The Week in Breach News: 08/31/22 – 09/06/22

Welcome to the Business Email Compromise special edition! This week, take a look at some recent BEC attacks and learn more about how to protect your clients from phishing-related disasters like BEC.

Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>

Klaviyo
Exploit: BEC
Klaviyo: Email Marketing Firm

Risk to Business: 1.706 = Severe
In an interesting twist on the usual data breach incident, email marketing firm Klaviyo suffered a concentrated and specific data breach on August 3, 2022. After gaining access to an employee’s account thanks to a successful phishing attack, bad actors then downloaded marketing lists used by cryptocurrency-related clients for outreach efforts and for Klaviyo product and marketing updates.
The threat actor used the internal customer support tools to search for primarily crypto-related accounts and viewed list and segment information for 44 Klaviyo accounts, downloading data from at least 38 accounts.
Stolen data includes customers’ names, addresses, email addresses, account profile information and phone numbers. The hackers also downloaded two internal lists used by Klaviyo for product and marketing updates that contain names, addresses, email addresses, and phone numbers.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business: Phishing is the most likely way for any organization to open the door to a data breach.
ID Agent to the Rescue: See the reasons why an AI-driven automated email security solution is the answer to email security challenges and why you and your clients will love it. DOWNLOAD INFOGRAPHIC>>
Atrium Health
Exploit: BEC
Atrium Health: Medical System








Risk to Business: 1.907 = Severe
North Carolina-based Atrium Health has announced a data breach impacting 7,000 patients. The healthcare provider says that an employee at Atrium Health at Home fell victim to a phishing attack, resulting in bad actors accessing that employee’s email and messaging account in April 2021. Atrium is mailing letters to the affected patients and hasn’t determined whether the unauthorized user accessed the protected health information in the accounts.
North Carolina-based Atrium Health has announced a data breach impacting 7,000 patients. The healthcare provider says that an employee at Atrium Health at Home fell victim to a phishing attack, resulting in bad actors accessing that employee’s email and messaging account in April 2021. Atrium is mailing letters to the affected patients and hasn’t determined whether the unauthorized user accessed the protected health information in the accounts.
How It Could Affect Your Customers’ Business: Healthcare data is always a desirable commodity for bad actors and letting them get their hands on it is always an expensive mistake for healthcare providers.
ID Agent to the Rescue: Security awareness training can help companies prevent costly mistakes like this. Learn how to make it happen in How to Build a Security Awareness Training Program. GET IT>>


Gain expert insight in the MSP Cybersecurity Roundtable: How Infrastructure Attacks Can Hurt Every Business. WATCH NOW>>
Spirit Super
Exploit: BEC
Spirit Super: Financial Services








Risk to Business: 1.836 = Severe
Spirit Super has announced that a cyberattack caused by an employee falling for a phishing message is the cause of a cyberattack that has led to data exposure for an estimated approximately 50,000 member records from 2019/2020. The company said that the incident was quickly mitigated, and the damage contained, with new security measures added.
Spirit Super says that the information potentially exposed includes client names, addresses, ages, email addresses, telephone numbers, member account numbers and member balances. The company was quick to assure members that the exposed data doesn’t include dates of birth, government identification numbers or any bank details.
How It Could Affect Your Customers’ Business: Phishing is the first step in more than 90% of data breaches, making stopping it a top security priority.
ID Agent to the Rescue: See the biggest risks that businesses in different sectors face today and get a look your clients will be facing tomorrow in The Global Year in Breach 2022. DOWNLOAD IT>>


Learn to identify and mitigate fast-growing supply chain risk with this eBook. DOWNLOAD IT>>
Chester Upland School District
Exploit: BEC
Chester Upland School District: Regional Education Authority








Risk to Business: 1.337 = Severe
A recent business email compromise attack on a Pennsylvania school district resulted in bad actors making off with more than $13 million. Authorities say hackers used a stolen district employee email account to snatch the money by sending official-looking messages from that account and then diverting payments to themselves. After diverting the payments, the cybercriminals then used a romance scam conducted through the dating site eHarmony to entice a Florida woman to launder the money unwittingly. The scheme came to light after the Pennsylvania Department of the Treasury flagged a large transfer, unraveling the whole mess. $10 million of the money has since been recovered.
How it Could Affect Your Customers’ Business: Business email compromise is hard to detect but causes the most financial damage. This school district got lucky recovering money.
ID Agent to the Rescue: Learn to build an effective program that reduces cyberattack risk with the guide How to Build a Security Awareness Training Program. DOWNLOAD IT>>
AllOne Health Resources, INC.
https://www.jdsupra.com/legalnews/allone-health-resources-inc-discovers-8173610/
Exploit: BEC
AllOne Health Resources: Insurance Company








Risk to Business: 1.809 = Severe
AllOne Health Resources, Inc. Has experienced a data breach as the result of a business email compromise attack. The company says that an unauthorized party gained access to sensitive consumer data contained on its network after landing the BEC attack. According to AllOne Health, the company discovered the breach after it realized that the company’s finance department had sent several wire transfers to a fraudulently created bank account. That prompted an investigation that revealed that bad actors had gained access to an employee’s email account and snatched sensitive data.
Exposed information includes the names, addresses, dates of birth, driver’s license numbers, Social Security numbers and health information of 13,669 individuals.
How it Could Affect Your Customers’ Business: A data security disaster in the healthcare sector is extra expensive and damaging after regulators weigh in.
ID Agent to the Rescue: Are you offering the right training solution to help your clients avoid risks like this? Find out with the Security Awareness Training: Buyer’s Guide for MSPs DOWNLOAD IT>>


See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>
City of Portland, OR
https://therecord.media/cybercriminal-scams-city-of-portland-ore-for-1-4-million/
Exploit: BEC
City of Portland, OR: Municipal Government








Risk to Business: 1.723 = Severe
Bad actors struck the city of Portland, Oregon in an audacious business email compromise attack that resulted in a $1.4 million fraudulent transaction with city funds in April. City officials say that cybercriminals obtained the money after gaining access to a city email account illegally. The compromise was detected in May when the same account attempted another transfer of funds. The incident is under investigation by the FBI, U.S. Secret Service and the Portland Police Bureau.
How it Could Affect Your Customers’ Business: Governments have been popular targets for cybercriminals even when they’re not nation-state aligned.
ID Agent to the Rescue: A strong security culture reduces the risk of an incident. Help your clients build one with The Building a Strong Security Culture Checklist! DOWNLOAD IT>>
Christie Clinic
https://www.securityweek.com/500000-impacted-email-breach-illinois-healthcare-firm
Exploit: BEC
Christie Clinic: Healthcare Provider








Risk to Business: 1.801 = Severe
Illinois medical services provider Christie Clinic has informed an estimated 500,000 individuals that their personal information was potentially compromised in a data breach that occurred last year. In the incident, a bad actor gained unauthorized access to one of the practice’s email accounts in a suspected business email compromise operation with the intent of interrupting financial communications between July 14 and August 19, 2021. The practice assured patients that the bad actor did not compromise other systems, electronic medical records, or the firm’s patient portal.
Christie Clinic is unsure of the scope of the breach but says that the bad actor may have gained access to patient names, addresses, medical and health insurance information and Social Security numbers through the compromised account.
How it Could Affect Your Customers’ Business: Business email compromise is the most expensive cyberattack businesses face and in this case, that price will come with regulatory trouble.
ID Agent to the Rescue: Cybersecurity horrors lurk around every corner, lying in wait for unwary organizations. Learn how to defeat them in our eBook Monsters of Cybersecurity. DOWNLOAD IT NOW>>


See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


See how today’s biggest threats may impact your MSP and your customers in our security blogs.
- Ransomware Attacks on Healthcare Organizations Have Devastating Results for Providers & Patients
- Almost Three-Quarters of Cyberattacks Have Something in Common: Phishing
- Why You Should Be on the Lookout for Spear Phishing & How to Spot It
- 4 Reasons Why Ransomware Risk Won’t Stop Rising for SMBs
- The Week in Breach News: 08/17/22 – 08/23/22


Solve five of the most exhausting remote and hybrid security problems fast with this handy infographic! DOWNLOAD IT>>


Resources to Help You Combat BEC
Learn more about how you can help your clients reduce their risk of a phishing-related disaster like BEC with these tools.
eBook: How to Build a Security Awareness Training Program
Webinar: Critical Components of a Profitable and Effective Security Awareness Program
Infographic: Building a Strong Security Culture Checklist
Did you miss… Are Your Users Trained to Handle These Risks? Checklist. GET IT>>


Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>




3 Paths to a Profitable Discussion About BEC & Phishing
What component appears in the vast majority of damaging cyberattacks? If you said phishing, you’re right. According to the analysis presented in the 2022 Unit 42 Incident Response Report, more than two-thirds of cyberattacks on businesses in the last 12 months are typically phishing-based scenarios. The two most punishing attacks that businesses have faced this year are business email compromise (BEC) and ransomware. Ransomware is the culprit for over one-third (36%) of business cyberattacks, followed by BEC in second place with another third of the cyberattacks (34%) analyzed in this report. Add that up and it’s easy to see that phishing is a dangerous enemy that your clients can’t afford to discount. Unfortunately, it can be a challenge to get clients to take phishing seriously.
BEC & Phishing Go Hand in Hand
Wired magazine recently warned that the combination of heavy scrutiny and high levels of law enforcement action around recent high-profile ransomware attacks are likely to push top ransomware groups into exploring new horizons. That will result in many skilled cybercriminals looking for a new way to make money, and BEC is a very attractive proposition. These bad actors can easily leverage their existing resources and skillset to shift operations into BEC. Social engineering is a critical component of BEC, and the bad guys have extensive expertise in that area. Ransomware groups also have the skills to easily establish “initial access” because they can call on their previous relationships with initial access brokers and other dark web resources. Plus, the software that they use is designed to be malleable, making it easy for them to jump in and conduct a successful attack quickly.
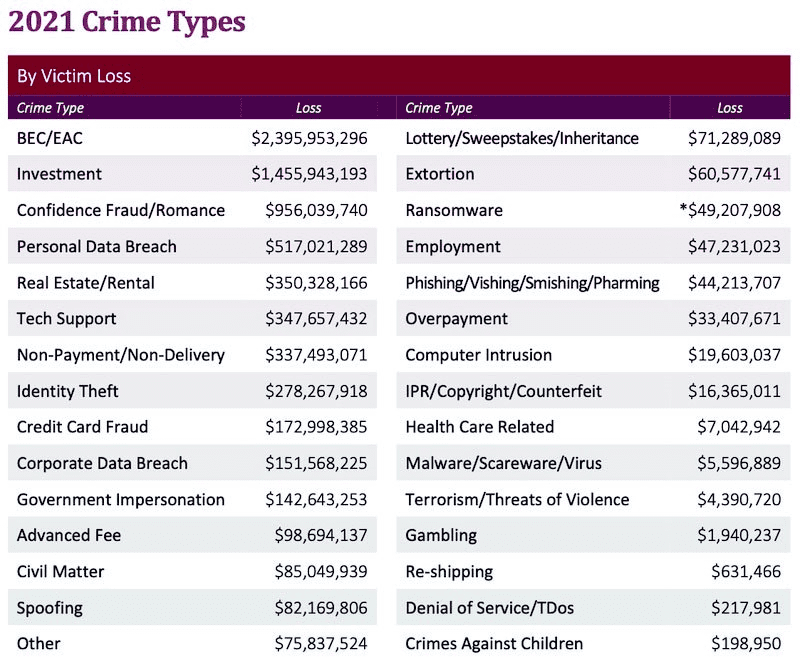

Source: FBI IC3


Get 10 tips to help you build a strong security culture & reduce your risk of cybersecurity trouble! GET INFOGRAPHIC>>
3 Paths to a Profitable Discussion About BEC & Phishing
These three pathways can open the door to conversations about phishing that bring home the danger to your clients.
Phishing is expensive for companies to handle even if it isn’t successful
Although it’s not exciting, phishing is the biggest cyber threat that businesses face today. It’s also the threat that employees encounter the most at work, with massive waves of phishing messages headed for businesses every day. An estimated 1 million phishing messages circulated in Q1 2022, setting a new record. That flood of phishing messages is a flood of danger, and every phishing message that makes its way to an employee’s inbox represents a threat to a company’s security. Unfortunately, employees are also notoriously bad at spotting complex phishing threats, creating a dangerous cycle that starts each time an employee receives a phishing message. But even with these problems, companies are still not taking the damage that phishing can do seriously.
Phishing is consistently growing more expensive for companies to maneuver through than it has been in previous years as attacks increase in severity and complexity. Businesses must take action now to prevent trouble. The financial impact of phishing attacks on large businesses is rapidly growing with no end in sight, quadrupling since 2015. The average cost of handling the results of phishing attack attempts and successes has skyrocketed, weighing in at an estimated $14.8 million per year for major U.S. Companies in 2021, compared with $3.8 million in 2015. That figure will only rise over time.
BEC & phishing-related breaches are hard to detect
IBM’s Cost of a Data Breach Report 2022 states that the average data breach takes 277 days to identify and contain, but the presence or absence of certain technologies and the attack vector can make a huge difference in that cost. Vectors with longer mean times to identify and contain, such as phishing or business email compromise, spawn the most expensive data breaches. Stolen or compromised credentials are the initial attack vector with the longest mean time to identify and contain a breach, 327 days. That time is 16.6% greater than the overall mean time to identify and contain a data breach.
If phishing or a phishing-related cyberattack is the vector for a data breach, it’s going to cost more than average. Breaches caused by business email compromise had the second highest mean time to identify and contain, at 308 days. Phishing can send the cost of a data breach soaring too. It is the costliest attack vector and it has the third highest mean time to identify and contain at 295 days.
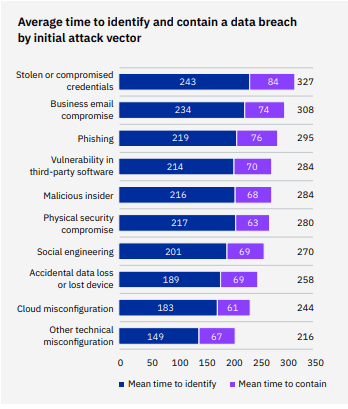

Source: IBM
Training reduces the chance of a phishing-related cyberattack disaster dramatically
One of the most effective weapons against phishing is regular security awareness training. This multi-benefit dynamo slashes the chance that employees will fall for a phishing lure dramatically. In fact, 80% of organizations in a study said that security awareness training reduced the chance that a staffer would fall for phishing substantially. Ultimately researchers determined that although security awareness training doesn’t work overnight, it makes steady progress that holds up over time reducing a company’s phishing risk from 60% to 10% within the first 12 months.
Beyond training with videos and quizzes (the most effective type of security awareness training), training employees to resist the temptations of phishing lures using phishing simulations is an effective tactic. In a report by Microsoft, analysts determined that when employees receive simulated phishing training, they’re 50% less likely to fall for phishing. People are more likely to learn and retain new knowledge by experience, and phishing simulations help employees hone their ability to spot red flags – and an estimated 90% of employees who receive more than five minutes of security awareness training every month are likely to know to divert suspicious messages to administrators or the IT team.


This MSP-focused guide gives you insight into finding the ideal dark web monitoring solution. GET THE GUIDE>>
Reduce Your Clients’ BEC & Phishing-Related Cyberattack Risk Fast
Reducing your clients’ risk of a cyberattack is an ongoing battle, but these solutions can help ensure that you’re using the best weapons to fight back against cybercrime and putting safeguards in place that are ready to handle the next generation of cyber threats.
Security awareness and compliance training plus phishing simulation
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size.
- An extensive library of security and compliance training videos in eight languages
- Plug-and-play or customizable phishing training campaign kits
- New videos arrive 4x per month and new phishing kits are added regularly
- Easy, automated training delivery through a personalized user portal
Dark web monitoring
Dark Web ID offers best-in-class dark web intelligence, reducing credential compromise risk.
- 24/7/365 monitoring using real-time, machine and analyst-validated data
- Fast alerts of compromises of business and personal credentials, including domains, IP addresses and email addresses
- Live dark web searches find compromised credentials in seconds
- Create clear and visually engaging risk reports
Automated, AI-powered antiphishing email security
Graphus AI-enabled, automated email security that catches 99.9% of sophisticated phishing threats and offers amazing benefits.
- Forget old-fashioned safe sender lists. Graphus analyzes the content of messages using more than 50 points of comparison to suss out fakes fast.
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- 3 layers of powerful protection at half the cost of competing solutions
- Don’t waste time on fussy configurations or adding threat reports. AI does that for you, getting everything up and running with just a few clicks and minimal maintenance.
Click here to watch a video demo of Graphus now.


Make sure your clients have all the bases covered with the Computer Security To-Do Checklist! GET IT>>


September 11-13: DattoCon REGISTER NOW>>
September 20: Dark Web ID: The Leading Dark Web Monitoring Program REGISTER NOW>
September 16: Cybersecurity Summitt in Charlotte REGISTER NOW>>
September 28-30: SpiceWorld 2022 REGISTER NOW>>
October 6-7: ASCII MSP Success Summit 2022 – Dallas REGISTER NOW>>
October 13: Cybersecurity Summit in Scottsdale REGISTER NOW>>
October 25-26: Southwest US Summit REGISTER NOW>>
November 2-3: ChannelPro SMB Forum 2022: Los Angeles REGISTER NOW>>
December 6: Connect IT Local – Atlanta REGISTER NOW>>
December 8: Connect IT Local – Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!