stored was accessed. This is the second cyberattack aimed at a Vancouver-based 2SLGBTQ+ resource in the past few weeks.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Adding or adjusting links to be malicious is a signature trick of cybercriminals and they never stop using it.
ID Agent to the Rescue Get the Building a Strong Security Culture checklist and send it to your clients to help them ensure that they’re making all the right security moves. GET CHECKLIST>>
The Town of St. Mary’s, Ontario
https://www.theverge.com/2022/7/22/23274372/st-marys-canada-lockbit-ransomware-cyber-incident
Exploit: Ransomware
St. Mary’s, Ontario: Municipality











Risk to Business: 2.017 = Severe
A ransomware attack has hit the town of St Mary’s in Ontario, locking staff out of internal systems and encrypted data. The ransomware group LockBit has claimed responsibility. The cybercriminals uploaded a sample to their leak site containing directories corresponding to municipal operations like finance, health and safety, sewage treatment, property files, and public works. Town officials were quick to reassure citizens that essential municipal services like transit and water systems haven’t been impacted. No word on any ransom demand or if the municipality plans to pay. LockBit is also responsible for another attack on a small town this week, hitting Frederick, Colorado on July 14. The group is demanding $200,000 not to publish the data snatched from Frederick, CO.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Governments and agencies have been targets for ransomware because the bad guys know they have a higher chance of getting paid thanks to the time-sensitive nature of government services.
ID Agent to the Rescue Learn how to choose a training solution that will offer you and your clients a high degree of satisfaction in our Security Awareness Training Buyer’s Guide for MSPs. DOWNLOAD IT>>


Watch this webinar to learn how to make Dark Web ID your prospecting secret weapon! WATCH NOW>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


See how today’s biggest threats may impact your MSP and your customers in our security blogs.
- 4 Reasons Why Upping Your Email Security Game Right Now is Mission Critical
- This Dynamic Duo Dramatically Reduces Phishing Risk
- 3 Major Email Security Threats & How to Conquer Them
- 3 Bottom-Line Reasons Why Every Business Should Have an Incident Response Plan
- Tips for Navigating the Security Awareness Training Program Development Landscape
- Training Transforms Employees into Security Assets Affordably
- The Week in Breach News: 07/13/22 – 07/19/22


Discover Powered Services Pro’s Done-4-U 2.0
Powered Services Pro’s Done-4-U 2.0, which includes full access to a social media scheduling and marketing platform with all the functionality you’ve been asking for. The platform will allow you to create and schedule your own content while also taking advantage of our monthly Done-4-U posts, but it won’t cost you anything extra. You can do away with tools like Hootsuite, Loomly, Buffer, etc., to save roughly $40 – $70 each month!
What’s New in Done-4-U 2.0:
✔️ Create a User Account for Increased Visibility & Tracking
Set up your own user account to view your schedule of Done-4-U posts and monitor your engagement analytics.
✔️ Easily Connect Your Social Media Profiles
With a streamlined, straightforward setup process, it takes just a few minutes to connect your company’s Facebook and LinkedIn accounts.
✔️ Reorder Your Done-4-U Posts & Customize the Messaging
With simple drag-and-drop functionality, reorder your Done-4-U posts to align with your overall marketing calendar. Easily customize the posts by editing the copy and adding your targeted hashtags and URLs to drive traffic to your blog posts, landing pages, and website.
✔️ Create & Publish Customized Content
From branded content pulled from the Powered Services Pro portal to your own graphics and videos, the user-friendly scheduler simplifies the publishing process while providing the flexibility to showcase your unique brand and messaging.
Enrollment in our enhanced Done-4-U 2.0 is available to you as part of your Powered Services Pro subscription at no additional charge. If you are currently enrolled in our Done-4-U social media program, our team will reach out within the next several days with additional information and setup instructions to support your transition to the new 2.0 platform in time for the August schedule of posts.
If you’re not currently enrolled and are interested in getting started, please contact your Channel Enablement Manager or email the Powered Services Pro team.


Take a deep dive into ransomware and learn to protect your clients affordably with this resource bundle! GET IT>>


3 Resources to Help You Expand Your Security Awareness Training Business
These resources are full of useful data and tips that can help you expand your security and compliance awareness training business, make compelling pitches to clients and prospects as well as overcome objections.
Security Awareness Training: Buyer’s Guide for MSPs
Explore the features and benefits of security training solutions and find the best one for your MSP and your customers. DOWNLOAD IT>>
The Global Year in Breach 2022
Everything that you need to know about the influences that drove today’s cybersecurity trends and will drive tomorrow’s. DOWNLOAD IT>>
Security Awareness Training: Buyer’s Guide For Businesses
Share this resource with your customers to help them see why security training is a must-have and a great investment. DOWNLOAD IT>>
Did you miss…the Q3 BullPhish ID & Graphus Product Update webinar. WATCH IT>>


Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>




3 Key Takeaways from IRTC Q1 Data Breach Report
See where threats to your clients’ data are coming from!
The data breach landscape is always in flux, and it has been evolving quickly in the last few years. As cybercrime numbers have jumped up, more organizations than ever are dealing with the menace of cybercriminals that are after their data. That means that your clients are at risk of a data disaster. The new Identity Theft Resource Center (ITRC) H1 2022 Data Breach Report illustrates the shifting sands of data security and offers a look at the vectors of the threats to their data that your clients are facing every day.


Gain expert insight in the MSP Cybersecurity Roundtable: How Infrastructure Attacks Can Hurt Every Business. WATCH NOW>>
Data Compromise Numbers Are Up Quarter-Over-Quarter
Data compromises have slightly increased between Q1 and Q2 2022, following a continual pattern of small but significant increases quarter over quarter. But year over year, the pace of data compromises has slowed a little bit. The number of data compromises that ITRC researchers noted in the first half (H1) of 2022 is down 4% percent compared to the same period in 2021, down from a record high of 1862 in 2021. So far in 2022, ITRC researchers have logged 817 publicly reported data breaches that added up to over 53 million victims. That’s a slight decrease from the same period in 2021 when ITRC logged a record-high 851.
H1 Compromise Report
- Total Data Compromises: 817 compromises; 53,350,425 victims
- Data Breaches: 802 data breaches; 46,209,107 victims
- Data Exposures: 10 data exposures; 7,136,948 victims
Researchers were quick to note that the declines in data compromise numbers could be due to an undesirable factor that played a big part in this report. In past years, most data breaches that ITRC recorded were attributed to a specific cause, but an increasingly large number of breaches that investigators are recording don’t have a cause attributed to them at all. An estimated 40% of data breach notices did not include basic information that allowed the researchers to categorize them accurately, such as attack vector and/or a victim count. That led to “unknown” making its way to the top of the list as the primary cause of data breaches so far this year, for the first time since ITRC began tracking them.
Why this matters: Even a slight increase in data compromises is bad news for businesses. Plus, the added complication of a large number of compromises that don’t have a cause attributed to them will make everyone’s job a little harder because it will make it harder for IT professionals to gain a clear picture of the direction that trouble might come from next.


Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>
Phishing Was the #1 Root Cause of Data Compromises in H1 2022
Phishing never stops being the bane of every IT professional’s job and the root cause of more data breaches than any other cyberattack in the first half of 2022. A flood of phishing has been inundating businesses, with a new record set in the number of phishing attacks recorded in Q1 2022, surpassing 1 million recorded attacks for the first time. For instances of a data breach where the cause was specified in this report, the phishing/smishing/BEC category reigned supreme, the cause of 219 breaches, followed by ransomware and other malware.
Origins of H1 Cyberattacks That Spawned a Data Breach
| Cause | Number |
| Phishing/smishing/BEC | 219 |
| Ransomware | 124 |
| Malware | 46 |
| Other | 17 |
| Non-secured Cloud Environment | 5 |
| N/A – not specified | 317 |
| Credential Stuffing | 6 |
Total: 734 breaches impacting 35,891,170 victims
Source: ITRC
That squares with recent data that shows that email is the riskiest channel for data loss in an organization, but phishing isn’t always the culprit for an organization’s email-related data loss. In a recent study, 65% of IT security practitioners cited email as their biggest data loss risk, followed by cloud file-sharing services (62%) and instant messaging platforms (57%). Much of that data loss was the result of improper employee behavior including mistakes and malicious insider activity. The leading cause of data loss incidents (40%) was employee negligence like the failure to comply with data security policies. An estimated 23% of organizations in the study experienced up to 30 security incidents involving employees’ use of email every month ranging from sending the wrong file to interacting with a phishing message.
Why this matters: It’s no secret that phishing is the biggest data compromise and cyberattack risk that your clients face but quantifying it can make it easier for clients to understand the depth of the problem and how it could impact them. This is good data to use when discussing your client’s email security needs and why it may be time for an upgrade.


Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>
An Estimated 87% of Data Compromises in H1 2022 Were Due to a Cyberattack
Cyberattacks are the top reason for data compromise overall, a result that isn’t unexpected. This is also where the lack of attribution in many of the data compromises in this period comes into play most significantly. Of the 367 breaches noted in Q2 2022, 169 of them had an unspecified root cause. But for the data breaches that did have a cause attributed, Phishing/BEC is at the top of the list followed by ransomware. There was a shift in the number of ransomware attacks that researchers logged between Q1 and Q2 2022. Ransomware attacks that could be linked to breaches dropped 20% in Q2 2022 from the previous quarter, the first drop since the ITRC began tracking ransomware in 2018. Researchers speculated on a number of factors that may have contributed to that decline, including the ongoing conflict in Ukraine and the downfall of cryptocurrencies.
When looking at year-over-year data the pattern is clear. Data compromises are increasing at a rapid clip every year, wth a major jump between 2020 and 2021. We’ve only got half-year data for 2022 so far, but it doesn’t look like threats to your clients’ data will abate anytime soon.
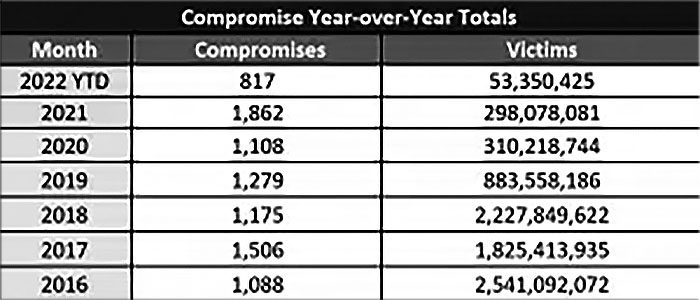

Source: ITRC
Why this matters: Every little bit of threat intelligence helps. Knowing the vectors of cyberattack-related data compromises, can help you better secure your clients from data compromise threats now and down the road. It also gives you information that you can use to establish a foundation for the argument that your clients need security upgrades.


Get tips from experts in our webinar MSP Cybersecurity Roundtable: How to Improve Your Incident Response Plan WATCH NOW>>
ID Agent Solutions Will Help You Protect Your Clients’ Data
The innovative solutions in the ID Agent digital risk protection platform can help secure your clients’ data and reduce their data breach risk affordably.
Security awareness and compliance training plus phishing simulation
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size.
- An extensive library of security and compliance training videos in eight languages
- Plug-and-play or customizable phishing training campaign kits
- New videos arrive 4x per month and new phishing kits are added regularly
- Easy, automated training delivery through a personalized user portal
Dark web monitoring
Dark Web ID offers best-in-class dark web intelligence, reducing credential compromise risk.
- 24/7/365 monitoring using real-time, machine and analyst-validated data
- Fast alerts of compromises of business and personal credentials, including domains, IP addresses and email addresses
- Live dark web searches find compromised credentials in seconds
- Create clear and visually engaging risk reports
Learn more about security awareness and phishing simulation training with BullPhish ID? Book a demo


This MSP-focused guide gives you insight into finding the ideal dark web monitoring solution. GET THE GUIDE>>


July 27 – 28: ASCII Success Summit Toronto REGISTER NOW>>
July 28: Dark Web ID & Passly Product Update Q3 Webinar REGISTER NOW>>
August 6 – 7: ISSA Cyber Executive Forum REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!