The Week in Breach News: 09/21/22 – 09/27/22

Explore the massive Optus telecom breach in Australia, two nasty airline cyberattacks, new BullPhish ID courses, new product sheets and five reasons why security automation and AI is a smart investment.

Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>


The City of Wheat Ridge, CO
https://www.denverpost.com/2022/09/22/wheat-ridge-ransomware-fremont-county-cyber-attack/
Exploit: Ransomware
The City of Wheat Ridge, CO: Municipal Government





Risk to Business: 2.175 = Severe
A Colorado city is putting its IT systems back in order after a successful cyberattack by the BlackCat group. Local media report that following the attack, Wheat Ridge had to shut down its phones and email servers to assess the damage the cybercriminals had done to its network. That, in turn, prompted the city to close down City Hall to the public for more than a week. The cybercriminals demanded $5 million in Monero as the ransom, but the city declined to pay, opting to restore from backups. The city government has been able to return to normal business, and the attack is under investigation by the U.S. Federal Bureau of Investigation.
How It Could Affect Your Customers’ Business: Ransomware attacks against governments and municipalities have been proliferating.
ID Agent to the Rescue: See the biggest risks that businesses in different sectors face today and get a look at what your clients will be facing tomorrow in The Global Year in Breach 2022. DOWNLOAD IT>>
Rockstar Games
https://www.hackread.com/uber-hacker-rockstar-games-hacked-gta-6-data/
Exploit: Hacking
Rockstar Games: Video Game Developer





Risk to Business: 2.136 = Severe
Rockstar Games confirmed on Monday that a hacker broke into its systems and stole confidential internal data, including footage and source code from the previously unannounced next installment of its popular Grand Theft Auto series. The New York-based company appears to have been breached through a stolen employee Slack account. The hacker that claimed responsibility, “teapotuberhacker”, also says that they’re behind a murky hacking incident at Uber last week. The cybercriminal shared a link to footage and clips purportedly from Grand Theft Auto 6 on a Grand Theft Auto fan forum. The company has confirmed that the game is in development and that the attack occurred.
How It Could Affect Your Customers’ Business: This is a mess for Rockstar Games with a potentially nasty impact on the marketing and sales of a major new release that wasn’t ready for prime time yet.
ID Agent to the Rescue: Curious to see if you’re offering your clients the right dark web monitoring solution? Explore your options with The Dark Web Monitoring Buyer’s Guide for MSPs. DOWNLOAD IT>>
New York Racing Association
Exploit: Ransomware
New York Racing Association: Professional Group





Risk to Business: 2.703 = Moderate
The Hive ransomware operation has claimed responsibility for an attack on the New York Racing Association (NYRA). The NYRA operates the three major thoroughbred horse racing tracks in New York, the Aqueduct Racetrack, the Belmont Park (home of the Triple Crown event the Belmont Stakes) and the historic Saratoga Race Course. The attack took place in late August 2022 and breach notices were filed with authorities last week. Press reports say that the hackers have also published a link to freely download a ZIP archive containing all of the files they allegedly stole from NYRA’s systems.





Risk to Individual: 2.624 = Major
Member data that may have been exposed includes Social Security numbers (SSNs), driver’s license identification numbers, health records and health insurance information.
How It Could Affect Your Customers’ Business: The involvement of health data could make this breach especially expensive and complicated.
ID Agent to the Rescue: Security awareness training helps your customers avoid ransomware. Build an effective program with the guide How to Build a Security Awareness Training Program. GET IT>>
American Airlines
Exploit: Business Email Compromise
American Airlines: Airline





Risk to Business: 2.639 = Moderate
American Airlines has filed a breach notice declaring that it has had a data breach that may have impacted personal data for about 1700 customers and employees. Bleeping Computer detailed the incident saying that the American Airlines Cyber Security Response Team found out the attack from the targets of a phishing campaign that was using an employee’s hacked Microsoft 365 account to send phishing messages. Reportedly, the attacker accessed multiple employees’ accounts via phishing and used them to send more phishing emails to additional targets that have not been named.





Risk to Individual: 2.714 = Moderate
Employee or customer personal information exposed in the attack may have included employees’ and customers’ names, dates of birth, mailing addresses, phone numbers, email addresses, driver’s license numbers, passport numbers or certain medical information.
How it Could Affect Your Customers’ Business: Business email compromise can take many forms but it is always an expensive nightmare in the end.
ID Agent to the Rescue: Learn more about real BEC scams and how to stay out of trouble in The Comprehensive Guide to Business Email Compromise. DOWNLOAD IT>>


Learn to identify and mitigate fast-growing supply chain risk with this eBook. DOWNLOAD IT>>


UK – Revolut
Exploit: Social Engineering
Revolut: Digital Bank




Risk to Business: 1.102 = Extreme
Revolut, a London-based digital banking application that provides banking, investing, currency transfer and other money management services to some 16 million users globally, has experienced a data breach. The FinTech startup confirmed that the personal information of an unspecified number of users (reports point to 50K customers) was accessed illegally after what the company is terming “a social engineering attack” in early September. The company said that impacted customers have been informed via email and relevant authorities have been informed. No information was available on the exact nature of the exposed data at press time.
How it Could Affect Your Customers’ Business: This kind of bad publicity could be a serious problem for a start-up in the competitive financial services space.
ID Agent to the Rescue: Are you offering the right training solution to help your clients avoid risks like this? Find out with the Security Awareness Training: Buyer’s Guide for MSPs DOWNLOAD IT>>
Portugal – TAP Air Portugal
Exploit: Ransomware
TAP Air Portugal: Airline





Risk to Business: 1.637 = Severe
The Ragnar Locker ransomware group has claimed responsibility for a ransomware attack that hit TAP Air Portugal, the country’s state-owned flagship airline. The incident began a month ago but was just confirmed by the airline. Ragnar Locker has been advertising the stolen data on its dark website since early September. No ransom amount has been reported, and the group has posted a portion of the stolen data already. Portugal’s President Marcelo Rebelo de Sousa, MPs, government staff and high-ranking military officers are among the passengers whose data has been stolen.





Individual Risk: 1.902 = Severe
Exposed customer data includes names, addresses, email addresses, phone numbers, corporate IDs, travel information, nationality, gender and other personal information.
How it Could Affect Your Customers’ Business: This breach could have far-reaching implications because it includes the personal information of major government players.
ID Agent to the Rescue: A strong security culture reduces the risk of an incident. Help your clients build one with The Building a Strong Security Culture Checklist! DOWNLOAD IT>>


Get tips from experts in our webinar MSP Cybersecurity Roundtable: How to Improve Your Incident Response Plan WATCH NOW>>


Australia – Optus
Exploit: Ransomware
Optus: Telecom




Risk to Business: 1.102 = Extreme
Australia’s second-largest telecom Optus has been hit by a ransomware attack. One of the largest data breaches in Australian history, the incident impacts an estimated 10 million customers or about one-third of Australia’s population. A bad actor using the moniker “optusdata” claimed to be the force behind the attack and initially posted a ransom demand of $1.5 million as well as the personal data of about 10k people on a dark web forum. They’ve since withdrawn that post. Some news articles have pointed at an API interface configuration error as the access point for the bad guys, but that has not been confirmed. The incident is under investigation.




Risk to Business: 1.236 = Extreme
Customer data has been exposed including home addresses, drivers’ licenses, passport numbers. names, addresses, phone numbers, email addresses and individuals’ preferred pronouns. The company says that no financial or commercial account data was accessed.
How it Could Affect Your Customers’ Business: An incident this massive is a catastrophe that may spur some changes in Australia’s data privacy laws.
ID Agent to the Rescue: Sell clients on the benefits of security and compliance training with the bottom-line data in The Business Case for Security Awareness Training. DOWNLOAD IT>>


See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


See how today’s biggest threats may impact your MSP and your customers in our security blogs.
- What Is Email Spoofing?
- How AI Protects Businesses from BEC
- 5 Overlooked Ways a Ransomware Attack Impacts a Company’s Bottom Line
- These 2 Cyberattacks Are Today’s Nastiest Threats Against Businesses
- The Week in Breach News: 09/14/22 – 09/20/22


It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>


8 New Training Courses Were Added to BullPhish ID in September
Eight new training courses have been added to BullPhish ID since the start of September. These video lessons are now available in the BullPhish ID Portal.
- Introduction to Business Email Compromise
- BEC Techniques & Red Flags
- PIPEDA 10 Principles
- UK GDPR vs. EU GDPR
- Social Media Phishing (Angler Phishing)
- Executive Impersonation/Whaling
- CMMC Understanding the 5 Maturity Levels
- Security for Remote & Hybrid Workers
Learn more about product updates, enhancements, integrations and new training courses in the BullPhish ID release notes. SEE RELEASE NOTES>>


New Product Sheets Are Here!
Fresh product sheets are available now for BullPhish ID and Dark Web ID in two versions. (MSPs: Product sheets for your customers are available in Powered Services Pro.)
Dark Web ID Product Sheet for Businesses DOWNLOAD IT>>
Dark Web ID Product Sheet for MSPs DOWNLOAD IT>>
BullPhish ID Product Sheet for Businesses DOWNLOAD IT>>
BullPhish ID Product Sheet for MSPs DOWNLOAD IT>>
Did you miss…? Security Awareness Training: Buyer’s Guide for MSPs DOWNLOAD IT>>


Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>




5 Reasons Why Your Clients Will Benefit from AI & Security Automation
Are your clients choosing to update their security with solutions that take advantage of AI and security automation? Those technologies have transformed cybersecurity for a reason. AI and security automation provide businesses a wide array of advantages, including helping them recover quickly and save money in the event that the worst does happen, and they experience a data breach. Plus, solutions that leverage AI and security automation aren’t prohibitively expensive. In fact, they can be cheaper than traditional solutions doing the same job. These five reasons are compelling arguments why you and your clients should consider upgrading to a more advanced approach to defense.



Find the perfect training solution for your clients & your MSP with our MSP-focused buyer’s guide. DOWNLOAD IT>>
1. The cost of a data breach is higher than ever
The IBM Cost of a Data Breach Report 2022 noted that the cost of a data breach has never been higher, reaching $4.35 million this year, an increase of 2.6% from the 2021 cost of $4.2 million per incident, which was at the time the highest ever recorded in the 17 years of the study. It’s also a look at how the data breach landscape is progressing and the way that risk has evolved over time. This represents a major jump in the cost of a breach in a two-year span, up 12.7% from 2020’s $3.86 million, illustrating the constantly rising danger of a data security incident to businesses. But there is some good news. Organizations that have invested in AI and security automation enjoy substantial cost savings in the event of a data breach.


Gain expert insight in the MSP Cybersecurity Roundtable: How Infrastructure Attacks Can Hurt Every Business. WATCH NOW>>
2. The presence of AI & automation affects the cost of a data breach more than any other factor
It’s easy to see that investing in AI and security automation is money well spent. The IBM Cost of a Data Breach Report offers a snapshot of the impact choosing those technologies has on the cost of a data breach. This is the fifth year that IBM researchers have examined the impact of AI and security automation on the cost of a data breach. In the context of this report, implementing security automation and AI refers to enabling security technologies that augment or replace human intervention in the identification and containment of incidents and intrusion attempts. Data about the performance and benefits of advanced technology is compared to data gathered from organizations that rely solely on manual security processes. No factor impacts the cost of a data breach more than the presence of AI and security automation.
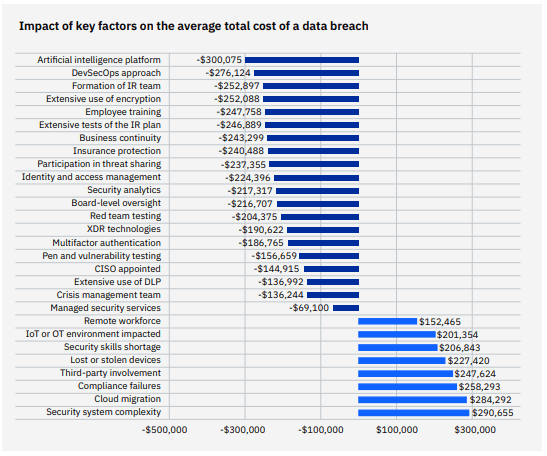

Source: IBM


Set businesses on the zero trust path with the 6 Tips for Implementing Zero Trust Security infographic! GET IT>>
3. AI & security automation slashes data breach costs dramatically
Companies that have taken the plunge and transformed their security with automation and AI-powered tools save a substantial sum in the event that they have a data breach. The top cost mitigation in the study, researchers determined that a data breach at an organization that has fully deployed security AI and automation costs $3.05 million less than breaches at organizations with AI and automation deployed. That’s a huge 65.2% difference in average breach. This result represents the largest cost savings in the study, definitively proving that AI and security automation are powerhouse technologies that businesses can look to as a tool to reduce costs even in the event of a damaging incident.
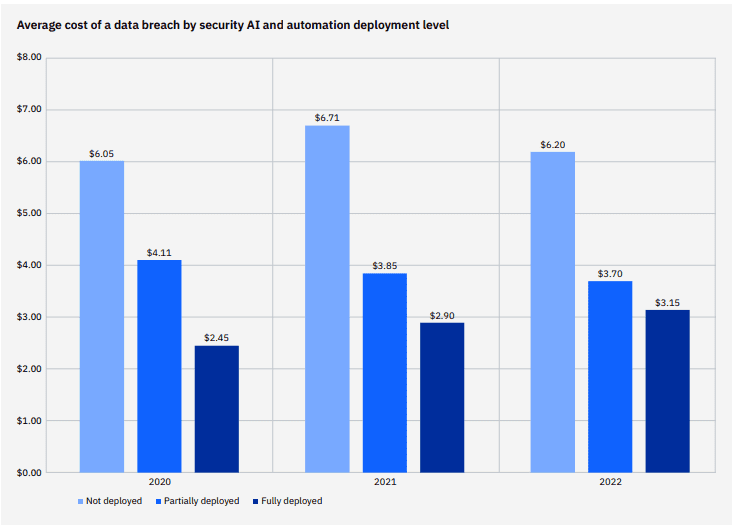

Source: IBM


See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>
4. Security automation & AI reduce breach detection & response times
Companies with fully deployed security AI and automation were able to detect and contain a breach much more quickly than organizations that didn’t have security AI and automation on their side. Organizations with fully deployed security AI and automation took an average of 181 days to identify and 68 days to contain a data breach, for a total lifecycle of 249 days. Compare that to the performance of companies without security AI and automation, where it took an average of 235 days to identify and 88 days to contain a breach, for a total lifecycle of 323 days. That’s 74 long, expensive days more than it takes to detect a breach at an organization utilizing AI and security automation. Even just some AI and security automation in place makes a difference. The average time to identify and contain a breach in organizations with partial deployment was a total of 299 days, still 24 days better than the time to detect and mitigate a breach at companies that didn’t choose to invest in security automation and AI technology.
Breach Response & Mitigation Times by Level of AI & Automation Deployment
| Level of AI & automation present | Days to detect & mitigate a breach |
| None | 323 |
| Low | 299 |
| High | 249 |
Source: IBM


Learn how to spot and stop malicious insiders and educate users with this handy infographic! GET IT>>
5. Smart companies are already investing in AI technology
Fortunately, an increasingly large number of organizations every year are getting the message about the big advantages they’ll gain from selecting AI-enabled and automated solutions. In the 2022 survey, the share of organizations with no security AI and automation deployed decreased from 35% in 2021 to 30% in 2022, down five percent. That drops even more over a two-year span, down from 41% of organizations in 2020 without AI or security automation in place, a difference of 11 percentage points. Most businesses surveyed here had at least some automation in place. The number of businesses that researchers classified as having fully or partially deployed security AI and automation in place increased by five percentage points, from 65% to 70%, between 2021 and 2022. However, it’s notable that there was a big jump in the number of companies with fully deployed security AI and automation. That number climbed by six percentage points, from 25% to 31% a gain of 10 points between 2021 and 2022. This shows that forward-thinking companies are increasingly opting for security automation and AI-enabled technologies to bolster their security.
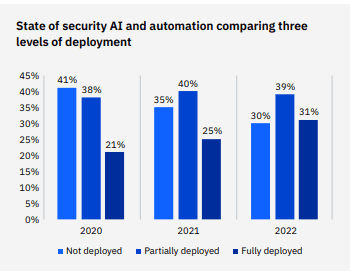

Source: IBM


Learn how to defeat terrifying cybersecurity monsters to keep systems & data safe in a dark world! READ IT IF YOU DARE!>>
Help clients stay safe in a dangerous world
Protecting your clients from cyberattacks is a tall order, but these award-winning security solutions can help you get the job done at a price you’ll both love.
Security awareness and compliance training plus phishing simulation
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size. This powerhouse is the channel leader in phishing simulations.
- An extensive library of security and compliance training videos in eight languages
- Plug-and-play or customizable phishing training campaign kits
- New videos arrive 4x per month and new phishing kits are added regularly
- Easy, automated training delivery through a personalized user portal
In a report by Microsoft, analysts determined that when employees receive simulated phishing training, they’re 50% less likely to fall for phishing.
You’ll love our latest integration between BullPhish ID and Graphus! If you’re already using BullPhish ID for security and compliance awareness training and phishing simulations, you’ll love our latest integration Advanced Phishing Simulations (Drop-A-Phish). This feature leverages the power of integration with Graphus to eliminate the need for domain whitelisting and ensure 100% campaign deliverability to end users when running phishing simulations. LEARN MORE>>
Dark web monitoring
Dark Web ID offers best-in-class dark web intelligence, reducing credential compromise risk.
- 24/7/365 monitoring using real-time, machine and analyst-validated data
- Fast alerts of compromises of business and personal credentials, including domains, IP addresses and email addresses
- Live dark web searches find compromised credentials in seconds
- Create clear and visually engaging risk reports
Automated, AI-powered antiphishing email security
Graphus AI-enabled, automated email security that catches 99.9% of sophisticated phishing threats and offers amazing benefits.
- Forget old-fashioned safe sender lists. Graphus analyzes the content of messages using more than 50 points of comparison to suss out fakes fast.
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- 3 layers of powerful protection at half the cost of competing solutions
- Don’t waste time on fussy configurations or adding threat reports. AI does that for you, getting everything up and running with just a few clicks and minimal maintenance.


Make sure your clients have all the bases covered with the Computer Security To-Do Checklist! GET IT>>


Connect IT Local is coming to a city near you! Join us for our free Cybersecurity Series in Hartford, CT on October 4th for a half-day of informative sessions from Kaseya IT experts and industry leaders, lunch and a networking happy hour at the beautiful Society Room. REGISTER NOW>>
September 28-30: SpiceWorld 2022 REGISTER NOW>>
October 6-7: ASCII MSP Success Summit 2022 – Dallas REGISTER NOW>>
October 13: Cybersecurity Summit in Scottsdale REGISTER NOW>>
October 25-26: Southwest US Summit REGISTER NOW>>
November 2-3: ChannelPro SMB Forum 2022: Los Angeles REGISTER NOW>>
December 6: Connect IT Local – Atlanta REGISTER NOW>>
December 8: Connect IT Local – Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!


Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!