The Week in Breach News: 06/09/21 – 06/15/21

We’re celebrating Flag Day with an All-American Edition of the Week in Breach. This week, REvil takes aim at a US nuclear defense contractor, hackers take a bite out of McDonald’s and our new book Ransomware Exposed! tells you behind the scenes to show you the real story of this devastating cybercrime.

Give your clients the cold, hard facts that tell the tale of exactly how much danger their business is in. GET THIS FREE BOOK>>

Electronic Arts Inc (EA)
https://www.reuters.com/business/hackers-steal-wealth-data-ea-vice-2021-06-10/
Exploit: Hacking
Electronic Arts Inc: Game Developer

Risk to Business: 1.355= Extreme
Electronic Arts (EA) has announced that it is investigating a data breach. Cybercriminals stole valuable corporate data from the company including game source code and related tools. Early reports noted that hackers had stolen source codes for the popular title “FIFA 21” and source code and tools for the Frostbite engine. Researchers estimate that 780 gigabytes of data was snatched then advertised for sale on underground hacking forums.
Customers Impacted: Unknown
How It Could Affect Your Customers’ Business: Hackers are always interested in proprietary data and corporate secrets, the 3rd most popular category for theft. They’re easy money in the busy dark web data markets.
ID Agent to the Rescue: Are you ready for the next risk? Find useful data to inform security decisions including our predictions for the biggest risks of 2021 in The Global Year in Breach 2021. READ IT NOW>>
Edward Don
Exploit: Ransomware
Edward Don: Foodservice Distributor

Risk to Business: 1.816 = Severe
Foodservice equipment distributor Edward Don has been hit by a ransomware attack. The incident has disrupted their business operations, including their phone systems, network and email. As a result, employees have been driven to using personal Gmail accounts to communicate with customers regarding urgent orders or fulfillment issues. The incident is under investigation and full functionality was quickly restored,
Individual Impact: No sensitive personal or financial information has been declared compromised in this incident and the investigation is ongoing.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business Ransomware attacks against strategic targets like this are becoming all too common as ransomware gangs seek to cause maximum buzz for maximum profit.
ID Agent to the Rescue: NEW! Go behind the scenes of ransomware to see who gets attacked, who gets paid and what’s next on the hit list in Ransomware Exposed! DOWNLOAD NOW>>


See how ransomware really works, who gets paid & what’s next in our tell-all Ransomware Exposed! DOWNLOAD IT>>
McDonald’s Corp
https://www.reuters.com/technology/mcdonalds-hit-by-data-breach-south-korea-taiwan-wsj-2021-06-11/
Exploit: Ransomware
McDonald’s Corp: Fast Food Chain


Risk to Business: 2.606= Moderate
McDonald’s Corp. said hackers exposed US business information and some customer data in South Korea and Taiwan. The attackers accessed e-mails, phone numbers and delivery addresses. The company reported that it had hired external consultants to investigate unauthorized activity on an internal security system, prompted by a specific incident in which the unauthorized access was cut off a week after it was identified. The announcement noted that the burger chain does not believe any customer payment data was stolen but cautioned that there may be employee data exposed.
Individual Impact: There has not yet been confirmation that sensitive personal or financial information has been compromised in this incident but the investigation is ongoing.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business Cyberattacks that focus on obtaining corporate or business data are increasingly troubling because each one adds more sensitive data to the dark web that can be used against other businesses.
ID Agent to the Rescue: Increase the chance of speeding past pitfalls to victory when you boost cyber resilience for every customer using the tips in our eBook The Road to Cyber Resilience. DOWNLOAD IT NOW>
Intuit
Exploit: Account Takeover (ATO)
Intuit: Financial Software Developer









Risk to Business: 1.612= Severe
Accounting software giant Intuit has notified customers that they have suffered a breach. The company warned users of TurboTax that their personal and financial information was accessed by attackers following what looks like a series of account takeover attacks. Intuit announced that the threat actors used credentials (usernames and passwords) obtained from “a non-Intuit source” to gain access to the accounts.









Risk to Business: 1.832= Severe
Intuit notified potentially impacted clients by mail that information contained in a prior year’s tax return or current tax returns in progress including their name, Social Security number, address(es), date of birth, driver’s license number and financial information (e.g., salary and deductions) and information of other individuals contained in the tax return may have been exposed.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business Clients expect a high level of information security from companies that they trust with their personal and financial information, and may stop doing business with companies that fail to protect it.
ID Agent to the Rescue: Make sure you’re protecting the access points to your clients’ assets with strong security, including strong passwords with our Build Better Passwords eBook. GET IT>>


Don’t let cybercriminals steal your profits! Learn to spot and stop ransomware fast in Ransomware 101. GET IT>>
Sol Oriens
Exploit: Ransomware
Sol Oriens: Defense Contractor









Risk to Business: 2.337= Severe
REvil has struck again, this time against a tiny but important target in the defense sector. Sol Oriens, which consults for the US Department of Energy’s National Nuclear Safety Administration, is a 50-person firm based in Albuquerque, New Mexico. Researchers noted finding Sol Oriens documents posted on the dark web, told CNBC that they include invoices for NNSA contracts, descriptions of research and development projects managed by defense and energy contractors dated as recently as 2021
Individual Impact: No sensitive personal or financial information has been confirmed as compromised in this incident although some sources are reporting that human resources data is in the mix.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business This seemingly small attack could pack big consequences. Ransomware gangs have been increasingly focused on hitting strategic targets that service major clients.
ID Agent to the Rescue: Secure your data and systems against today’s nastiest threat with Ransomware 101, our most popular eBook, to guide you through how to secure your clients effectively. READ IT>>
Volkswagen Group of America
Exploit: Third- Party Data Breach
Volkswagen Group of America: Automotive Manufacturer









Risk to Business: 1.825 = Severe
Volkswagen US has announced that it has suffered a data breach impacting millions of US customers and prospective customers. the car company released information saying that a data breach at a vendor has exposed data on more than 3.3 million buyers and prospective buyers in North America. An unauthorized third party obtained limited personal information about customers and interested buyers from a vendor that its Audi Volkswagen brands and some U.S. and Canadian dealers used for digital sales and marketing.









Risk to Business: 2.213 = Severe
The information was gathered for sales and marketing between 2014 and 2019 and was in an electronic file the vendor left unsecured. According to Volkswagen, the majority of people impacted had phone numbers and email addresses exposed, but some clients had their driver’s license information stolen as well. In some cases, information about a vehicle purchased, leased, or inquired about was also obtained. VW said 90,000 Audi customers and prospective buyers also had sensitive data impacted relating to purchase or lease eligibility. VW said it will offer free credit protection services to those individuals.
Customers Impacted: 3.3 million
How it Could Affect Your Customers’ Business: Attacks on data processors and other essential service providers have escalated as cybercriminals look for big data scores and information that facilitates more cybercrimes.
ID Agent to the Rescue: Third-party and supply chain risk growing exponentially. Learn strategies to fight back in our eBook Breaking Up with Third-Party and Supply Chain Risk! DOWNLOAD IT>>


Third party and supply chain risk are a menace to every business. Learn how to detect and mitigate it fast. GET THIS BOOK >>
New York City Law Department
https://www.nytimes.com/2021/06/07/nyregion/cyberattack-law-department-nyc.html
Exploit: Ransomware
New York City Law Department: Municipal Government Agency









Risk to Business: 1.633 = Severe
The New York City Law Department experienced a cyberattack that impacted its computer systems, forcing it to shut down its technology. The network also had to be disconnected from other city systems for safety. Systems are being restored slowly and the FBI is investigating along with New York police.
Individual Impact: No sensitive personal or financial information has been confirmed as compromised in this incident.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Attacks that strike at government and infrastructure targets frequently use ransomware to get the job done, and no matter how big or small, no organization is safe.
ID Agent to the Rescue: Are your clients maintaining strong security? The Security Awareness Champion’s Guide shows you how to close vulnerabilities fast! GET IT>>
Carter’s
https://threatpost.com/baby-clothes-carters-leaks-customer-records/166866/
Carter’s: Children’s Clothier
Exploit: Third Party Data Breach









Risk to Business: 2.331 = Severe
In a new disclosure, baby clothing giant Carter’s admitted that it had suffered a data breach through a third-party data processor, exposing the personal data of hundreds of thousands of its customers over a multiyear period. The service provider, Linc, handled automation for online purposes. The Linc system was used to send customers shortened URLs containing everything from purchase details to tracking information without basic security protections.
Individual Impact: At this time, no sensitive personal or financial information was announced as compromised in this incident, but the investigation is ongoing.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Every business has relationships with other businesses, and every relationship they have creates risk. Protecting companies from supply chain risk is imperative.
ID Agent to the Rescue: Are all of your clients protected from this kind of risk? Use our Cybersecurity Risk Protection Checklist to make sure you’ve dotted the “I”s and crossed the “T”s. DOWNLOAD IT>>


Don’t let cyberattacks wreck your 2022! Start your journey on The Road to Cyber Resilience now! DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a wide range of factors related to the assessed breach.


Go Inside the Ink to Get the Inside Scoop on Cybercrime
Are you up to date on the latest news that can impact your business and your customers? Here’s a recap:
- RockYou2021 Password Leak Supercharges Dark Web Danger
- 10 More Ransomware Facts That You Need to Know
- Why Single Sign-On is the Unsung Hero of Security
- Are You Safe from Malicious Insider Threats by Remote Workers?
- Phishing with Government Bait Hooks Unwary Employees
- The Week in Breach: 05/19/21 – 05/25/21


Explore the dark web with experts & get a deck of screenshots in Unveiling Cybercrime Markets on the Dark Web. WATCH NOW>>


NEW THIS WEEK: AN ESSENTIAL EBOOK!
NOW PLAYING: Ransomware Exposed Tells You All of Ransomware’s Dirty Secrets!
Ransomware is a devastating weapon whether it’s wielded by nation-state cybercriminals or freelance hackers. In our new eBook Ransomware Exposed!, we’ll take you behind the scenes to learn the real story of today’s nastiest cybersecurity threat. You’ll learn:
- Who gets paid in a ransomware operation (and how much)
- New, hot threat varieties that are coming soon to an inbox near you
- How to secure systems and data for less
We did all the research you’ll need to start profitable conversations about ransomware risks and included a wealth of current data and statistics about just how dangerous and damaging this threat can be and how to defend against it. An estimated 60% of companies go out of business after a cyberattack – don’t let any of your clients join that club!
See the latest statistics on ransomware attacks and find out what’s next in ransomware risk. DOWNLOAD RANSOMWARE EXPOSED! NOW>>


Help your clients stay off of cybercriminal hooks with the expert tips and strategies that we share to combat phishing in our webinar The Phish Files. LISTEN NOW>>


BEC Attacks Are Rising & They’re Costing Businesses a Fortune
A great deal of time and attention is given to splashy ransomware attacks and audacious hacking incidents. While those reports are exciting and full of interesting details, they’re not the whole story of cybercrime and related business loss. There’s another threat flying under the radar that the Federal Bureau of Investigation (FBI) has declared responsible for 64 times as many losses as ransomware: business email compromise. This old cybercriminal trick has gained new life in the email-dependent remote work business world through a lethal combination of social engineering, phishing and fraud – and it’s been wreaking havoc with impunity on businesses around the world.
In the most recent Internet Crimes Complaint Center (IC3) Report, the FBI goes a little bit deeper inside the dangerous landscape of business email compromise. The multi-year champion didn’t disappoint in its 2020 performance, with a big rise in both prevalence and cost. The 2020 report notes that BEC schemes continued their reign at the top of the IC3 list of the costliest cybercrime. In a banner year for all cybercrime, BEC had an impressive surge. IC3 recorded 19,369 complaints about BEC scams with an adjusted loss of approximately $1.8 billion. If spoofing, a subset of BEC, is added to the mix, the total loss for businesses hit by BEC in 2020 creeps closer to $2.1 billion.

Its A Growing Revenue Stream for Cybercriminals
How big is the BEC business? It’s the biggest profit center for cybercriminals noted in the 2020 IC3 Report, which also noted an increase of more than 300,000 BEC scam complaints from 2019. The rising tide of BEC complaints spurred the FBI into adding assets that are devoted to dealing with BEC complaints. Since 2018, the FBI has been running a Recovery Asset Team that specializes in tracking down BEC money and freezing accounts used for unauthorized transfers. IC3 works closely with victims, other law enforcement officials and financial institutions to recover funds while they can still be tracked. The costs to businesses in stolen money, investigation and remediation are also on the rise. In 2020, BEC costs increased rapidly, from $54,000 in Q1 2020 to $80,183 in Q2.
The COVID-19 pandemic was a huge boon to cybercriminals in every cybercrime segment. An estimated 80% of firms experienced an increase in cyberattacks in 2020. The pandemic and was an especially fortunate gift for practitioners of BEC. The rapid shift to remote work combined with an increase in email usage and millions of targets that are shaken by all of the pandemic chaos created a ripe atmosphere for credential theft and BEC. Investigators at IC3 were busy too, handling thousands of complaints regarding COVID-19 themed phishing attacks that belied BEC operations. In those schemes, cybercriminals targeted pandemic-stressed businesses with spoofed emails about the Coronavirus Aid, Relief, and Economic Security Act (CARES) stimulus funds, unemployment insurance, Payment Protection Program (PPP) loans and Small Business Economic Injury Disaster Loans in order to perpetrate BEC attacks.
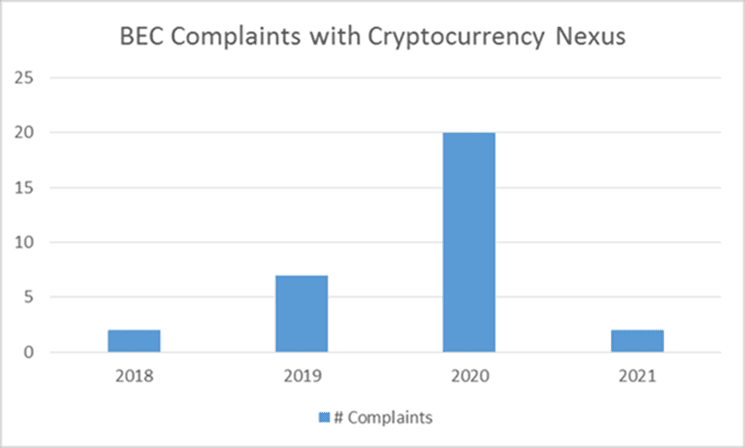

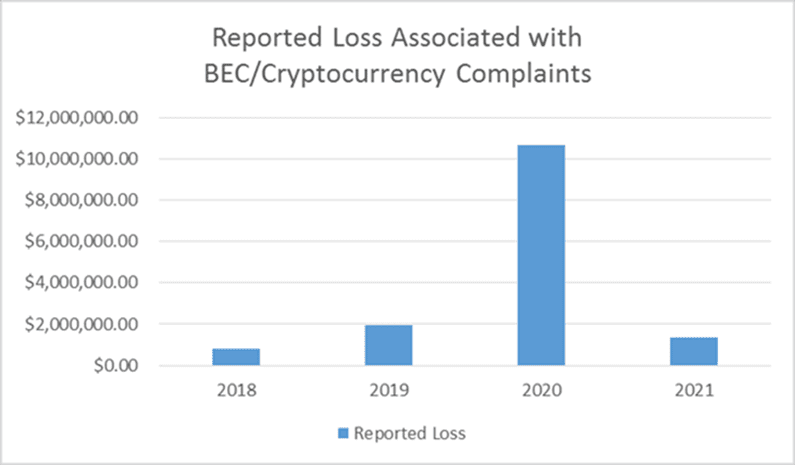
The Bad Guys Make Bold Moves Into New Territory
Cybercriminals have grown bolder in the sums that they ask their victims to transfer too. In Q4 2020, the average amount requested in wire transfer-based BEC attacks nearly doubled to $75,000 in the fourth quarter. Increasingly, those funds are being moved around in cryptocurrency. Cybercriminals have flocked to cryptocurrency because it’s hard to pin down, making it less likely to be seized in a criminal investigation. Cryptocurrency can also be moved around and laundered more easily. In a March 2021 bulletin, IC3 warned that it had received an increased number of BEC complaints involving the use of cryptocurrency. Losses to BEC cryptocurrency scams have been staggering. In 2020, businesses lost more than $10 million in crypto-related BEC scams.
How are cybercriminals still scamming people with BEC? By executing complex, sophisticated schemes that involve a great deal of obfuscation and run like a well-oiled machine. In their 2020 report, the IC3 detailed some of the ways that successful BEC operations scored and laundered their money using cryptocurrency. One scenario followed this script: an initial victim would be scammed in a non-BEC fraud, like a romance scam. The goal of that operation would be for a victim to provide a form of ID to a bad actor, ideally accompanied by credentials or passwords for financial accounts. The bad actor could then use that stolen identifying information to establish a bank account to receive illicitly acquired BEC/EAC funds. After the proceeds of the other BEC scams that the crooks were running were deposited in that bogus account, those funds would then be transferred to a cryptocurrency account and quickly dispersed, making it challenging (or impossible) for law enforcement to find and seize the victim’s stolen money.

Risk Keeps Rising
Business email compromise risk is high and will keep growing. As reported in the Graphus State of Email Security report, this type of flexible and devastating attack rose 14% in 2020, with a whopping 65% of organizations facing down a BEC threat. A flood of information about businesses gleaned in data breaches reached the dark web last year, providing details that enable cybercriminals to mount convincing future attacks that range from BEC scenarios to ransomware. That’s a risk no business can take. An estimated 60% of companies that are hit with a cyberattack go out of business. Profit will also keep driving this category forward in the future, and your clients need to be ready.
Reducing BEC risk starts with reducing phishing risk. BullPhish ID is the perfect choice to increase phishing resistance in employees at any level. Security awareness training reduces a company’s chance of suffering a damaging cyberattack by up to 70%. It’s a strong long and short-term solution for businesses to keep systems and data secure, with constant benefits for every company’s cyber resilience.


Would you trust a flimsy old lock for your front door? Why trust one on your data? Learn to Build Better Passwords. GET IT>>
BullPhish ID is the streamlined, user-friendly solution to every training challenge, including:
- Offer plenty of up-to-date lessons covering all of the latest threats and concerns including data handling, compliance, phishing and more!
- Give clients a top-notch customer experience with customized portals that make their training experience (and yours) smooth and painless.
- Use our frequently updated library of plug-and-play phishing simulation kits in 8 languages that can be scheduled to run automatically.
- Lots of options for customization, with video, attachments, content, online tests and more ready for you to adjust as needed to reflect your clients’ real threats.
- The simple, clear reporting enables you to quickly demonstrate employee progress and measure the value of training for clients.
We’re here to help if you would like to learn more about ways that you can protect your business and your clients from today’s nastiest cybersecurity nightmares. Let’s get together and talk about it: SCHEDULE A CONSULTATION>>


June 22: See Something Wrong? Do Something Right! REGISTER NOW>>
Jun 22: MSP Gym (North America Edition) REGISTER NOW>>
Jun 24: Phish & Chips: Demo our products and get dinner on us! REGISTER NOW >>
Jun 29: Hacker Hotbeds and Malicious Marketplaces REGISTER NOW>>




Learn the strats to beat today’s nastiest cybersecurity mobs in the Security Awareness Champion’s Guide. GET IT>>


Are You Ready For the Attack That Caused 2020’s Biggest Business Losses?
Stories about hacking and ransomware are making headlines all over the media, with splashy coverage of big consequences and big price tags. But as problematic as ransomware is, that’s not the cyberattack that the FBI said caused the most business losses in 2020. That’s an under-the-radar menace that you may not be expecting: business email compromise (BEC).
BEC caused a staggering 64 times as many losses as ransomware in 2021, and it’s not far off the pace to send that number even higher in 2021. These aren’t your father’s BEC scams either. Today BEC scams are elaborate with sophisticated messages and carefully crafted lures that can be tricky to spot. Plus, cybercriminals are increasingly using cryptocurrency as their payment of choice, making it harder for officials to track and seize their ill-gotten gains. In 2020, businesses lost more than $10 million in crypto-related BEC scams.
One thing hasn’t changed about BEC though. It’s still primarily targeting your business using phishing. Sometimes called Executive Account Compromise, BEC practitioners are adept at tricking employees into thinking that their believable messages actually come from company executives, service providers or suppliers in order to get them to transfer money fast. An estimated 65% of organizations faced BEC threats in 2020 and that’s not slowing down. You need to be ready for BEC threat actors to knock on your door.
Conquer BEC by combatting it directly at the source through phishing resistance training. By increasing your employees’ awareness of BEC threats with a dynamic, customizable training solution like BullPhish ID, you’ll build a stronger defense against some of today’s most devastating and expensive cybersecurity threats.
ID Agent Partners: Feel free to re-use this blog post (in part or in its entirety) for your own social media and marketing efforts. Please send an email to [email protected] to let us know – we love to hear about how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!


We’d love to hear your story of security success with ID Agent. Contact our marketing/pr team to set up a meeting with our staff to tell the world about your experiences in our next case study! To learn more about how the ID Agent Digital Risk Protection Platform can secure your prosperity, book a personalized demo today.