The Week in Breach News: 08/03/22 – 08/09/22

Supply chain breaches lead to expensive problems for the UK NHS and Aetna, a ransomware kerfuffle in an Iowa school district and explore three factors that make a data breach more or less expensive.

See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>

Aetna
https://www.bankinfosecurity.com/aetna-reports-326000-affected-by-mailing-vendor-hack-a-19691
Exploit: Supply Chain
Aetna: Insurer

Risk to Business: 2.631 = Moderate
Health insurance heavyweight Aetna has reported a data breach to federal regulators affecting nearly 326,000 individuals. This breach was spurred by a ransomware attack at a service provider for an Aetna subcontractor, mailing company OneTouchPoint. This incident is one of the first reported as a direct result of that cyberattack. The OneTouchPoint breach is expected to impact over 30 large and small health insurers and plan providers.



Individual Risk: 2.755 = Moderate
Aetna said that the exposed information for individuals may include names, addresses, dates of birth, and limited medical information.
How It Could Affect Your Customers’ Business: Business services companies are becoming choice targets for cybercriminals looking for quick scores of data.
ID Agent to the Rescue: Our Monsters of Cybersecurity eBook helps you discover and mitigate the killer risks that are lurking around every corner. DOWNLOAD IT>>
Lin-Mar School District
https://www.kcrg.com/2022/08/03/leaked-image-shows-ransomware-attack-hit-linn-mar-school-district/
Exploit: Ransomware
Lin-Mar School District: Local Public Education Authority










Risk to Business: 2.372 = Severe
Thanks to a bit of timely reporting by local media, it has been revealed that the Lin-Mar School District in Iowa has become a victim of the Vice Society ransomware group. Screenshots of the group’s ransom note were given to the media by an anonymous district staff member. This leak occurred after the school district informed parents and students that it was suffering unspecified “technical difficulties”, raising concerns about the district’s readiness to open for the new school year. The school district has so far refused further comment.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business School districts will be especially appealing right now since the new school year time crunch makes them more likely to pay a ransom.
ID Agent to the Rescue: Learn to build an effective program that reduces cyberattack risk with the guide How to Build a Security Awareness Training Program. DOWNLOAD IT>>
Wisan Smith Racker & Prescott
https://www.jdsupra.com/legalnews/wisan-smith-racker-prescott-confirms-5913417/
Exploit: Hacking
Wisan Smith Racker & Prescott: Accounting Firm










Risk to Business: 1.716 = Severe
Salt Lake City Utah Based accounting firm Wisan Smith Racker & Prescott has disclosed that they have experienced a data breach. On June 14, 2022, the firm learned that an unauthorized party had penetrated its IT security and accessed information about their clients. That information was subsequently used to file fraudulent tax returns supposedly on behalf of several of the company’s clients. Data breach letters have been sent to all of the clients impacted by this breach.










Individual Risk: 1.788 = Severe
The exposed information varies depending on the individual, but it may include a clients’ name, Social Security number, driver’s license or state identification card number, passport number, military identification number, government-issued identification number, financial account information, date of birth, electronic signature, medical information and health insurance information.
How It Could Affect Your Customers’ Business: Ransomware attacks on service providers in the supply chain are an ongoing problem that won’t be going away anytime soon.
ID Agent to the Rescue: See the biggest risks that businesses face today and get a look at what cyber threats your clients will be facing tomorrow in The Global Year in Breach 2022. DOWNLOAD IT>>
Goodman Campbell Brain and Spine
https://www.bankinfosecurity.com/neuro-practice-tells-363000-that-phi-was-posted-on-dark-web-a-19706
Exploit: Ransomware
Goodman Campbell Brain and Spine: Specialty Medical Practice










Risk to Business: 1.719 = Severe
Goodman Campbell Brain and Spine, a medical practice in Indiana, has disclosed that it has experienced a data breach as a result of a suspected ransomware attack. The Hive ransomware group is implicated in the attack. The practice noted that they discovered the attack had been successful on May 20, 2022. An estimated 363,000 people had data exposed in this incident.










Individual Risk: 1.606 = Severe
Information affected in the incident includes patient PII and PHI including name, date of birth, address, telephone number, email addresses, medical record number, patient account number, diagnosis and treatment information, physician name, insurance information, dates of service and Social Security numbers.
How it Could Affect Your Customers’ Business: Healthcare is the industry with the highest data breach cost, and its’ been beleaguered by ransomware.
ID Agent to the Rescue: Get the resources that you need to help you protect clients from complex risks in the Deep Dive Into Cybersecurity Bundle. GET BUNDLE>>


See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>


United Kingdom – National Health Service
https://www.bbc.com/news/uk-wales-62442127
Exploit: Supply Chain
National Health Service: Healthcare System










Risk to Business: 2.304 = Severe
United Kingdom’s National Health Service (NHS) has experienced a service outage of its 111 non-emergency medical service system that was triggered by a cyberattack that hit the systems of British MSP Advanced. The MSP’s Adastra system is used by 85% of NHS 111 services for patient management. Advanced said that the suspected ransomware attack was spotted at 07:00 BST last Thursday. This attack has had a widespread impact, affecting ambulance dispatch, out-of-hours appointment bookings and emergency prescriptions throughout the UK. Advanced says that the issue may not be resolved until this week. The emergency 999 system was not impacted.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business This is a great illustration of how no organization is safe from potential supply chain trouble.
ID Agent to the Rescue Help your clients make sure they’ve dotted the i’s and crossed the t’s when it comes to security with The Computer Security To-Do List. DOWNLOAD IT>>
Germany – Semikron
Exploit: Ransomware
Semikron: Semiconductor Manufacturer










Risk to Business: 1.529 = Severe
Semikron, a manufacturer of semiconductors for electric vehicles and industrial automation systems, has confirmed it has fallen victim to a ransomware attack, likely by the LV ransomware group. The attackers are demanding an unspecified ransom after stealing an estimated 2TB of documents and encrypting systems at the Nuremberg-based company. No specifications have been given for the exact data types stolen or the ransom amount demanded.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Service disruptions from cyberattacks can cost manufacturers and the companies that they supply a fortune.
ID Agent to the Rescue The most likely vehicle for a cyberattack is a phishing message. Help your clients learn to spot phishing red flags with this informative infographic! GET INFOGRAPHIC>>
Germany – The Association of German Chambers of Industry and Commerce (DIHK)
Exploit: Ransomware
The Association of German Chambers of Industry and Commerce (DIHK): Business Association










Risk to Business: 2.017 = Severe
The Association of German Chambers of Industry and Commerce (DIHK) has announced that it has been the victim of what it characterized as a “massive cyberattack”. The organization said that all internet connections at the organization were shut off as a way to address the issue, leading to phone, email and website outages that impacted all 79 local outposts to varying degrees. The DIHK is a business association that notes that it helps companies with legal issues, provides general support and promotes German businesses internationally.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Groups like this offer a great opportunity for cybercriminals to snatch profitable and useful data.
ID Agent to the Rescue Get the Building a Strong Security Culture checklist and send it to your clients to help them ensure that they’re making all the right security moves. GET CHECKLIST>>
Luxembourg – Encevo Group
Exploit: Ransomware
Encevo Group: Energy Conglomerate










Risk to Business: 2.017 = Severe
The BlackCat/ AlphV ransomware group is allegedly responsible for a ransomware attack that landed on two subsidiaries of the Encevo Group, a Luxembourg-based energy supplier. The company disclosed that energy network operator Creos and supplier Enovos had been affected. The attack took down customer portals for both companies but did not affect the supply of electricity and gas. The Encevo Group is partially owned by the government of Luxembourg. The attackers claim to have stolen 150 GB of data that they said includes contracts, passports, bills and emails although that has not been confirmed by Creos, Enovos or the Encevo Group.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business The energy sector has been a popular target for the bad guys who are continuing to pound critical infrastructure with ransomware attacks.
ID Agent to the Rescue Learn how to choose a training solution that will offer you and your clients a high degree of satisfaction in our Security Awareness Training Buyer’s Guide for MSPs. DOWNLOAD IT>>


Learn to identify and mitigate fast-growing supply chain risk with this eBook. DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


See how today’s biggest threats may impact your MSP and your customers in our security blogs.
- 2 Factors Make Data Breaches More Expensive
- AI is a Cost Mitigation Superstar for a Data Breach
- Inside 3 Specialized Phishing Attacks
- 10 Facts About Business Email Compromise That You’ve Got to See
- The Week in Breach News: 07/27/22 – 08/02/22


See How Our Solutions Have Performed
Are you interested in seeing performance data from BullPhish ID, Dark Web ID and Graphus? Our annual reports are full of product-specific data like:
- Which BullPhish ID phishing simulations fooled employees
- What types of phishing messages Graphus stopped
- How many compromises were uncovered with Dark Web ID
Download The State of Email Security 2022 and The Global Year in Breach 2022 for the whole story.


Solve five of the most exhausting remote and hybrid security problems fast with this handy infographic! DOWNLOAD IT>>


Take a deep dive into ransomware and learn to protect your clients affordably with this resource bundle! GET IT>>


Have You Watched Our MSP Cybersecurity Roundtable Series?
Take some time to sit down and learn about today’s hottest cybersecurity issues from experts with our MSP Cybersecurity Roundtable webinar series. The next webinar in this series is Insider Risk, coming up next week on Tuesday, August 16th. Register for that webinar now!
MSP Cybersecurity Roundtable recordings that are available now:
How Infrastructure Attacks Can Hurt Every Business
Nation-State Hacking: It’s Everyone’s Problem Now
How to Improve Your Incident Response Plan
Did you miss…? The Security Awareness Training Buyer’s Guide for MSPs DOWNLOAD IT NOW>>


Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>



These 4 Variables Dramatically Impact the Cost of a Data Breach
Learn What Makes the Cost of a Data Breach Better or Worse
A data breach is an expensive disaster for any organization. As the IBM Cost of a Data Breach 2022 report revealed, the cost of a data breach has gone up, reaching $4.35 million this year, a new record. That’s an increase of 2.6% from the 2021 data breach cost of $4.2 million per incident, and a substantial increase in the cost of a breach in a two-year span, up 12.7% from 2020’s $3.86 million. Many factors can impact the cost of a data breach. Here’s a look at three cost factors that can increase or decrease the cost of a data breach for most organizations.


Get 10 tips to help you build a strong security culture & reduce your risk of cybersecurity trouble! GET INFOGRAPHIC>>
These 4 Variables Impact the Cost of a Data Breach
When looking at the overall picture of contributing factors to increased and decreased cost for organizations that experience a data breach, it’s easy to see that some circumstances, technologies and investments can greatly increase or decrease the cost of a data security event. Unfortunately, most IT professionals know that in today’s volatile cybercrime landscape, it’s no longer a question of “if” when it comes to a company experiencing a data breach, it’s a “when”. Especially when factoring in risks that are beyond your client’s control like supply chain trouble. Taking a look at this chart of factors that impact the cost of a data breach can help you guide your clients into making security investments and process improvements that will help them avoid additional expenses in the event of a data breach.
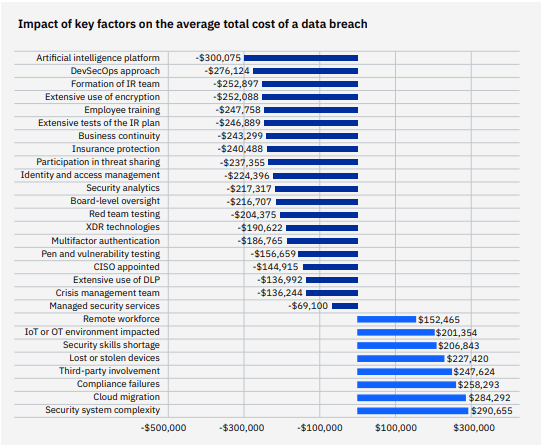

Source: IBM


Find the right dark web monitoring solution for your customers & your MSP with this checklist! DOWNLOAD IT>>
Reduces cost: AI & security automation
First, the good news: AI and security automation are great ways to reduce the cost of a data breach. This is the fifth year that researchers have examined the impact of those technologies on the cost of a data breach. Companies that have taken the plunge and transformed their security with automation and AI-powered tools save a substantial sum in the event that they have a data breach. Researchers determined that a data breach in an organization that has fully deployed security AI and automation costs $3.05 million less than breaches at organizations with AI and automation deployed. That’s a huge 65.2% difference in average breach. The higher the level of AI and automation, the more a company saves in breach costs. AI and security automation came out on top as the number one factor that can reduce the cost of a data breach for a company.
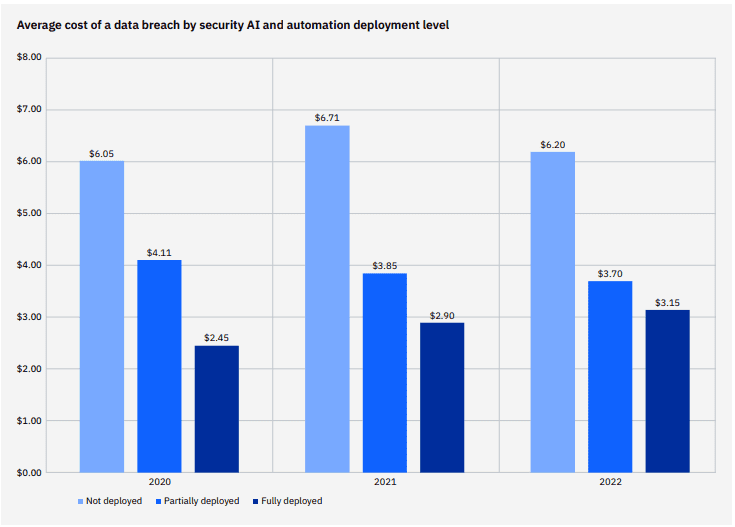

Source: IBM


It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>
Drives cost up: remote workers
Now for some bad news: remote work is a factor that can drive the cost of a data breach up. Companies that support almost total or a totally remote workforce (81 – 100% of their workers) are in the best position here, but their breach costs will still be higher than the baseline average ($4.35 million) at $5.10 million. That’s slightly lower than the increase in data breach costs experienced by companies in this cohort in 2021, but still a major increase from the average. In all other cases, the cost of a data breach when supporting a remote workforce in 2022 is significantly higher than it was in 2021.
Remote workforce support has been a challenge for businesses forced to pivot quickly at the start of the global pandemic. IBM has been tracking the impact of remote workers on the cost of a data breach for three years in response to that development. A major complication that businesses that support a remote workforce face in the event of a data breach is whether or not that breach was directly caused by a remote worker. There’s a considerable effect on the cost of a breach when a remote worker was the root cause of the breach, like when a remote worker falls for a phishing attack that leads to credential compromise. On average, a data breach caused by a remote worker adds about $1 million to the bill or 21.5% more than the general average.
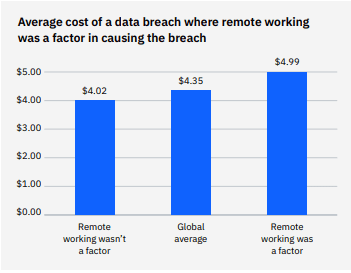

Source: IBM


Learn why ransomware is today’s nastiest threat and how to defend against it in Ransomware 101. READ IT>>
Drives cost up: compliance failures
It’s no surprise that regulatory penalties and compliance failures drive the cost of a data breach up. This factor is one of the most worrisome aspects of a breach for companies in highly regulated industries and may result in fines and penalties that tack on big bills years after the data breach takes place. In fact, a data breach that features any level of compliance failures adds about $258k to the total bill. The higher the level of compliance failures, the bigger the price tag, with a difference of $2.26 million, or 50.9%, between high levels and low levels of compliance failure in the event of a breach. Compliance failures are the third biggest factor in increasing the cost of a data breach behind cloud migration in second place and security system complexity in first place.
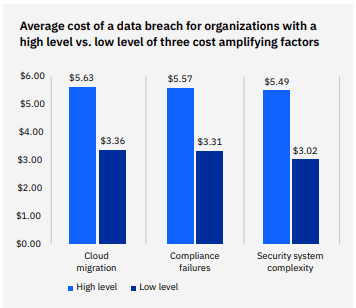

Source: IBM
Compliance failures pack a big punch. Organizations lose an average of $4 million in revenue due to a single non-compliance event. The penalties for compliance violations vary wildly by statute, severity, industry and geography, but here are a few averages to keep in mind:
- For a HIPAA violation, a company could be looking at penalties ranging from $100 to $50,000 per violation (or per record).
- A GDPR penalty could set a company back up to 4% of its annual global revenue or 20 million euros ($22.8 million).
- A company in breach of PIPEDA requirements can be fined up to $100,000 for each violation.


Learn the secret to conjuring up amazing stress-free marketing campaigns in 5 Ways to Make Marketing Magic! GET IT>>
Choose Security Solutions That Can Get the Job Done
You and your clients can feel confident that you’ve made a smart move when you choose our security solutions that include automated components and a robust menu of features.
Security awareness and compliance training plus phishing simulation
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size.
- An extensive library of security and compliance training videos in eight languages.
- Plug-and-play or customizable phishing training campaign kits.
- New videos arrive 4x per month and new phishing kits are added regularly.
- Easy, automated training delivery through a personalized user portal.
Dark web monitoring
Dark Web ID offers best-in-class dark web intelligence, reducing credential compromise risk.
- 24/7/365 monitoring using real-time, machine and analyst-validated data.
- Fast alerts of compromises of business and personal credentials, including domains, IP addresses and email addresses.
- Live dark web searches find compromised credentials in seconds
- Create clear and visually engaging risk reports.
Email security
Graphus AI-enabled, automated email security that catches 99.9% of sophisticated phishing threats and offers amazing benefits.
- Forget old-fashioned safe sender lists. Graphus analyzes the content of messages using more than 50 points of comparison to suss out fakes fast.
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- Put 3 layers of protection between employees and dangerous email messages.
- Don’t waste time on fussy configurations or adding threat reports. AI does that for you, getting everything up and running with just a few clicks and minimal maintenance.
Click here to watch a video demo of Graphus now.
NEW INTEGRATION! If you’re already using BullPhish ID for security and compliance awareness training and phishing simulations, you’ll love our latest integration Advanced Phishing Simulations (Drop-A-Phish). This feature leverages the power of integration with Graphus to eliminate the need for domain whitelisting and ensure 100% campaign deliverability to end users when running phishing simulations. LEARN MORE>>


Make sure your clients have all the bases covered with the Computer Security To-Do Checklist! GET IT>>


August 16: MSP Cybersecurity Roundtable Insider Risk REGISTER NOW>>
August 23: How to Grow Your Revenue with Dark Web ID REGISTER NOW>>
August 25: A 15-Minute Demo: Graphus AI-Driven Email Security REGISTER NOW>>
September 16: Cybersecurity Summitt in Charlotte REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!