The Week in Breach News: 03/01/23 – 03/07/23

This week: Cybercriminals snatch sensitive data from the U.S. Marshals Service, employee mistakes cause big problems for two companies & the unexpected benefits of incident response planning.

Give your clients 7 lucky tips to secure their data & remind them that they can’t rely on luck to stay safe! GET THE INFOGRAPHIC>>

U.S. Marshals Service
https://www.cbsnews.com/news/us-marshals-office-cyber-attack-compromised-sensitive-data/
Exploit: Ransomware
U.S. Marshals Service: Federal Agency

Risk to Business: 1.402 = Extreme
The U.S. Marshals Service announced that it is investigating a ransomware attack on its system. The attack has compromised some of its most sensitive information, including law enforcement materials, and the personal information of employees and potential targets of federal investigations. In the February 17 incident, cybercriminals were able to obtain access to sensitive administrative data including personal information of certain employees, and data about wanted fugitives, as well as information on unidentified third parties. The affected system also contained sensitive law enforcement information like ongoing legal procedures.
How It Could Affect Your Customers’ Business: Highly sensitive data like this can do a lot of damage in the wrong hands
ID Agent to the Rescue: Learn more about how our Security Suite can help MSPs protect their clients from expensive and damaging cyberattacks and other information security trouble. GET IT>>
Pipefitters Local 537
https://www.securityweek.com/cyberattack-on-boston-union-results-in-6-4m-loss/
Exploit: Business Email Compromise
Pipefitters Local 537: Trade Union

Risk to Business: 1.702 = Severe
Pipefitters Local 537 in Boston is investigating a cyberattack that resulted in a loss of $6.4 million. Officials called the incident a social engineering attack, saying that their internal systems were not compromised or hacked. The evidence so far points to a business email compromise attack. The union was quick to assure members that it does not appear that the personal information of members was stolen or compromised and that this attack will have no impact on the members’ health fund. The incident is under investigation by private and federal investigators.
How It Could Affect Your Customers’ Business: Business email compromise is a dangerous and damaging nightmare that can strike any organization even charities and professional groups.
ID Agent to the Rescue: Learn how to reduce risk and prevent damage from devastating BEC attacks in our Comprehensive Guide to Business Email Compromise. DOWNLOAD IT>>
Animker.com
https://www.hackread.com/video-marketing-software-animker-data-leak/
Exploit: Misconfiguration
Animaker: Video Marketing Software Maker







Risk to Business: 1.808 = Severe
A misconfigured database owned by Animaker.com has exposed test and personal data belonging to over 700,000 people who are users of the websites getshow.io (an all-in-one video marketing platform) and animaker.com (a DIY video animation software). The database contains 5.3 GB of data, and new data is still being added daily. Exposed data includes full names, device type, postal codes, IP addresses, mobile numbers, email addresses, Animaker profile details and user country/city/state/location. The company doesn’t think that user passwords were exposed.
How It Could Affect Your Customers’ Business: Employee mistakes like misconfiguring a database are gateways to expensive problems like this.
ID Agent to the Rescue: Learn how security awareness training can help businesses combat security risks from phishing to employee mistakes in an infographic. LEARN MORE>>
Chick-fil-A
Exploit: Hacking
Chick-fil-A: Fast Food Restaurant Chain







Risk to Business: 2.779 = Moderate
Fast food giant Chick-fil-A has confirmed that over 71,000 customers’ accounts were breached in a months-long credential stuffing attack. In this attack, threat actors were able to use customers’ stored rewards balances and access those customers’ personal information. In a security notice submitted to multiple Attorney General offices, the company specified that they suffered a credential stuffing attack between December 18, 2022, and February 12, 2023. This sustained attack allowed the threat actors to hack a total of 71,473 Chick-fil-A accounts. The cybercriminals had access to customers’ personal information including their name, email address, Chick-fil-A One membership number and mobile pay number, QR code, masked credit/debit card number and the amount of Chick-fil-A credit (e.g., e-gift card balance) on your account (if any).
How It Could Affect Your Customers’ Business: The incidence of credential stuffing attacks has been growing in the past two years.
ID Agent to the Rescue: Managed SOC helps overtaxed security teams detect and address security issues without spending on additional equipment or expanding the payroll. LEARN MORE>>
Denver Public Schools (DPS)
Exploit: Hacking
Denver Public Schools (DPS): Regional Education Authority







Risk to Business: 1.783 = Severe
Denver Public Schools (DPS has disclosed that the personal information of an estimated 15,000 system employees was recently exposed in a hacking incident. The district said that between Dec. 13, 2022, and Jan. 13, 2023, a hacker accessed, and potentially downloaded employee-related files stored on the district’s computer servers. Data stolen in this incident includes the names and Social Security numbers of current and former participants in the DPS employee health plan, employee fingerprints, bank account numbers or pay card numbers, driver’s license numbers, passport numbers and health plan enrollment information. No student information was involved.
How it Could Affect Your Customers’ Business: School systems have been under fire from cybercrime gangs hoping for a quick payout.
ID Agent to the Rescue: The Cybersecurity Risk Protection Checklist helps businesses make sure that they’re covering all of their security bases. GET CHECKLIST>>
Southeastern Louisiana University
Exploit: Hacking
Southeastern Louisiana University: Institution of Higher Learning







Risk to Business: 1.709 = Severe
Southeastern Louisiana University is experiencing a cyberattack that has left students and staff unable to access systems for at least five days. The university was left without a functional website, email system or system for submitting assignments after being forced to shut its network down as a response to an unnamed cyberattack. Students and faculty have been struggling with getting though daily business like completing coursework and conducting remote classes since late last week. Systems are slowly being restored.
How it Could Affect Your Customers’ Business: The time-sensitive nature of online learning has made colleges bigger targets for cyberattacks.
ID Agent to the Rescue: See the biggest SMB security challenges and attitudes toward security, training and more in the Kaseya Security Insights Report. DOWNLOAD IT>>



This infographic helps IT professionals get the most out of a security awareness training solution. DOWNLOAD IT>>


United Kingdom – WH Smith
Exploit: Hacking
WH Smith: Retailer


Risk to Business: 2.701 = Moderate
Leading convenience store and newsstand chain WH Smith has disclosed that they have experienced a data breach. In this incident, bad actors gained illegal access to some company data, including current and former employee data. The company reassured the public that there was no business interruption expected and that customer data was not affected because it is stored on separate systems. No further information was given about the incident, which remains under investigation.
How it Could Affect Your Customers’ Business: This incident could have been much worse like the one that shut down Canadian retailer Indigo a few weeks ago.
ID Agent to the Rescue: Develop an effective, efficient incident response plan with the tips in our guide How to Build an Incident Response Plan. GET YOUR GUIDE>>
Austria – Falkensteiner
Exploit: Misconfiguration
Falkensteiner: Hotelier







Risk to Business: 2.397 = Severe
An unprotected server has been uncovered that is storing the personal information of a significant number of customers of the European hotel chain Falkensteiner. Researchers discovered more than 102,000 records in the exposed database. Some records were repeats, but they ultimately determined that unique records for 22,000 people were involved. The exposed data includes full names, phone numbers, email addresses and booking details. The company says that it is investigating the incident.
How it Could Affect Your Customers’ Business: An employee mistake like this will cost this company big bucks after regulators get finished with their assessment.
ID Agent to the Rescue: Show the dollars and cents value of security awareness training with the data you’ll find in our eBook The Business Case for Security Awareness Training. DOWNLOAD IT>>


See how security awareness training stops the biggest security threats! GET INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


See how Managed SOC gives businesses an essential edge against cyberattacks. DOWNLOAD INFO SHEET>>


See how today’s biggest threats may impact businesses in our security blogs.
- 7 Security Solutions That Make Incident Response Faster & Easier
- GPT-3 Makes Phishing Scams Like These Worse
- Why Should Businesses Choose a Managed SOC?
- A Guide to Phishing Incident Response
- The Week in Breach News: 02/22/23 – 02/28/23


Don’t miss the industry’s best event, Connect IT Global April 24 – 27, 2023, in Las Vegas! REGISTER NOW>>


2 New Powered Services Pro Campaigns are Here to Kick Off Your Spring Marketing
Powered Services Pro has two fresh marketing campaigns available for MSPs. Let us help you hit one of today’s hottest security topics and undertake a great outreach effort to your clients’ internal IT departments.
Campaign 1: Defense in Depth (DiD) – Security Campaign
Defense in Depth (DiD) – Strengthen Your Security Posture with the 7-Layer Cake of Cybersecurity
End Buyer Value Proposition:
As threat actors and their toolsets grow more sophisticated, organizations need more layers of defense. What’s more, those solutions need to tightly snap together to form a unified front against threats. Discover the 7-layer cake of security that can help your organization strengthen its security posture and avoid costly downtime.
Campaign 2: Better Together: Co-Managed IT Services Campaign
MSP Value Proposition:
Internal IT departments are stretched beyond what’s reasonable. Simply keeping up with routine activities can be overwhelming. Partnering with an IT service provider can help businesses ensure all their bases are covered, without existing team members needing to overextend themselves.
End Buyer Value Proposition:
Cyberthreats are real and growing, with no signs of slowing down anytime soon. How is your business going to face these threats? How can you ensure your business is protected—all while managing the technology that keeps it running and thriving? Let the experts help! Maybe it’s time to consider outsourcing some—or all—of your technology to an IT service provider.
Learn more about using Powered Services Pro campaigns



This infographic helps IT professionals get the most out of a security awareness training solution. DOWNLOAD IT>>


!NEW INFOGRAPHIC! 5 Ways the Dark Web Endangers Businesses
The booming dark web economy is great for cybercriminals but bad news for businesses. Learn more about the biggest threats that businesses face today from dark web sources in our new infographic 5 Ways the Dark Web Endangers Businesses.
Here’s a sneak peek at one of the threats:
INITIAL ACCESS BROKERS (IAB) These cybercriminals provide access to secure networks for a fee. Sometimes, IABs are hackers that have cracked those secure networks themselves, but they can also be traders in credentials that have been stolen or sold to them by a malicious insider. Today, there are more than 300 IABs operating on the dark web
See four more threats when you download our infographic! DOWNLOAD THE INFOGRAPHIC>>
Did you miss… our infographic 5 Tips for Incident Response? DOWNLOAD IT>>


Go inside BEC scams & get tips to keep businesses safe from today’s most expensive cyberattack. DOWNLOAD EBOOK>>




Incident Response Planning Brings Businesses Other Benefits
An incident response plan is a must-have for any business in today’s volatile cybercrime landscape. Planning for trouble helps businesses resolve incidents and get back to work faster. Yet 1 in 3 businesses is flirting with disaster by not having an incident response plan. Incident response planning helps companies uncover possible problems or weaknesses before the bad guys do, giving businesses an edge against cybercrime. However, making a plan can be a daunting prospect. But making use of some available free resources can make the planning process something any IT professional can handle.
Excerpted in part from our new eBook How to Build an Incident Response Plan. DOWNLOAD IT NOW>>


Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>
Incident response planning brings unexpected benefits
According to CompTIA only 45% of all companies in the United States have incident detection and response practices in place. That’s not good. Every organization – businesses, non-profits, medical offices, schools, professional groups, etc. – needs to be ready to face a cybersecurity or information security problem. These days, it’s not a matter of “if” a business will be impacted by a cyberattack, it’s “when”. Even if a company’s security is never breached, it can still be affected by a security problem or cyberattack at one of its suppliers or partners. In 2022, supply chain attacks surpassed the number of malware-based attacks by almost 40%. Incident response planning also brings some unexpected benefits.
Readiness – Making an incident response plan increases a company’s readiness for a problem. Plus, if there’s a plan in place that everyone knows about, there’s less of a chance that people will panic and make mistakes when an incident occurs. Unfortunately, as a recent study by insurer Hickox Ltd. discovered, readiness to face a cyberattack is decreasing, not increasing for businesses.
Resilience – Companies that are ready for trouble have considered all of the ways that trouble could come calling, including finding security gaps and closing them. IBM researchers announced that 39% of organizations with a formal, tested incident response plan experienced an incident, compared to 62% of those who didn’t have a plan.
Savings – Regularly reviewing security tools and possible cyberattack scenarios when creating an incident response plan can be beneficial for budgeting. Experts estimate that many enterprises maintain 19 different security tools, with only 22% of such tools serving as vital to primary security objectives. Almost half of the security tools that are available to IT teams are just clutter, with only about 47% of companies’ existing IT security tools actually used daily.


Learn 5 red flags that could indicate a malicious insider is at work in your organization! DOWNLOAD INFOGRAPHIC>>
Making a plan isn’t as hard as it seems
Making an incident response plan sounds daunting, but there’s help available that makes it easier. The U.S. National Institute of Standards and Technology (NIST) has outlined out a series of steps for cybersecurity incident response that are generally considered to be the industry standard. The NIST incident response lifecycle includes four main stages: Preparation, Detection and Analysis, Containment, Eradication and Recovery and Post-Event Activity.
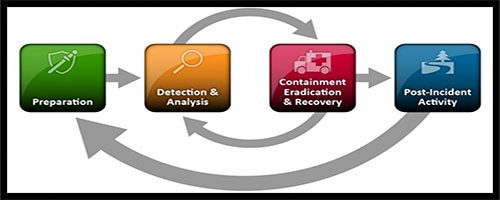

Source: NIST


Learn more about how the Kaseya Security Suite helps MSPs & their customers thrive in a dangerous world. GET BRIEF>>
Exploring the four stages of an incident response
The National Institute of Standards and Technology (NIST) has set clear standards and practices for incident response and cybersecurity to help organizations stay prepared for an adverse event. These standards are categorized in four of the below-mentioned stages.
Preparation
The preparation stage is the fundamental phase where incident response teams set strategies to help the organization stay prepared for an incident. This phase includes establishing and training an incident response team and acquiring the necessary tools and resources to prevent an incident from causing severe damages.
The preparation stage also emphasizes establishing mechanisms to limit the number of future incidents by selecting and implementing a set of controls. There are three key precautionary measures for securing networks, systems and applications.
Risk assessments: A periodic risk assessment of systems and applications can help organizations identify existing threats and vulnerabilities before cybercriminals exploit them. It also helps organizations identify critical resources, enabling their workforce to emphasize monitoring and response activities for those resources.
Malware detection: Every organization should have software deployed throughout their organization to detect and mitigate malware. For effective detection and prevention, malware protection solutions should monitor operating systems, endpoints, email servers and web proxies at a minimum.
User awareness and training: Having an incident response plan serves no purpose without educating every user about the policies and procedures regarding appropriate use of networks, systems and applications. With effective user awareness training, organizations can drastically minimize the number of security incidents.


Are you ready to slay the Monsters of Cybersecurity? This checklist tells you what you’ll need to succeed! GET CHECKLIST>>
Detection and analysis
While the preparation stage helps organizations limit the number of cyberattacks, some attacks still sneak past even the most stringent cyber defenses. The detection and analysis phase helps organizations identify the source of the incident, gauge the severity of the incident and alert the concerned authorities to curb its impact.
According to the NIST, detecting and assessing incidents is one of the most challenging parts of incident response for organizations. This is because incidents can happen in a plethora of ways, and each incident merits a different response strategy. However, profiling networks and systems, studying normal behaviors, creating a log retention policy and maintaining a knowledge base of information can help make incident analysis easier and more effective.
Rapid detection and analysis is key after an incident has occurred. The team should rapidly perform an initial analysis to get a detailed insight into the incident’s scope, such as knowledge about the affected networks, systems or applications, information about the cause and origin of the incident, and details about the perpetrators, the tools they use and their attack methods. An accurate initial analysis goes a long way in helping organizations in the containment stage.


Be the hero that defeats a company’s security threats to declare victory over cybercriminals! GET THE GUIDE>>
Containment, eradication and recovery
Containment is a significant step to limit the damage of a cyberattack. Organizations should create different containment strategies for each incident type, with criteria documented clearly to facilitate decision-making. For example, a phishing attack requires a different approach than a network-based DDoS attack.
Once the incident has been contained, you can work on eliminating components of the incident, such as removing malware and disabling breached user accounts, and identifying and mitigating all exploited vulnerabilities. Identifying all affected systems within the organization and disabling them to prevent future damage is essential.
In recovery, the incident response team works toward restoring normal operations. The team confirms that all the systems are functioning normally and remediates any existing vulnerabilities to prevent similar incidents. The recovery stage includes actions, such as restoring systems from backups, rebuilding systems, replacing affected files with clean versions, installing software patches, changing compromised passwords and tightening network perimeter security with additional measures.


Find the right dark web monitoring solution for your customers & your MSP with this checklist! DOWNLOAD IT>>
Post-incident activity
Learning and improving after each incident is vital for incident response teams. After handling the incident, the organization should draft a detailed report about the cause and cost of the incident and steps to take to prevent future incidents.
Organizations should have subjective and objective data regarding each incident to limit the chances of the incident happening again and to identify ways of improving future incident response activity. The incident response team should collaborate regularly to learn about and fix any gaps in their cyber defense. An effective post-incident activity report must:
- Document the exact reason and time of the incident.
- Evaluate how well the staff and management dealt with the incident.
- Identify if proper procedures were followed by the staff.
- Indicate what information, if provided sooner, would have resulted in a better incident response.
- Note corrective steps to be taken to prevent similar incidents in the future.
- Cite what the staff and management should do differently if a similar incident occurs in the future.
- List additional tools or resources needed to detect, analyze and mitigate future incidents.


Get tips & advice to help you build a smart incident response plan in our guide. GET YOUR GUIDE>>
Managed SOC helps you find and fix security problems fast
Kaseya’s Managed SOC puts the power of years of expertise at your fingertips without breaking the bank. Stop advanced threats with Kaseya’s Managed SOC — a world-class MDR solution that offers an innovative, affordable and effective way to power up your security. By partnering with us, you can gain access to an elite team of cybersecurity veterans that will help you hunt for threats and triage them. They will be available 24/7/365 to dive in immediately and work with your team when actionable threats are discovered.
Kaseya’s Managed SOC includes:
- Continuous monitoring: Round-the-clock protection with real-time advanced threat detection.
- Expertise on-demand: Get the cybersecurity expertise you need to keep your organization out of trouble without adding to your headcount.
- Breach detection: Thwart sophisticated and advanced threats that bypass traditional AV and perimeter security solutions.
- Threat hunting: Focus on other pressing matters while an elite cybersecurity team proactively hunts for malicious activities.
- No hardware requirements: Patent-pending, cloud-based technology eliminates the need for costly and complex on-premises hardware.


Kaseya’s Security Suite makes keeping businesses out of cybersecurity trouble easy & affordable. SEE HOW>>


March 2: Kaseya + Datto Connect Local New Jersey REGISTER NOW>>
March 7 – 8: Kaseya + Datto Connect Local Pittsburgh REGISTER NOW>>
March 8: Security Suite Product Demo Webinar REGISTER NOW>>
March 9: Kaseya + Datto Connect Local Philadelphia REGISTER NOW>>
March 14: Kaseya + Datto Connect Local Chicago REGISTER NOW>>
March 16: Kaseya + Datto Connect Local Dallas REGISTER NOW>>
March 16: Kaseya + Datto Connect Local London REGISTER NOW>>
March 21: Kaseya + Datto Connect Local Washington D.C. REGISTER NOW>>
March 23: Kaseya + Datto Connect Local Netherlands REGISTER NOW>>
March 23: Kaseya + Datto Connect Local Denver REGISTER NOW>>
March 30: Kaseya + Datto Connect Local Boston REGISTER NOW>>
April 24 – 27: Connect IT Global in Las Vegas REGISTER NOW>>
June 26-28: DattoCon Europe REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!